- NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine things such as the source and destination of traffic, class of service, and the causes of congestion
https://en.wikipedia.org/wiki/NetFlow
Network Monitoring:
network operations (NetOps) and security operations (
SecOps) teams can monitor when and how frequently users access an application in the network.
Network Planning: Team can use
NetFlow to track and
anticipate network growth. For example, they can plan upgrades to increase the number of ports, routing devices or
higher-bandwidth interfaces needed to meet growing demand
Security Analysis: With
NetFlow, security teams can detect changes in network behavior to identify anomalies indicative of a security breach. The data is also a valuable forensic tool to understand and replay the history of security incidents so security teams can learn from them
https://blog.gigamon.com/2018/01/08/what-is-netflow/
- Automating Provisioning of NetFlow Analyzers
The solution proposed automates the provisioning of the
NetFlowanalyzer groups using the central repository. In an environment which is dynamic or has a lot of host’s, automation is a
must to avoid the configurations being out of sync.
If the central database contains detailed information about all the allowed network flows, then this solution can
be extended to automate the generation of
customer defined flow whitelisting rule.
The
NetFlowanalyzer will alert on any flows which are anomalous.
This rule can be very useful to detect any lateral or abnormal flows by malicious users or programs communicating using an unknown protocol or host.
NetFlowanalyzer,
in conjunction with automation, is a great tool to implement detective controls to address Center for Internet Security control
#9
:Limitation and Control of Network
Ports,Protocols,Services as well as control
#12: Boundary Defense.
https://www.sans.org/reading-room/whitepapers/critical/automating-provisioning-netflow-analyzers-37272
- Center for Internet Security (CIS) releases a prioritized list of twenty security controls, named as Critical Security Controls(CSC).
This document focuses on using
NetFlowanalyzer as a tool to address portions of the following CIS Security Controls.
2.1
.CSC #1 Inventory of
Authorized and Unauthorized Devices
An accurate inventory of the hardware is one of the most important security hygiene.
NetFlowcan passively detect any IP device in the network. Routers and switches will export the metadata for all network conversations and forward it to the
NetFlowcollector.IP addresses are available from the source and destination IP address fields in the
NetFlowrecord.The
NetFlowanalyzer will use the flow information from the collector and generate an alert if it detects any unknown IP device (not configured in the analyzer) in the network.
2.2
.CSC #3 Secure Configuration of Hardware and Software
The control recommends automated monitoring and alerting on unexpected open ports or use of insecure protocols
liketelnet, VNC, RDP, and other insecure protocols.
NetFlowrecords contain the network layer-4 attributes, source and destination ports. This information from the
NetFlowcan be used by the
NetFlowanalyzer to detect and report on any new listening port in the Network. The source and destination ports can also
be used to alert on the usage of any insecure protocol based on the standard port numbers used for such communications.
2.1
.CSC #8 Malware Defenses
The goal of this control is to detect and contain the installation, execution, and spread of Malware
.NetFlowcan be use used to detect malware based on its behavior or anomaly in the network behavior. Communication attempts or actual communication from IP-devices to
known command and control or a blacklisted site can
be alerted based on the IP address stored in the
NetFlowrecords. Other typical malware behavior like a lateral movement across the network, host or port scans originating from unexpected network devices, attempt to use an unauthorized DNS server, network traffic pattern deviations
indicating possible data exfiltration’s, Denial of Service or Distributed Denial of Service can
be alerted
2.2
.CSC #9 Limitations and Control of Network Ports, Protocols, and Services
The goal of this control is to monitor and manage the use of ports,
protocol,and services on any networked device
.The intention is to remediate the use of
unknown port or service immediately to reduce the attack surface by removing any
potentiallyvulnerable services or remote listening ports.
NetFlowbased detection can complement the standard network scanner based or local listening port detection.
Advancedmalicious software can evade detection by
portscanners by closing the ports during the scan window. This evasion is not
possible if
NetFlowis used to complement the port scans.
2.3
.CSC #12 Boundary Defense
NetFlowadds another layer of detection for this control.
