- list federation protocols used along with FIDO2 authentication.
Federation protocols are used to establish trust between different entities across different systems. FIDO2 is a set of authentication protocols that enable users to securely authenticate with online services. FIDO2 can be used with various federation protocols to provide secure authentication. Some of the federation protocols used with FIDO2 authentication are:
OAuth 2.0: OAuth 2.0 is an open standard authorization protocol that enables applications to access user data on behalf of the user. It is often used in conjunction with FIDO2 to enable users to authenticate to online services.
OpenID Connect: OpenID Connect is an identity layer built on top of OAuth 2.0. It provides authentication and authorization for web applications. FIDO2 can be used with OpenID Connect to enable users to authenticate to online services.
SAML (Security Assertion Markup Language): SAML is an XML-based standard for exchanging authentication and authorization data between parties. FIDO2 can be used with SAML to enable users to authenticate to online services.
WS-Federation (Web Services Federation): WS-Federation is a protocol for federated identity and access management. FIDO2 can be used with WS-Federation to enable users to authenticate to online services.
Shibboleth: Shibboleth is an open-source software package for web single sign-on (SSO). FIDO2 can be used with Shibboleth to enable users to authenticate to online services.
These are just a few of the federation protocols that can be used with FIDO2 authentication. The choice of protocol will depend on the specific requirements of the system and the preferences of the developers.
- explain passwordless FIDO2 authentication with ctap2 and webauthn API.
Passwordless FIDO2 authentication with CTAP2 and WebAuthn API involves several steps:
The user initiates the authentication process by visiting a website or application that supports WebAuthn.
The website or application sends a request to the user's device, asking it to provide authentication credentials using the CTAP2 protocol.
The user's device generates a new public-private key pair and sends the public key to the website or application using the CTAP2 protocol.
The website or application creates a challenge and sends it to the user's device using the WebAuthn API.
The user's device signs the challenge with the private key and sends the signed response back to the website or application using the CTAP2 protocol.
The website or application verifies the signed response using the public key that was previously received from the user's device using the CTAP2 protocol.
If the verification is successful, the website or application authenticates the user using the WebAuthn API.
CTAP2 (Client to Authenticator Protocol version 2) is a protocol that defines how a client, such as a website or application, communicates with a FIDO2 authenticator, such as a security key or a biometric sensor. CTAP2 provides a secure and standardized way for clients to communicate with authenticators, allowing for seamless integration with WebAuthn.
WebAuthn API is a web authentication standard that provides a platform- and browser-agnostic API for communicating with FIDO2 authenticators, such as security keys or biometric sensors. WebAuthn enables passwordless authentication using public key cryptography and eliminates the need for traditional password-based authentication methods.
Overall, the combination of CTAP2 and WebAuthn API provides a secure and standardized way for clients to communicate with FIDO2 authenticators, enabling passwordless authentication using public key cryptography. By adopting this approach, websites and applications can provide their users with a convenient and secure authentication experience, while also improving their overall security posture by eliminating the use of weak and easily guessable passwords.
- explain internal authenticator with windows hello
Windows Hello is a biometric authentication feature in Windows 10 that enables users to sign in to their devices using facial recognition, fingerprint scanning, or a PIN. Windows Hello supports both external and internal authenticators, with internal authenticators being built-in sensors, such as cameras and fingerprint readers, that are integrated into the user's device.
An internal authenticator with Windows Hello works by capturing and securely storing the user's biometric data on their device. When the user attempts to log in, Windows Hello uses the built-in sensor to capture their biometric data, such as a facial scan or fingerprint, and compares it to the previously stored data to verify their identity.
Internal authenticators offer several benefits over external ones, including:
Convenience: Internal authenticators are always with the user and do not require any additional hardware or accessories.
Security: Internal authenticators use hardware-based security features, such as secure enclaves, to protect the user's biometric data from unauthorized access or tampering.
Privacy: Internal authenticators keep the user's biometric data on their device, reducing the risk of data breaches or unauthorized access to their personal information.
Windows Hello supports a variety of internal authenticators, including cameras, fingerprint readers, and infrared sensors. These sensors are typically built into the user's device, such as their laptop or tablet, and are integrated with Windows Hello to provide a seamless and secure authentication experience.
Overall, Windows Hello's support for internal authenticators provides a convenient, secure, and privacy-enhancing authentication experience for users, while also helping organizations to improve their overall security posture by reducing the risk of password-related attacks and data breaches
- explain passwordless FIDO2 authentication with webauthn.
WebAuthn is a web authentication standard that enables passwordless authentication using public key cryptography. It is a part of the FIDO2 authentication specification and is supported by most modern web browsers. WebAuthn provides a secure and easy-to-use alternative to traditional password-based authentication methods.
