- Setting Up A Penetration Testing Lab
Setting up a test lab on a single machine
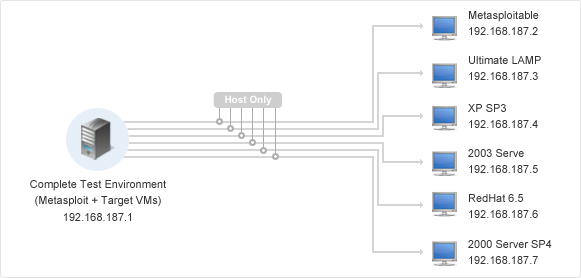
If you have limited resources, the best way thing to do is use a single machine to set up your virtual machines and Metasploit Framework box.
Setting up a test lab on multiple machines
In this
type of test lab environment, you will want to keep your vulnerable machines unavailable to any machine except for your penetration testing box; therefore, it’s important to make the vulnerable machine dependent on the Metasploit Framework box for connectivity. In the section below, we’ll show you how to set up the access to go out on eth0 for the Metasploit Framework box and access to go to the target box on eth1.
The
Metasploitable and
UltimateLAMP vulnerable VMs are Ubuntu machines running vulnerable services and containing weak accounts.
The
Metasploitable VM focuses on network-layer vulnerabilities, while the
UltimateLAMP VM is primarily focused on web vulnerabilities.
The
Metasploitable VM also contains a weak system account with the username user and the password user.
The default login is
msfadmin:msfadmin.
Several vulnerable applications have been installed on the VM.
The
UltimateLAMP VM
's default credentials are:
root:vmware. Each application is available by browsing to
:80 on the VM's assigned IP address.
https://kb.help.rapid7.com/v1.0/docs/setting-up-a-penetration-testing-lab
UltimateLAMP includes a long list of popular LAMP stack applications. For more
information take a look
a the UltimateLAMP products list.
With the success of this first product, research has already
commenced in our next two products
UltimateLAMJ (Open Source Java Based Applications) and
UltimateLAMR (Open Source Ruby Applications).
https://www.vulnhub.com/entry/ultimatelamp_02,36/
- Metasploitable is a virtual machine based on Linux that contains several intentional vulnerabilities for you to exploit. Metasploitable is essentially a penetration testing lab in a box, available as a VMware virtual machine (VMX). (The Metasploitable login is “msfadmin”; the password is also “msfadmin”.)
https://information.rapid7.com/metasploit-framework.html
- Metasploit and Metasploitable 2 installation
Username: msfadmin
Password: msfadmin
Metasploitable 2 is an intentionally vulnerable Linux machine which can be downloaded and setup as a virtual machine in any hypervisor such as VMware Player and Virtual box. In the Metasploitable 2 tutorial we will be setting up the vulnerable Linux machine in VMware Player.
https://www.hackingtutorials.org/metasploit-tutorials/metasploit-metasploitable-2-installation/
- The Samurai Web Testing Framework is a virtual machine, supported on VirtualBox and VMWare, that has been pre-configured to function as a web pen-testing environment. The VM contains the best of the open source and free tools that focus on testing and attacking websites.
We have included the tools used in all four steps of a web pen-test.
reconnaissance tools
such as the Fierce domain scanner and
Maltego.
mapping tools
such as
WebScarab and
ratproxy.
discovery
w3af and burp
exploitation
BeEF,
AJAXShell
http://www.samurai-wtf.org/
- Emulab is a network testbed, giving researchers a wide range of environments in which to develop, debug, and evaluate their systems.
https://www.emulab.net
- ORBIT is a two-tier wireless network emulator/field trial designed to achieve reproducible experimentation, while also supporting realistic evaluation of protocols and applications.
http://www.orbit-lab.org/
- PlanetLab is a global research network that supports the development of new network services.
https://www.planet-lab.org/
- These virtual machine hacking challenges, more commonly known as boot2roots, are relatively easy to make
It begins with an idea; think of a challenge (or a set of challenges), that you’d like a player to solve.
A goal should be set, such as
obtaining root access on the virtual machine, or getting access to a flag. The challenges
that you come up with, will define the difficulty level of the boot2root
I prefer creating my boot2roots using
VMware ESXi and exporting it into an OVA file. OVAs can be imported by all incarnations of
VMware, and by
VirtualBox
Whatever
hypervisor you choose,
you should try to test it on the popular ones such as
VMware Player and
VirtualBox - both of which are free.
When you’re satisfied with everything, it’s time to make your boot2root public! Announce it on Twitter, your blog, IRC, whatever.
VulnHub makes a slew of boot2roots available so
you should definitely
consider having it hosted there.
https://blog.techorganic.com/2013/12/10/creating-a-virtual-machine-hacking-challenge/
- when we connect to an IP address, the device provides a banner identifying itself and some of its parameters.
This information can be
VERY useful for searching for vulnerable or unprotected devices.
It
was developed by John Matherly in 2009 and
it is named Shodan. You can find it at www
.shodan.io
Matherly's crawler scans each IP address (there are 4.3B
IPv4 IP addresses) and attempts to pull and collect the banner information from each device.
This information in the banner usually includes the manufacturer of the device and some key parameters.
It's important to note here that
Shodan indexes the data that
is presented in the banner.
It has no way of knowing whether the banner is accurate.
Some firms
that are vigilant about security
actually replace these banners with fake or bogus banners to throw off
Shodan or attackers.
https://www.hackers-arise.com/single-post/2016/06/22/Using-Shodan-The-Worlds-Most-Dangerous-Search-Engine
- CHECK POINT THREAT ALERT: SHODAN
Shodan can identify the physical location of any Internet-connected equipment,
as well as its IP address, and often even what type of software it’s running.. This provides sufficient information for hackers to carry out targeted attacks.
https://blog.checkpoint.com/2016/01/04/check-point-threat-alert-shodan/
- information disclosure in server banner. In Apache 2.4, there is a default setting “ServerTokens Full” which means Server response header field which is sent back to clients includes a description of the generic OS-type of the server as well as information about compiled-in modules.
To prevent the disclosure of configuration information by your Apache instance, the best general-purpose strategy is to implement the CIS Benchmark for establishing a secure configuration posture for Apache HTTP Server. In CIS Apache HTTP Server 2.4 Benchmark,
more than 15% of the recommendations relate to prohibiting unnecessary but sensitive information disclosure, and provide a good baseline for most environments
https://blog.qualys.com/securitylabs/2015/01/26/protect-your-applications-from-hacker-research
No comments:
Post a Comment