ssl
Since your certificate grade is public knowledge and is easily determined SSLLabs
https://www.ssllabs.com/
compliance testing output for PCI/HIPAA/NIST
https://www.immuniweb.com/ssl/
- Verify your SSL, TLS & Ciphers implementation.
Having misconfigured
- Check if your SSL Certificate
is installed
https://www.thesslstore.com/ssltools/ssl-checker.php
- SSL/TLS Vulnerability &
Configuration Scanner
Check the supported protocol, server preferences,
certificate details, common vulnerabilities and more
TLS Scanner –
https://gf.dev/tls-scanner
- TLS Test
– which TLS protocol version is supported is capable of testing
Check TLS Version
Test supported TLS version on the site
https://gf.dev/tls-test
- Test an SSL Web Server
https://www.wormly.com/test_ssl
- SSL Certificate Checker
https://www.digicert.com/help/
- The Mozilla Observatory has helped over 170,000 websites by teaching developers, system administrators, and security professionals how to configure their sites safely and securely.
https://observatory.mozilla.org/
- Let’s Encrypt is an open certificate authority that allows you
to easily create
Let’s Encrypt is a free, automated, and open Certificate Authority.
https://letsencrypt.org/
HTTP Public Key Pinning, or HPKP, has sure had an interesting journey as a standard but today marks what will probably be the final blow for the dying mechanism. Chrome has announced their plans to deprecate and remove support for HPKP as soon as 29th May 2018.
What is HPKP?
This document defines a new HTTP header that allows web host operators to instruct user agents to remember ("pin") the hosts' cryptographic identities overa period of effectively due to
https://scotthelme.co.uk/the-death-knell-for-hpkp/
Sadly be accidentally deleted have the ability to
I also crawl the Alexa Top 1 Million sites every day and oneof the things
https://scotthelme.co.uk/im-giving-up-on-hpkp/
Smashing Magazine used to send an HTTP header with each response that looked like this:
Public-Key-Pins:
pin-sha256="8RoC2kEF47SCVwX8Er+UBJ44pDfDZY6Ku5mm9bSXT3o="
pin-sha256="78j8kS82YGC1jbX4Qeavl9ps+ZCzb132wCvAY7AxTMw="
pin-sha256="GQGOWh/khWzFKzDO9wUVtRkHO7BJjPfzd0UVDhF+LxM "
max includeSubDomains
In theory, this header can be a strong weapon against the threat of “Man in the middle attacks.” These are attacks where someone would impersonate Smashing Magazine with a false certificate somehow generated via a Certificate Authority that your browser already trusts.
The key pinning header above tells browsers to refuse to accept any certificate that hasn’tbeen signed indicated . smashingmagazine subdomains
Key pinning protects against a relatively rare attack that’s very hard to pull off and that’s not a major threat scenario against a content-driven websitelike
For Smashing Magazine this happened when they were updating their expiring SSL certificate. They created a new wildcard certificate, added the digest of the new private key to the Public-Key-Pins header
The old header had told visitors to Smashing Magazine that their browser shouldnever accept any wasn’t listed
all previous visitors with a browser that had pinned the old certificatewere now completely unable to
Even worse, this could notsimply be rolled
If you really think you needpublic
https://www.smashingmagazine.com/be-afraid-of-public-key-pinning/
To ensure the authenticity of a server's public key used in TLS sessions, this public keyis wrapped a X is usually signed is able to
HPKP is a Trust on First Use (TOFU) technique. The first time a web server tells a client via a special HTTP header which public keys belong to it, the client stores this information for agiven period of time whose fingerprint is already known
Firefox and Chrome disable pin validation for pinned hosts whose validated certificate chainterminates all pinning violations are ignored
Enabling HPKP
First you need to extract the public key information from your certificate or key file and encode them using Base64.
Setting up yourwebserver
Apache
Nginx
Lighttpd
IIS
https://developer.mozilla.org/en-US/docs/Web/HTTP/Public_Key_Pinning
- The death knell for HPKP?
