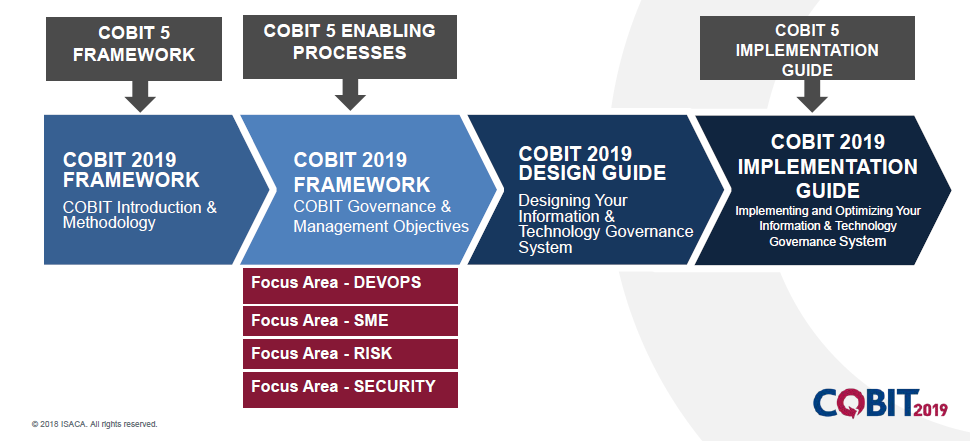
Control Objectives for Information and Related Technology (COBIT) is a framework created by ISACA for information technology (IT) management and IT governance. It is a supporting toolset that allows managers to bridge the gap between control requirements, technical issues and business risks.
- The COBIT - Control Objectives for Information and related Technology corresponds to a structure that embraces all the activities related to the "informatics" for the Information Technology (IT) governance, while the ITIL - Information Technology Infrastructure Library helps in the definition of the processes associated to the IT services which complements the initiative of businesses processes. In general, the ITIL is centered on the best practices in order to ensure the delivery and support of the IT services. These two frameworks (or guidelines) are widely recognized by their complementarity for the IT governance. In this context, after the applicability of the certification of quality services (in particular the ISO 9001 standard) in a Portuguese Private School of the basic and secondary levels, this work was centered in the study, implementation and use of ITIL and COBIT frameworks with the purpose of management and control the IT and in this way, ensure the IT and Information Systems (IS) governance in the institution. The implementation of these frameworks in the institution made possible the management and control of the IT and IS, bringing advantages in terms of performance and efficiency of the quality of the services, as well as a more efficient monitoring in the control of the technological infrastructure, namely through the reduction of 23% in the number of time spent on the accomplishment of tasks; in the reduction of 25% in the number of incidents that were solved and closed by the several information technology services, as well as in the reduction of 10% in the number of reopened incidents.
http://ieeexplore.ieee.org/document/6263073/
The COSO framework was updated in 2016 to provide the approach of an applied risk management for internal controls. It applies to both internal and financial reporting, where its framework encompasses these five strategic pillars.
Strategy and
Objective Setting
– goals of risk tolerance must
be measured objectively.
Governance and Culture
– to oversight enterprise risk management daily.
The Performance Segment- risks should
be prioritized for effective reporting.
Information, Communication and Reporting- proper communication internally and externally
Review and Revision
– continuous internal audit and measuring to revise measures
Just like COSO, COBIT has its 5 strategic principles, with varying purposes and goals, as follows.
Covering Enterprise End-to-End
– Apart from focusing on the IT function, ERM incorporates applications, assets and all technologies and information.
Meeting Stakeholder Needs- Determines resources needed based on people bearing risks and those receiving benefits.
Applying a Single Integrated Framework
–multiple standards are mapped out to the framework of single governance and management.
Enabling a Holistic Approach- has the interconnection of information, policies, infrastructure, people, organizational structures, culture and all processes.
