- What is 802.1X? Everything you need to know about LAN authentication
Understanding what the IEEE 802.1x standard means understanding two related concepts: PPP and EAP
But to understand it and why
PPP - Point-to-Point Protocol. PPP is most commonly used for dial-up Internet access. PPP
PPP evolved beyond its original use as a dial-up access method and
EAP sits inside of PPP's authentication protocol and provides a generalized framework for
By supporting EAP authentication
the IEEE 802.1X standard, which is
With 802.1X, you package EAP messages in Ethernet frames and don't use PPP. It's authentication and nothing more. That's desirable in situations in which the rest of PPP
802.1X uses three terms
The protocol in 802.1X
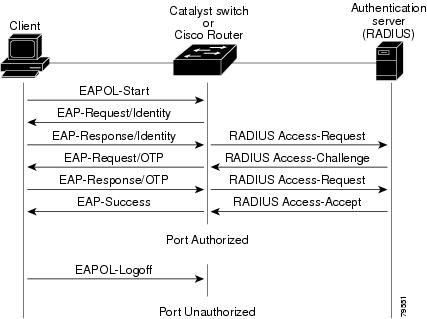
1. The authenticator sends an "EAP-Request/Identity" packet to the supplicant as soon as it detects that the link is active (e.g., the supplicant system has associated with the access point).
2. The supplicant sends an "EAP-Response/Identity" packet to the
3. The authentication server sends back a challenge to the authenticator, such as with a token password system. The authenticator unpacks this from IP and repackages it into EAPOL and sends it to the supplicant. Different authentication methods will vary this message and the total number of messages. EAP supports client-only authentication and strong mutual authentication. Only strong mutual authentication
4. The supplicant responds to the challenge via the authenticator and passes the response onto the authentication server.
5. If the supplicant provides proper identity, the authentication server responds with a success message, which
https://www.networkworld.com/article/2216499/wireless-what-is-802-1x.html
- 802.1X authentication procedures
802.1X authentication has two methods: EAP relay and EAP termination. You choose either mode depending on support of the RADIUS server for EAP packets and EAP authentication methods.
EAP relay
the basic 802.1X authentication procedure in EAP relay mode, assuming that MD5-Challenge EAP authentication is used
EAP termination
the basic 802.1X authentication procedure in EAP termination mode, assuming that CHAP authentication is used .
http://h22208.www2.hpe.com/eginfolib/networking/docs/switches/5130ei/5200-3946_security_cg/content/485048062.htm
- What is 802.1x security authentication?
The IEEE 802.1X standard defines how to provide authentication for devices trying to connect with other devices on LANs or wireless LANs.
he purpose of 802.1x is to accept or reject users who want full access to a network using 802.1x. It is a security protocol that works with 802.11 wireless networks such as 802.11b, g, n, as well as with wired devices.
The main parts of 802.1x Authentication are:
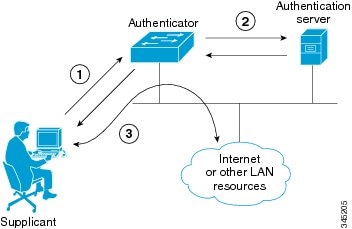
A supplicant, a client end user, which wants to be authenticated .
An authenticator (an access point or a switch), which is a "go between", acting as proxy for the end user, and restricting the end user's communication with the authentication server.
An authentication server (usually a RADIUS server), which decides whether to accept the end user's request for full network access.
A benefit of 802.1x is the switches and the access points themselves do not need to know how to authenticate the client. All they do is pass the authentication information between the client and the authentication server. The authentication server handles the actual verification of the client’s credentials. This lets 802.1x support many authentication methods, from simple user name and password, to hardware token, challenge and response, and digital certificates.
802.1x uses EAP (Extensible Authentication Protocol) to facilitate communication from the supplicant to the authenticator and from the authenticator to the authentication server.
In a wireless network, 802.1x is used by an access point to implement WPA. In order to connect to the access point, a wireless client must first be authenticated using WPA.
