- An Internet Protocol address (IP address) is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication.[1][2] An IP address serves two principal functions: host or network interface identification and location addressing.
IP networks may be divided into subnetworks in both IPv4 and IPv6. For this purpose, an IP address
is recognized as
consisting of two parts: the network prefix in the high-order bits and the remaining bits called the rest field, host identifier, or interface identifier (IPv6), used for host numbering within a network
.The subnet mask or CIDR notation determines how the IP address
is divided into
network and host parts.
The term subnet mask is only used within IPv4. Both IP versions however use the CIDR concept and notation. In this, the IP address
is followed by a slash and the number (in decimal) of bits used for the network part, also called the routing prefix. For example, an IPv4 address and its subnet mask may be 192.0.2.1 and 255.255.255.0, respectively. The CIDR notation for the same IP address and subnet is 192.0.2.1/24, because the first 24 bits of the IP address
indicate the network and subnet.
Private addresses
Early network design, when global end-to-end connectivity
was envisioned for communications with all Internet hosts, intended that IP addresses be globally unique. However, it
was found that this was not always necessary as private networks developed and public address space needed to
be conserved.
Computers not connected to the Internet, such as factory machines that communicate only with each other via TCP/IP, need not have globally unique IP addresses. Today, such private networks
are widely used and typically connect to the Internet with network address translation (NAT), when needed.
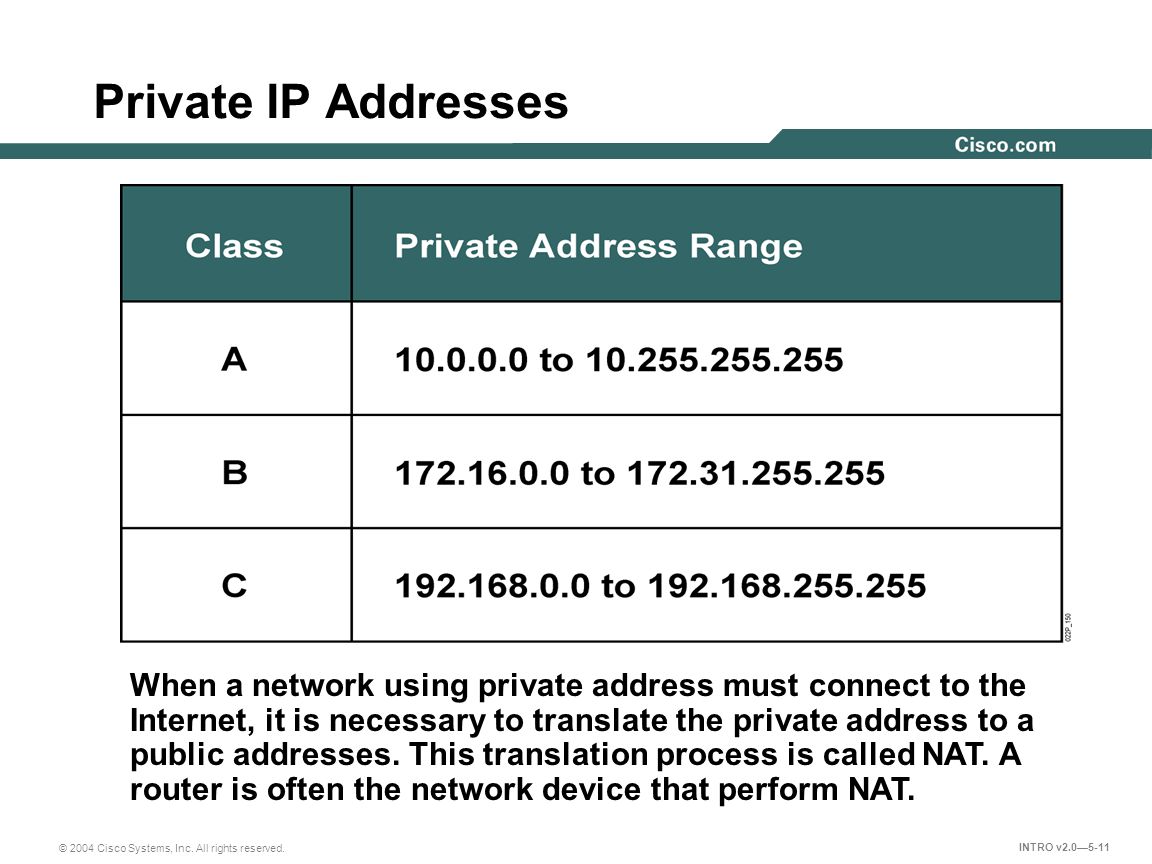
Three non-overlapping ranges of IPv4 addresses for private networks
are reserved.These addresses
are not routed on the Internet and thus their use need not
be coordinated with an IP address registry. Any user may use any of the reserved blocks. Typically, a network administrator will divide a block into subnets; for example, many home routers automatically use a default address range of 192.168.0.0 through 192.168.0.255 (192.168.0.0/24).