NetFlowadds another layer of detection for this control. A
NetFlowanalyzer configured with flow whitelist across the trust boundaries can alert on any network anomaly
.NetFlowanalyzers can alert based on the number of packets, bytes of data transferred, rate and thresholds of ingress or egress connections, long running TCP sessions, egress or ingress connections from blacklisted IP to or from the DMZ systems, or any other network behavior anomaly.
2.4
.CSC #13 Data Protection
This critical control is about tools and processes to prevent data exfiltration, mitigate the effect of
exfiltrated data and ensure the confidentiality and integrity of sensitive data
NetFlowdoes not have access to the actual network packets traversing the network. It only has the metadata of the network traffic.
NetFlowcannot inspect traffic and hence cannot look for patterns in the network
trafficto detect data
exfiltrationhowever it can detect anomalous traffic. The
NetFlowanalyzer can learn the traffic behavior over time and can alert on any deviation from the standard traffic.
NetFlowcan also
be configured to generate an alert if it detects traffic
toaknown file transfer ore-mail exfiltration websites
As previously mentioned, the main issue with the manual provisioning of the tool is it is hard to manage and can quickly be out of sync with the central configuration database. Configuration not aligned with existing
setupmakes the system unreliable. Many security tools, such as Security Incident and Event Managers (SIEMs), Intrusion Detection Systems (IDS), Network Intrusion Prevention Systems (NIPS), Network Behavior Analysis (NBA) and other systems require similar configuration. Configuration items described above like host groups, hosts, port groups, port names, and application (with its
correspondingsignature)must be in the Central Configuration Management Database (CMDB). Automated provisioning tools must use the information in CMDB to generate specific provisioning information as required by the product. Automation of provisioning will reduce the manual provisioning errors and ensure that the tools are in sync with the latest information from the CMDB.
NetFlowinformation, supported in most of the routers, switches, and firewalls, with the automated configuration of
NetFlowAnalyzer, helps organizations continuously monitor six of the top 20 Critical Controls.
1
.A user or a process triggers a provisioning process which updates the central configuration database
2
.A process running on the central configuration server frequently checks for any updates to the database. If it detects an update, it dumps configuration files in the format required by the