Separating Governance and Management
–analyzing needs to set objectives with clear direction while severing tracking duties from governance authority
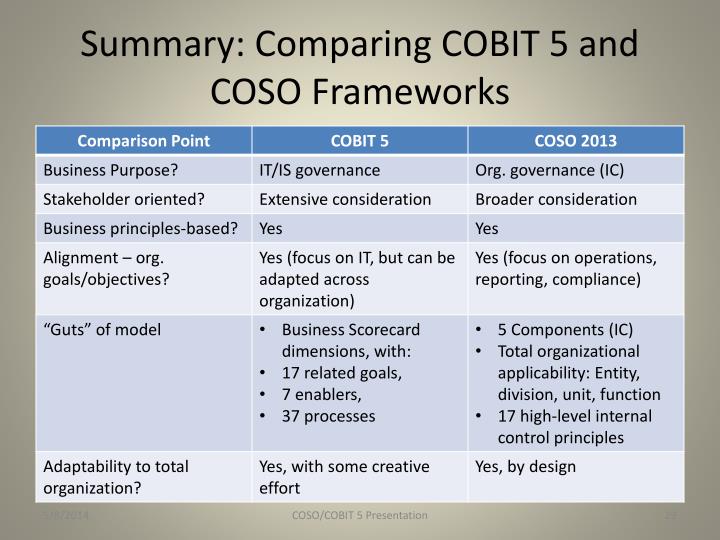
Difference between COBIT 5 and COSO
COSO establishes the guiding principles for organizations to institute risk tolerance and reduce fraud.
On the other hand, COBIT 5 delivers the framework for organizations to build controls of best practices.
Companies that use COSO for establishing their risk reporting approaches can
employ COBIT 5 to organize their control ecosystem
COBIT 5 sets the plans of COSO in
real action so that companies can secure their IT and reporting departments.
Why do organizations need both COSO and COBIT?
COSO and COBIT 5 need to work together on risk governance and a controlled landscape for companies to comply with security requirements.
https://knowtechie.com/what-are-the-differences-between-cobit-coso/
- What is the COSO Framework?
The COSO Framework, most recently updated in 2016, provides an applied risk management approach to internal controls. Applicable to both financial reporting and internal reporting, the COSO framework focuses on five interrelated strategic points.
What are the differences between COBIT 5 and COSO?
COSO acts like the building plans for a new house. The framework lays out the general locations of rooms. COSO allows an organization to frame the building. However, walking through a framed home only shows an outline of how the final plan will look.
COBIT 5 shows organizations where to put the electrical systems, plumbing, and then puts up the drywall. This framework sets the COSO plan into action with details that allow organizations to secure the IT environment.
https://reciprocitylabs.com/what-are-the-differences-between-cobit-coso/
- COSO is a model for corporate governance, and COBIT is a model for IT governance
COSO deals more at the strategic level, while COBIT focuses more at the operational level.
COBIT is a way to meet many of the COSO objectives, but only from the IT perspective.
COSO deals with non-IT items also, as in company culture, financial accounting principles, board of director responsibility, and internal
communication structures
Frameworks such as the Control Objectives for Information and related Technology (CobiT) and the Committee of Sponsoring Organizations of the Treadway Commission (COSO) framework aid regulatory compliance, but don't provide actual risk management methodologies.
Instead they include some high-level goals for risk management as part of their overall scope. While CobiT helps a company define risk goals at an operational level, COSO helps a company define organizational risks at a business level.
While
CobiT is a model for IT governance, COSO is a model for corporate governance.
CobiT was derived from the COSO
framework
COSO focuses on the strategic level, while CobiT focuses more on the operational level. You can think of CobiT
as a way to meet many of the COSO objectives, but only from the IT perspective.
http://www.pearsonitcertification.com/articles/article.aspx?p=1594876&seqNum=2
- What is the ISO 27000 series of standards?
The ISO/IEC 27000 family of information security standards, also known as the ISO 27000 series,
is developed and published by the International Organization for Standardization (ISO) and the International
Electrotechnical Commission (IEC) to provide a globally recognised framework for best-practice information security management.
https://www.itgovernance.co.uk/blog/what-is-the-iso-27000-series-of-standards
- What is an ISMS and 9 reasons why you should implement one
What is an ISMS?
A centrally managed framework for keeping an organisation’s information safe.
A set of policies, procedures, technical and physical controls to protect the confidentiality, availability and integrity of information.