IPv6 addresses
In IPv6,
the address size was increased from 32 bits in IPv4 to 128 bits, thus providing up to 2128 (approximately 3.403×1038) addresses
Private addresses
Just as
IPv4 reserves addresses for private networks, blocks of addresses are set aside in IPv6. In IPv6,
these are referred to as unique local addresses (ULAs).
IP address assignment
Dynamic IP addresses are assigned using methods such as
Zeroconf for self-configuration, or by the Dynamic Host Configuration Protocol (DHCP) from a network server. The address assigned with DHCP usually has an expiration period, after which the address may
be assigned to another device, or to the originally associated host if it
is still powered up. A network administrator may implement a DHCP method so that the same host always receives a specific address.
Sticky dynamic IP address
A sticky dynamic IP address is an informal term used by cable and DSL Internet access subscribers to describe a dynamically assigned IP address which seldom changes.
The addresses are usually assigned with DHCP. If
a modem is turned off and powered up again before the next expiration of the address
lease, it often receives the same IP address.
Routing
Unicast addressing
The most common concept of an IP address is in
unicast addressing, available in both IPv4 and IPv6. It normally refers
to a single sender or a single receiver, and can be used for both sending and receiving.
Broadcast addressing
Broadcasting is an addressing technique available in IPv4 to send data to all
possible destinations on a network in one transmission operation, while all receivers capture the network packet (all-hosts broadcast). The address 255.255.255.255
is used for network broadcast
.IPv6 does not implement broadcast
addressing, and replaces it with
multicast to the
specially-defined all-nodes
multicast address
Multicast addressing
A
multicast address is associated with a group of interested receivers. In IPv4, addresses 224.0.0.0 through 239.255.255.255 (the former Class D addresses)
are designated as
multicast addresses
IPv6 uses the address block with the prefix ff00::/8 for
multicast applications. In either case, the sender sends a single
datagram from its
unicast address to the
multicast group address and the intermediary routers take care of making copies and sending them to all receivers that have joined the corresponding
multicast group.
Anycast addressing
Like broadcast and multicast, anycast is a one-to-many routing topology.
Anycast address is an inherent feature of only IPv6. In IPv4, anycast addressing implementations typically operate using the shortest-path metric of BGP routing and do not take into account congestion or other attributes of the path
Public address
A public IP address is a globally routable unicast IP address,
Public IP addresses may be used for communication between hosts on the global Internet.
Firewalling
For security and privacy considerations, network administrators often desire to restrict public Internet traffic within their private networks. The source and destination IP addresses contained in the headers of each IP packet are a convenient means to discriminate traffic by IP address blocking or by selectively tailoring responses to external requests to internal servers. This is achieved with firewall software running on the networks gateway router. A database of IP addresses of permissible traffic may be maintained in blacklists or whitelists.
Address translation
Multiple client devices can appear to share an IP address, either because they are part of a shared hosting web server environment or because an IPv4 network address translator (NAT) or proxy server acts as an intermediary agent on behalf of the client, in which case the real originating IP address might be masked from the server receiving a request.
A common practice is to have a NAT mask a large number of devices in a private network. Only the "outside" interface(s) of the NAT needs to have an Internet-routable address.
Commonly, the NAT device maps TCP or UDP port numbers on the side of the larger, public network to individual private addresses on the masqueraded network.