NetFlowAnalyzer tool
(server groups, application mapping, ports, and protocols, etc.)
3
.The process copies the file to the
NetFlowAnalyzer server using SSH PKA-based authentication using a
low privileged account in a particular directory
4
.A Process running on the
NetFlowanalyzer polls for any updated provisioning files then it compares with previous and checks for any update
5
.If the provisioning files
are updated, it loads the new information into the
NetFlowAnalyzer using the interface provided
https://www.sans.org/reading-room/whitepapers/critical/automating-provisioning-netflow-analyzers-37272
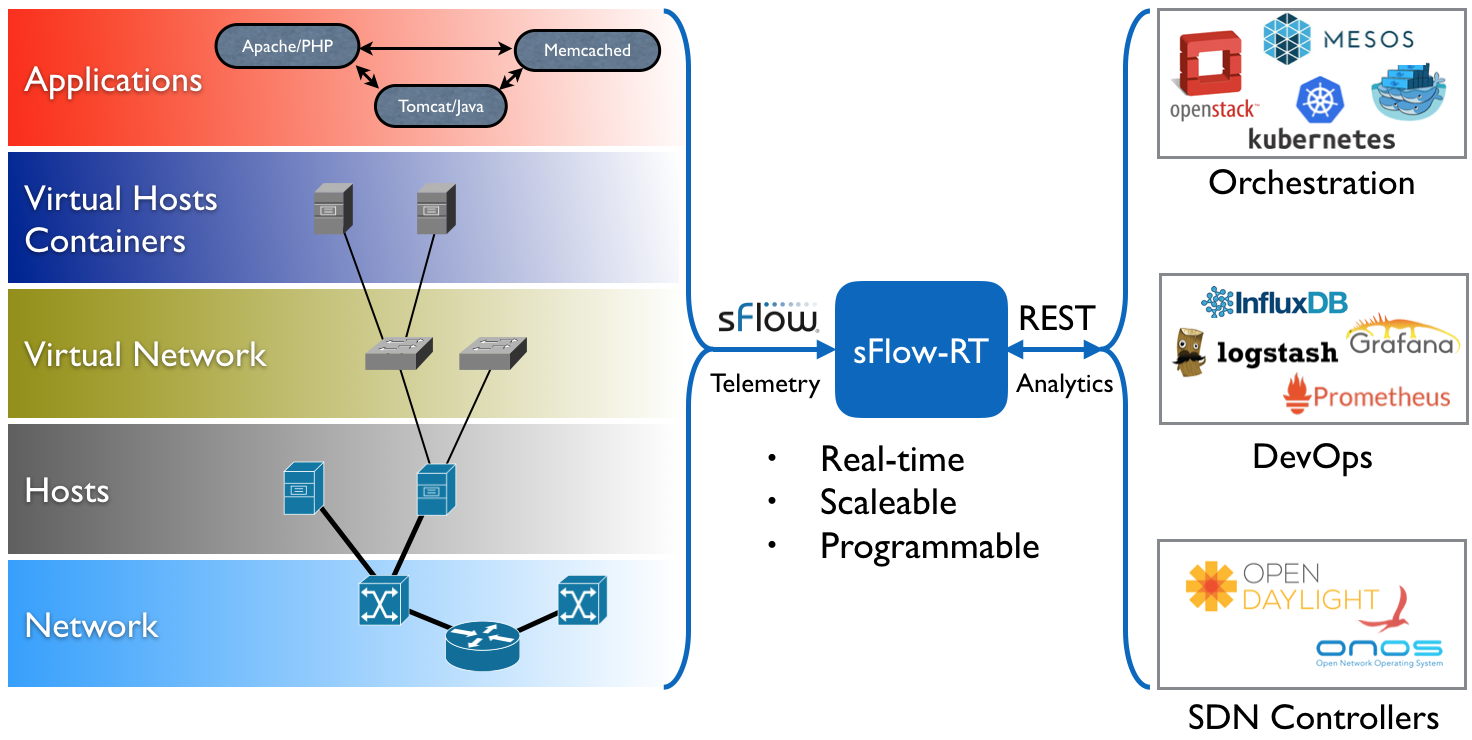
- sFlow® is an industry standard technology for monitoring high speed switched networks. It gives complete visibility into the use of networks enabling performance optimization, accounting/billing for usage, and defense against security threats.
https://sflow.org/
NetFlow is a network protocol developed by Cisco for collecting IP traffic information and monitoring network traffic. By analyzing flow data,
a picture of network traffic flow and volume can be built. Using a
NetFlow collector and analyzer, you can see where network traffic is coming from and going to and how much traffic is being generated.
https://www.solarwinds.com/what-is-netflow
- What is NetFlow/J-Flow/sFlow?
NetFlow data
is generated by network devices like routers and firewalls. Flow data will
generally contain details like source and destination IP addresses, port numbers, protocols, and more.
The term “
NetFlow” is proprietary to Cisco, but other vendors have their own versions of “Flow.” For instance, Juniper calls it “J-Flow”, and several vendors, including HP and Fortinet, use “
sFlow.”
Implementation details vary from vendor to vendor, but most flavors of
xFlow produce the same
sort of data. In this article, we’ll refer to all
xFlow variants as
NetFlow to keep things simple, but
be aware that not all tools support the same flavors of Flow.
How to Enable
NetFlow
Before you can use one of the free flow analyzers,
NetFlow must
be enabled on the devices you want to monitor.
https://www.networkmanagementsoftware.com/5-free-netflow-analyzer-tools-for-windows/
- NetFlow Vs. sFlow: Which is better?
What is a Flow?
A flow is a sequence of packets from a sending application to a receiving application.
What is
NetFlow?
NetFlow is a true flow technology whereby cached flow entries in the hardware (e.g. router/switch) aggregate packets based on a matching tuple which is most often a set of seven key fields:
Which scales better
sFlow or
NetFlow?
