ITWatchDogs environmental monitors enable you to keep an eye on remote conditions in critical areas for environmental factors including temperature, humidity, airflow, light, sound, door position, power and much more. Get alerts for abnormal conditions via Email, SMS & SNMP traps.
http://www.itwatchdogs.com/
Tuesday, September 29, 2015
KMS
KMS activates computers on a local network, eliminating the need for individual computers to connect to Microsoft. To do this, KMS uses a client–server topology. KMS client computers can locate KMS host computers by using Domain Name System (DNS) or a static configuration. KMS clients contact the KMS host by using remote procedure call (RPC). KMS can be hosted on computers that are running the Windows Vista, Windows 7, Windows Server 2003, Windows Server 2008, or Windows Server 2008 R2 operating systems
Labels:
windows
Sunday, September 27, 2015
Preboot Execution Environment
In computing, the
https://en.wikipedia.org/wiki/Preboot_Execution_Environment
- In order
to setup PXE server, you need to have a working DHCP and TFTP servers.DHCP server is used to distribute the IP addresses for the network systems, so that the client systems can communicate with PXE server. And,TFTP server is used to download the installation files from PXE server and send them to the PXE clients. We can deploy PXE, and DHCP servers on the same system or use different systems for each server.Due to lack of resources, I have tested this on a single system. You can either use a separate system orsingle machine for all servers.
The setup that requires here is
The Services required on the PXE Server:
1. TFTP
2. DHCP
3. NFS
https://community.mellanox.com/docs/DOC-2164
Labels:
HPC
Power cycling
Power cycling is the act of turning a piece of equipment, usually a computer, off and then on again. Reasons for power cycling include having an electronic device reinitialize its set of configuration parameters or recover from an unresponsive state of its mission critical functionality, such as in a crash or hang situation. Power cycling can also be used to reset network activity inside a modem.
https://en.wikipedia.org/wiki/Power_cycling
https://en.wikipedia.org/wiki/Power_cycling
Labels:
Systems and Networks
Wednesday, September 16, 2015
ISDN
Integrated Services for Digital Network (ISDN) is a set of communication standards for simultaneous digital transmission of voice, video, data, and other network services over the traditional circuits of the public switched telephone networkhttps://en.wikipedia.org/wiki/Integrated_Services_Digital_Network
Labels:
Systems and Networks
Network Address Translation (NAT)
- you could have 4,294,967,296 unique addresses (232). The actual number of
available addresses is smaller (somewhere between 3.2 and 3.3 billion) because ofthe way that the addressesare separated into classes, andbecause some addresses are set aside for multicasting, testing or other special uses.
http://computer.howstuffworks.com/nat1.htm
- NAT serves three main purposes:
Enables a company to use more internal IP addresses. Since they're used internally only, there's no possibility of
Allows a company to combine multiple ISDN connections into a single Internet connection.
http://www.webopedia.com/TERM/N/NAT.html
- Network address translation (NAT) is a
methodology of remapping one IP address space into another bymodifying network address information in Internet Protocol (IP)datagram packet headers while they are in transit across a traffic routing device.[ 1]The technique was originally used for ease of rerouting traffic in IP networks without renumbering every host. It has become a popular and essential tool in conserving global address space allocations in face of IPv4 address exhaustion.
- Network Address Translation (NAT) is the process where a network device, usually a firewall, assigns a public address to a computer (or group of computers) inside a private network. The main use of NAT is to limit the number of public IP addresses an organization or company must use, for both economy and security purposes.
- So what does the size of the Internet have to do with NAT?