In a wired network, switches use 802.1x in a wired network to implement port-based authentication. Before a switch forwards packets through a port, the attached devices must be authenticated . After the end user logs off, the virtual port being using is changed back to the unauthorized state.
https://kb.netgear.com/188/What-is-802-1x-security-authentication
- As the modern workplace is full of external personnel such
as temporary workers, contractors, and guests who may
use their personal devices within the workplace, identity and
device visibility have become valuable components during
the authentication and authorization phase. This data is then
used to enforce policies on wireless and wired networks
For instance,
depending on the access switch configuration, users may be
able to access the wired network through an authenticated
device such as an IP phone’s built-in switch port
This paper discusses options that bring wired networks
closer to the same level of control that have been on wireless
networks, regardless of access control method, either
through secure means or non-AAA enforcemen
OPTION 1: NON-AAA ENFORCEMENT
With non-AAA enforcement, the goal on a wired network is
to minimize the effort it takes to deploy a policy enforcement
service
Endpoints do not require a supplicant or agent, which
makes it convenient for laptops, printers, and IoT devices –
many of which do not support an 802.1X supplica
When a device plugs into a wired port, the policy engine
can be notified of the new device, and profiling techniques
such as DHCP Fingerprinting or Windows Management
Instrumentation (WMI) can be used to identify the type of
device and the user
With this information, we can validate
this device and user against the Active Directory or a device
database so that appropriate policies can be applied to the
switch port.
This means that every device connecting to
the wired network is profiled and evaluated providing much
needed visibility
Profiling consists of fingerprinting each device as well as the
ability to perform device assessments to better understand
the posture of a device
Methods of profiling and assessment
include DHCP fingerprinting, SNMP scans, NMAP scans, Link
Layer Discovery Protocol (LLDP), Cisco Discovery Protocol
(CDP), Windows Management Instrumentation (WMI),
and more.
The advantage of using non-AAA enforcement is that there
is minimal configuration, and it allows IT to quickly meet
internal or external audit or compliance demand
You’re also able to build a comprehensive database of all devices
connecting to the wired network, which becomes more
important as IoT devices emerge in greater number
OPTION 2: IDENTITY-BASED 802.1X AUTHENTICATION
802.1X is the most secure option and provides real-time
certificate or login and password based authentication
You also benefit by performing authentication before a device
receives an IP address
In the non-AAA model, devices receive
limited access to the network before any authentication
Using 802.1X also provides better options for the
authorization of device privileges. Instead of just VLAN
placement, the use of ACLs, downloadable ACLs, and
roles can be used to define access when the status of a
device changes
The ability to use granular identity-based
enforcement also makes it easier to share user information
with firewalls and other security components for enhanced
downstream policies and threat prevention
There are three components that must be in place and
configured for 802.1X to work; a supplicant, an authenticator,
and an authentication server
The supplicant resides on the
endpoint device, the authenticator is the switch in a wired
network, and the authentication server is a AAA component
that typically uses the RADIUS protocol
For a wired environment, 802.1X eliminates port VLAN
configuration issues as each device that connects can
initiate a session for that specific connection. A user can’t
unplug a printer, connect a laptop and gain access to the
printer VLAN
The workflow, once a laptop is connected,
would be to establish the identity of the user and device and
perform a role-based enforcement for that user or device
For devices that do not support 802.1X, you can also use MAC
address based authentication to enable connectivity to the
wired network.