Packet sampling can
be performed by
sFlow or
NetFlow which doesn’t scale in a way
that is acceptable to most customers.
For example, a massive burst in traffic (E.g. DoS attack) would cause
sFlow to sample more
as it needs to keep up with 1
:N sampling. With NetFlow, a massive packet volume depending on the attack would likely show up as just a few flows with high packet volumes. The amount of additional work for NetFlow is minimal especially if we are comparing apple to apples with both technologies implemented in hardware.
NetFlow provides details on 100% of the traffic whereas
sFlow often misses the traffic you need to look at making
sFlow almost unusable for network threat detection and forensic analysis.
If I have to sample, which should I choose: flow sampling or packet sampling?
If you must sample, flow sampling over packet sampling is the best option
If
NetFlow is better than
sFlow, why would anyone ever use
sFlow?
Many switches today only support
sFlow.
https://www.plixer.com/blog/netflow-vs-sflow-2/netflow-vs-sflow-which-is-better/
- Switch port Analyzer (SPAN) is an efficient, high performance traffic monitoring system. It duplicated network traffic to one or more monitor interfaces as it transverse the switch. SPAN is used for troubleshooting connectivity issues and calculating network utilization and performance, among many others. There are three types of SPANs supported on Cisco products
Local SPAN: Mirrors traffic from one or more interface on the switch to one or more interfaces on the same switch.
Remote SPAN (RSPAN): An extension of SPAN called remote SPAN or RSPAN. RSPAN allows you to monitor traffic from source ports distributed over multiple switches,
which means that you can centralize your network capture devices. RSPAN works by mirroring the traffic from the source ports of
an RSPAN session onto a VLAN that
is dedicated for the RSPAN session. This VLAN is then
trunked to other switches, allowing the RSPAN session traffic to
be transported across multiple switches. On the switch that contains the destination port for the session,
traffic from the RSPAN session VLAN is simply mirrored out the destination port.
Encapsulated remote SPAN (ERSPAN): encapsulated Remote SPAN (ERSPAN), as the name says, brings generic routing encapsulation (GRE) for all captured traffic and allows it to
be extended across Layer 3 domains.
https://community.cisco.com/t5/network-architecture-documents/understanding-span-rspan-and-erspan/ta-p/3144951
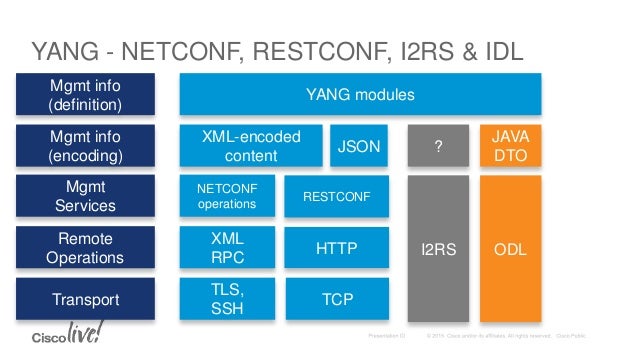
The NETCONF protocol defines a simple mechanism through which
a network device can be managed, configuration data information can
be retrieved, and new configuration data can
be uploaded and manipulated.
http://sdntutorials.com/what-is-netconf/
RESTCONF Overview
A REST like protocol running over HTTP for accessing data defined in YANG using
datastores defined in NETCONF.
http://sdntutorials.com/what-is-restconf/
Step 3. Understanding how to interface with a RESTCONF API
https://developer.cisco.com/learning/modules/dna-restconf-netconf-yang/lab03-using-restconf-to-interface-with-networking-devices/step/3
DEVNET-1152
OpenDaylight YANG Model Overview and Tools
https://www.slideshare.net/CiscoDevNet/devnet-1152-open-daylight-yang-model-overview-tools
Model-driven Programmability: The Rise of Network Automation
https://blogs.cisco.com/getyourbuildon/model-driven-programmability
Simplifying Network Programmability with Model-Driven APIs
https://d1nmyq4gcgsfi5.cloudfront.net/site/ydk/documents/overview/