In residential networks, NAT functions are usually implemented in a residential gateway. In this scenario, the computers connected to the router have private IP addresses and the router has a public address on its external interface to communicate on the Internet. The internal computers appear to share one public IP address.
http://en.wikipedia.org/wiki/IP_address
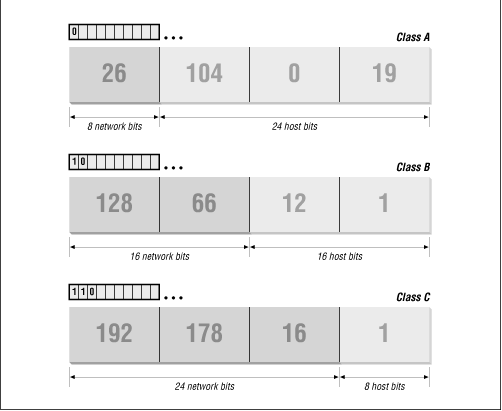
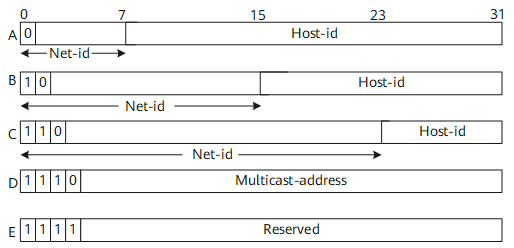
IP address classes
Note: Class A addresses 127.0.0.0 to 127.255.255.255 cannot be used and is reserved for loopback and diagnostic functions.
A
1 – 126*
B
128 – 191
C
192 – 223
D
224 – 239
E
240 – 254
http://www.vlsm-calc.net/ipclasses.php
- A private IP address is an IP address that's reserved for internal use behind a router or other Network Address Translation (NAT) device, apart from the public.
Private IP addresses are in contrast to public IP addresses, which are public and can not be used within a home or business network
Sometimes a private IP address is also referred to as a local IP address.
Which IP Addresses Are Private?
The Internet Assigned Numbers Authority (IANA) reserves the following IP address blocks for use as private IP addresses:
10.0.0.0 to 10.255.255.255
The first set of IP addresses from above allow for over 16 million addresses
172.16.0.0 to 172.31.255.255
The second for over 1 million
192.168.0.0 to 192.168.255.255
over 65,000 for the last range.
Why Private IP Addresses Are Used
Instead of having devices inside a home or business network each use a public IP address, of which there's a limited supply, private IP addresses provide an entirely separate set of addresses that still allow access on a network but without taking up a public IP address space.
For example, let's consider a standard router on a home network. Most routers in homes and businesses across the globe, probably yours and your next door neighbor's, all have the IP address of 192.168.1.1, and assign 192.168.1.2, 192.168.1.3, ... to the various devices that connect to it (via something called DHCP).
It doesn't matter how many routers use the 192.168.1.1 address, or how many dozens or hundreds of devices inside that network share IP addresses with users of other networks because they aren't communicating with each other directly.
Instead, the devices in a network use the router to translate their requests through the public IP address, which can communicate with other public IP addresses and eventually to other local networks.
For example, before landing on this page, your device (be it a computer, phone, or whatever), which uses a private IP address, requested this page through a router, which has a public IP address. Once the request was made and Livewire responded to deliver the page, it was downloaded to your device through a public IP address before reaching your router, after which it got handed off to your private/local address to reach your device
Reserved IP Addresses
Another set of IP addresses that are restricted even further are called reserved IP addresses. These are similar to private IP addresses in the sense that they can't be used for communicating on the greater internet, but they're even more restrictive than that.
The most famous reserved IP is 127.0.0.1. This address is called the loopback address and is used to test the network adapter or integrated chip.
No traffic addressed to 127.0.0.1 is sent over the local network or public internet.
Technically, the entire range from 127.0.0.0 to 127.255.255.255 is reserved for loopback purposes but you'll almost never see anything but 127.0.0.1 used in the real world.
Addresses in the range from 0.0.0.0 to 0.255.255.255 are also reserved but don't do anything at all. If you're even able to assign a device an IP address in this range, it will not function properly no matter where on the network it's installed
https://www.lifewire.com/what-is-a-private-ip-address-2625970
- Note: Class A addresses 127.0.0.0 to 127.255.255.255 cannot be used and is reserved for loopback and diagnostic functions.
Private IP Addresses
http://www.vlsm-calc.net/ipclasses.php
Most organizations have far more computers than available IP addresses. Using private IP addresses helps to tackle this issue by allowing companies to have a single Internet gateway with a public IP address. All of the other nodes have private IP addresses. The gateway uses a Network Address Translation (NAT) server to translate the private IP addresses to an address that can be routed across the Internet.
https://www.sqa.org.uk/e-learning/WebTech01CD/page_12.htm
- The most common use of private addresses is in residential IPv4 networks since most Internet service providers (ISPs) allocate only a single publicly routable IPv4 address to each residential customer, but many homes have more than one computer or another Internet-connected device, such as smartphones. In this situation, a network address translator (NAT/PAT) gateway is usually used to provide Internet connectivity to multiple hosts.
