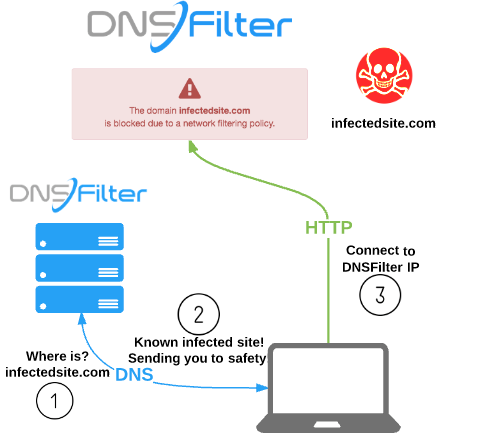
- How Does DNS Filtering Work?
With DNS filtering in place, rather than the DNS server returning the IP address if the website exists,
Can DNS Filtering
Proxy servers and
https://www.spamtitan.com/web-filtering/how-does-dns-filtering-work/
- Open DNS Filtering - Disadvantages You Should Know
When surfing the web,
The OpenDNS filtering service is fast and gives assurance against phishing and different issues frequently experienced when surfing the web
Enhances security by blocking access to malicious and risky sites
Keep malware downloads from malicious and risky sites
Keeps your defense up to date to protect your users as threats arise
OpenDNS filtering service is more reliable and
When blocking a phishing site, the OpenDNS filtering service shows a warning page instead of the fraudulent site.
there are various drawbacks.
The OpenDNS filtering service will know which sites you
The OpenDNS filtering service does not filter the
https://cdome.comodo.com/opendns-filtering.php
- What is DNS Filtering?
How Does DNS Filtering Work?
How is DNS used by Hackers?
All that a hacker does is
Cache Poisoning
In simple, cache poisoning as the term refers to is placing false information into the cache of a server. Hackers accomplish this by assigning a bogus “reply” with a tricked source IP address to an information request.
How long does the cache remain poisoned?
There is a time limit for the DNS information (TTL) to be active and then it requires to
DNS Protection
configure it to be as strong as possible against cache poisoning, the potential ways of doing it includes:
➢ instead of UDP port 53
➢ randomizing the case of the letters of the domain names
➢ randomizing the query ID
➢ maintaining your DNS servers securely
Configuring DNS Filtering
By altering the MX records internally,
https://cdome.comodo.com/blog/what-is-dns-filtering/
- DNS Web Filtering 4 Myths And
Some Truth
DNS filtering provides protection from online threats such as viruses, malware, ransomware, phishing attacks and botnets.
The Domain Name System (DNS) makes it so
Myth 1: We don’t need web filtering, we already have endpoint antivirus
antivirus software can only detect known viruses while it’s running
end users are notorious for turning off antivirus and the local firewall on their computers to avoid sluggish performance or install software
the business is liable for how its network
If an end user is serving up pirated movies from your IP address, can your business afford the fine?
If an employee accidentally gets infected with a
Myth 2:
It starts with DNS lookup in just three steps:
Query: You type a web address into the browser, triggering a DNS query.
Lookup: The DNS server specified in your network interface configuration (usually provided automatically by your DHCP server) receives the request and looks up the IP address relating to that domain.
Response: As long as the domain name exists,
The filter protects your network by only providing lookup requests with a valid IP address for safe websites, but returns a local IP address to deliver a block page for forbidden sites.
DNS logging will show which lookups people have performed, but not which sites they
Myth 3: DNS web filtering is easy to bypass
In most cases
They’ll find a proxy service or change their DNS settings locally on their computer if you haven’t locked it down
No web filtering approach is immune to circumvention
It’s time to roll up your sleeves and set some firewall rules on your Internet gateway/router
You can block DNS requests to anything other than your approved DNS service and block all other DNS requests.
If you use an external DNS server,
If you have your own, locally hosted, internal DNS server,
local computers query your local DNS server, and only your DNS server queries the web filtering DNS service on the Internet.