Not an IT function but a business management process.
An ISMS can be certified to the international best-practice information security standard ISO 27001. Achieving accredited certification to the Standard
demonstrates to your clients, customers, regulators and stakeholders that your organisation is following
information security best practice and your data is sufficiently protected.
https://www.itgovernance.co.uk/blog/what-is-an-isms-and-9-reasons-why-you-should-implement-one
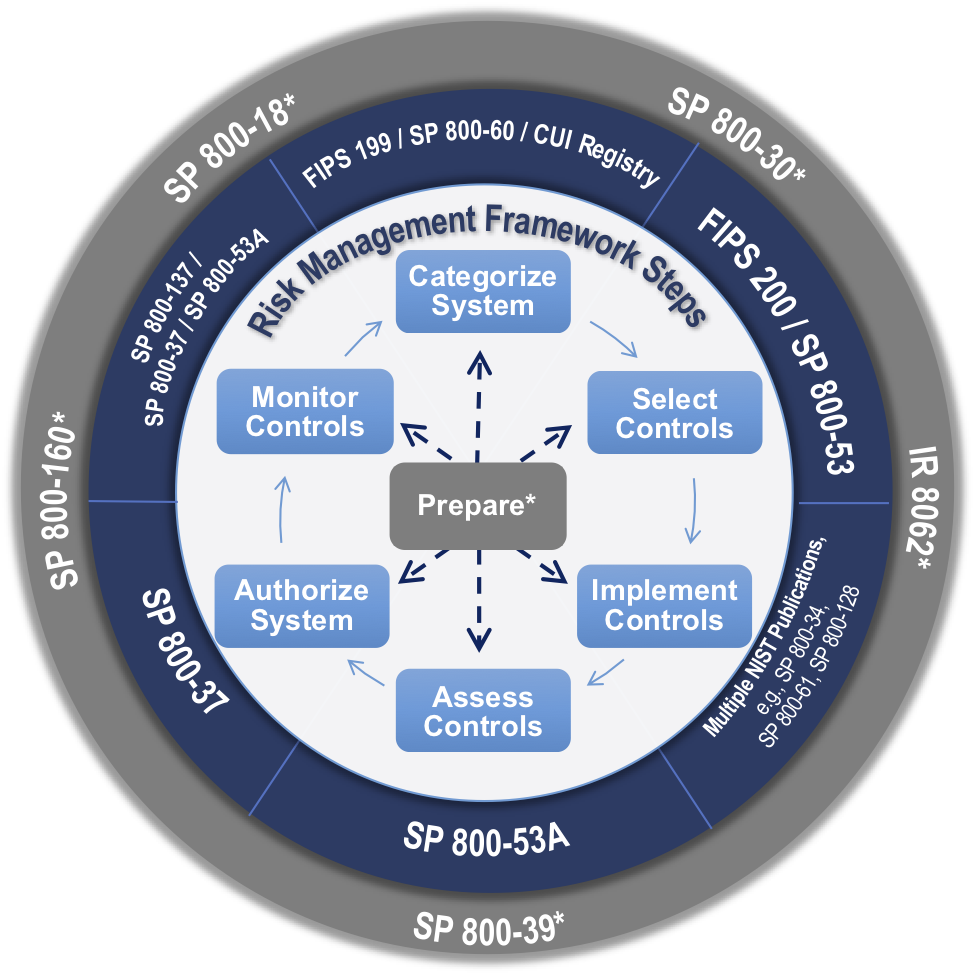
Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy
This publication describes the Risk Management Framework (RMF) and provides guidelines for applying the RMF to information systems and organizations. The RMF provides a disciplined, structured, and flexible process for managing security and privacy risk that includes information security categorization; control selection, implementation, and assessment; system and common control authorizations; and continuous monitoring. The RMF includes activities to prepare organizations to execute the framework at
appropriate risk management levels. The RMF also promotes near real-time risk management and ongoing information system and common control authorization through
the implementation of continuous monitoring processes; provides senior leaders and executives with the
necessary information to make efficient, cost-effective, risk management decisions about the systems supporting their missions and business functions; and incorporates security and privacy into the system development life cycle. Executing the RMF
tasks links essential risk management processes at the system level to risk management processes at the organization level. In addition, it establishes responsibility and accountability for the controls implemented within an organization’s information systems and inherited by those systems.
https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final
- What is NIST SP 800-53? Definition and Tips for NIST SP 800-53 Compliance
NIST SP 800-53 is a set of standards and guidelines to help federal agencies and contractors meet the requirements set by the Federal Information Security Management Act (FISMA).
