- Framework for Improving Critical Infrastructure Cybersecurity
O v e r v
The Framework is a risk-based approach to managing cybersecurity risk, and
Ho w
An organization can use the Framework as a key part of its systematic process for identifying, assessing,
https://www.nist.gov/sites/default/files/documents/cyberframework/cybersecurity-framework-021214.pdf
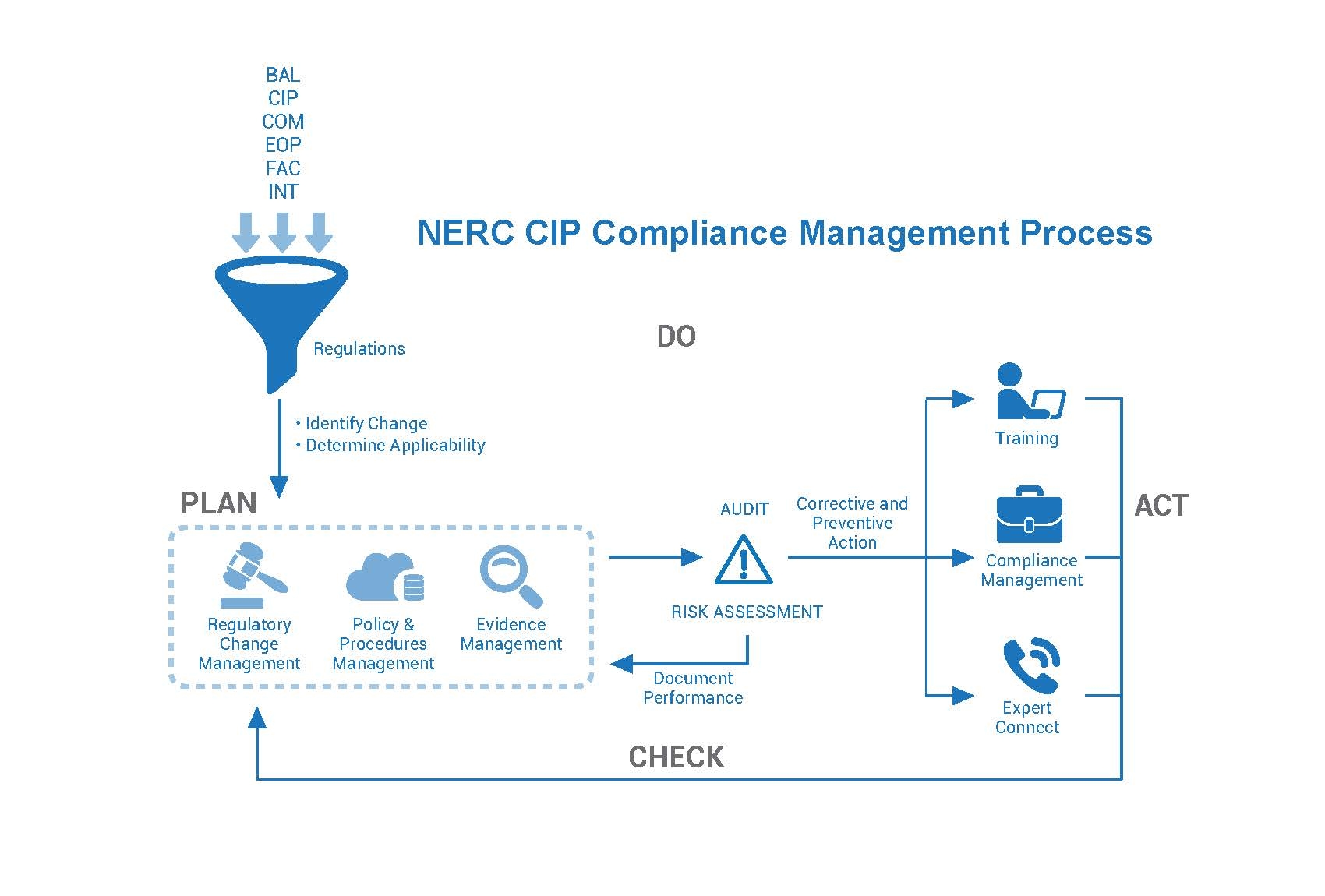
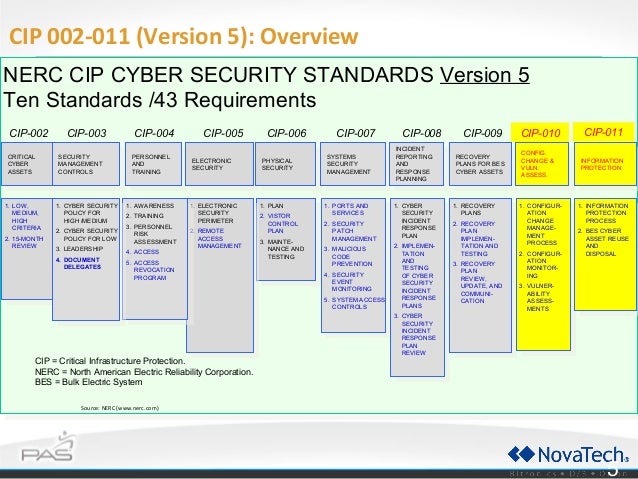
- The NERC CIP (North American Electric Reliability Corporation critical infrastructure protection) plan is a set of requirements designed to secure the assets required for operating North America's bulk electric system.