HTTP Public Key Pinning, or HPKP, has sure had an interesting journey as a standard but today marks what will probably be the final blow for the dying mechanism. Chrome has announced their plans to deprecate and remove support for HPKP as soon as 29th May 2018.
What is HPKP?
This document defines a new HTTP header that allows web host operators to instruct user agents to remember ("pin") the hosts' cryptographic identities over
https://scotthelme.co.uk/the-death-knell-for-hpkp/
- HPKP Suicide
I also crawl the Alexa Top 1 Million sites every day and one
https://scotthelme.co.uk/im-giving-up-on-hpkp/
Smashing Magazine used to send an HTTP header with each response that looked like this:
Public-Key-Pins:
pin-sha256="8RoC2kEF47SCVwX8Er+UBJ44pDfDZY6Ku5mm9bSXT3o=
pin-sha256="78j8kS82YGC1jbX4Qeavl9ps+ZCzb132wCvAY7AxTMw=
pin-sha256="GQGOWh/
In theory, this header can be a strong weapon against the threat of “Man in the middle attacks.” These are attacks where someone would impersonate Smashing Magazine with a false certificate somehow generated via a Certificate Authority that your browser already trusts.
The key pinning header above tells browsers to refuse to accept any certificate that hasn’t
Key pinning protects against a relatively rare attack that’s very hard to pull off and that’s not a major threat scenario against a content-driven website
For Smashing Magazine this happened when they were updating their expiring SSL certificate. They created a new wildcard certificate, added the digest of the new private key to the Public-Key-Pins header