The SP 800-53 guidelines were created to heighten the security of the information systems used within the federal government. The guidelines themselves apply to any component of an information system that stores, processes, or transmits federal information.
https://digitalguardian.com/blog/what-nist-sp-800-53-definition-and-tips-nist-sp-800-53-compliance
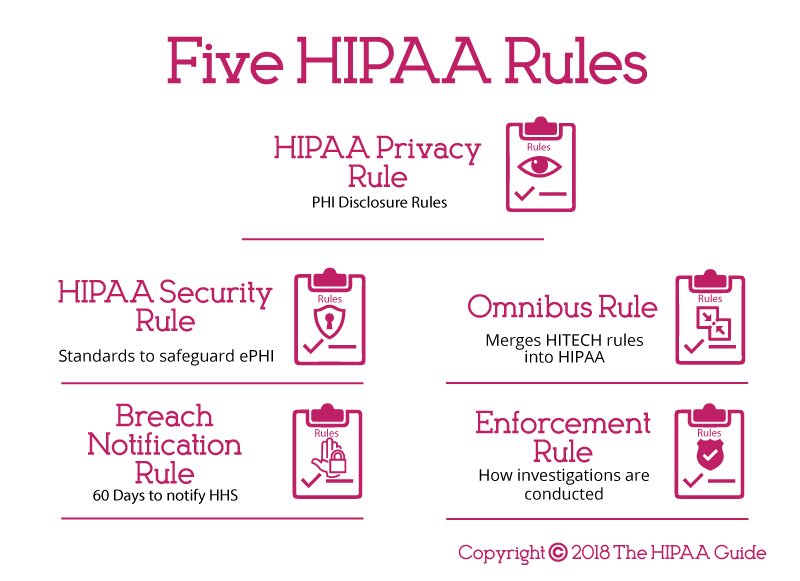
- What is HIPAA Compliance?
HIPAA, the Health Insurance Portability and Accountability Act, sets the standard for protecting sensitive patient data. Any company that deals with protected health information (PHI) must ensure that all the required physical, network, and process security measures are in place and followed.
http://www.onlinetech.com/resources/references/what-is-hipaa-compliance
- HIPAA Compliance Checklist
If your organization has access to electronic Protected Health Information (
ePHI),
it is recommended that you review our HIPAA compliance checklist. The purpose of our HIPAA compliance checklist
is help ensure that your organization complies with the HIPAA regulations covering the security and privacy of confidential patient data.
http://www.hipaajournal.com/hipaa-compliance-checklist/
- What is HITRUST vs. HIPAA?