Myth 4: Configuring DNS filtering is a lot of work
Most routers and firewalls will allow you to block port 53
By editing your internal MX records, a single configuration change in one
Key Benefits of DNS Filtering
Block Malware & Malicious Sites
Control Internet Access
Prevent malware downloads from malicious or hacked websites
Keeps your defense up to date with targeted threat analysis and zero day updates to protect your customers as threats arise.
https://www.titanhq.com/blog/4-myths-about-dns-filtering-and-some-truth
- How to Use OpenDNS on Your Router, PC, Tablet, or Smartphone
Changing Your DNS
You have two configuration options on your home network. You can change the DNS on your router, which is the main connection point to and from the Internet.
This has the advantage of covering everything in an umbrella of protection. This is also its disadvantage because every computer behind the router must then use the same router settings unless you specifically assign a client to use another DNS server.
Another disadvantage is that there’s no way to tell, at least with the free version of OpenDNS, where the traffic is coming from, so if you see a bunch of blocked websites, it could be you, it could be your spouse, it could be your children, or anyone else who comes over and connects to your network.
Preferred Method: Configuring Your Router
Clearing Your DNS Resolver Cache on Windows Clients
“
Clearing Your Browser History
Clearing Internet Explorer’s Cache
Clearing Mozilla Firefox’s Cache
Clearing Google Chrome’s Cache
Alternative Method: Configuring Individual Clients
Changing DNS Servers on Windows Computers
Changing DNS Servers on an Android Device
Changing DNS Servers on an
https://www.howtogeek.com/201312/how-to-use-opendns-on-your-router-pc-tablet-or-smartphone/
- OpenDNS is a free online service that offers an extra layer of safety on the Interne
Technically, the service is DNS resolution
The main defensive computing advantage it provides is protection from bad Web sites
You don't have to register to use the service, and there is no software to download or install.
All that's involved is a change to the networking configuration of either your computer or your router. This is a
Should you ever want to stop using the service
Should you ever want to stop using the service
https://www.cnet.com/news/opendns-provides-added-safety-for-free/
- OpenDNS is a company and service that extends the Domain Name System (DNS) by adding features such as phishing protection and optional content filtering
in addition to its DNS servers are used
The company hosts a cloud computing security product suite, Umbrella, designed to protect enterprise customers from malware, botnets, phishing, and targeted online attacks.
DNS services for personal home use
On May 13, 2007, OpenDNS launched a domain-blocking service to block web sites or non-Web servers visited based upon categories, allowing control over the
In 2008, OpenDNS changed from a closed list of blocked domains to a community-driven list allowing subscribers to suggest sites for blocking; if enough subscribers (the number has not
Other free, built-in features include a phishing filter. OpenDNS also run a service called PhishTank for users to submit and review suspected phishing sites
OpenDNS supports the
https://en.wikipedia.org/wiki/OpenDNS
- Dynamic Domain Name System
DNS is static so the IP address associated with it should be static. If you have a dynamic IP, the computer changes the IP address frequently. So by accessing the Domain Name, you
http://www.techcuriosity.com/tutorials/networking/difference_between_DNS_and_DDNS.php
Dynamic Detection of Malicious DDNS
- In the past, you needed a static IP address, or an IP address that never changed,
in order
http://www.serv-u.com/kb/1408/how-does-dynamic-dns-work
- it can be
quite been received any changes to your IP Address are immediately made
http://whatismyipaddress.com/dynamic-dns
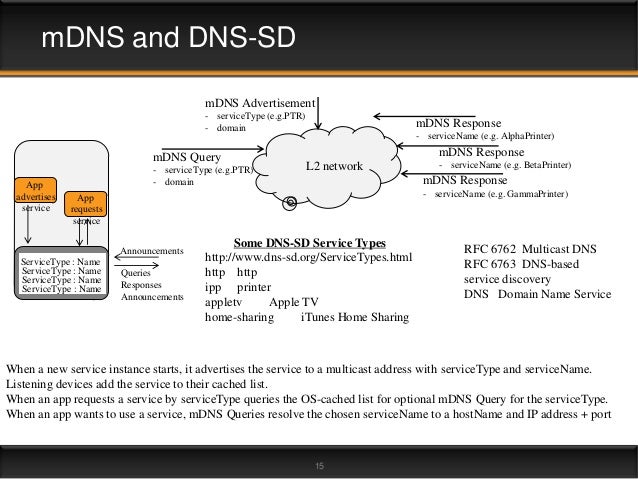
Multicast been installed
http://www.multicastdns.org/
- DNS-SD uses
Multicast multicast mdns quite are designed is kept
Service discovery is a
The second step in service discovery is to resolve the
https://stackoverflow.com/questions/11835782/how-exactly-does-mdns-resolve-addresses
- Bonjour is Apple's implementation of zero-configuration networking (
zeroconf multicast mDNS
https://en.wikipedia.org/wiki/Bonjour_%28software%29
- Zero-configuration networking (
zeroconf are interconnected
https://en.wikipedia.org/wiki/Zero-configuration_networking
- What is a DNS leak and why should I care?