Passwordless FIDO2 authentication with WebAuthn involves the following steps:
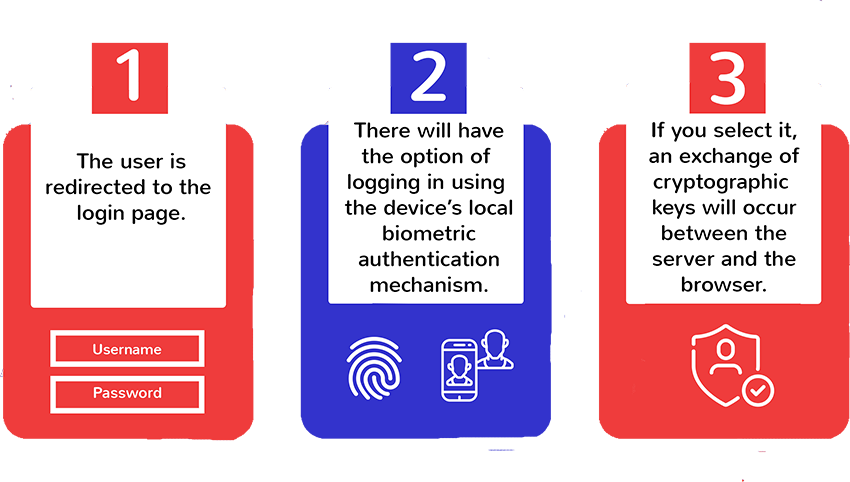
The user initiates the authentication process by visiting a website or application that supports WebAuthn.
The website or application sends a request to the user's device, asking it to provide authentication credentials.
The user's device generates a new public-private key pair.
The user's device sends the public key to the website or application.
The website or application creates a challenge and sends it to the user's device.
The user's device signs the challenge with the private key and sends the signed response back to the website or application.
The website or application verifies the signed response using the public key that was previously received from the user's device.
If the verification is successful, the website or application authenticates the user.
This process allows for secure and convenient authentication without the need for passwords. Instead, the user relies on their device's built-in security features, such as a biometric sensor or a hardware security key, to securely store their private key and handle the authentication process.
WebAuthn is an open and interoperable standard that is supported by a growing number of web browsers and web applications. By adopting WebAuthn, websites and applications can provide their users with a secure and seamless authentication experience, while also improving their overall security posture by eliminating the use of weak and easily guessable passwords.
- explain passwordless FIDO2 authentication with ctap.
FIDO2 is a modern authentication standard that aims to replace traditional password-based authentication methods with a more secure and convenient approach. FIDO2 authentication is based on public-key cryptography, which makes it more resistant to various types of attacks, such as phishing and brute-force attacks.
CTAP (Client to Authenticator Protocol) is a protocol that enables communication between a user's device, such as a smartphone or laptop, and an external authenticator, such as a USB security key. CTAP allows the user's device to request and receive authentication credentials from the authenticator, without the need for the user to manually enter a password.
Passwordless FIDO2 authentication with CTAP involves the following steps:
The user initiates the authentication process by visiting a website or application that supports FIDO2 authentication.
The website or application sends a request to the user's device, asking it to provide authentication credentials.
The device communicates with the external authenticator, using the CTAP protocol, to request a public key credential.
The authenticator generates a new key pair (public and private keys) and sends the public key to the user's device.
The user's device creates a challenge and sends it to the authenticator.
The authenticator signs the challenge with the private key and sends the signed response back to the user's device.
The user's device verifies the signed response using the public key that was previously received from the authenticator.
If the verification is successful, the user's device sends the public key credential to the website or application, which uses it to authenticate the user.
This process allows for secure and convenient authentication without the need for passwords. Instead, the user relies on an external authenticator, such as a USB security key, to securely store their private key and handle the authentication process.
Passwordless FIDO2 authentication is a method of authentication that uses FIDO2 (Fast Identity Online) protocols and standards to authenticate users without the need for a password. Instead, the user is authenticated using a hardware security key or biometric authentication, such as a fingerprint or facial recognition.
Here is how passwordless FIDO2 authentication works:
User initiates authentication: The user navigates to a website or application that supports FIDO2 authentication and initiates the authentication process.
FIDO2 request: The website or application sends a request to the user's FIDO2 security key, asking it to authenticate the user.
User verification: The user is prompted to verify their identity using their hardware security key or biometric authentication.
FIDO2 response: The FIDO2 security key generates a response that is sent back to the website or application, which verifies the user's identity without the need for a password.
Access granted: If the user is successfully authenticated, they are granted access to the website or application.
Passwordless FIDO2 authentication provides a more secure and convenient authentication method than traditional passwords. Hardware security keys are resistant to phishing attacks and other forms of identity theft, and biometric authentication provides a fast and easy way for users to verify their identity.
Passwordless FIDO2 authentication is supported by a growing number of websites and applications, including Microsoft Windows 10 and Google Chrome. It is expected to become more widely adopted in the coming years as the need for strong authentication methods continues to grow.
- FIDO
- Enable FIDO2 authentication
- FIDO2 is a FIDO framework of specifications designed to replace passwords with credentials that cannot be phished, replayed, or breached when servers are compromised – and to do that without sacrificing user convenience across difference types of devices and clients.
- detailed information on how FIDO can be integrated with leading federation protocols, namely SAML, OIDC, and OAuth, including how:
- The FIDO (Fast IDentity Online) authentication standard defines a fast and secure authentication mechanism for users to access websites and applications.
- FIDO consists of three protocols for strong authentication1 to web applications: Universal 2nd Factor (U2F), Universal Authentication Framework (UAF), and FIDO2 or WebAuthn
- FIDO2 is a joint project by the FIDO Alliance (Fast IDentity Online) and the W3C to provide strong authentication for web applications. Thus, it aims to improve security by reducing or eliminating identity theft through providing passwordless authentication.
No comments:
Post a Comment