- Transmission Control Protocol (TCP)
TCP is
connection-oriented protocol
When a file or message send it will get delivered unless connections fails
You don't have to worry about data arriving in the wrong order.
(TCP) protocol provides extensive error checking mechanisms such as flow control and acknowledgment of data.
Examples:
World Wide Web (TCP port 80)
e-mail (SMTP TCP port 25
Postfix MTA)
File Transfer Protocol (FTP port 21)
Secure Shell (
OpenSSH port 22)
- User Datagram Protocol (UDP)
UDP is
connectionless protocol.
When you a send a data or message, you don't know if it'll get there, it could get lost on the way.
If you send two messages out, you don't know what order they'll arrive in
a lot quicker, and the network card / OS have to do
very little work to translate the data back from the packets
User
Datagram protocol (UDP) has only the basic error checking mechanism using checksum
Examples:
Domain Name System (DNS UDP port 53)
streaming media applications such as IPTV or movies
Voice over IP (VoIP)
Trivial File Transfer Protocol (TFTP)
online
multiplayer games
http://www.cyberciti.biz/faq/key-differences-between-tcp-and-udp-protocols/
- What is the difference between TCP and UDP? When would you use each of them?
What I'm looking for: someone who not only parrots the "connectionless vs. connection-oriented" idea, but can
demonstrate they understand the reasons you might choose one or the other.
what advantages does UDP have over TCP?
UDP does not include a "handshake" in its protocols, it
tends to be faster than TCP. UDP assumes that error checking and correction is
either not necessary or performed in the application, avoiding the overhead of such processing at the network interface level.
Time-sensitive applications often use UDP because dropping packets is preferable to waiting for delayed packets, which may not be an acceptable option in a real-time system.
UDP advantage is primarily speed - no error detection or correction
is used, and
handshaking is not employed either so it is a faster transport mechanism (although it is not reliable).
http://wiki.answers.com/Q/What_advantage_does_UDP_have_over_TCP
- How do I find out running processes were associated with each open port on Linux?
How do I find out what process has open TCP port # 111 or UDP port 7000 under Linux using the CLI?
A port is nothing but an endpoint of communication used in computer networks. You have physical or wireless connections at the hardware level. At software or operating system level a port act as a logical construct that acts as communication port of network service such as SSH, HTTPD and more. TCP and UDP are the most common port.
https://www.cyberciti.biz/faq/what-process-has-open-linux-port/
- Introducing TCP/IP concepts: Selecting sockets
You can choose among the following
types of sockets:
Stream
Datagram
Raw
Stream sockets perform like streams of information. There are no record lengths or character boundaries between data, so communicating processes must agree on their own mechanisms for distinguishing information. Usually, the process sending information sends the length of the data, followed by the data itself. The process receiving information reads the length and then loops, accepting data until all of it has
been transferred. Because there are no boundaries in the data, multiple concurrent read or write socket calls of the same type, on the same stream socket, will yield unpredictable results. For example, if two concurrent read socket calls
are issued on the same stream socket, there is no guarantee of the order or amount of data that each instance will receive. Stream sockets guarantee to deliver data in the order sent and without duplication. The stream socket defines a reliable connection service. Data
is sent without error or duplication and
is received in the order sent.
Flow control is built in to avoid data overruns.
No boundaries are imposed on the data;
the data is treated as a stream of bytes.
Stream sockets are most common because the burden of transferring the data reliably
is handled by TCP/IP, rather than by the application.
The
datagram socket is a connectionless service.
Datagrams are sent as independent packets. The service provides no guarantees. Data can
be lost or duplicated, and
datagrams can arrive out of order. The size of a
datagram is limited to the
size able to
be sent in a single transaction.
Currently, the default value is 8192 bytes, and the maximum value is 65535. The maximum size of a
datagram is 65535 for UDP and 65535 bytes for raw
The raw socket allows direct access to lower layer protocols, such as IP and the ICMP.
This interface is often used to test new protocol implementation, because
the socket interface can be extended and new socket types defined to provide additional services
https://www.ibm.com/support/knowledgecenter/en/SSLTBW_2.3.0/com.ibm.zos.v2r3.hala001/itcsocketconselsoc.htm
- TCP/IP and UDP Comparison
Connection Versus Connectionless — TCP/IP is a connection-based protocol, while UDP is a connectionless protocol. In TCP/IP,
the two ends of the communication link must be connected at all times during the communication. An application using UDP prepares a packet and sends it to the receiver's address without first checking to see if the receiver is ready to receive a packet. If the receiving end is not ready to receive a packet,
the packet is lost.
Stream Versus Packet — TCP/IP is a stream-oriented protocol, while UDP is a packet-oriented protocol. This means that
TCP/IP is considered to be a long stream of data that
is transmitted from one end of the connection to the other end, and another long stream of data flowing in the opposite direction. The TCP/IP stack
is responsible for breaking the stream of data into packets and sending those packets while the stack at the other end
is responsible for reassembling the packets into a data stream using information in the packet headers. UDP
, on the other hand, is a packet-oriented protocol where the application itself divides the data into packets and sends them to the other end. The other end does not have to reassemble the data into a stream. Note, some applications might present the data as a stream when the underlying protocol is UDP. However, this is the layering of an additional protocol on top of UDP, and it is not something inherent in the UDP protocol itself.
TCP/IP Is a Reliable Protocol, While UDP Is Unreliable — The packets that
are sent by TCP/IP contain a unique sequence number.
