- Security Automation and Orchestration (SOAR)
https://www.cyberbit.com/solutions/security-operations-automation-orchestration/
- The Evolution of SOAR Platforms
https://www.securityweek.com/evolution-soar-platforms
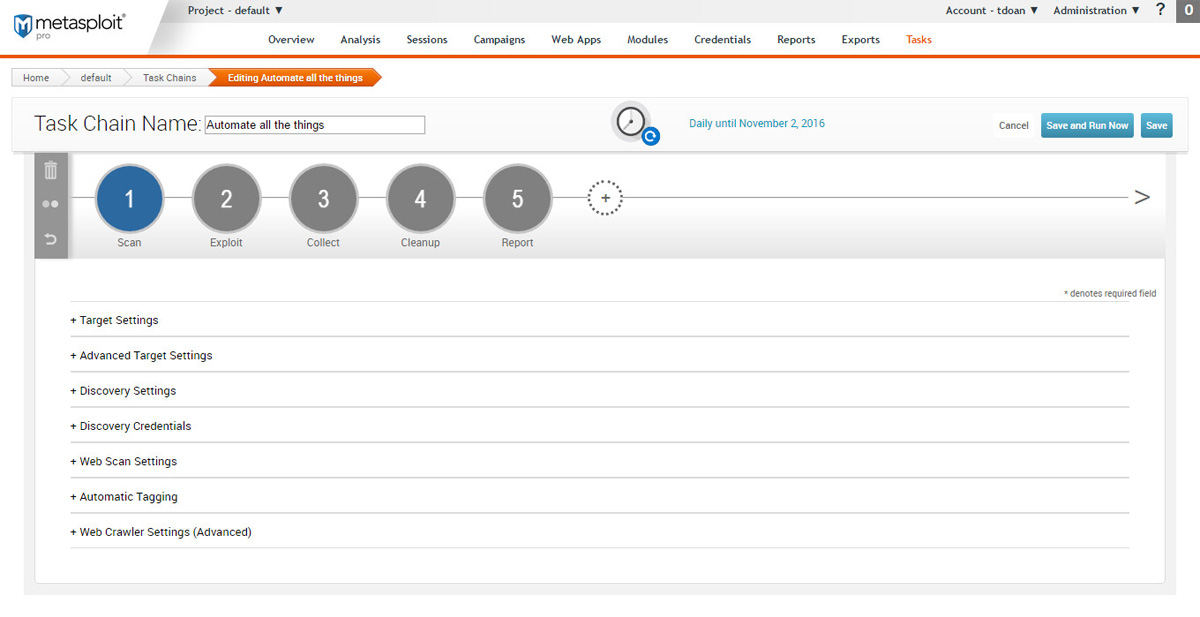
- How to build an incident response playbook
Here are the steps the IACD recommends following to construct an incident response playbook:
Identify the
List all
Categorize all
Build the playbook process order using only the “required” elements determined in step 3.
Determine
Insert the categorized optional actions into the options box below the process steps box.
Identify the end state or another
List the regulatory laws and requirements that the playbook satisfies.