https://dnsleaktest.com/what-is-a-dns-leak.html
- Unfortunately for VPN users, WebRTC allows a website (or other WebRTC service)
to directly detect machine’s
Given that WebRTC is potentially useful, it is something of does allow
The WebRTC issue only affects the Firefox, Chrome, and Opera browsers (not Internet Explorer or Safari etc., as these do not include WebRTC functionality.)
https://www.bestvpn.com/blog/31750/a-complete-guide-to-ip-leaks/
- You might think your anonymity service protects you completely, but don’t get too cocky. If
any trackable data is stored be giving
Just one leak is enough to link you back to your real IP and your real identity.
https://www.doileak.com/
-
What is a "
WebRTC "
Mozilla Firefox: Type "about:config ” . peerconnection .
Google Chrome: Install Google official extension WebRTC
What is a "DNS leaks"?
In this context, with "DNS leak" we mean an unencrypted
Why my system suffers DNS leaks?
In brief: Windows lacks the concept of global DNS. Each network interface can have its own DNS. Under various circumstances, the system process svchost
Should I be worried
If you don't want that your ISP, and anybody with the ability to monitor your line, knows the names your system tries to resolve (so the web sites that you're living in a human rights hostile country, or in any way the above mentioned you should
How Does Torrent Detection Work?
To detect data from your torrent client an http url tracker
https://ipleak.net/
WebRTC
https://en.wikipedia.org/wiki/WebRTC
- One of the primary reasons to use a VPN is to hide your true IP address. When using a VPN, all your internet traffic
is encrypted . provider
https://www.bestvpn.com/blog/31750/a-complete-guide-to-ip-leaks/
WebRTC
To enable rich be developed
http://www.webrtc.org/
- DNS spoofing
DNS spoofing (or DNS cache poisoning) is a computer hacking attack, whereby data is introduced
DNS is a hierarchical naming system built on a distributed database for resources connected to the Internet.
DNS maps domain names to their corresponding Internet Protocol (IP) addresse
DNS has no authentication mechanisms included by default
The lack of authentication increases the risk of falsified DNSinformation
DNS spoofing and DNS cache poisoning can permit an adversary to map the internal network of an organisation based on queries from the internal DNS Resolver to upstream DNS Resolvers. DNS cache poisoning can subvert client connections to provide false information, facilitating installation of malicious code or the extraction of sensitive information
DNS Resolvers are typically configured
Entries will remain in a DNS Resolver’s cache depending on the time to live (TTL) value in the returned record.
