- How are devices represented in UNIX?
All devices
are represented by files called special files that
are located in/dev directory
A 'regular file' is just an ordinary data file in the disk
A 'block special file' represents a device with characteristics similar to a disk (data transfer in terms of blocks)
A 'character special file' represents a device with characteristics similar to a keyboard (data transfer is
by stream of bits in sequential order).
All UNIX files have its description stored in a structure called '
inode'
Inode consists of the following fields:
File owner identifier
File type
File access permissions
File access times
Number of links
File size
Location of the file data
Directories are also represented as files and have an associated
inode
inode
In computing, an
inode (index node) is a data structure found in many Unix file systems. Each
inode stores all the information about a file system object (file, directory, device node, socket, pipe, etc.), except data content and file name.
http://en.wikipedia.org/wiki/Inode
Type
ls command with -i
( print the index number of each file
) option:
ls -i a.txt
1898766 a.txt
- How do you change File Access Permissions?
(user permission-group permission-others permission)
r-read,
w-write, x-execute
Each operation
is represented by discrete values
'
r' is 4
'
w' is 2
'x' is 1
To change mode of
myfile to '
rwxr–
r–' we give the
args as
chmod(myfile,0744)
When using the numeric system, the code for permissions is
as follows:
r = 4
w = 2
x = 1
rwx = 7
The first 7 of "
chmod 775" tells Unix to change the user's permissions to
rxw because r=4 + w=2 + x=1 adds up to 7.
The second 7 applies to the group,
and the last number 5, refers to others (4+1=5).
read permission for all roles on a file/directory (
user,group,others)
ls -
l
---x
--x
--x 1 root
root 7 Dec 1 2011 a.txt
chmod a+r a.txt
ls -
l
-
r-xr-xr-x 1 root
root 7 Dec 1 2011 a.txt
Apply the permission to all the files under a directory recursively
ls -
l test
-
rw-
r--r-- 1 root
root 3 Nov 6 11:45 a.txt
-
rw-
r--r-- 1 root
root 3 Nov 6 11:45 b.txt
chmod -R 177 test
[
root@localhost yeniceri]#
ls -
l test
total 16
---
xrwxrwx 1 root
root 3 Nov 6 11:45 a.txt
---
xrwxrwx 1 root
root 3 Nov 6 11:45 b.txt
A shell is an interactive user interface to an operating system services that allows an user to enter commands as character strings or through a graphical user interface
- Explain fork() system call.
The `fork
()' used to create a new process from an existing process
.The new process
is called the child process, and the existing process
is called the parent
Predict the output of the following program code
main
()
{
fork
();
printf("Hello World!");
}
output:
Hello
World!Hello World!
Explanation:
The fork creates a child that is a duplicate of the parent process. The child begins from the fork
().All the statements after the call to fork
() will
be executed twice.
(once by the parent process and other by
child). The statement before fork
() is executed only by the parent
process
2^n times where n is the number of calls to fork
()
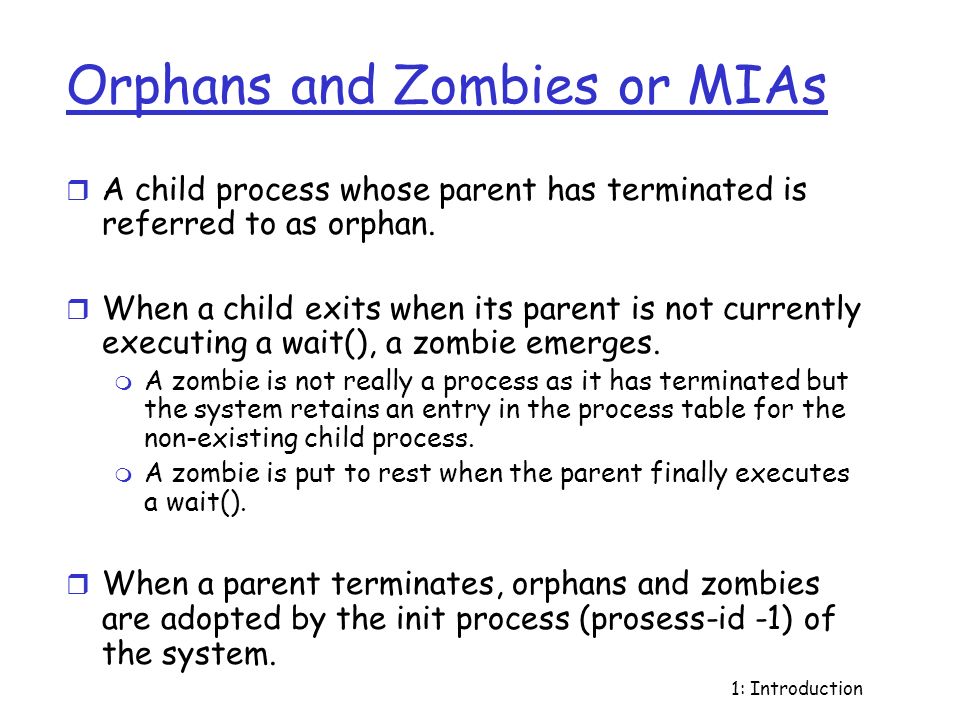
When a program forks and the child finishes before the parent, the kernel still keeps some of its information about the child in case the parent might need it
Zombie
: The process is dead but have not
been removed from the process table.