https://swimlane.com/blog/incident-response-playbook/
Incident Response Playbook Example
Intelligently Automate Incident Response
- Automated Website Unblock Requests
Another good example of an automation worthy processes is website unblock requests. Many organizations use a web proxy to block unwanted and/or malicious web traffic. Sometimes these proxies block sites necessary for employees to do their job, so the employees have
https://www.splunk.com/blog/2017/11/02/playbooks-going-beyond-incident-response-use-cases.html
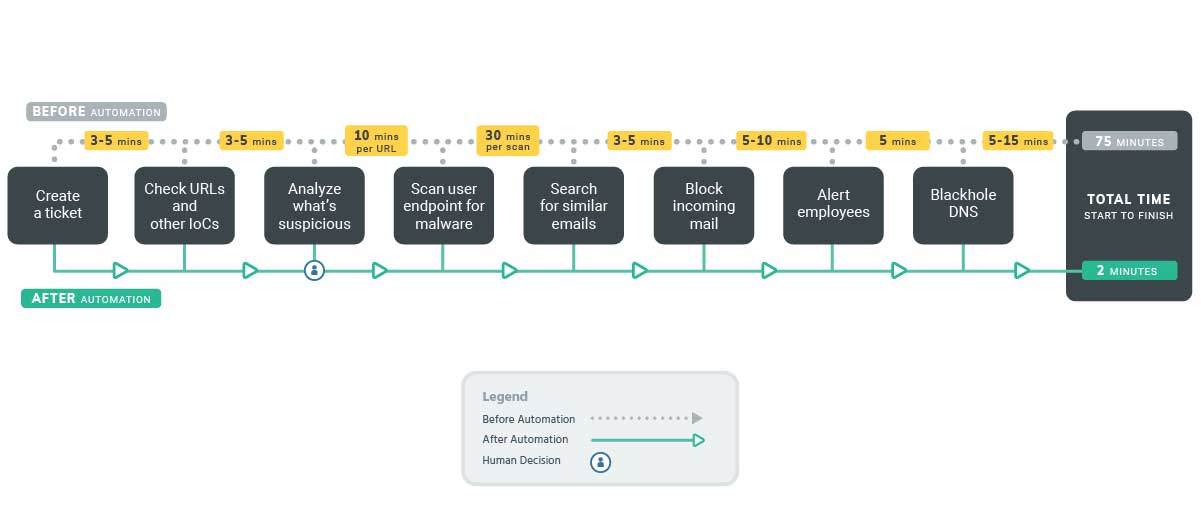
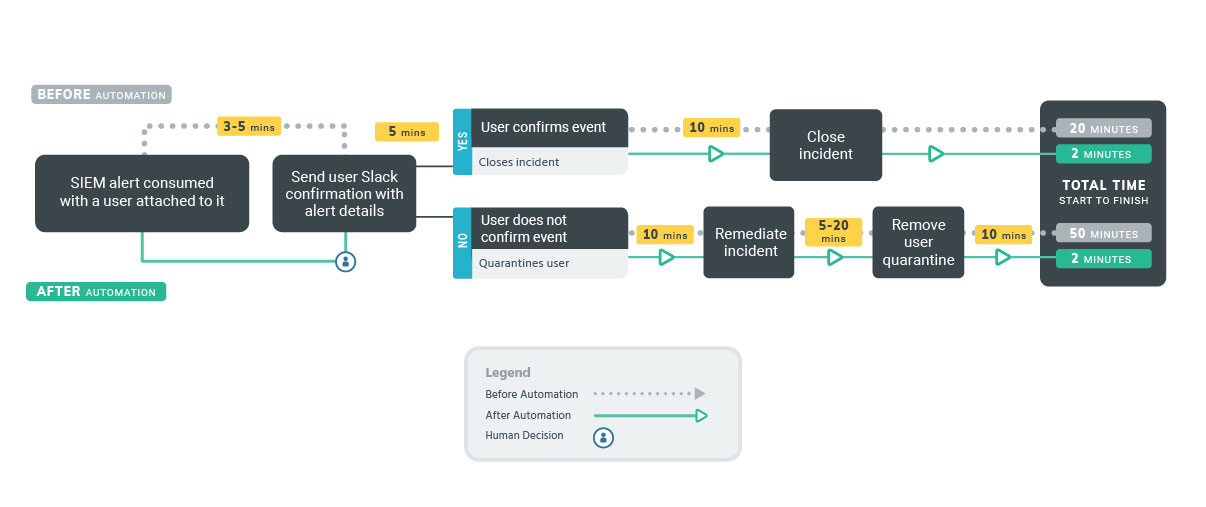
- Phishing remains the most common attack vector behind successful breaches. However, investigating phishing emails involves time-consuming, manual tasks such as investigating and detonating attachments, checking URLs, or following up on suspicious requests for sensitive information. Orchestration and automation solutions can execute tasks like these behind the scenes while your team works on the rest of your investigation and response, ensuring the situation
is handled accelerating for is identified
Scan attachments and URLs
Use plugins for safe browsing, sandboxes, and more to contain and investigate suspicious attachments and check suspicious URLs.
