IP (short for Internet Protocol) specifies the technical format of packets and the addressing scheme for computers to communicate over a network.
Transmission Control Protocol (TCP), which establishes a virtual connection between a destination and a source.
IP by itself can be compared to something like the postal system. It allows you to address a package and drop it in the system, but there's no direct link between you and the recipient. TCP/IP, on the other hand, establishes a connection between two hosts so that they can send messages back and forth for a period of time.
IPv4 and a new version called IPv6. IPv6 is an evolutionary upgrade to the Internet Protocol. IPv6 will coexist with the older IPv4 for some time.
- The Difference Between IPv6 and IPv4 IP Addresses
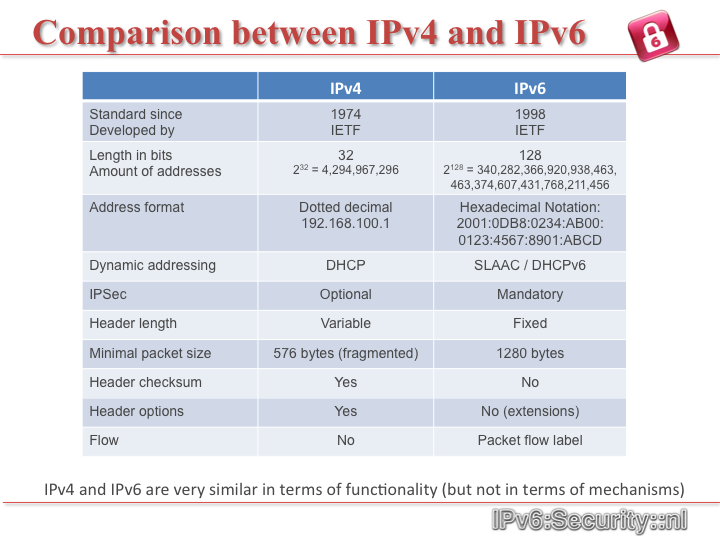
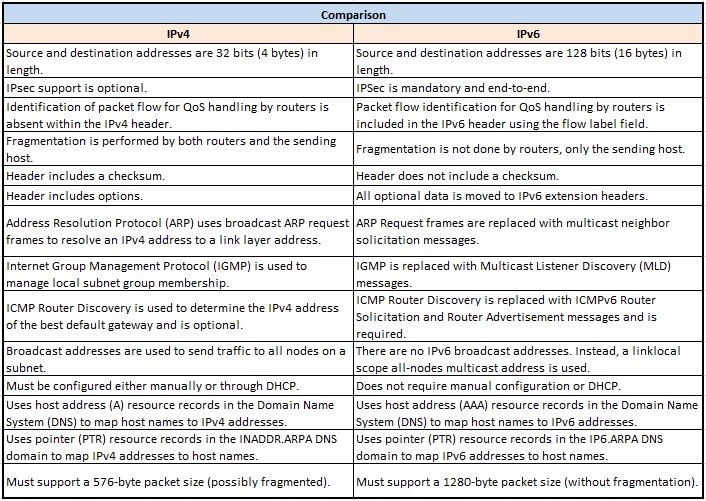
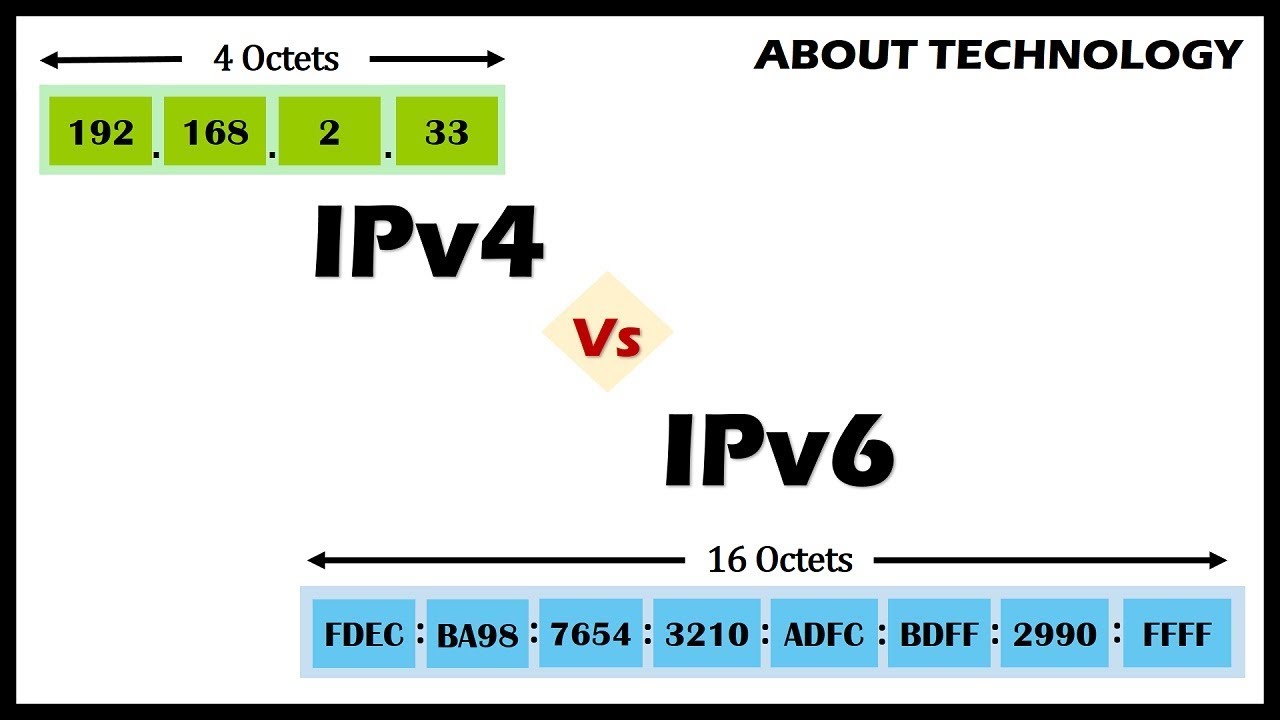
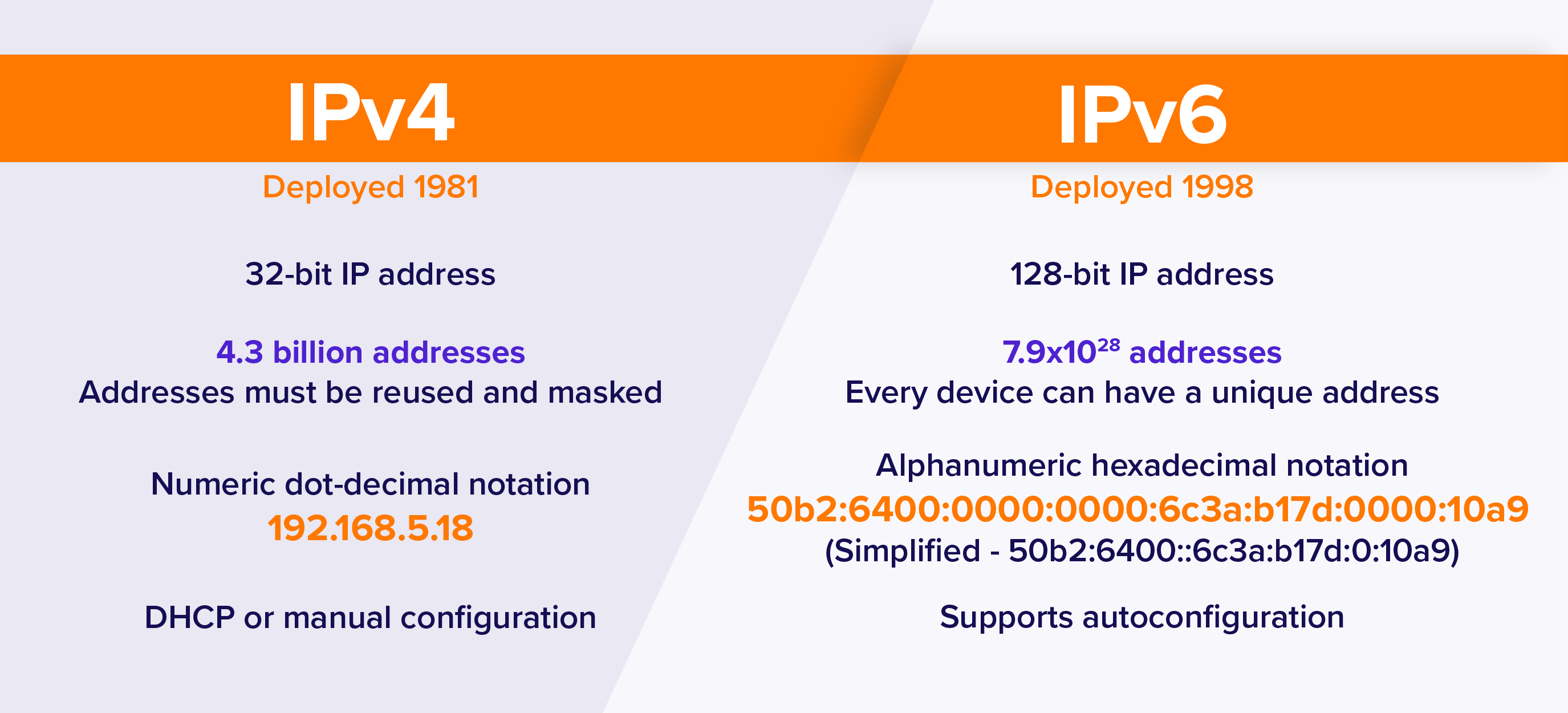
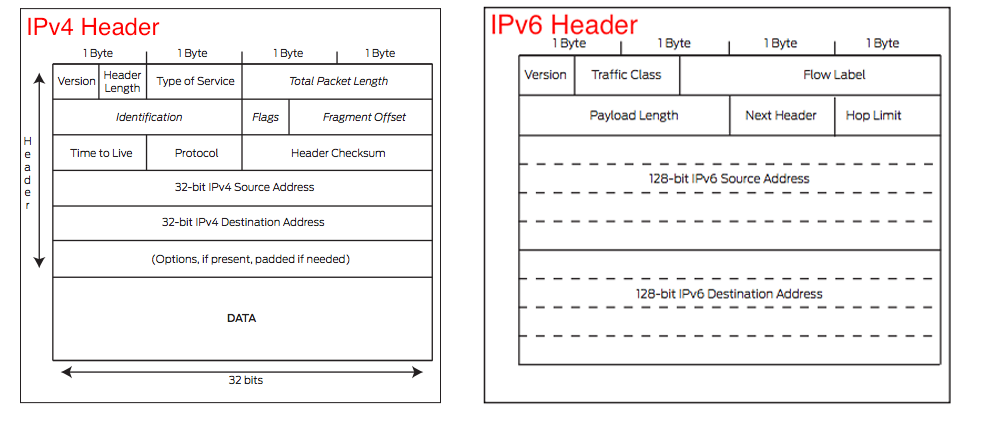