DNS spoofing
DNS cache poisoning
DNS cache poisoning with flooding
Mitigation strategies
Separate authoritative and recursive DNS Resolvers
Limit zone transfers
Randomise source ports and transaction IdentifiersDNS are used . more specifically,
https://www.cyber.gov.au/sites/default/files/2019-05/PROTECT%20-%20Domain%20Name%20System%20Security%20%28April%202019%29.pdf
- Firewalls
Let's begin at the most prevalent security system: your firewall. All firewalls should let you define rules to prevent IP spoofing. Include a rule to deny DNS queries from IP addresses outside your allocated numbers space to prevent your name resolver from being exploited as an open reflector in DDoS
Enable inspection of DNS traffic for suspicious byte block
Intrusion detection systems
Whether you use Snort, Suricata, or OSSEC, you can compose rules to report DNS requests from unauthorized clients. You can also compose rules to count or report NXDOMAIN responses, responses containing resource records with short TTLs, DNS queries made using TCP, DNS queries to nonstandard ports, suspiciously large DNS responses
Traffic analyzers
Capture and filter DNS traffic between your clients and your resolver,
Passive DNS replication
This involves using sensors at resolvers to create a database that contains every DNS transaction (query/response) through a given be instrumental in identifying in cases
Logging at your resolver
The logs of your local resolvers are a last and perhaps most obvious data source for investigating DNS traffic
https://www.darkreading.com/analytics/threat-intelligence/5-ways-to-monitor-dns-traffic-for-security-threats/a/d-id/1315868
- A logical next step towards a new, more secure Internet is to remove any central points of trust from the core of the Internet. Following the trust-to-trust principle, DNS and PKI functionality for end-hosts should exist near the edges of the network and not in the core.
Let’s imagine a server that provides DNS and PKI functionality and runs in a (local) network you trust. This server needs two things:
Decentralized Consensus: Ability to reach consensus
Tamper Proofing: Mechanism to ensure that data records in the DNS and PKI system cannot be easily tampered
Blockchains are great at providing both these properties; nodes can independently reach consensus and tampering with data records requires an enormous amount of compute blockchains have been used to implement decentralized DNS and PKI systems
https://medium.com/@muneeb/next-steps-towards-a-secure-internet-a057217acebb
- The hosts file is like your speed dial directory for the internet.
Where is the hosts file located?
The hosts file does not have an extension, but it can be viewed
Before resolving an internet request (to look up the IP that belongs to a domain name), Windows looks in the hosts file to see if there is a predefined
These predefined
Blocking: some people (who are oftentimes be installed
Pointing: for example, system administrators use the hosts file to map intranet addresses.
Malware uses it for their own reasons, where the two most common ones are:
To block detection by security software: for example, by blocking the traffic to all the download or update servers of the most well-known security vendors.
To redirect traffic to servers of their choice: for example, by intercepting traffic to advertisement servers and replacing the advertisements with their own.
https://blog.malwarebytes.com/cybercrime/2016/09/hosts-file-hijacks/
What is a HOSTS file?
Each time you try to connect to internet computer This is usually done computer Simply put , the
connectivity and speed, as these addresses are kept
For example, you have the BBC website cached in your HOSTS file: its entry would be displayed . bbc . . uk .
load faster than websites that are not cached
That said ( )
https://www.2-viruses.com/blocking-spyware-using-the-hosts-file
- There is another way to resolve domain names without using the Domain Name System, and that is by using your HOSTS file. Almost every operating system that communicates via TCP/IP, the standard of communication on the Internet, has a file called the HOSTS file. This file allows you to create mappings between domain names and IP addresses.
The HOSTS file is a text file that contains IP addresses separated by at least once space and then a domain name, with each entry on its own line. For example, imaging that we wanted to make it so that if you typed in www. . In order to .
One of the IP addresses for Yahoo is 216.109.118.69. If we wanted to map Google to that IP address we would add an entry into our HOSTS file as follows
216.109.118.69 www.
Network Testing - I manage a large Internet Data center and many times we need to set up test machines or set up development servers for our customers applications. When connecting to these development that you had a domain name for a development computer called development. mydomain . mydomain . mydomain . mydomain that you will be testing . mydomain modified really that are using . mydomain
https://www.bleepingcomputer.com/tutorials/hosts-files-explained/
- 7 Ways to Use Hosts File on Your Computer
1. Editing Hosts File to Block a website
To block any site from hosts file, you only need to map the hostname to the localhost
For instance, to block users from access Twitter, add one of the following entries at the end of the hosts file:
127.0.0.1 twitter.com www.