Workflows to identify threats
Leverage workflows to analyze email URLs and file attachments using multiple intelligence sources. Add steps to output reports detailing each indicator identified.
Designate decision points
After the routine scans and investigations have occurred, configure workflows to trigger a decision point on how best to proceed. Examples include marking as verified phish, automatically posting a message alerting others in your organization to the phishing threat via Slack, and other actions.
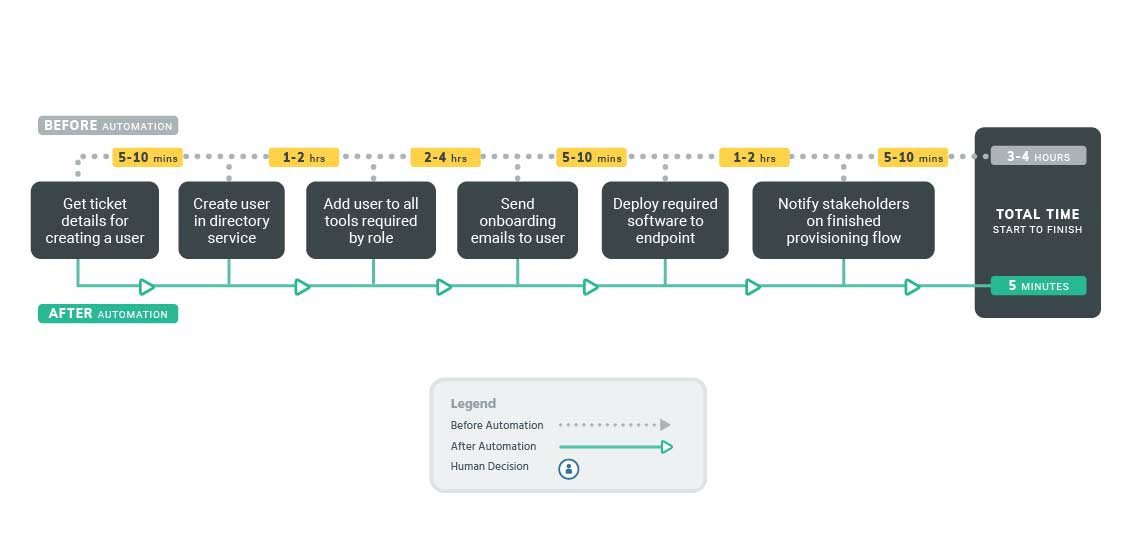
Provisioning new accounts
Different employees require different access levels to various tools and systems within your organization. Easily orchestrate tools such as Okta or Active Directory together,
No matter the reason why
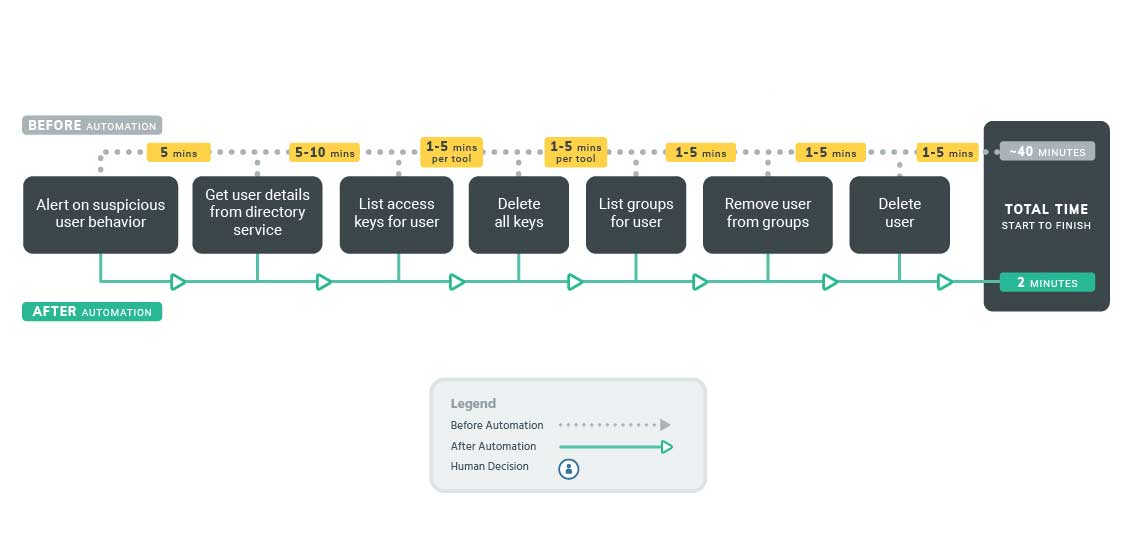
Shutting the [access] doors
User accounts are commonly exploited In the event deprovision the threat is contained
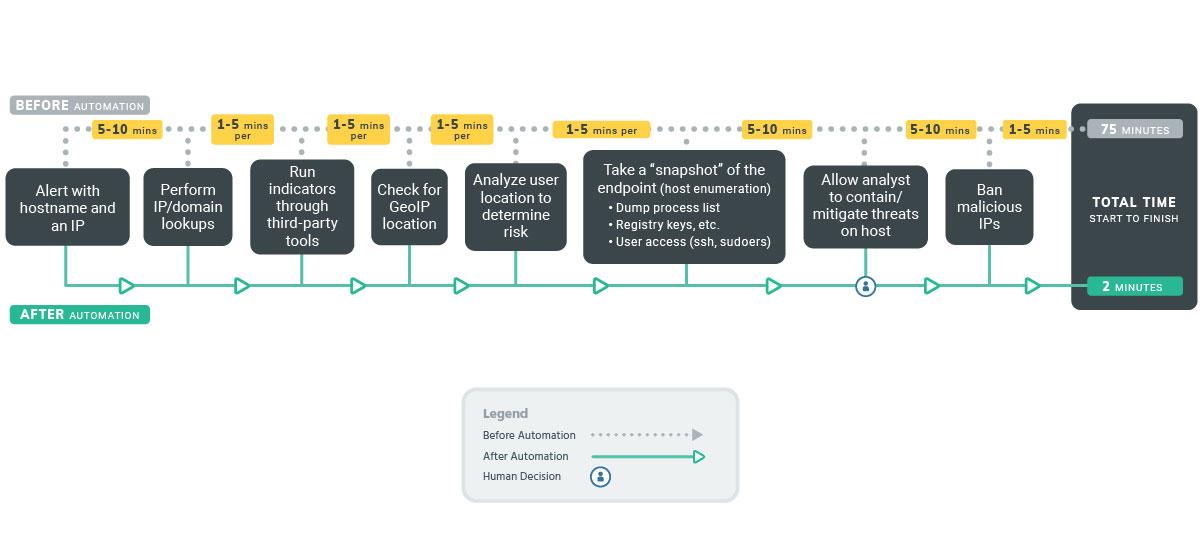
Identify malicious activity
When dealing with malware in a timely manner
Investigate the threat
When malware is detected
Containment and removal
All malware will require some type of necessary
Alert Enrichment
Leave the heavy-lifting to the machines
Reduce the noise
Alert Enrichment
Leave the heavy-lifting to the machines
Reduce the noise
Teams are always striving to reduce the time between security alert generation and resolution to a theoretical null. First popularized by the security team at Slack, a Distributed Alerting strategy avoids alert fatigue and staffing issues in the SOC by immediately bringing up alerts into the Slack instance of the person who generated it. Augmented with multi-factor authentication (MFA), analysts spend less time dealing triaging due to
Streamline business operations
Trigger actions to push comments to solutions like JIRA or Slack. With your security ecosystem set up to deliver alerts,incident
Two-way flow of information
Automation can deliver alerts that come in from your security tools straight into your chat applications and delegate tasks back to other connected tools, making communication and case management bi-directional.