Private addresses are also commonly used in corporate networks, which for security reasons, are not connected directly to the Internet. Often a proxy, SOCKS gateway, or similar devices are used to provide restricted Internet access to network-internal users.
In both cases, private addresses are often seen as enhancing network security for the internal network, since it is difficult for the Internet (external) host to connect directly to an internal system.
https://en.wikipedia.org/wiki/Private_network
- Automatic Private IP Addressing (APIPA) is a DHCP fail-safe that protects a computer system from failure by invoking a standby mechanism for local Internet Protocol version 4 (IPv4) networks supported by Microsoft Windows. With APIPA, DHCP clients can obtain IP addresses even when DHCP servers are not functional. APIPA exists in all modern versions of Windows, including Windows 10.
How APIPA Works
Networks that are set up for dynamic addressing rely on a DHCP server to manage the pool of available local IP addresses. When a Windows client device attempts to join the local network, it contacts the DHCP server to request its IP address. If the DHCP server stops functioning, a network glitch interferes with the request, or some issue occurs on the Windows device, this process can fail.
When the DHCP process fails, Windows automatically assigns an IP address from the private range, which is 169.254.0.1 to 169.254.255.254. Using Address Resolution Protocol (ARP), clients verify that the chosen APIPA address is unique on the network before they use it. Clients then check back with the DHCP server at periodic intervals—usually every five minutes—and update their addresses automatically when the DHCP server is able to service requests.
All APIPA devices use the default network mask 255.255.0.0, and all reside on the same subnet.
Limitations of APIPA
APIPA addresses do not fall into any of the private IP address ranges defined by the Internet Protocol standard and are restricted for use on local networks only. Like private IP addresses, ping tests or any other connection requests from the internet and other outside networks cannot be made to APIPA devices directly.
APIPA-configured devices can communicate with peer devices on their local network but cannot communicate outside of it. While APIPA provides Windows clients a usable IP address, it does not provide the client with nameserver (DNS or WINS) and network gateway addresses as DHCP does.
Local networks should not attempt to manually assign addresses in the APIPA range because IP address conflicts will result. To maintain the benefit APIPA has of indicating DHCP failures, administrators should avoid using those addresses for any other purpose and instead limit their networks to use the standard IP address ranges.
https://www.lifewire.com/automatic-private-internet-protocol-addressing-816437
- If no DHCP server is currently available (either because the server is temporarily down or because none exists on the network), the computer selects an IP address from a range of addresses (from 169.254.0.0 - 169.254.255.255) reserved by the Internet Assigned Numbers Authority (IANA) for that purpose. The client uses the Address Resolution Protocol (ARP) to ensure that the chosen address is not already being used by another network computer. Once the computer has assigned itself an IP address, it can communicate over TCP/IP with other computers on the LAN that are either configured for APIPA or are manually set to the correct address range and a subnet mask value of 255.255.0.0. APIPA is enabled by default but can be disabled in some cases. DHCP messages notify the user when they are switched between DHCP addressing and APIPA.
https://whatis.techtarget.com/definition/Automatic-Private-IP-Addressing-APIPA
127.0.0.1 is the loopback address in IP. Loopback is a test mechanism of network adapters. Messages sent to 127.0.0.1 do not get delivered to the network. Instead, the adapter intercepts all loopback messages and returns them to the sending application. IP applications often use this feature to test the behavior of their network interface.
IPv6 uses 0:0:0:0:0:0:0:1 as its loopback address, equivalent to 127.0.0.1 in IPv4
http://compnetworking.about.com/od/workingwithipaddresses/l/aa042400c.htm
- Identifying the Problem Source
A logical approach is helpful when troubleshooting any problem. Some common questions to ask during troubleshooting include the following:
What works?
What does not work?
How are the things that do and do not work related?
Have the things that do not work ever worked?
If so, what has changed since it last worked?
Table 16-1 Tools and Services for Troubleshooting TCP/IP
Arp
Allows viewing and editing of the Address Resolution Protocol (ARP) cache.
Hostname
Displays the host name of the computer.
Ipconfig
Displays the current TCP/IP configuration for both IPv4 and IPv6. Also used to manage Dynamic Host Configuration Protocol (DHCP)-allocated IPv4 address configurations, display or flush the DNS client resolver cache, and register DNS names.
Nbtstat
Displays NetBIOS over TCP/IP (NetBT) configuration and allows management of the NetBIOS name cache.
