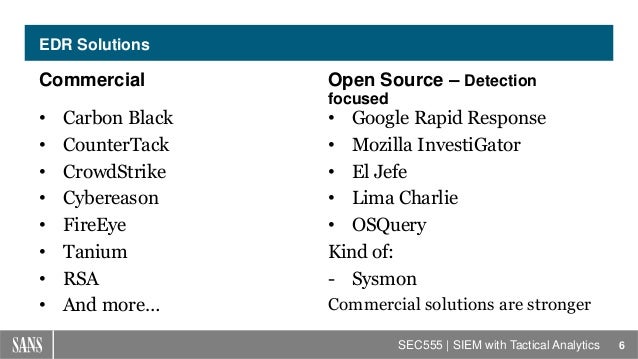
- The features that most EDR solutions have include:
The ability to detect and prevent hidden exploit processes that are more complex than a simple signature or pattern and evade traditional AV
Threat intelligence
Visibility throughout endpoints, including applications, processes and communications, to detect malicious activities and simplify security incident response
Automation of alerts,
Forensic capabilities, because once an attacker is inside, you need the ability to take a deep dive into their activities so you can understand their movements and minimize the impact of the breach
Data collection to build a repository used for analytics
https://www.esecurityplanet.com/products/top-endpoint-detection-response-solutions.html
- Let’s Define Endpoint Detection and Response (EDR)
Endpoint detection and response solutions collect, record, and store large volumes of data from endpoint activities to provide security professionals with the comprehensive visibility they need to detect, investigate, and mitigate advanced
Traditional antivirus solutions,
Endpoint detection and response, or EDR, solutions provide a different capability to the security stack. With EDR in place, security teams can continuously collect, record, and store endpoint data, providing them with surveillance-like visibility they can use to investigate a past incident or
Where Does AV Stop... And EDR Start?
NGAV solutions can prevent known and unknown malware attacks, but comprehensive security programs need more power when they want to go after the undetected, persistent campaigns and attacks that act slowly and purposefully to evade automated defenses.
One of the most important benefits that EDR brings to a security team is visibility, which, when supported by the power of the cloud, can store large masses of data which
However, the best endpoint security scenario brings NGAV and EDR solutions together in a single integrated solution that leverages a single agent to provide the most secure approach possible.
https://www.carbonblack.com/resources/definitions/what-is-endpoint-detection-and-response/
- WHAT IS ENDPOINT DETECTION AND RESPONSE?
“the tools primarily focused on detecting and investigating suspicious activities (and traces of such) other problems on hosts/endpoints.”
HOW ENDPOINT DETECTION AND RESPONSE WORKS
Endpoint detection and response tools work by monitoring endpoint and network events and recording the information in a central database where further analysis, detection, investigation, reporting, and alerting take place. A software agent installed on host systems provides the foundation for event monitoring and reporting.
https://digitalguardian.com/resources/data-security-knowledge-base/endpoint-detection-and-response-edr
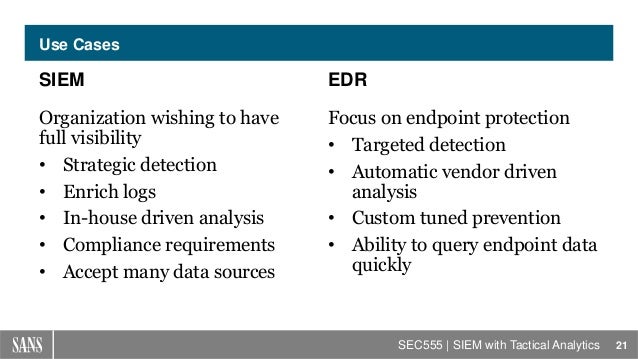
- The difference between SIEM and EDR
an EDR is used to determine if malware (APTs, advanced persistent threats) has been installed on an endpoint device (detect) and find ways to reply to this kind of threat (response).
Often, EDR solutions are using agents installed on such an endpoint to collect data from many different kind of data sources directly on the endpoint and store them in a central database.
data from the following sources:
ARP
DNS
Sockets
Registry
Memory dumps
System calls
IP addresses
Hardware types
An EDR is seen complimentary to traditional means of protection like signature-based tools or a SIEM.
They all provide dashboards or reports and data analysis is performed.
SIEM
It is possible to understand
Summary
https://www.logpoint.com/en/blog/the-difference-between-siem-and-edr/
- SIEM vs EDR: Which One Does Your Business Need?
What is SIEM?
SIEM refers to Security Information and Event Management. It provides log management and security event correlation, both of which offers more visibility into enterprise IT environments. In fact, SIEM places a great emphasis on its log capabilities.
What is EDR?
EDR functions as an extension of next-generation endpoint security.
EDR can help your enterprise detect cyber attacks which slipped past your digital perimeter security. Also, it offers granular visibility, threat investigations, and detection of
SIEM vs EDR
EDR draws from endpoint data sources as one might expect from an endpoint security capability
Its design lends itself to endpoint prevention, endpoint detection, and analysis.
EDR
EDR remains heavily tied to the endpoint rather than the network as a whole
SIEM draws from unlimited data sources; the only constraints come for the correlation rules placed on it by enterprises themselves. Thus SIEM allows for security analysis and compliance fulfillment much more readily. It also provides data contextualization.