When IP addressing first came out, everyone thought
Network Address Translation allows a single device, such as a router, to act as an agent between the Internet (or "public network") and a local (or "private") network. This means that
http://computer.howstuffworks.com/nat.htm
Labels:
Systems and Networks
Sunday, September 13, 2015
Man-In-The-Middle (MITM)
- Proxy only tools
https://www.owasp.org/index.php/Man-in-the-middle_attack
mitmproxy is a free and open source interactive HTTPS proxy.
https://mitmproxy.org/
A Man-In-The-Middle (MITM) attack is achieved when an attacker poisons the ARP cache of two devices with the (48-bit) MAC address of their Ethernet NIC (Network Interface Card). Once the ARP cache hasbeen successfully poisoned , each of the victim devices send all their packets to the attacker when communicating to the other device. This puts the attacker in the middle of the communications path between the two victim devices; hence the name Man-In-The-Middle (MITM) attack. It allows an attackerto easily monitor all communication between victim devices.
- In cryptography and computer security, a man-in-the-middle attack
( often abbreviated to MITM,MitM , MIM, MiM or MITMA) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other
- In computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network.
Generally, the aim is to associate the attacker's MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address tobe sent to the attacker instead.
https://en.wikipedia.org/wiki/ARP_spoofing
- ARP is the Address Resolution Protocol. Essentially all it does is resolve a logical IP address to a physical Hardware (MAC) address.
http://mellowd.co.uk/ccie/?
http://forums.sureshkumar.net/networking-interview-technical-questions/14810-networking-what-arp-how-does-work.html
- ARP cache
Entries in the static ARP table
You can add entries to the static ARP table
Layer 3 switches have a static ARP table. Layer 2 switches do not.
http://www.brocade.com/content/html/en/configuration-guide/FI_08030_L3/GUID-B5A197B6-5EB5-481E-8535-5DC9FD66CA14.html
- Gratuitous ARP could mean both gratuitous ARP request or gratuitous ARP reply.
A gratuitous ARP request is an
Gratuitous ARPs are useful for four reasons:
They can help detect IP conflicts. When a machine receives an ARP request containing a source IP that matches its own, then it knows there is an IP conflict.
They assist in the updating of other machines' ARP tables. Clustering solutions
They inform switches of the MAC address of the machine on a
Every time an IP interface or link goes up, the driver for that interface will typically send a gratuitous ARP to preload the ARP tables of all other local hosts. Thus, a gratuitous ARP will tell us that that host just has had a link up event, such as a link bounce, a machine just being rebooted or the user/
A typical clustering scenario might play out like
Assume that node A
Using the heartbeat protocol, node B determines that node A has died.
Node B configures a secondary IP on an interface with
Node B issues a gratuitous ARP with
https://wiki.wireshark.org/Gratuitous_ARP
- One such
way is to spoof your MAC address and poison thearp table. Sincearp keeps no state information, thearp cache can be overwritten (unlessan entry is explicitly marked as permanent)
http://www.admin-magazine.com/Articles/Arp-Cache-Poisoning-and-Packet-Sniffing
ProxyFuzz
- Different types of network-based evidence
Full content data
Nothing is being filtered, exact copies ofall thetraffic (often called "packet captures", abbreviated toPCAP) are being stored.
Session data
It usually consists of aggregated traffic metadata and usually refers to the conversation between two network entities, grouped together into"flows" and/or groups of network packets related to one another
session data areable to informthe investigator about questions such aswho talked to whom, when, for how long, etc. without looking at any contents of the conversation(s) at all.
all an investigator needs to know is that700,000 packets have been transferred between two otherwise "quiet" network nodeson a Sunday at 02:15 am.
Alert data
Whenever network traffic triggers a pre-defined item of interest (such as a particular pattern of bytes, or counts of activity, or other characteristics) the analyst will be dealing withalert data. Alerts are typically generated by Network Intrusion Detection Systems (NIDS) such as Suricata or Snor
Statistical data
Statistical data providethe analyst with network-related aspects such as the number of bytes contained in a packet trace, start and end times of network conversations, number of services and protocols being used, most active network nodes, least active network nodes, outliers in network usage, average packet size, average packet rate, and so on. It can therefore also actas auseful source for anomaly detectio
Acquiring traffic in cables
Network taps
Inline network tapsare OSI layer 1 which can be insertedinlinebetween two physically connected network devices.The network tap will pass along the packetsandphysically replicate copies to one or more monitoring ports.They are commonly designed to require no power for passively passing packets. This reduces the risk of a network outage caused by the tap. This does not cover the power requirements of the monitoring station though
Vampire taps redevices that pierce the shielding of coaxial cables to provide access to the signal within. The device clamps onto and "bites" into the cable.