Netsh
Configuration tool for many network services. For each network service, there is a context containing commands specific for that service. For the netsh interface ip and netsh interface ipv6 contexts, displays and administers TCP/IP protocol settings on either the local computer or a remote computer.
Netstat
Displays protocol statistics and information on current TCP connections.
Nslookup
Performs DNS queries and displays the results.
Ping
Sends Internet Control Message Protocol (ICMP) Echo or Internet Control Message Protocol for IPv6 (ICMPv6) Echo Request messages to test reachability.
Route
Allows viewing of the IPv4 and IPv6 routing tables and editing of the IPv4 routing table.
Tracert
Sends ICMP Echo or ICMPv6 Echo Request messages to trace the network route taken by IPv4 or IPv6 packets to a specific destination.
Pathping
Sends ICMP Echo or ICMPv6 Echo Request messages to trace the route an IPv4 or IPv6 packet takes to a destination and displays information on packet losses for each router and link in the path.
SNMP service
Provides status and statistical information to Simple Network Management System (SNMP) management systems.
Event Viewer
Records errors and events.
Performance Logs and Alerts
Logs TCP/IP core protocol performance and sends alerts (the SNMP service must be installed).
Network Monitor
Captures and displays the contents of TCP/IP packets sent to and from computers running Windows Server 2003.
Netdiag
Runs a series of diagnostics test on networking components. Netdiag is installed as part of the Windows XP and Windows Server 2003 Support Tools in the Support\Tools folder of the Windows XP or Windows Server 2003 product CD-ROM.
Telnet
Tests TCP connection establishment between two nodes.
Ttcp
Listens for and sends TCP segment data or UDP messages between two nodes.Ttcp.exe is provided with Windows XP Service Pack 2 in the Valueadd\Msft\Net\Tools folder of the Windows XP Service Pack 2 CD-ROM.
Troubleshooting IPv4
The following sections describe the tools and techniques used to identify a problem at successive layers of the TCP/IP protocol stack that is using an IPv4 Internet layer. Depending on the type of problem, you might do one of the following:
Start at the bottom of the stack and move up.
Start at the top of the stack and move down.
The following sections are organized from the top of the stack and describe how to:
Verify IPv4 connectivity.
Verify DNS name resolution for IPv4 addresses.
Verify NetBIOS name resolution.
Verify IPv4-based TCP sessions.
Repair the Connection
The tasks that are performed by Network Connection Repair are the following:
Checks whether DHCP is enabled and, if enabled, sends a broadcast DHCPRequest message to refresh the IPv4 address configuration.
Flushes the ARP cache. This is equivalent to the arp -d * command.
Flushes and reloads the DNS client resolver cache with entries from the Hosts file. This is equivalent to the ipconfig /flushdns command.
Re-registers DNS names using DNS dynamic update. This is equivalent to the ipconfig /registerdns command.
Flushes and reloads the NetBIOS name cache with #PRE entries in the Lmhosts file. This is equivalent to the nbtstat -R command.
Releases and then re-registers NetBIOS names with the Windows Internet Name Service (WINS). This is equivalent to the nbtstat -RR command.
Chapter Summary
The chapter includes the following pieces of key information:
To try and isolate the components that might be at fault when approaching a troubleshooting issue, you should determine what works, what does not work, whether it has ever worked, and what has changed since it last worked.
Windows provides the following tools for troubleshooting TCP/IP problems: Arp, Hostname, Ipconfig, Nbtstat, Netsh, Netstat, Nslookup, Ping, Route, Tracert, Pathping, SNMP service, Event Viewer, Performance Logs and Alerts, Network Monitor, and Netdiag.
Troubleshoot IPv4 communications by verifying IPv4 connectivity, verifying DNS name resolution for IPv4 addresses, verifying NetBIOS name resolution, and verifying IPv4-based TCP sessions.
Troubleshoot IPv6 communications by verifying IPv6 connectivity, verifying DNS name resolution for IPv6 addresses, and verifying IPv6-based TCP sessions.
https://docs.microsoft.com/en-us/previous-versions/tn-archive/bb727023(v=technet.10)
- What Is Straight Through Cable?
A straight through cable is a type of twisted pair cable that is used in local area networks to connect a computer to a network hub such as a router. This type of cable is also sometimes called a patch cable and is an alternative to wireless connections where one or more computers access a router through a wireless signal. On a straight through cable, the wired pins match. Straight through cable use one wiring standard: both ends use T568A wiring standard or both ends use T568B wiring standard.