The profiling data that can be captured is similar to what can
be collected in the non-AAA model
Another advantage is that 802.1X supports logins and
passwords, or the use of device certificates, which provide a
higher level of security.Certificates can’t be spoofed
Today,onboarding services can automate the configuration of
endpoint supplicants and create a database for use when
performing authorization and enforcement
This can be used
on wired, wireless and VPN networks to provide a consistent
user experience
Other advantages include the ability to change the privileges
of connected devices based on their behaviour
r. If multiple devices are connected behind a switch port, a change of
authorization (CoA) to adjust security policies would not
affect all devices, only the target devic
Given that more and more security breaches are targeting
IoT devices on wired network
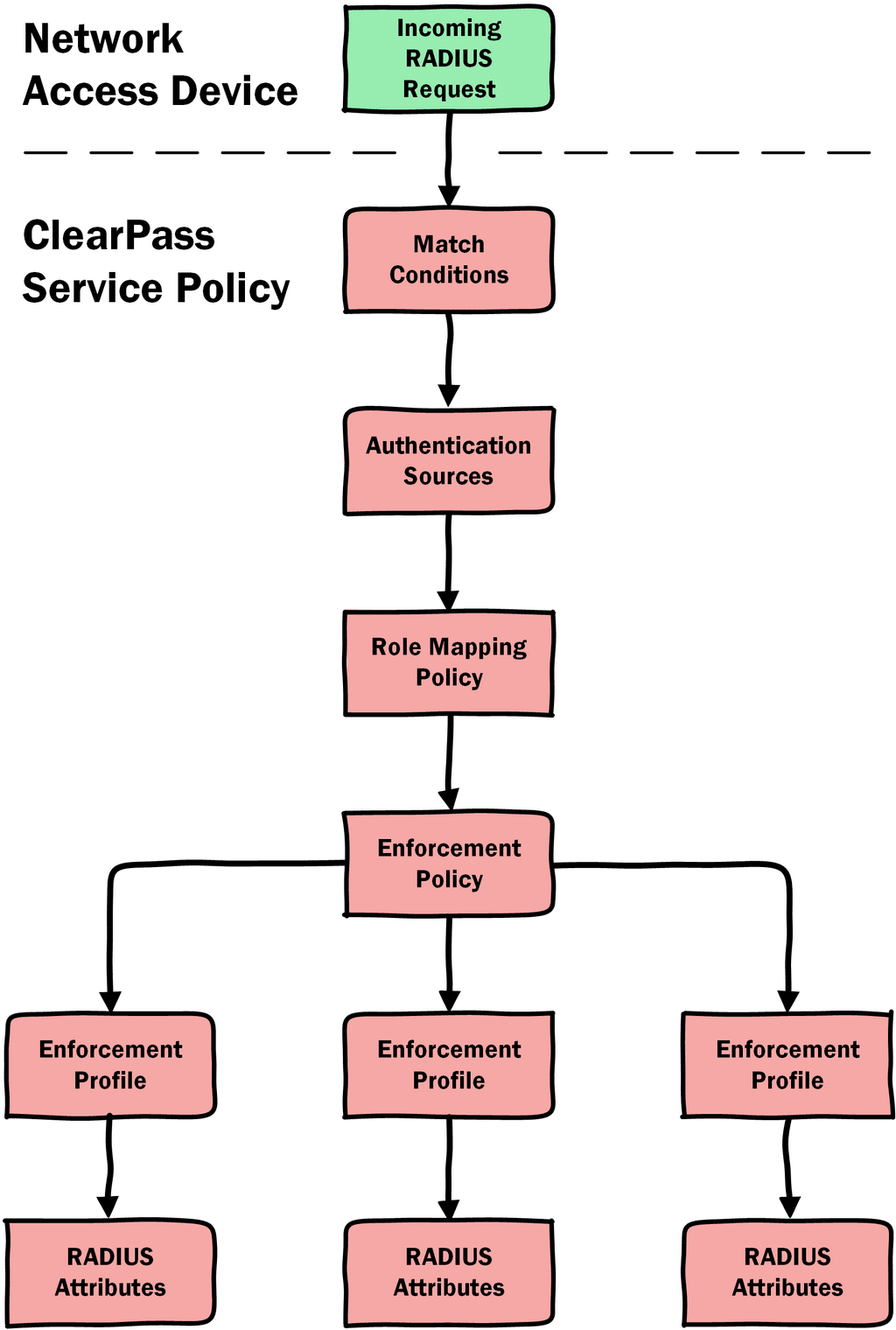
Aruba ClearPass supports
both non-AAA and secure 802.1X policy enforcement for
wired, as well as wireless networks
ClearPass OnConnect
allows for non-AAA wired enforcement so that customers can
start down the policy and access control path. All devices can
be profiled with user based authorization, all with minimal
configuration on the switching infrastructur
The more secure 802.1X enforcement model should be
considered for greater policy enforcement options. As it
will require more planning and configuration, if 802.1X is
already being used for a wireless service, ClearPass provides
mechanisms to unify policy enforcement across different
network transport types, all from a single solutio
https://www.arubanetworks.com/assets/so/SB_AccessControlOptions.pdf
- WIRED 802.1X
Physical port-based network access control
o The new device has to authenticate in order to access the network beyond the switch
WIRED 802.1X
o IEEE standard originally created in 2001
o Physical port-based network access control
o The new device has to authenticate in order to access the network beyond the switch
o 3 roles involved
o SUPPLICANT : The new device
o AUTHENTICATOR : The switch (or Wireless AP)
o AUTHENTICATION SERVER : The server responsible for checking credentials
(Usually a RADIUS server)
PORT-BASED ACCESS CONTROL
o The Authenticator defines 2 logical states per physical port
o Uncontrolled State
o Controlled State
o The uncontrolled state allows 802.1x frames only
o The Authenticator forwards the frames to the Authentication Server
o The controlled state acts like a “normal” port
o The network is fully accessible
o From this point, any packet can go wherever it needs to on the network without
authentication
802.1x only acts as a gatekeeper
o If a device is compromised when already connected to the LAN, 802.1x protection
is useless
802.1x is not a solution to protect a LAN against BYOD hazards
o The compromised device will authenticate against 802.1x as usual
It is also possible to retrieve credentials/certificates
on legitimate devices
o Mimikatz
BYPASS BY DESIGN
o 802.1x only acts as a gatekeeper
o If a device is compromised when already connected to the LAN, 802.1x protection
is useless
o 802.1x is not a solution to protect a LAN against BYOD hazards
o The compromised device will authenticate against 802.1x as usual
o It is also possible to retrieve credentials/certificates
on legitimate devices
o Mimikatz
Note : bruteforce is not possible