0.0.0.0 twitter.com www.
2. Re-directing a Website Using Hosts File
You can also redirect the website to a particular domain. For example, you may edit the hosts file such that whenever a user tries to access Twitter, they are redirected
First, you need to know the IP for your target website.
Then use the hosts file to map the IP to Twitter.com. To redirect Twitter to Google.com IP address 216.58.223.110, enter “216.58.223.110 www.
3. Create Shortcuts for Websites or Intranet Services
You can also modify
For instance, if you have a server with an IP, 192.168.1.10 on your network, it will be easier to remember a descriptive name than the IP address.
To create a shortcut for the device, you only need to map its IP to your preferred name with a .com extension.
Add “192.168.1.10 mydevice ”
4. Testing Network / Web Servers
When you are running a web development server on your local network, it will be safe to test its functionality before publishing it live.
For instance, if you are running a web server (IP: 192.168.0.11), hosting two sites mysite1.com and mysite2.com, you can add the following entries to the hosts file:
192.168.0.11 mysite1.com
192.168.0.11 mysite2.com
5. Content Filtering and Ads Blocking
You can block Ad networks or unwanted sites by mapping the site to the localhost
This will point back to your own PC blocking access to known malicious or Ads sites.
6. Adding Websites to Hosts File to Improve Browsing Speed
Add a site to the hosts file can increase the browsing speed. This is simply doesn’t need to
7. Preventing Malicious Attacks
You can prevent such unauthorized edits by changing the properties for the “hosts” file.
Under the “General” tab, tick the “Read-only” checkbox to disable editing.
https://www.webnots.com/7-ways-to-use-hosts-file-on-your-computer/
Subdomain Records
- Learning About DNS Record Types
Name Servers
When you bought your domain name, your registrar probably configured default DNS records for you and provided the Name Servers (NS) for them. You need to have a Name Server (which are often mirrored in pairs and triplets for redundancy, e.g. ns1. yourregistrarserver .com, ns2. yourregistrarserver .com) to tell the Internet's DNS directory the numeric IP addresses of your web servers and services.
A Records
If a web user types in jeffreifman .com, the request will be passed off to a directory which will look for a DNS record that corresponds to my root domain. By root, I mean no prefix, no www, i.e. no sub-domain, just http://jeffreifman.com. For example, the root-level A record of your domain might point to 107.164.32.96. That will tell the Internet to which IP address to send your browsing request.
You can also configure A records for a variety of sub-domains. For example, if you want www. yourwebsite .com to go to the same address, you can set up an identical A record for the sub-domain www, i.e. the root domain, and the www domain would have identical IP addresses.
Wildcard Entries
DNS records also allow wildcard entries (using an asterisk *) that make it easy to route all sub-domain traffic to one IP address.
Inbound Routing on Your Server
When traffic arrives at your server from the DNS mapping system, how your server handles it must be configured there
CNAME Records
CNAMEs are essentially domain and sub-domain text aliases to map traffic to. For example, if you've ever set up a blog through a service such as WordPress or Tumblr, they may ask you to map your domain name to a CNAME rather than with an A record to an IP address
MX Records
MX records tell the DNS system where to send all that email you receive.
Changing Email Providers and Moving Email
MX records only instruct the DNS system where to route today's email—your existing email is stored in the cloud databases of your current email provider. If you wish to move all of your existing messages, you'll need to rely on their tools or your mail client software. And, of course, you'll also have to update your MX records to your new provider's settings.
TXT Records
TXT records allow the domain owner to authenticate themselves by posting secret codes within their DNS. When you register with Google Webmaster Tools, it will ask you to verify that you own the domain by doing just that.
AAAA Records
If you decide to support IPv6 addressing, you'll need to configure an AAAA record with its larger addressing scheme:
https://code.tutsplus.com/tutorials/an-introduction-to-learning-and-using-dns-records--cms-24704
Cisco Umbrella Malware and Content Filtering through DNS. ... Cisco Umbrella offers security protection for both Home and Enterprise users through filtering DNS requests. The job of the DNS servers are to translate website URLs to their respective IP address.