The old header had told visitors to Smashing Magazine that their browser should
all previous visitors with a browser that had pinned the old certificate
Even worse, this could not
If you really think you need
https://www.smashingmagazine.com/be-afraid-of-public-key-pinning/
- HTTP Public Key Pinning (HPKP) is a security feature that tells a web client to associate a specific cryptographic public key with a certain web server to decrease the risk of MITM attacks with forged certificates.
To ensure the authenticity of a server's public key used in TLS sessions, this public key
HPKP is a Trust on First Use (TOFU) technique. The first time a web server tells a client via a special HTTP header which public keys belong to it, the client stores this information for a
Firefox and Chrome disable pin validation for pinned hosts whose validated certificate chain
Enabling HPKP
First you need to extract the public key information from your certificate or key file and encode them using Base64.
Setting up your
Apache
Nginx
Lighttpd
IIS
https://developer.mozilla.org/en-US/docs/Web/HTTP/Public_Key_Pinning
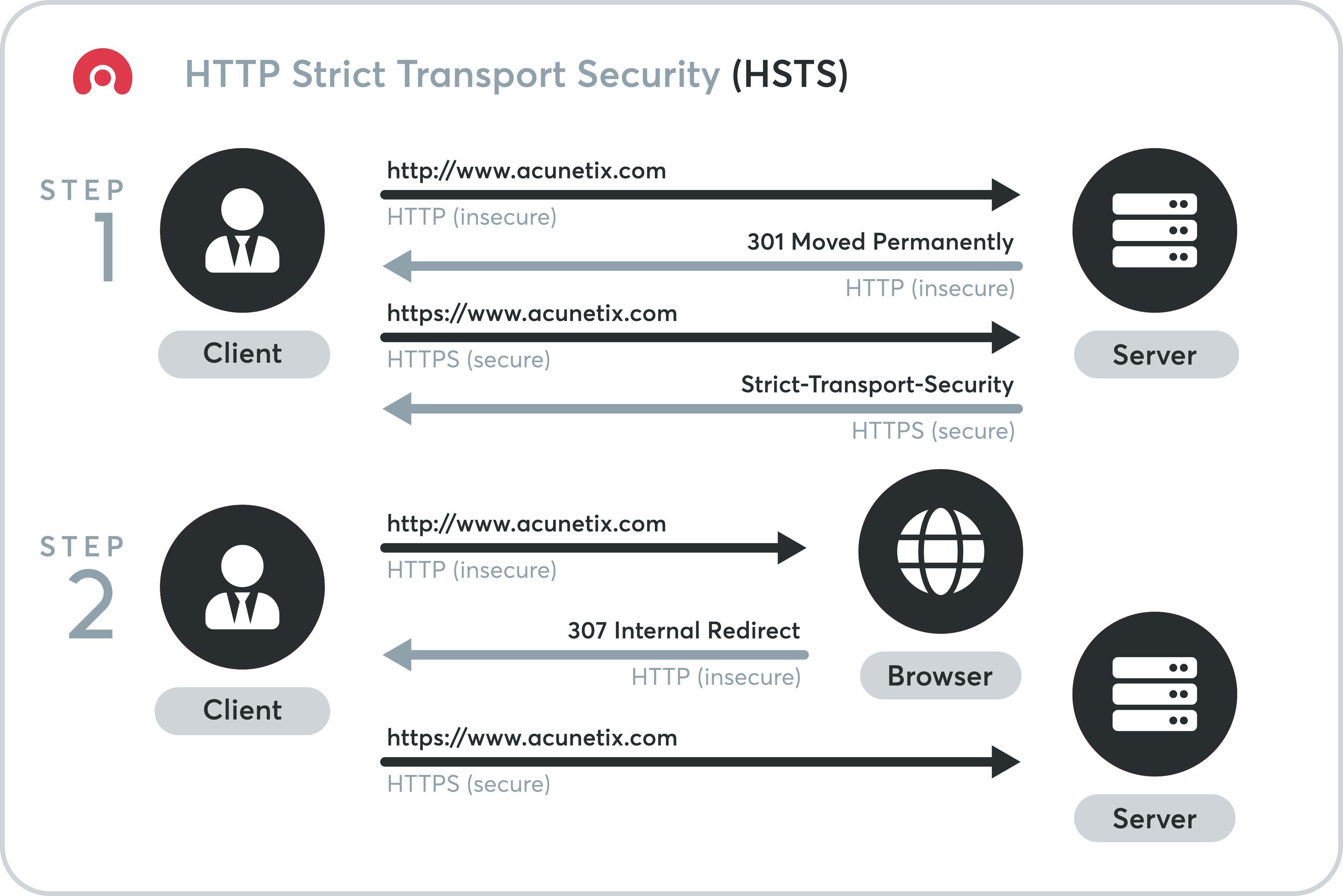
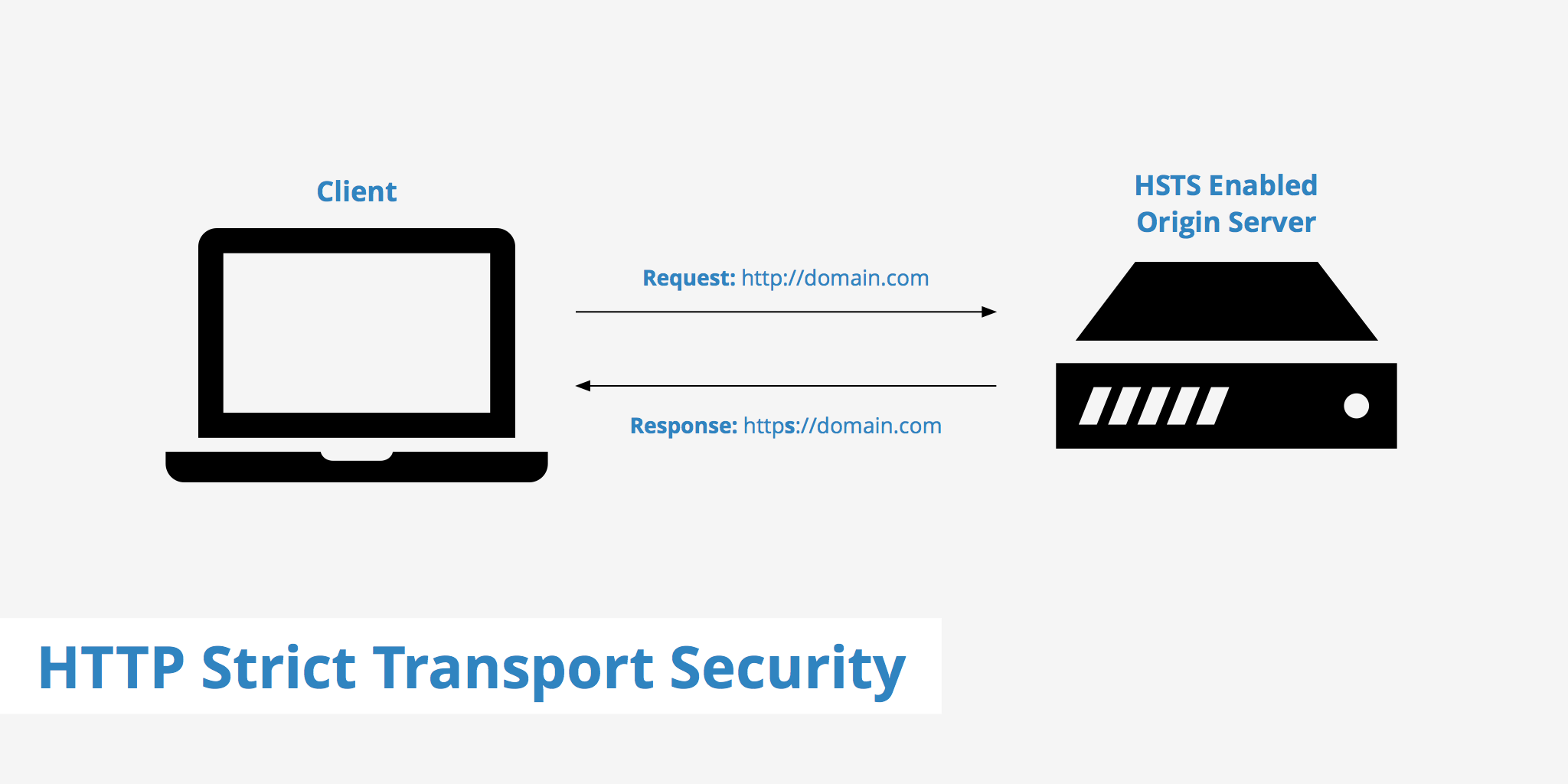
- What is HSTS?
HTTPS (HTTP encrypted with SSL or TLS) is an essential part of the measures to secure traffic to a website, making it very difficult for an attacker to intercept, modify , or fake traffic between a user and the website.
When a user enters a web domain manually (providing the domain name without the http:// or https is sent unencrypted an HTTPS well‑placed man‑in‑the‑middle