The NERC CIP plan
CIP-002-1: Critical Cyber Asset Identification
CIP-003-1: Security Management Controls
CIP-004-1: Personnel and Training
CIP-005-1: Electronic Security Perimeters
CIP-006-1: Physical Security of Critical Cyber Assets
CIP-007-1: Systems Security Management
CIP-008-1: Incident Reporting and Response Planning
CIP-009-1: Recovery Plans for Critical Cyber Assets
https://searchcompliance.techtarget.com/definition/NERC-CIP-critical-infrastructure-protection
- What You Need to Know about NERC CIP Cybersecurity Standards
energy and utility organizations have
NERC Critical Infrastructure Protection (CIP) standards
Critical Assets: These assets include but
https://www.trustwave.com/en-us/resources/blogs/trustwave-blog/what-you-need-to-know-about-nerc-cip-cybersecurity-standards/
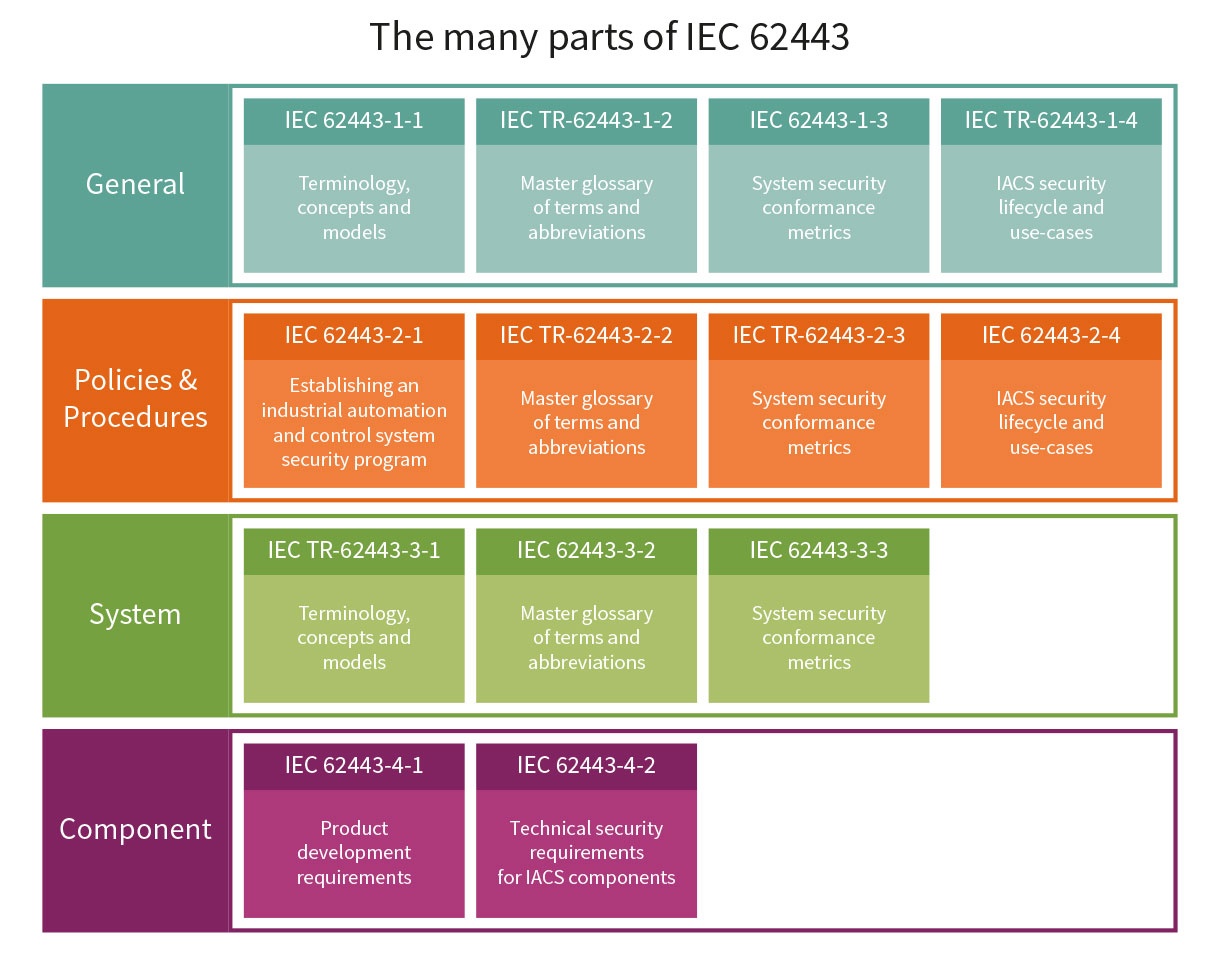
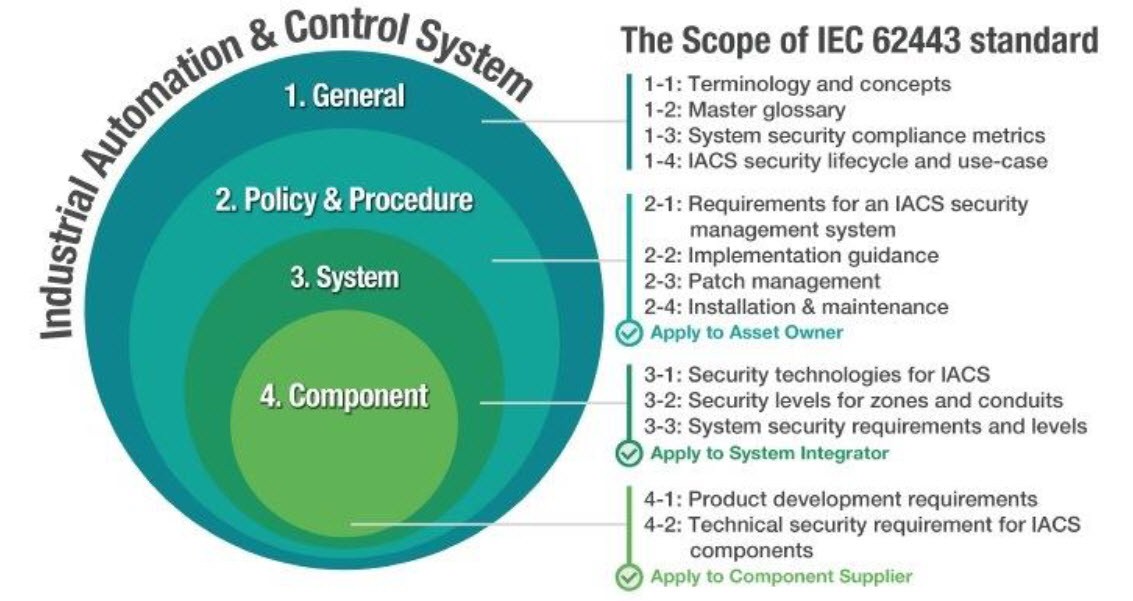
- New ISA/IEC 62443 standard specifies security capabilities for control system components
The ISA/IEC 62443 series of standards, developed by the ISA99 committee and adopted by the International
https://www.isa.org/intech/201810standards/
- IEC 62443 Security Assurance Levels Explained
Schneider Electric has created a white paper to introduce IEC 62443 concepts to an individual with limited exposure to cybersecurity in industrial control systems. The paper defines security assurance levels and illustrates how architectures can change as
https://blog.se.com/cyber-security/2018/03/30/iec-62443-security-assurance-levels-explained/
- How to implement IEC 62443
With Industrie 4.0 and Industrial IoT, the Industrial Automation and Control Systems industry faces exciting opportunities. Along with these opportunities come security threats:
https://www.infineon.com/cms/en/product/promopages/iec62443/