The company hosts a cloud computing security product suite, Umbrella, designed to protect enterprise customers from malware, botnets, phishing, and targeted online attacks. The OpenDNS Global Network processesan estimated 100 billion DNS queries daily from 85 million users through 25 data centers worldwide.
The company hosts a cloud computing security product suite, Umbrella, designed to protect enterprise customers from malware, botnets, phishing, and targeted online attacks. The OpenDNS Global Network processesan estimated 100 billion DNS queries daily from 85 million users through 25 data centers worldwide.
Google also has a public DNS (8.8.8.8 and 8.8.4.4 forIPv4 service, and 2001:4860:4860::8888 and 2001:4860:4860::8844 for IPv6 access), but Cloudflare is faster than Google, and faster than OpenDNS (part of Cisco) and Quad9.
- What is Cisco umbrella DNS?
Cisco Umbrella Malware and Content Filtering through DNS. ... Cisco Umbrella offers security protection for both Home and Enterprise users through filtering DNS requests. The job of the DNS servers are to translate website URLs to their respective IP address.
The company hosts a cloud computing security product suite, Umbrella, designed to protect enterprise customers from malware, botnets, phishing, and targeted online attacks. The OpenDNS Global Network processes
- What is umbrella OpenDNS?
The company hosts a cloud computing security product suite, Umbrella, designed to protect enterprise customers from malware, botnets, phishing, and targeted online attacks. The OpenDNS Global Network processes
- Which is better OpenDNS or Google DNS?
Google also has a public DNS (8.8.8.8 and 8.8.4.4 for
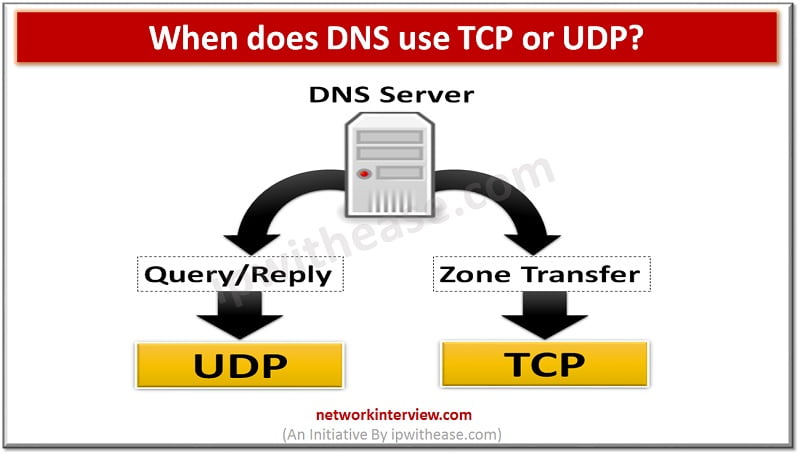
- DNS or other Services works on both TCP and UDP
Two protocols are different from each other. TCP is a connection-oriented protocol and it requires data to be consistent at the destination and UDP is connection-less protocol and doesn't require data to be consistent or don't need a connection to be established with host for consistency of data.
UDP packets are smaller in size. UDP packets can't be greater than 512 bytes. So any application needs data to be transferred greater than 512 bytes require TCP in place. For example, DNS uses both TCP and UDP for valid reasons described below. UDP messages aren't larger than 512 Bytes and are truncated when greater than this size. DNS uses TCP for Zone transfer and UDP for name, and queries either regular (primary) or reverse. UDP can be used to exchange small information whereas TCP must be used to exchange information larger than 512 bytes. If a client doesn't get response from DNS, it must retransmit the data using TCP after 3-5 seconds of interval.
There should be consistency in DNS Zone database. To make this, DNS always transfers Zone data using TCP because TCP is reliable and make sure zone data is consistent by transferring the full zone to other DNS servers who has requested the data.
https://docs.microsoft.com/en-us/troubleshoot/windows-server/networking/dns-works-on-tcp-and-udp





.jpg)