HSTS seeks to deal with the potential vulnerability by instructing the browser that a domain can only be accessed
https://www.nginx.com/blog/http-strict-transport-security-hsts-and-nginx/
- Whenever a website connects through HTTP and then redirects to HTTPS, an opportunity for a man-in-the-middle attack is created and the redirect can lead the users to a malicious website because users first have to communicate with the non-encrypted version of the website
A server implements the HSTS policy by supplying a header over an HTTPS connection which informs the browser to load a site using HTTPS rather than HTTP
Explanation: If a user type in an address bar http://www.geeksforgeeks.com/ or geeksforgeeks.com this will create a chance for a man-in-the-middle attack. The redirect could be exploited to direct visitors to a malicious site instead of the secure version of the original site.
https://www.geeksforgeeks.org/http-headers-strict-transport-security/
- Securing Mobile Applications With Cert Pinning
Securing your mobile applications with cert pinning will help you ward off man-in-the-middle (MiTM) attacks, verify users using trusted certificates, and secure HTTPS network traffic
Implementing cert pinning in your mobile app can strengthen the security of its network communications and is a big step in protecting your app data. Once you invest in cert pinning, test to ensure that you have properly implemented cert pinning to prevent MiTM attacks
https://dzone.com/refcardz/securing-mobile-applications-with-cert-pinning?chapter=1