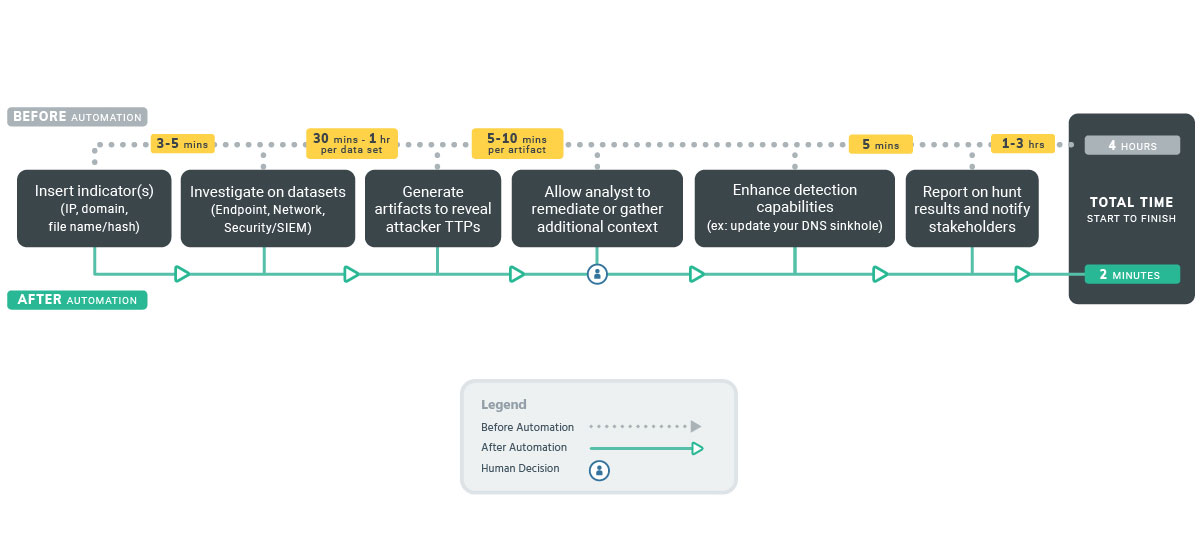
Threat Hunting
being proactive in this area can enable your analysts to better uncover and defend against complex advanced persistent threats (APTs)—the attacks that are almost guaranteed
The more data sets you are able to
Automate repeatable tasks
By automating the ongoing tasks associated with threat hunting, such as recurring scans, your team will have more time to do what they do bes
Notify and respond faster
Create and kick off designated response workflows based on the type of
Monitor advisory lists
Coordinating vendor vulnerability response used to be a manual process requiring multiple stakeholders. With an automation solution, you can build workflows to automatically monitor
Notify stakeholders
When a vulnerability needs to be addressed
https://www.rapid7.com/info/security-orchestration-and-automation-playbook/
Sample Workflow
Phishing Investigations