While HIPAA is an act that details standards for compliance, HITRUST is an organization that helps you achieve those standards. The major difference is that HIPAA is simply a set of regulations while HITRUST assists companies with achieving compliance to those regulations
Additionally, it is important to be aware of how the two relate. HITRUST can be of service to those who are looking to use multiple service vendors while ensuring HIPAA compliance
https://www.givainc.com/blog/index.cfm/2017/2/6/What-is-HITRUST-vs-HIPAA
•
ISO/IEC 27001 ISMS requirements
•
ISO/IEC 27002 Code of practice for information security management
•
ISO/IEC 27003 Guideline for ISMS implementation
•
ISO/IEC 27004 Guideline for information security management measurement and metrics framework
•
ISO/IEC 27005 Guideline for information security risk management
•
ISO/IEC 27006 Guidance for bodies providing audit and certification of information security management systems
•
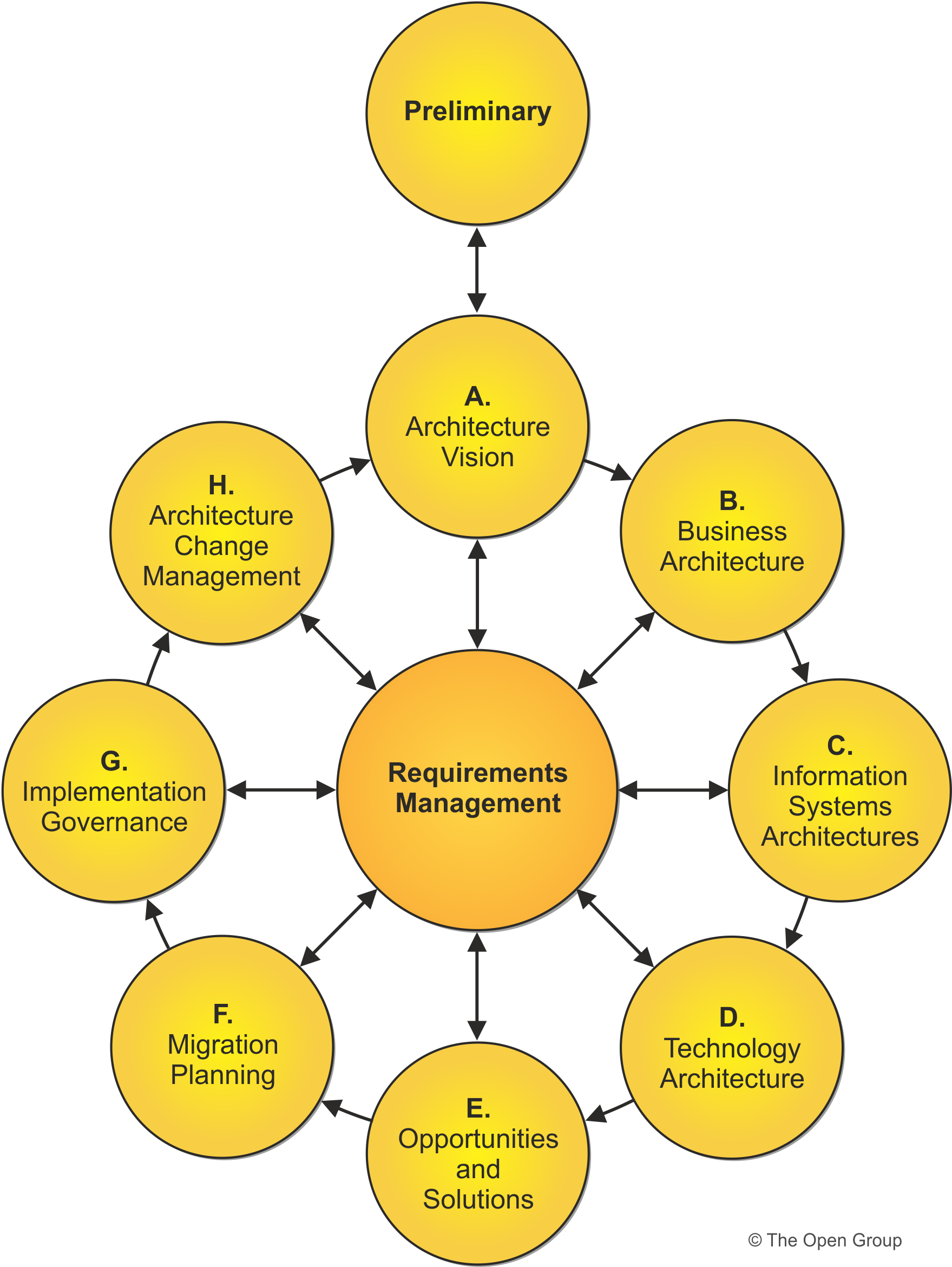
TOGAF Model and
methodology for the development of enterprise architectures developed by The Open Group
•
ITIL Processes to allow for IT service management developed by the United Kingdom’s Office of Government Commerce
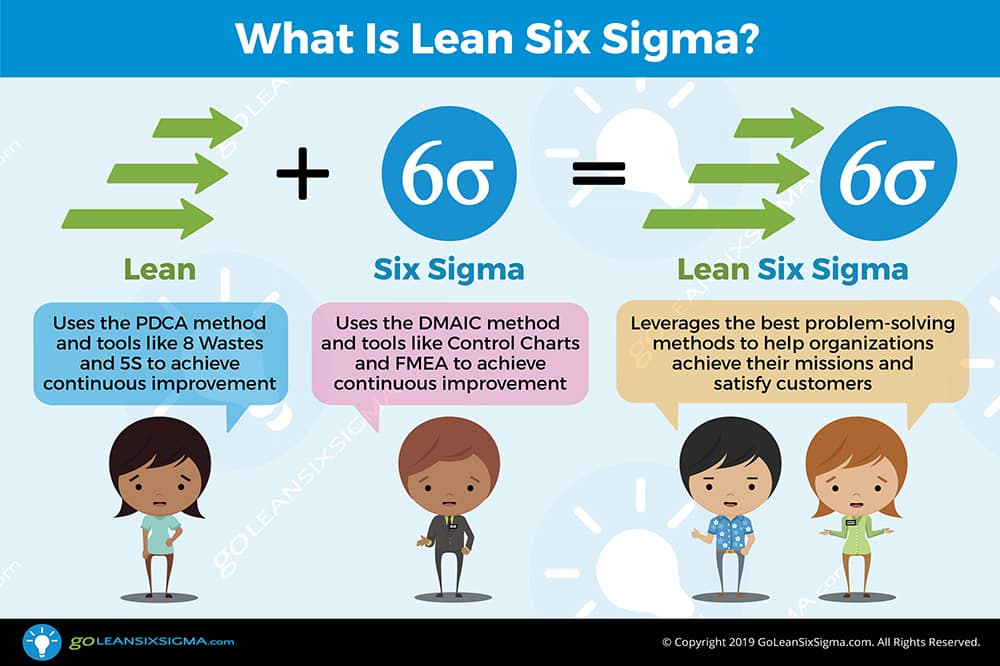
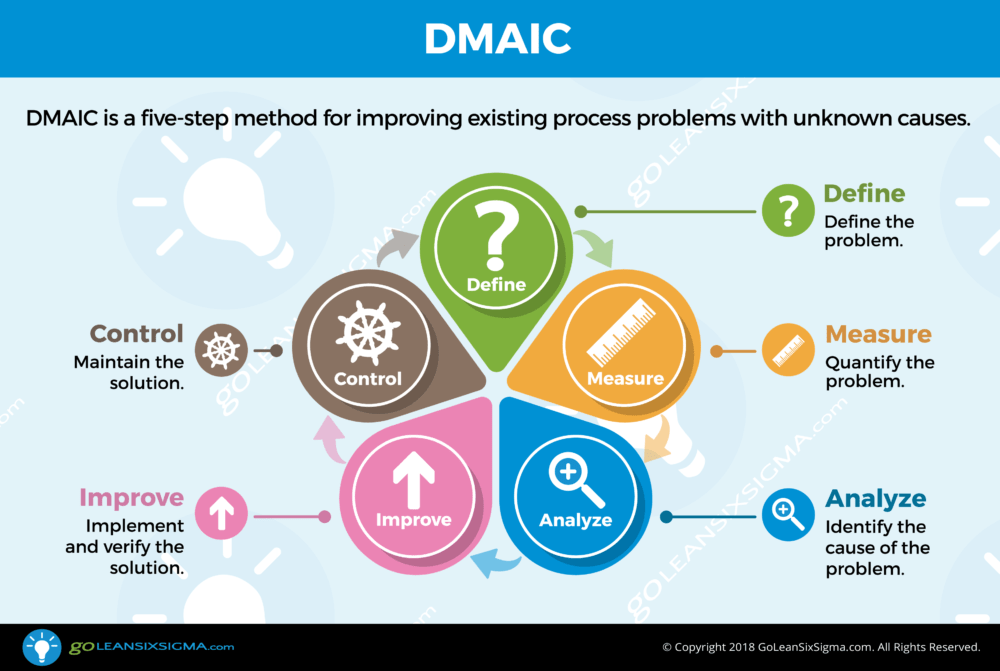
•
Six Sigma Business management strategy that can
be used to carry out process improvement
•
Capability Maturity Model Integration (CMMI) Organizational development for process improvement developed by Carnegie Mellon
General Data Protection Regulation
The European Data Protection Regulation is applicable as of May 25th, 2018 in all member states to harmonize data privacy laws across Europe.
https://gdpr-info.eu/
Maintaining payment security
is required for all entities that store, process or transmit cardholder data.