Simulate zombie process, orphan process scenario
- The arrangement of disk blocks in Unix is
boot block
super block
I-node list
data blocks
The boot block contains the code to bootstrap the OS
The super block contains information about the entire disk
The I-node list a list of
inodes
the data blocks
contains the actual data in the form of directories and files
http://www.angelfire.com/myband/binusoman/Unix.html
- Explain the difference between a static library and a dynamic library?
Static library is linked into the executable, while
a dynamic library (or shared object) is loaded while the executable has started.
It’s an environment variable that lists all the directories
which should be searched for libraries before
the standard directories are searched.
- In Unix, what is a daemon?
Daemon stands for Disk and Execution Monitor. A daemon is a long-running background process that answers requests for services. The term originated with Unix, but most operating systems use daemons in some form or another. In Windows NT, 2000, and XP, for example,
daemons are called "services". In Unix, the names of daemons conventionally end in "d". Some examples include
inetd,
httpd,
nfsd,
sshd, named, and
lpd.
- What's the difference between `telnet` and `ssh`?
TELNET, by default,
does not encrypt any data sent over the connection
(including password, and so it is often practical to eavesdrop on the communications and use the password later for malicious purposes
;SSH by default encrypt password and traffic.
- SSH is Application layer protocol which allows data to be exchanged over a secure channel between two computers. SSH by default encrypt password and traffic. SSH is recommended for all use
start the SSH server by typing /etc/init
.d/
sshd start
SSH works, then you should disable the
telnet service on your Linux machine by editing /etc/
inetd.conf, commenting out the "
telnet" line, saving /etc/
inetd.conf, and then typing /etc/
rc.d/init
.d/
inet restart to re-read /etc/
inetd.conf.
Secure Shell (SSH) is a cryptographic network protocol for securing data communication. It establishes a secure channel over an insecure network in a client-server architecture, connecting an SSH client application with an SSH server.
[1] Common applications include remote command-line login, remote command execution, but
any network service can be secured with SSH. The protocol specification distinguishes between two major versions that
are referred to as SSH-1 and SSH-2.
It was designed as a replacement for
Telnet and other insecure remote shell protocols such as the Berkeley
rsh and
rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis
http://en.wikipedia.org/wiki/Secure_Shell
The term run level refers to a mode of operation in one of the computer operating systems that implement Unix System V-style initialization
a 'run level' determines
which programs are executed at system startup.
* 0
System Halt
* 1
Single user
* 2
Full multi-user mode (Default)
* 3-5
Same as 2
* 6
System Reboot
Run level 0 is the system halt condition
Run Level 1 is known as 'single user' mode.
A more apt description would be 'rescue', or 'trouble-shooting' mode.
In run level 1,
no daemons (services) are started.
Run levels 2 through 5 are full multi-user mode
common practise in other Linux distributions to use run level 3 for a text console login and run level 5 for a graphical login.
Runlevel 2 is used to start most of the machines services. However, it does not start the network file sharing service (SMB, NFS). This will allows multiple users to login to the machine.
Runlevel 3
is commonly used by servers. This loads all services except the X windows system. This means the system will boot to the equivalent of DOS. No GUIs (KDE, Gnome) will start. This level allows multiple users to login to the machine.
Runlevel 4 is usually a "custom" level. By default it will start a few more services than level 3. This level is usually only used under special circumstances.