The starting sequence number is communicated to the other side at the beginning of communication. The receiver acknowledges each packet, and the acknowledgment contains the sequence number so that the sender knows
which packet was acknowledged. This implies that
any packets lost on the way can be retransmitted (the sender would know that they did not reach their destination because it had not received an acknowledgment). Also, packets that arrive out of sequence can
be reassembled in the proper order by the receiver.
timeouts can be established because the sender knows (from the first few packets) how long it takes on average for a packet to
be sent and its acknowledgment received. UDP
, on the other hand, sends the packets and does not keep
track of them. Thus, if packets arrive out of sequence, or
are lost in transmission, the receiving end (or the sending end) has no way of knowing.
Note that "unreliable"
is used in the sense of "not guaranteed to succeed" as opposed to "will fail
a lot of the time."
In practice, UDP is
quite reliable as long as the receiving socket is active and is processing data as quickly as it arrives.
https://www.mathworks.com/help/instrument/tcpip-and-udp-comparison.html
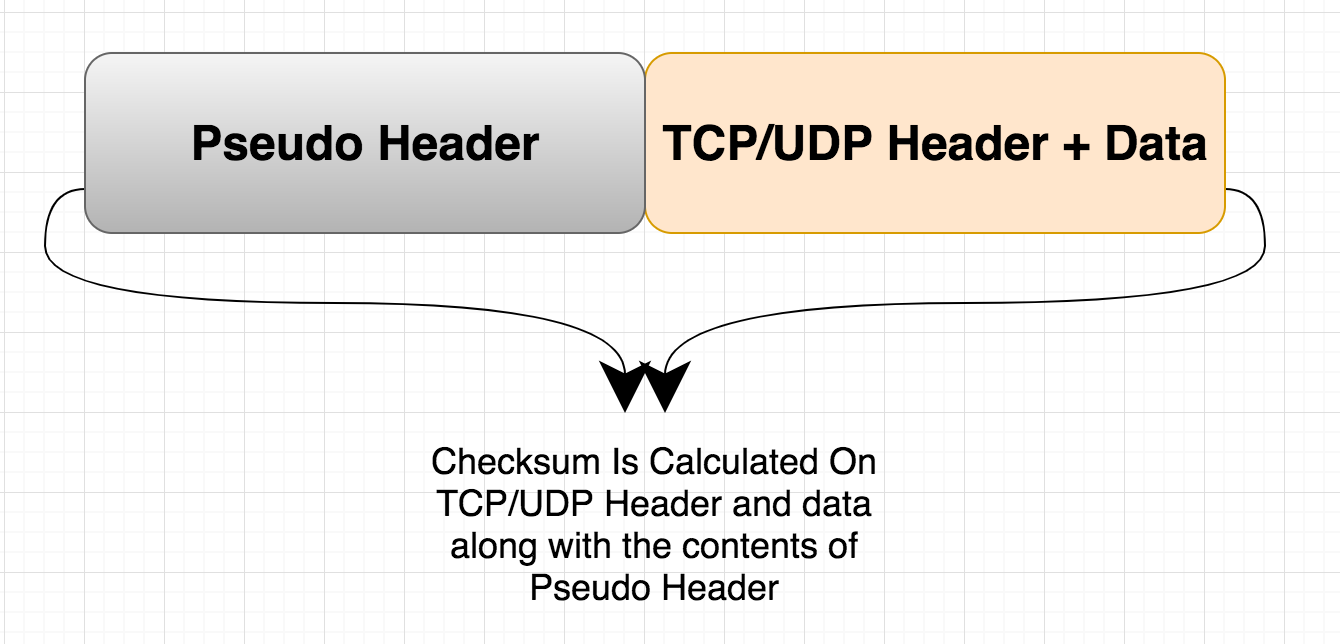
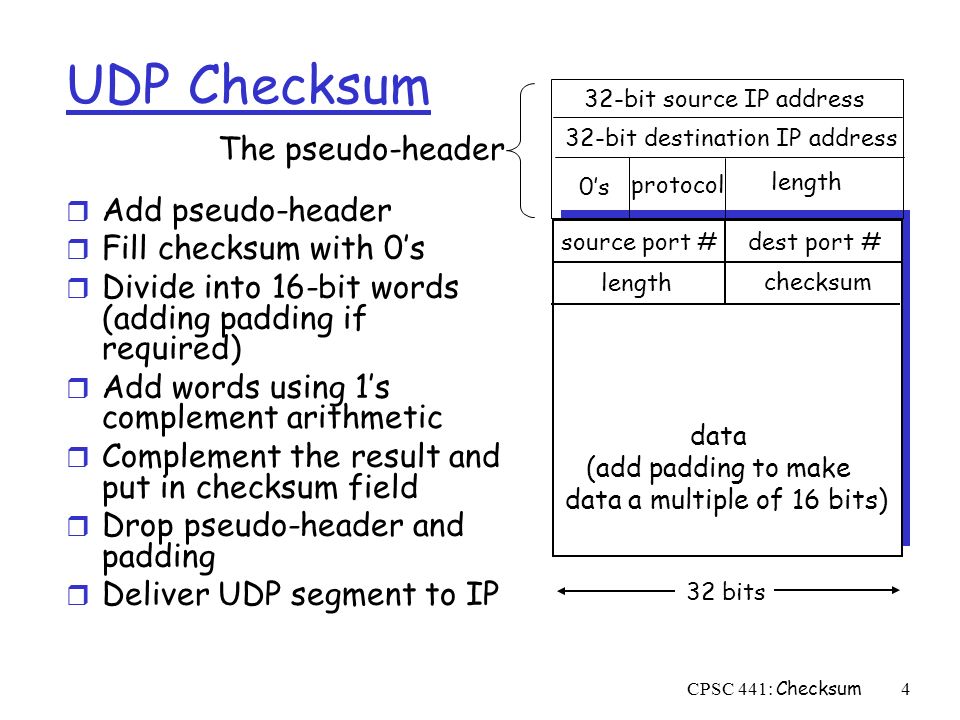
How is TCP & UDP Checksum Calculated?