Unlike inline network taps, the cable does not need to be severed (or disconnected) for a vampire tap to be installed.
Fibre Optic network taps work similarly to inline taps for copper cables.
Hubs
A network hub is an OSI Layer 1 device that physically connects all stations on a local subnet to one circuit. It maintains no knowledge of what devices are connected to what ports. When the hub receives a frame, it forwards it toall other ports. Therefore, every device connected to the hub physically receives all traffic destined to every other device attached to the hub. Thus, all traffic on the segment can be trivially captured by connecting to any unused port on a hub.A reliable way to determine if a device is actually a hub is to connect a station to it, put the network interface into promiscuous mode, and observe the traffic. If only packets destined for the monitoring station and broadcast traffic can be seen, then the device is a switch. If it is a hub, traffic to all other connected stations should be seen.
Switches
Unlike hubs, switches usesoftware to keep track of which stations are connected to which ports, in its CAM (Content Addressable Memory) table.
A switches CAM table stores MAC addresses with corresponding switch ports.Switches can often be configured to replicate traffic from one or more ports to some other port for aggregation and analysis.The most vendor-neutral term for this is “port mirroring.”
nvestigators will need administrative access to theswitch’s operating system to configure port mirroring. A monitoring station needs to be connected to the mirroring port to capture the traffic. Investigators mustconsider the bandwidth mirroring port in comparison tothe traffic on the monitored ports,not to drop packets
Active acquisition
In cases when the network administrators themselves are not trusted, investigators may need to use the same techniques asattackers.This is not recommended and should be seen only as a measure of last resort, as they cause the switch to operate outside normal parameters and will likely trigger intrusion detection mechanisms in the network.
First, the attacker can flood theCAM table of the switch with information (by sending packets with different MAC addresses). This attack is referred to as “MAC flooding” or “CAM table overflow”. When the CAM table overflows, switches by default will “fail open” to a hub mode of operationand send traffic for systems not in the CAM table out to every port.
Second, an “ARP spoofing”, or “ARP (cache) poisoning” attack can be conducted. The Address Resolution Protocol (ARP) is used by stations on a LAN to dynamically map IPv4 addresses (Layer 3) to corresponding MAC addresses (for IPv6 this function is carried out within ICMPv6, but the principle is otherwise identical). The attacker broadcasts bogus ARP packets, which link the attacker’s MAC address to the victim’s IP address. Other stationson the LAN add this bogus information to their ARP tables, and send traffic for the router’s IP address to the attacker’s MAC address instead. This causes all IP packets destined for the victim station to be sent instead to the attacker (who can then copy, change, and/or forward them on to the victim).
Acquiring traffic in radio networks
There are many protocols in use today that enable wireless networking.For each protocol, there are severalfrequency bandsover which data can be transmitted, with each band subdivided into smaller bands, called channels.Not all frequency bands or all channels are in use everywhere in the world. Most countries limit what frequency and channels are used within their jurisdiction. The consequence isthat network equipment made for one country may operate on different frequencies and channels than one made for another country.Thus, adversaries using wireless technology from a different country which may not be detected by that countries network equipment.
Spectrum analysers are designed to monitor RF frequencies and report on usage. They can be very helpful for identifying rogue wireless devices and channels in use.