Sample Workflows
Provisioning Users
Sample Workflows
Sample Workflow
Alert Enrichment
Sample Workflow
Sample Workflow
Threat Hunting
Sample Workflow
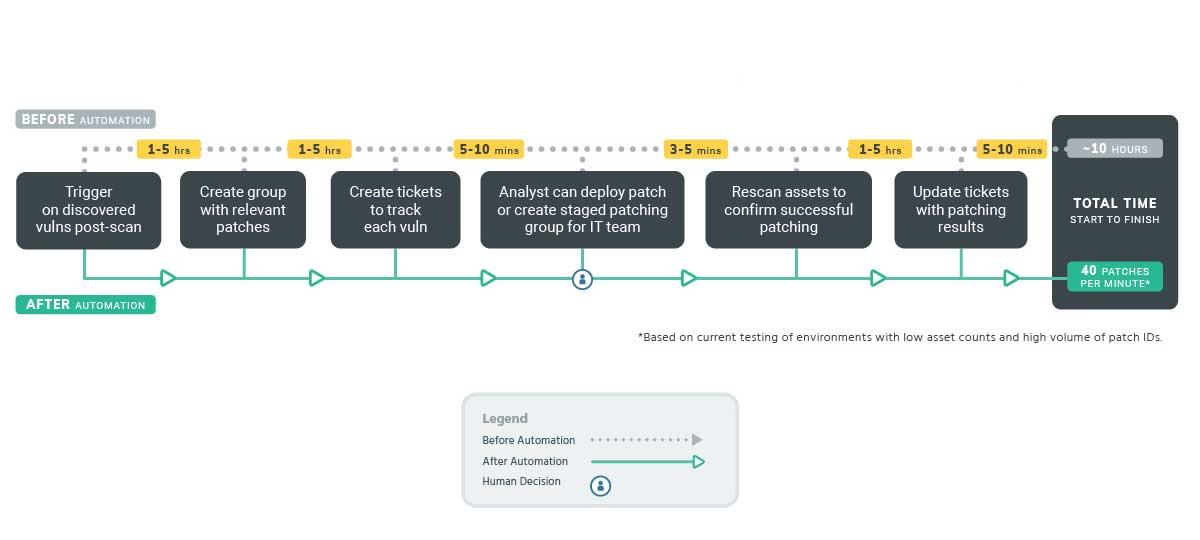
Patching and Remediation
The BigFix solution comprises several application products that provide consolidated
Built-in remediation processes through Microsoft Intune
Verify remediation – your host has been patched
Automate mundane, manual functions to free up IT and security teams to address critical issues. By leveraging ServiceWatch are created
- the Splunk Phantom platform creates a complete picture of an incident, moving through Orient and Decide with crafted
playbo
https://web.tufin.com/hubfs/partners/Splunk-TAP-partner-brief.pdf
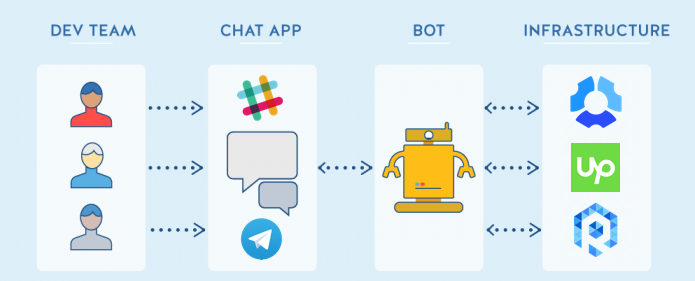
- What is
C hatOps ? Conversations, put to work
They also replaced repetitive tasks with
And they pulled it all together into a central tool like