What Is Crossover Cable?
An Ethernet crossover cable is a type of Ethernet cable used to connect computing devices together directly. Unlike straight through cable, crossover cables use two different wiring standards: one end uses the T568A wiring standard, and the other end uses the T568B wiring standard. The internal wiring of Ethernet crossover cables reverses the transmit and receive signals.
It is most often used to connect two devices of the same type: e.g. two computers (via network interface controller) or two switches to each other.
http://www.cables-solutions.com/difference-between-straight-through-and-crossover-cable.html
- Netstat: network analysis and troubleshooting, explained
In lines saying 'ESTABLISHED', you need the remote port to identify what has connected to the remote site.
In lines saying 'LISTENING', you need the local port to identify what is listening there.
Each outbound TCP connection also causes a LISTENING entry on the same port.
Most UDP listening ports are duplicates from a listening TCP port. Ignore them unless they don't have a TCP twin.
TIME_WAIT entries are not important.
If it says 0.0.0.0 on the Local Address column, it means that port is listening on all 'network interfaces' (i.e. your computer, your modem(s) and your network card(s)).
If it says 127.0.0.1 on the Local Address column, it means that port is ONLY listening for connections from your PC itself, not from the Internet or network. No danger there.
If it displays your online IP on the Local Address column, it means that port is ONLY listening for connections from the Internet.
If it displays your local network IP on the Local Address column, it means that port is ONLY listening for connections from the local network.
https://sites.google.com/site/xiangyangsite/home/technical-tips/linux-unix/networks-related-commands-on-linux/how-to-read-netstat--an-results
- A bundle of network tools
The
netstat command doesn’t really do unique things. It can print network statistics, but
ifconfig can do so, too. It can print routing tables, but route can do that, too. It can print open connections, but
lsof does that, and more. So why use
netstat at all? There are two main reasons:
netstat bundles a few often-used network analysis actions in a single command and