WLAN passive evidence acquisition
Tocapture WLAN traffic, investigators need an 802.11 wireless card capable of running in Monitor mode.a mode that many WLAN cards do not support. There is a difference between Monitor mode and Promiscuous mode that can be summed up as follows
An important difference between Monitor mode and promiscuous mode is that in monitor mode the packets are captured in 802.11 format while in promiscuous mode theyare presented in Ethernet (802.3) format. From a forensic standpoint, monitor mode is preferable as it is completely passive and conveys more information. It is recommended to use a special-purpose WiFi monitoring card that can be configured to operate completely passively.
https://www.enisa.europa.eu/topics/trainings-for-cybersecurity-specialists/online-training-material/documents/introduction-to-network-forensics-handbook.pdf
Labels:
security,
Systems and Networks
Monday, September 7, 2015
QoS (Quality of Service) technique
- Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate, excess traffic
is dropped retains
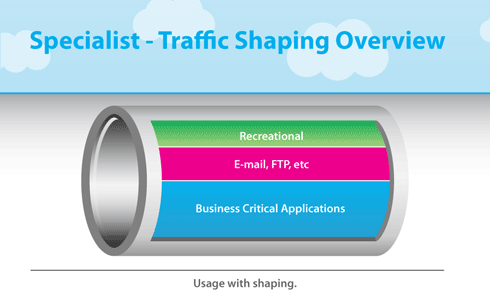
- Shaping is a QoS (Quality of Service) technique
that we can use to enforce lowerbitrates than what the physical interface is capable of. Most ISPs will use shaping or policing to enforce “traffic contracts” with their customers.
- A broadband remote access server (BRAS, B-RAS or BBRAS) routes traffic to and from broadband remote access devices
such as digital subscriber line access multiplexers (DSLAM) on an Internet service provider's (ISP) network.
The BRAS
https://en.wikipedia.org/wiki/Broadband_remote_access_server
- What is Traffic Shaping?
Traffic shaping (also known as packet shaping) is bandwidth management technique that delays the flow of certain types of network packets
The most common type of traffic shaping is application-based traffic shaping. Fingerprinting tools are first used to identify the application associated with a data packet. Based on this,
Many application protocols use encryption to circumvent application-based traffic shaping. To prevent applications from bypassing traffic shaping policies, route-based traffic shaping can
Limited network resources make bandwidth prioritization a necessity. Traffic shaping is
https://www.barracuda.com/glossary/traffic-shaping
- Traffic shaping, also known as packet shaping, is a
type of is forwarded is rate
Traffic shaping techniques are core components of most network architectures. The benefits of traffic shaping include converging network technologies into a common network architecture and guaranteeing performance requirements for
Quality of Service (QoS) is a specific implementation of network traffic shaping.
Data Center LAN Networks
Data Center LAN Networks include traffic categories including:
High-Priority
Network traffic to network storage and for database transactions require low-latency network performance with high reliability. These network applications are highly sensitive to network performance and do not tolerate dropped packets well.
Storage Systems
Database Systems
Medium-Priority
User access to business applications are business critical, but do not have the performance and reliability requirements as Storage and Database systems.
User access to Applications
IP Telephony
Low-Priority
Bulk data transfers will completely consume the bandwidth of a network. If
Large file copies
Data backups
Peer-to-Peer applications
https://www.a10networks.com/blog/traffic-shaping/
- During penetration testing, the main
objective it is required be exploited is required at the same time
Active Fingerprinting
Active fingerprinting
Passive Fingerprinting
also maintains a database for
It
https://resources.infosecinstitute.com/passive-fingerprinting-os/#gref
Taxonomy of OS fingerprinting tools
- Active Fingerprinting
Active fingerpringinting
Xmas attack. This is a specific type of specailly
Port scanning. A port scanner sends queries on specific ports. If the server answers a query on a port, it indicates indicates be sent
Passive Fingerprinting
Passive fingerprinting uses a sniffer (such as Wireshark instead passive fingerprinting cannot be done be done
https://blogs.getcertifiedgetahead.com/active-fingerprinting-passive-fingerprinting/
Labels:
security
Subscribe to:
Comments (Atom)