Guidance for maintaining payment security is provided in PCI security standards.
https://www.pcisecuritystandards.org/pci_security/
FedRAMP simplifies security for the digital age by providing a standardized approach to security for the cloud.
The
FedRAMP Program Management Office (PMO) mission is to promote the adoption of secure cloud services across the Federal Government by providing a standardized approach to security and risk assessment.
https://www.fedramp.gov/
Bringing science to software security
The Building Security In Maturity Model (BSIMM, pronounced “bee
simm”) is a study of existing software security initiatives. By quantifying the practices of
many different organizations, we can describe the common ground shared by many
as well as the variations that make each unique.
BSIMM is not a how-to guide, nor is it a one-size-fits-all prescription. Instead, it
is a reflection of software security.
https://www.bsimm.com/about.html
- BSIMM is made up of a software security framework used to organize the 116 activities used to assess initiatives. The framework consists of 12 practices organized into four domains.
https://www.bsimm.com/framework.html
Beyond ISO Intel's Product Security Maturity Model (PSMM)

Varonis and the Building Security in Maturity Model (BSIMM)
SSAE 16 stands for Statements on Standards for Attestation Engagements No. 16. Effective in mid-2011, this new auditing standard superseded the SAS 70 standard. According to AICPA, the SSAE 16 requires companies, like data centers, to provide a written report that describes
any and all controls at organizations that provide services to customers when those controls are likely to
be relevant to user entities internal control over financial reporting. In
May of 2017, SSAE 16 was super-ceded by SSAE 18.
What Is SSAE 18?
the AICPA’s Auditing Standards Board (ASB) completed the clarity project, the result of which was the issuance of SSAE 18, “Concepts common to all Attestation Engagements”. As the SOC 1 is an attestation engagement, the SSAE 18 standard will apply to SOC 1’s and supersedes the SSAE 16 standard.
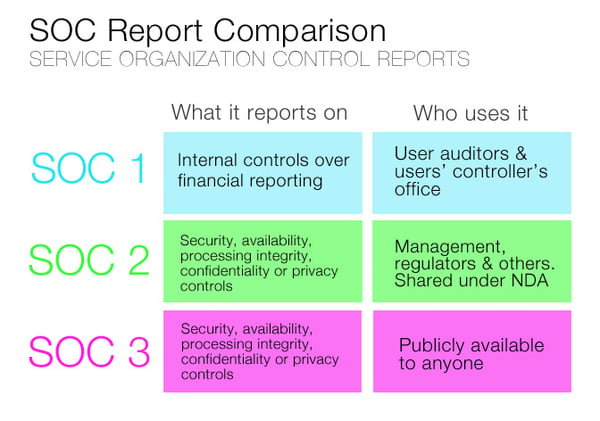
What Is SOC 1?
The SSAE 18 SOC 1, sometimes just stated as SOC 1, is the report you get when you
are audited for SSAE 18. The SOC 1 Type 1 report focuses on a service provider’s processes and controls that could impact their client’s internal control over their financial reporting (ICFR). The examination helps ensure that both the system and personnel responsible for these controls at the third-party provider are doing their job in a manner that will not adversely affect their client’s ICFR. This report is
key with respect to services such as
payroll and taxation since when performed by a third-party
provider, such services will have a direct impact on a client’s ICFR. For example, if you outsource payroll management to a provider that doesn’t have the proper controls in place, you risk payroll errors in your internal data. This will come with problematic consequences since
, in the end, you will be held accountable for those errors.
What Is SOC 2?
The SOC 2 is a separate report that focuses on controls at a service provider relevant to security, availability, processing integrity, confidentiality, and privacy of a system. It ensures that
your data is kept private and secure while in storage and in transit and that it is available for you to access
at any time.