These rooms are replacing email threads and meetings and are
As the members of a chat room perform their work, pull, share, or display information, others
Technical teams have
https://www.atlassian.com/blog/software-teams/what-is-chatops-adoption-guide?_ga=2.254598990.775318353.1497538188-1315074878.1497538188
How ChatOps Can Help You DevOps Better
- ServiceNow versus Splunk/Phantom for automation
Phantom is on prem ,
https://medium.com/@IrekRomaniuk/servicenow-versus-splunk-phantom-for-automation-ad7bfe4e8cfa
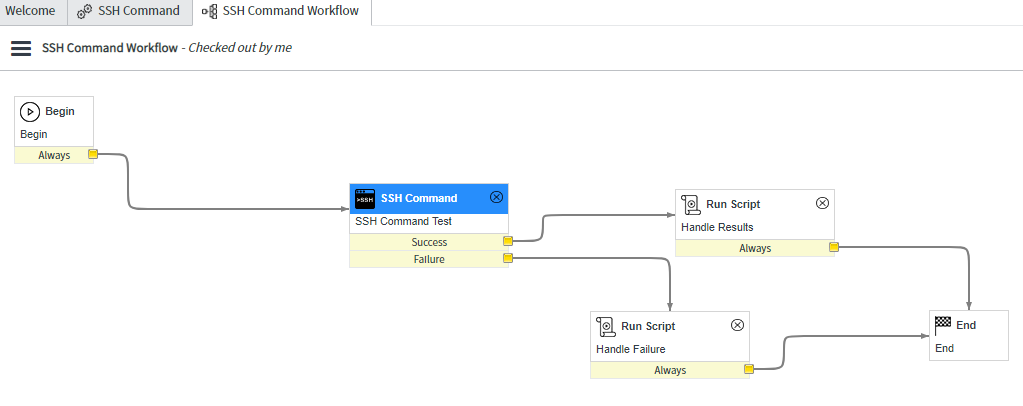
SSH command workflow in ServiceNow
Playbook running ssh command on remote
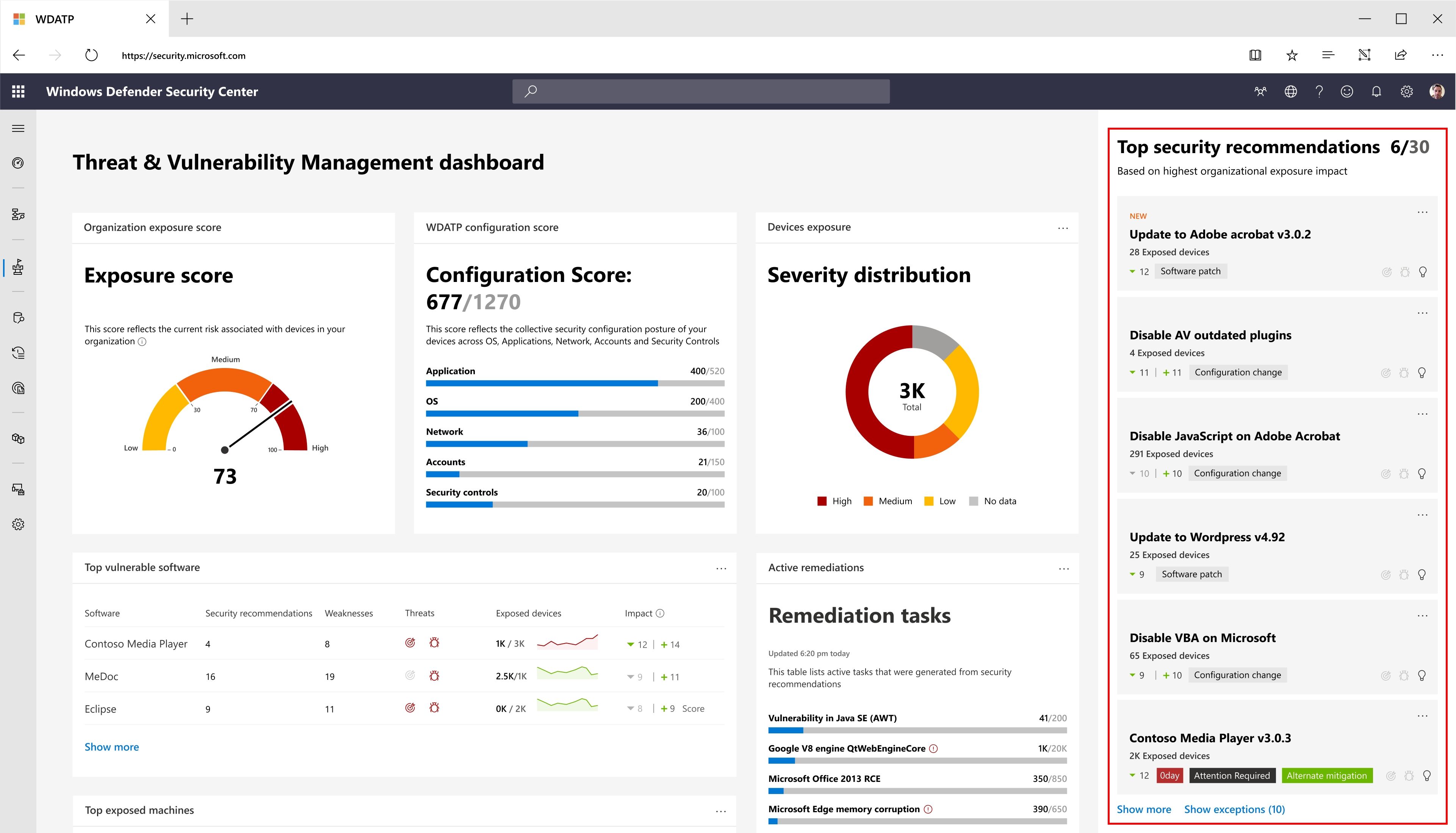
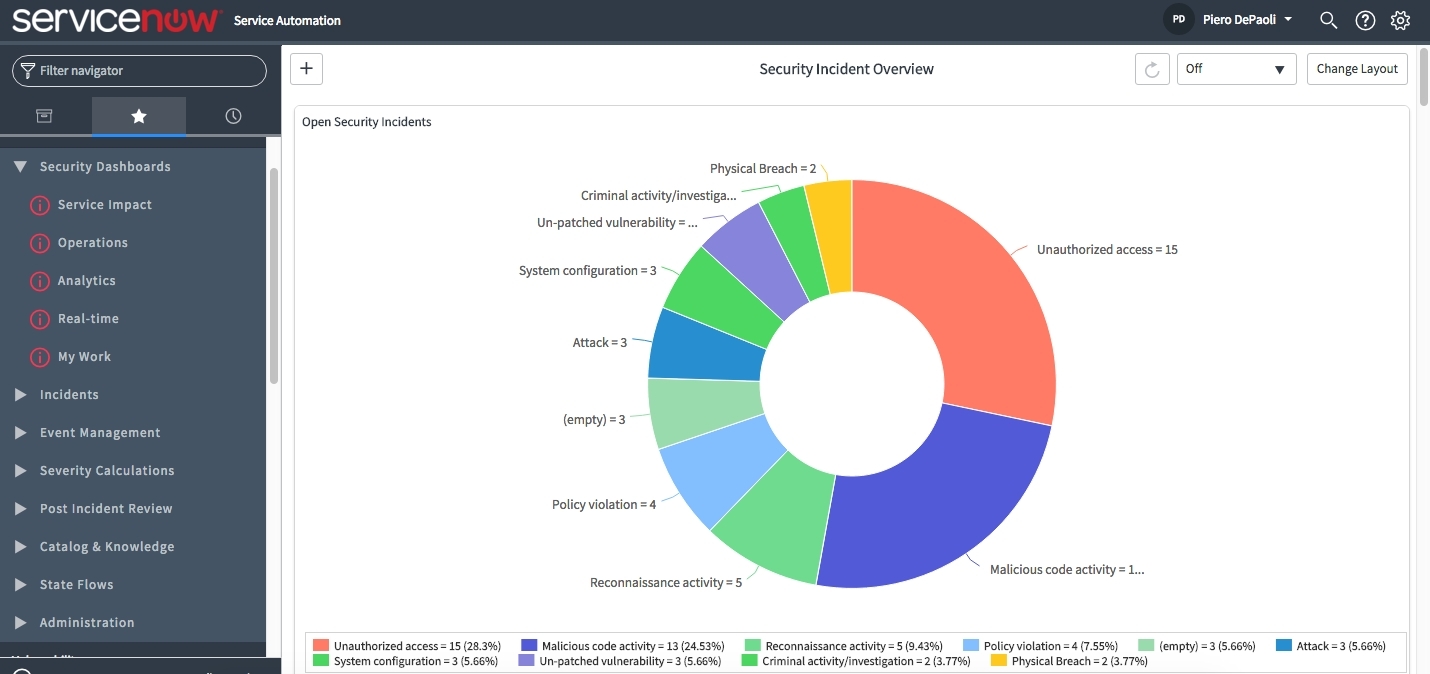
- What is SIEM? What is SOAR? How are they different?
What is SIEM?
Firewalls, network appliances and intrusion detection systems generate an immense amount of event-related data—more data than security teams can reasonably expect to interpret.
So why isn’t
It usually needs regular tuning
What is SOAR?
Like SIEM,
OAR takes things a step further by combining comprehensive data gathering, case management, standardization, workflow and analytics to provide organizations the ability to implement sophisticated defense-in-depth capabilities.
SOAR solutions include multiple playbooks in response to specific threats: Each step in a playbook can
Using SIEM and SOAR for improved
https://swimlane.com/blog/siem-soar/
What is SOAR? SOAR connects all of the other tools in your security stack together into defined
workflows, which can be run automatically. In other words, SOAR lets you increase your team's
efficiency by Automating repetitive manual processes
https://training.fortinet.com/pluginfile.php/1625390/mod_scorm/content/1/story_content/external_files/NSE%202%20SOAR%20Script_EN.pdf