An IP address is binary numbers but can be stored as text for human readers. For example, a 32-bit numeric address (IPv4) is written in decimal as four numbers separated by periods. Each number can be zero to 255. For example, 1.160.10.240 could be an IP address.
Addresses are 32 bits (4 bytes) in length.
IPv6 addresses are 128-bit IP address written in hexadecimal and separated by colons. An example IPv6 address could be written like this: 3ffe:1900:4545:3:200:f8ff:fe21:67cf
Addresses are 128 bits (16 bytes) in length
1.Simplified header format.Even though the IPv6 header contains two 128 bit addresses (source and destination IP address) the whole header has a fixed length of 40 bytes only. This allows for faster processing.
2.Address extended to 128 bits.
3.A lot of the new IPv6 functionality is built into ICMPv6 such as Neighbor Discovery, Autoconfiguration, Multicast Listener Discovery, Path MTU Discovery.
4.Enhanced Security and QoS Features.
- Why are we running out of IPv4 addresses?
IPv4 uses 32 bits for its Internet addresses. That means it can support 2^32 IP addresses in total — around 4.29 billion. That may seem like a lot, but all 4.29 billion IP addresses have now been assigned to various institutions, leading to the crisis we face today.
How does IPv6 solve this problem?
As previously stated, IPv6 utilizes 128-bit Internet addresses. Therefore, it can support 2^128 Internet addresses — 340,282,366,920,938,000,000,000,000,000,000,000,000 of them to be exact. That's a lot of addresses, so many that it requires a hexadecimal system to display the addresses. In other words, there are more than enough IPv6 addresses to keep the Internet operational for a very, very long time.
http://mashable.com/2011/02/03/ipv4-ipv6-guide/
IPv4 vs IPv6
Address space
End-to-End Connectivity
Ease of configuration
Security concerns
QoS
https://docs.google.com/viewer?a=v&q=cache:R-ZDXo1midMJ:www.uwplatt.edu/csse/courses/prev/csse411-materials/f09/Keith%2520Wichman%2520-%2520Seminar%2520IPv6.ppt+&hl=en&pid=bl&srcid=ADGEEShmTC41diPwxG8iBpS8R7UYKZyIkcmDhE1qnq7YM8LntEOcpXclld9StzSiXzzPmGkW-5Y1pNxHIgpn-2k1_150YFKCH0d_8yjReQA8rxuf6SyxI91hN3_ahIy9eYa12fjo1IHL&sig=AHIEtbSJ3HSo7oSDinoEY7_B1JQo3rRtnA
6in4 is an Internet transition mechanism for migrating from Internet Protocol version 4 (IPv4) to IPv6.