netstat is
multi-platform
https://linuxacademy.com/blog/linux/netstat-network-analysis-and-troubleshooting-explained/
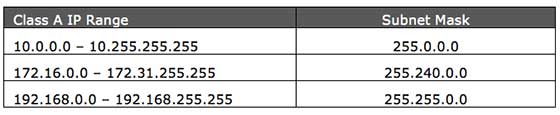
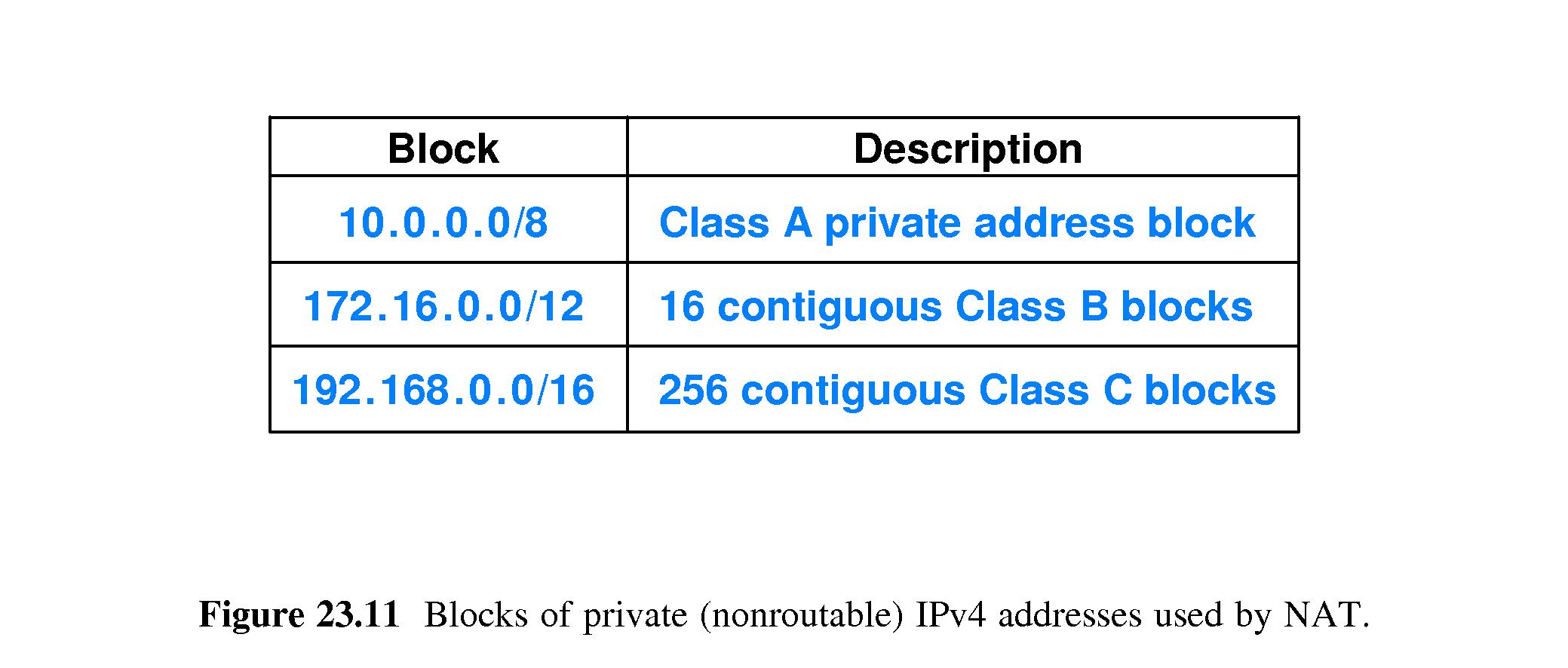
the following IPv4 address ranges are reserved by the IANA for private internets, and are not publicly routable on the global internet:
10.0.0.0/8 IP addresses: 10.0.0.0 – 10.255.255.255
172.16.0.0/12 IP addresses: 172.16.0.0 – 172.31.255.255
192.168.0.0/16 IP addresses: 192.168.0.0 – 192.168.255.255
Note that only a portion of the “172” and the “192” address ranges are designated for private use. The remaining addresses are considered “public,” and thus are routable on the global Internet.
https://www.arin.net/reference/research/statistics/address_filters/
In IP networking, a private network is a computer network that uses private IP address space. Both the IPv4 and the IPv6 specifications define private IP address ranges.[1][2] These addresses are commonly used for local area networks (LANs) in residential, office, and enterprise environments.
Private network addresses are not allocated to any specific organization. Anyone may use these addresses without approval from regional or local Internet registries. Private IP address spaces were originally defined to assist in delaying IPv4 address exhaustion. IP packets originating from or addressed to a private IP address cannot be routed through the public Internet.
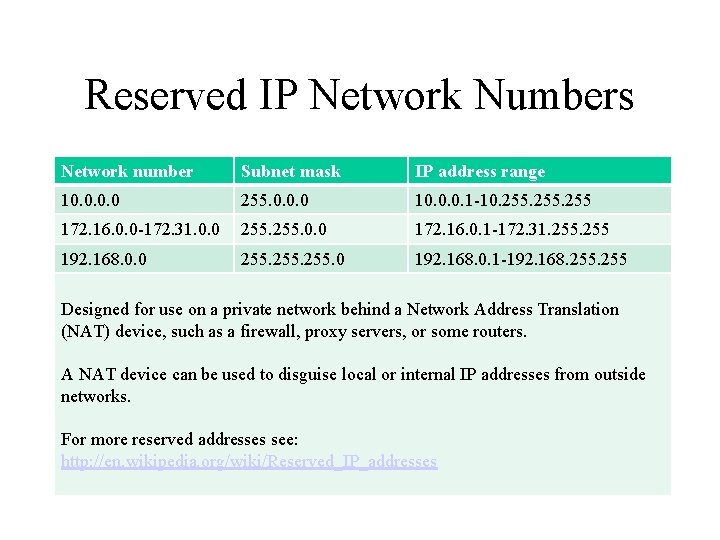
24-bit block 10.0.0.0 – 10.255.255.255 16777216 10.0.0.0/8 (255.0.0.0) 24 bits 8 bits single class A network
20-bit block 172.16.0.0 – 172.31.255.255 1048576 172.16.0.0/12 (255.240.0.0) 20 bits 12 bits 16 contiguous class B networks
16-bit block 192.168.0.0 – 192.168.255.255 65536 192.168.0.0/16 (255.255.0.0) 16 bits 16 bits 256 contiguous class C networks
Private IPv6 addresses
The concept of private networks has been extended in the next generation of the Internet Protocol, IPv6, and special address blocks are reserved.
The address block fc00::/7 is reserved by IANA for Unique Local Addresses (ULA)
https://en.wikipedia.org/wiki/Private_network
In the Internet Protocol Version 4, the address 0.0.0.0 is a non-routable meta-address used to designate an invalid, unknown or non-applicable target.