SIEM can run into issues with encryption.
these solutions
Without logged data, SIEM can’t function, which can create new challenges for
both SIEM and EDR provide security alerts. Therefore, both can run into similar problems concerning false positives and alert bombardments overwhelming security teams.
https://solutionsreview.com/endpoint-security/siem-vs-edr-which-one-does-your-business-need/
- What is Endpoint Detection and Response?
endpoint detection and response solutions record system activities and events taking place on endpoints and provide security teams with the visibility they need to uncover incidents that would otherwise remain invisible
What is the difference between EDR and Antivirus? Antivirus is the prevention component of endpoint security, which aims to stop threats from entering a network. When threats slip past an antivirus, EDR detects that activity and allows teams to contain the adversary before they can move laterally in the network
EDR Security Capabilities
Incident data search and investigation
Alert triage or suspicious activity validation
Suspicious activity detection
Threat hunting or data exploration
Stopping malicious activity
Choosing an EDR Solution
1. Visibility:
Real-time visibility across all your endpoints allows you to view adversary activities, even as they attempt to breach your environment, and stop them immediately.
2. Threat Database:
Effective EDR requires massive amounts of telemetry collected from endpoints and enriched with context so it can be mined for signs of attack with a variety of analytic techniques.
3. Behavioral Protection:
Relying solely on signature-based methods or indicators of compromise (IOCs) lead to the “silent failure” that allows data breaches to occur. Effective endpoint detection and response requires behavioral approaches that search for indicators of attack (IOAs), so you are alerted of suspicious activities before a compromise can occur.
4. Insight and Intelligence:
An endpoint detection and response solution that integrates threat intelligence can provide context, including details on the attributed adversary that is attacking you or other information about the attack.
5. Fast Response:
EDR that enables a fast and accurate response to incidents can stop an attack before it becomes a breach and allow your organization to get back to business quickly.
6. Cloud-based Solution:
Having a cloud-based endpoint detection and response solution is the only way to ensure zero impact on endpoints, while making sure capabilities such as search, analysis and investigation can be done accurately and in real time
How EDR Works?
The solution lies in having continuous and comprehensive real-time visibility into what is happening on your endpoints and the ability to apply behavioral analysis and actionable intelligence to stop an incident from turning into a breach.
Integrates With Threat Intelligence
Security Operation Centers (SOCs) and security analysts receive a detailed narrative that specifies the “who, why and what” of the event — empowering organizations to be better prepared to protect itself.
Provides Real-Time and Historical Visibility
This gives security teams the useful information they need, including:
local and external addresses to which the host is connected
all the user accounts that have logged in, both directly and remotely
a summary of changes to ASP keys, executables and administrative tool usage
process executions
both summary and detailed process-level network activity, including DNS requests, connections, and open ports
archive file creation, including RAR and ZIPS
removable media usage
Real Time Response includes two sets of built-in commands you can execute during investigations to accelerate remediation.
Information collectors allow security teams to immediately understand the risk and scope of a threat by enabling tasks such as:
Explore the file system and extract files
List running processes
Extract Windows event log
Query Windows registry
List current network connections and configuration
Extract process memory
Calculate file hashes
Collect environment variables
Collect additional desired information using PowerShell or other tools
Remediation actions enable teams to take action to contain or remediate a threat with speed and decisiveness including:
Delete a file
Kill a process
Delete or modify Windows registry key or value
Put a file
Run a script or an executable file
Encrypt a file
Restart/Shutdown
Why is EDR Important?
Reason #1: Prevention alone can’t ensure 100 percent protection
Reason #2: Adversaries can be inside your network for weeks and return at will
Reason #3: Organizations lack the visibility needed to effectively monitor endpoints
Reason #4: Access to actionable intelligence is needed to respond to an incident
Reason #5: Having the data is only part of the solution
Reason #6: Remediation can be protracted and costly
https://www.crowdstrike.com/epp-101/what-is-endpoint-detection-and-response-edr/
- Endpoint Detection and Response: Threat Hunting and Incident Response for Hybrid Deployments
VMware Carbon Black EDR initially is an incident response and threat hunting solution designed for security operations center (SOC) teams with offline environments or on-premises requirements.Carbon Black EDR continuously records and stores comprehensive endpoint activity data, so that security professionals can hunt threats in real time and visualize the complete attack kill chain. It leverages the VMware Carbon Black Cloud’s aggregated threat intelligence, which is applied to the endpoint activity system of record for evidence and detection of these identified threats and patterns of behavior.
https://www.carbonblack.com/resources/endpoint-detection-and-response-threat-hunting-and-incident-response-for-hybrid-deployments/
- Endpoint Detection and Response (EDR)
Identify, isolate and remove endpoint threats in real-time
Continuous monitoring for real-time EDR security
EDR works through continuous monitoring of the endpoint using Indicators of Compromise (IoC).
Rapid incident response times
Many endpoint threats can bypass traditional and advanced security in the time it takes for a human to respond to the activity
Complete visibility across your entire endpoint network
How EDR works
Endpoint Detection and Response tools work by continuously monitoring activity on endpoints, with the aim of identifying suspicious or threatening behaviour in real time.
Information is recorded and analysed for internal or external attacks.
EDR can identify specific behaviors to alert organizations to potential threats before the attackers can cause harm.
Once a threat has been detected, EDR can isolate and deflect attacks from internal and external sources, protecting endpoint devices from risks.
The end-to-end analysis is supported by a range of innovative technologies, including machine learning and behavioral analysis.
https://www.fireeye.com/products/endpoint-security/endpoint-detection-response.html


:max_bytes(150000):strip_icc()/behavioral-job-interview-questions-2061629_round2-5b4f594846e0fb005b443466.png)

