- A hardware security module (HSM) is a physical computing device that safeguards and manages digital keys, performs encryption and decryption functions for digital signatures, strong authentication and other cryptographic functions. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessor chips.
A hardware security module can be employed in any application that uses digital keys.
The functions of an HSM are:
onboard secure cryptographic key generation
onboard secure cryptographic key storage, at least for the top level and most sensitive keys, which are often called master keys
key management
use of cryptographic and sensitive data material, for example, performing encryption or digital signature functions
offloading application servers for complete asymmetric and symmetric cryptography.
HSMs are also deployed to manage transparent data encryption keys for databases and keys for storage devices such as disk or tape.
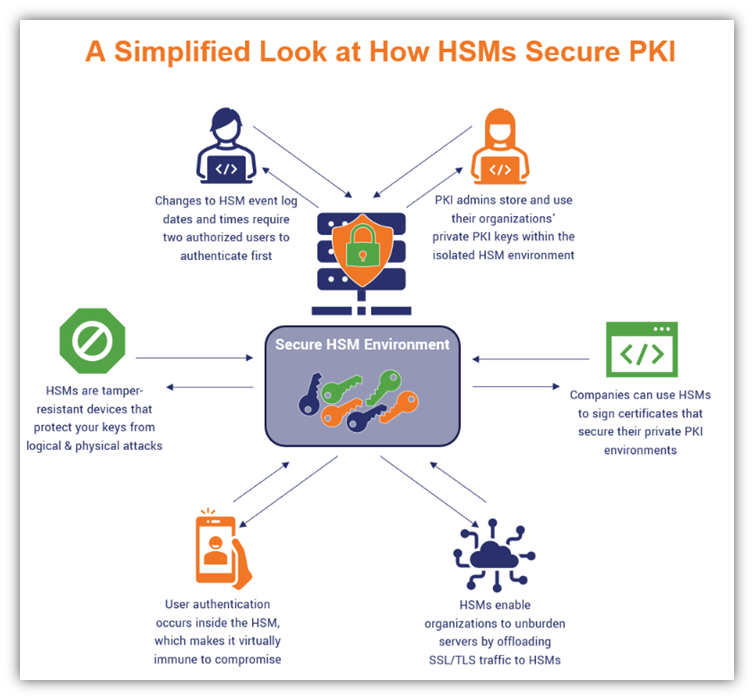
HSMs provide both logical and physical protection of these materials, including cryptographic keys, from disclosure, non-authorized use, and potential adversaries.
HSMs support both symmetric and asymmetric (public-key) cryptography
For some applications, such as certificate authorities and digital signing, the cryptographic material is asymmetric key pairs (and certificates) used in public-key cryptography
With other applications, such as data encryption or financial payment systems, the cryptographic material consists mainly of symmetric keys.
Some HSM systems are also hardware cryptographic accelerators. They usually cannot beat the performance of hardware-only solutions for symmetric key operations.
PKI environment (CA HSMs)
In PKI environments, the HSMs may be used by certification authorities (CAs) and registration authorities (RAs) to generate, store, and handle asymmetric key pairs. In these cases, there are some fundamental features a device must have, namely:
Logical and physical high-level protection
Multi-part user authorization schema (see Blakley-Shamir secret sharing)
Full audit and log traces
Secure key backup
Card payment system HSMs (bank HSMs)
Specialized HSMs are used in the payment card industry. HSMs support both general-purpose functions and specialized functions required to process transactions and comply with industry standards
Typical applications are transaction authorization and payment card personalization
SSL connection establishment
Performance-critical applications that have to use HTTPS (SSL/TLS), can benefit from the use of an SSL Acceleration HSM by moving the RSA operations, which typically requires several large integer multiplications, from the host CPU to the HSM device.
DNSSEC
An increasing number of registries use HSMs to store the key material that is used to sign large zonefiles. OpenDNSSEC is an open-source tool that manages signing DNS zone files.
Cryptocurrency wallet
Cryptocurrency can be stored in a cryptocurrency wallet on a HSM
https://en.wikipedia.org/wiki/Hardware_security_module
Friendly Intro to Hardware Security Modules (HSMs)
- store keys in tamper-proof box
No comments:
Post a Comment