As a host address
A way to specify "any IPv4 address at all". It is used in this way when configuring servers (i.e. when binding listening sockets). This is known to TCP programmers as INADDR_ANY.
The address a host claims as its own when it has not yet been assigned an address. Such as when sending the initial DHCPDISCOVER packet when using DHCP.
The address a host assigns to itself when address request via DHCP has failed, provided the host's IP stack supports this. This usage has been replaced with the APIPA mechanism in modern operating systems.
A way to explicitly specify that the target is unavailable
A way to route request to a nonexistent target instead of the original target. Often used for adblocking purposes.
In the context of servers, 0.0.0.0 can mean "all IPv4 addresses on the local machine". If a host has two IP addresses, 192.168.1.1 and 10.1.2.1, and a server running on the host is configured to listen on 0.0.0.0, it will be reachable at both of those IP addresses.
Routing
In the context of routing tables, a network destination of 0.0.0.0 is used with a network mask of 0 to depict the default route as a destination subnet. This destination is expressed as "0.0.0.0/0" in CIDR notation. It matches all addresses in the IPv4 address space and is present on most hosts, directed towards a local router.
In routing tables, 0.0.0.0 can also appear in the gateway column. This indicates that the gateway to reach the corresponding destination subnet is unspecified. This generally means that no intermediate routing hops are necessary because the system is directly connected to the destination
In IPv6
In IPv6, the all-zeros address is typically represented by ::, which is the short notation of 0000:0000:0000:0000:0000:0000:0000:0000
The IPv6 variant serves the same purpose as its IPv4 counterpart.
https://en.wikipedia.org/wiki/0.0.0.0
- IANA IPv4 Special-Purpose Address Registry
Documentation (TEST-NET-1)
Documentation (TEST-NET-2)
Documentation (TEST-NET-3)
http://www.iana.org/assignments/iana-ipv4-special-registry/iana-ipv4-special-registry.xhtml
Assigned as TEST-NET-1, documentation and examples.
Assigned as TEST-NET-2, documentation and examples
Assigned as TEST-NET-3, documentation and examples
https://en.wikipedia.org/wiki/Reserved_IP_addresses




- a link-local address is a network address that is valid only for communications within the network segment or the broadcast domain that the host is connected to.
Link-local addresses are most often assigned automatically with a process known as stateless address autoconfiguration or link-local address autoconfiguration
also known as automatic private IP addressing (APIPA) or auto-IP.
Link-local addresses are not guaranteed to be unique beyond their network segment. Therefore, routers do not forward packets with link-local source or destination addresses.
IPv4 link-local addresses are assigned from address block 169.254.0.0/16 (169.254.0.0 through 169.254.255.255). IPv6, they are assigned from the block fe80::/10
https://en.wikipedia.org/wiki/Link-local_address
Network 169.254.0.0/16 is a "reserved network" named IPv4 Link-Local Addresses
IPv4 Link-Local addresses are not suitable for communication with
devices not directly connected to the same physical (or logical)
link, and are only used where stable, routable addresses are not
available (such as on ad hoc or isolated networks)
https://access.redhat.com/solutions/4403501
Link local addresses allow machines to automatically have an IP address on a network if they haven't been manually configured or automatically configured by a special server on the network (DHCP).
Before an address is chosen from that range, the machine sends out a special message (using ARP which stands for address resolution protocol) to the machines on the network around it (assuming that they also haven't been assigned an address manually or automatically) to find out if 169.254.1.1 is free. If it is, then the machine assigns that address to its network card. If that address is already in use by another machine on the same network, then it tries the next IP 169.254.1.2 and so on, until it finds a free address
IP addresses, either IPv4 or IPv6. It is valid in some circumstances to refer to a MAC address as a link-local address but it is a less common use of the term.
the range for IPv4 is 169.254.0.0/16 (169.254.0.1 to 169.254.255.254), with 169.254.0.0 and 169.254.255.255 reserved as network/broadcast addresses
IPv6 has fe80::/10 reserved for Link-Local addresses with most automatically assigned ones being in the fe80::/64 range.
The link-local IP address must be unique within its network segment
The process a device assigning an address to itself is a common use for Link-local IP addresses but it is not the only way they are used. In stateless address autoconfiguration the device should check that an address it wants to try and use is available and then use it. There is nothing to stop you manually assigning the same link-local IP address to two devices you administe
https://serverfault.com/questions/118324/what-is-a-link-local-address