o Temporization rules on authentication server
BYPASS - The easy way :
Usually : old devices, low-grade equipment (printers), or very specific systems
(security cameras)
These devices can be unplugged and their Ethernet port hijacked in order to access the
network without the need to authenticate
Solution : MAC Authentication Bypass (MAB)
MAB uses the device’s MAC address to validate its identity
o The authenticator first tries to authenticate the new device by sending EAP Request-
Identity messages
o After 3 unsuccessful attempts, the authenticator falls back to MAB and sends the
device’s MAC address to the authentication server
BYPASS - The hard way :
802.1x provides Network Access Control
o It provides authentication over who can access the network
o It does NOT provide traffic encryption
o It does NOT provide per-packet authentication
Traffic Injection : spoof a legitimate and authenticated supplicant’s MAC and IP address to
fake legitimate packets
Traffic Injection is the most reliable technique to physically attack a 802.1x network
https://hackinparis.com/data/slides/2017/2017_Legrand_Valerian_802.1x_Network_Access_Control_and_Bypass_Techniques.pdf
Understand how the Dot1X (802.1x) protocol works
dot1x does not allow people to bring access point or any other network device to attach to network
rogue access point which is attached to network
supplicant,authenticator,authentication server
supplicant; end users, end points
authenticator; switches
supplicant sends credentials to authenticator and authenticator send those credentials to authentication server
authenticator does not authorize
authentication server decides if the supplicant is allowed to connect to network or not
this supplicant is a user or computer stored in the database which is held on authentication server
authentication server tells authenticator that the supplicant is allowed to connect to network
authenticator then opens port to allow supplicant to connect to network
authentication server has different types ; e.g radius server
there are different types of radius servers; e.g free radius server
how does the authentication happen?
e.g supplicant is authenticating with username/password
e.g supplicant is authencating with MAC address of NIC
e.g supplicant is authencating with digital certificate
802.1x protocol only allows EAPOL traffic not others
EAPOL sends identifying information for network authentication in a secure way
EAPOL provides encrypted EAP tunnel
802.1X | Network Basics
what is this device?
Should it be on my network?
Does it get corporate access? or guest access?
e.g: when you plug in your laptop to network, if you have domain membership and are configured with 802.1x, you have corporate access on wired port.
e.g: if you have authentication server configured to give guest access to a guest, guest has access to internet but not to corporate infrastructure
e.g: if you are not part of a domain, when you plug in your laptop you have no access to network
802.1x provides authentication mechanism for physical access to your network
In public use spaces like bus,campus etc or conference rooms ports are secured
somebody can not walk in your environment to get access to corporate network



A very interesting article. The insights are really helpful and informative. Thanks for posting. Visit here for more info.
ReplyDeleteNetgear Support Phone Number
netgear australia
How to setup Netgear router