6in4 uses tunneling to encapsulate IPv6 traffic over explicitly-configured IPv4 links as defined in RFC 4213
6in4 traffic is sent over the IPv4 Internet inside IPv4 packets whose IP headers have the IP protocol number set to 41.
This protocol number is specifically designated for IPv6 encapsulation.
The 6in4 protocol has no security features, thus one can easily inject IPv6 packets by spoofing the source IPv4 address of a tunnel endpoint and sending it to the other endpoint. This problem can partially be solved by implementing network ingress filtering or with IPsec. Another solution is to use a secure protocol such as AYIYA or other tunneling methods that compute digital signatures for each packet thus facilitating verification of packet authenticity.
The mentioned packet injection loophole of 6in4 was exploited for a research benefit in a method called IPv6 Tunnel Discovery which allowed the researchers to discover operating IPv6 tunnels around the world.
http://en.wikipedia.org/wiki/6in4
- IPv6 transition mechanisms
IPv6 transition mechanisms are technologies that facilitate the transitioning of the Internet from its initial (and current) IPv4 infrastructure to the successor addressing and routing system of Internet Protocol Version 6 (IPv6). As IPv4 and IPv6 networks are not directly interoperable, these technologies are designed to permit hosts on either network to participate in networking with the other network.
Dual IP stack implementation
Dual-stack (or native dual-stack) refers to side-by-side implementation of IPv4 and IPv6. That is, both protocols run on the same network infrastructure, and there's no need to encapsulate IPv6 inside IPv4 (using tunneling) or vice-versa. Dual-stack is defined in RFC 4213
Tunneling
Many current internet users do not have IPv6 dual-stack support, and thus cannot reach IPv6 sites directly. Instead, they must use IPv4 infrastructure to carry IPv6 packets. This is done using a technique known as tunneling, which encapsulates IPv6 packets within IPv4, in effect using IPv4 as a link layer for IPv6
Automatic tunneling
Automatic tunneling refers to a technique by which the routing infrastructure automatically determines the tunnel endpoints
Configured and automated tunneling (6in4)
6in4 tunneling requires the tunnel endpoints to be explicitly configured, either by an administrator manually or the operating system's configuration mechanisms, or by an automatic service known as a tunnel broker
Proxying and translation for IPv6-only hosts
It is likely that hosts newly added to the Internet might only have IPv6 connectivity. For these clients to have backward-compatible connectivity to existing IPv4-only resources, suitable IPv6 transition mechanisms must be deployed.
One form of address translation is the use of a dual-stack application-layer proxy server, for example a web proxy.
http://en.wikipedia.org/wiki/IPv6_transition_mechanisms
Our work aims to develop non-invasive methods for discovering, and collecting information about, IPv6-in-IPv4 tunnels in the Internet at large. This can be useful for diagnostic and troubleshooting purposes, and also provides insight on the evolution and the present structure of the IPv6 Internet.
http://www.dia.uniroma3.it/~compunet/tunneldiscovery/
- IPv6 probable side-effects
4G implements over VoIP which requires IPv6
hard-coded IP addresses in software
of companies: those that have been hacked and those that don’t know they’ve been hacked
Cyber Attack Deterrence by Punishment
a legal foundation for the cyber attack, defense, and deterrence strategies is needed as soon as possible.
Improved Security?
a better network protocol is needed, both for size and for security.
IPv6 offers clear security upgrades over IPv4.
First, IPv6 is much more cryptography-friendly. A mechanism called IP Security (IPSec) is built directly into the protocol’s “code
stack.” IPSec should reduce Internet users’ vulnerability to spoofing, illicit traffic sniffing and Man-in-the-Middle (MITM) attacks.
IPv6 also offers end-to-end connectivity, which is afforded by the incredibly high number of IP addresses available. Since it is possible, in theory, to give anything anIP address, any two points on the Internet may communicate directly with each other.
For example, the astronomical number of IP addresses may mean that attackers will no longer be able to randomly “scan” the Internet to find their victims.
IPv6 Answers Some Questions, Creates Others
Hackers have already demonstrated that IPv6 is not invulnerable to many traditional, IPv4 attack methods, including DoS packetcrafting, and MITM attacks. Vulnerabilities in software (operating systems, network services, web applications) will continue to exist, no matter which protocol they use
And perhaps most crucially, although IPSec is available, it is not required
The need for cyber defense exercises (CDX) is clear.
virtual battlefield
A robust CDX requires a team-oriented approach.
There are friendly forces (Blue), hostile forces (Red), technical infrastructure (Green), and game management (White).
https://ccdcoe.org/uploads/2018/10/2011_Proceedings_0-1.pdf