Runlevel 5 is everything! This will start any GUIs, extra services for printing, and 3rd party services. Full multi-users support
as well. This
runlevel is
generally used on by workstations.
Run level 6 is used to signal system reboot.
This is just like run level 0 except a reboot
is issued at the end of the sequence instead of a power off.
All the run level files are found in the /etc directory according to the following table:
/etc/rc0
.d
Run level 0
/etc/rc1
.d
Run level 1
/etc/rc2
.d
Run level 2
/etc/rc3
.d
Run level 3
/etc/rc4
.d
Run level 4
/etc/rc5
.d
Run level 5
/etc/rc6
.d
Run level 6
Use the '
runlevel' command to tell you two things: The last run level, and the current run level.
[
root@localhost ~]#
runlevel
N 5
http://www.debian-administration.org/articles/212
- What is the default Window system / Windows manager used in Linux?
X
.org
- Explain process ID zero and process ID 1?
All the idle task has a process ID zero, and never
exits.
The init process, with process ID 1, which does nothing but wait around for its child processes to die. Usually started for /etc/
inittab
- What is POSIX? Name 2 POSIX-oriented operating systems?
Portable Operating System Interface is the collective name of a family of related standards specified by the IEEE to define the application programming interface (API). HP-UX, Solaris, AIX
etc.
The idea is that a program written for one POSIX-Compliant OS would be easier to port to another POSIX-compliant OS than porting between non-POSIX-compliant
OSes.
This is why it is much easier to port an application from, say, FreeBSD to Linux than it is to port it from FreeBSD to Windows (though Windows ostensibly supports a subset of POSIX.)
- You issue the following command useradd -m bobm But the user cannot logon. What is the problem?
You need to assign a password to
bobm's account using the
passwd command.
- What is the minimum number of partitions you need to install Linux?
Answer: 2. Linux can
be installed on two partitions, one as / which will contain all files and a swap partition
- What is the difference between POP3 and IMAP?
The Difference
POP3 works by reviewing the inbox on the mail server and downloading the new messages to your computer. IMAP downloads the headers of the new messages on the server, then retrieves the message you want to read when you click on it.
When using POP3,
your mail is stored on your PC. When using IMAP,
the mail is stored on the mail server. Unless you copy a message to a "Local Folder" the messages
are never copied to your PC.
Scenarios of Use
POP3
· You only check e-mail from one computer.
· You want to remove your e-mail from the mail server.
IMAP
· You check e-mail from multiple locations.
· You use
Webmail.
- Open relays are e-mail servers that are configured to accept and transfer e-mail on behalf of any user anywhere, including unrelated third parties.
http://www.technojobs.co.uk/info/candidate-guides/linux-interview-answers.phtml
http://bipinkdas.blogspot.com/2007/04/interview-questions-for-linux.html
http://nixcraft.com/hangout/11918-linux-unix-interview-questions-answers.html
http://nixcraft.com/linux-software/9693-linux-administrator-interview-questions.html
http://rhcelinuxguide.
wordpress.com/2006/06/01/linux-job-interview-questions/
- What key combination can you press to suspend a running job and place it in the background?
ctrl-
z
- The semi-colon may be used to tell the shell that you are entering multiple commands that should be executed serially. If these were commands that you would frequently want to run, then a script might be more efficient
- What's system call in unix?
A system call is just what its name implies
-- a request for the operating system to do something on behalf of the user's program. The system calls are functions used in the kernel itself.
In computing, a system call is how a program requests a service from an operating system's kernel.
http://www.di.uevora.pt/~
lmr/
syscalls.html
The UID number 0 is special and used by the root user. The zero (0) UID enjoys the unrestricted/unlimited access to Linux system. Note that 0 UID assigned to name root; if you wish you can change this (poorly written program may fail) and assign a different name.
http://www.cyberciti.biz/tips/linux-more-on-user-id-password-and-group-management.html
Udev is an important device management system primarily used by the kernel and the
userspace to more readily detect, manage, and populate your hardware to the system.
When you first boot a Linux system, the
bootscripts found in the
initramfs will use
udev to dynamically detect and load drivers for all your hardware and populate /dev with virtual device files.
udev
udev is a device manager for the Linux kernel. Primarily, it manages device nodes in /dev. It is the successor of
devfs and
hotplug,
which means that it handles the /dev directory and all user space actions when adding/removing devices, including firmware load.
http://en.wikipedia.org/wiki/Udev




No comments:
Post a Comment