This is a crucial report for any
type of data
that you entrust with a third-party provider, whether it includes large video files or confidential medical records.
If you use a third-party CRM provider, for instance, the SOC 2 report will verify the provider’s ability to keep the records online and the identity of your customers secure and in line with your own Privacy Policy.
The SOC 1 and SOC 2 reports come in two forms: Type I and Type II. Type I
reports evaluating whether proper controls are in place at a specific point in time.
Type II reports are done over
a period of time to verify operational efficiency and effectiveness of the controls.
https://www.
atlantic.net/hipaa-compliant-hosting/ssae-16-soc-1-soc2-care/
Certified Information Systems Auditor (CISA) is a professional certification for Information Technology Audit professionals sponsored by ISACA, formerly the Information Systems Audit and Control Association. Candidates for the certification must meet requirements set by ISACA on educational qualification and professional experience.
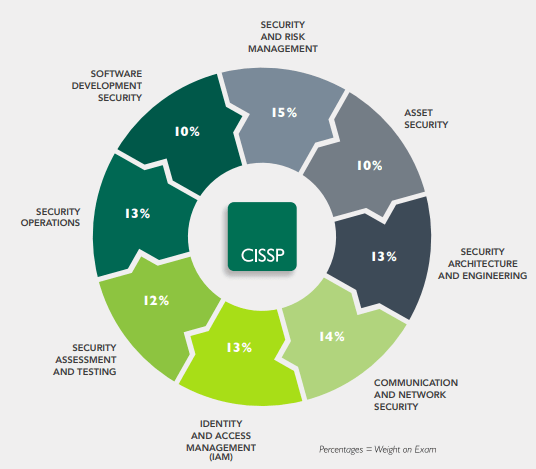
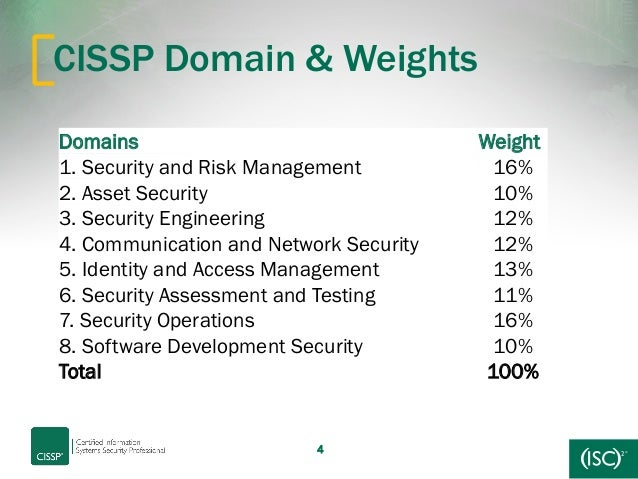
- CISSP® - Certified Information Systems Security Professional
The vendor-neutral CISSP certification is the ideal credential for those with proven deep technical and managerial competence, skills, experience, and credibility to design, engineer, implement, and manage their overall information security program to protect organizations from growing sophisticated attacks.
https://www.isc2.org/cissp/default.aspx
Certified Information Security Manager (CISM) is a certification for information security managers awarded by ISACA (formerly the Information Systems Audit and Control Association)
Why Employers Hire CISMs?
Enterprises and government agencies increasingly recognize, require and expect
their IS and IT professionals to hold CISM certification.
CISM employees:
Identify critical issues and customize company-specific practices to support the governance of information and related technologies
Bring credibility to the enterprise for which
they are employed
Take a comprehensive view of information systems security management and their relationship to organizational success
Demonstrate to enterprise customers their commitment to compliance, security and integrity; ultimately contributing to the attraction and retention of customers
Ensure that there
is improved alignment between the organization's information security program and its broader goals and objectives
Provide the enterprise with a certification for Information security management that
is recognized by multinational clients and enterprises, lending credibility to the enterprise
http://www.isaca.org/Certification/CISM-Certified-Information-Security-Manager/What-is-CISM/Pages/default.aspx
- Certified in Risk and Information Systems Control (CRISC)
Why Employers Hire CRISCs
CRISCs bring additional professionalism to any organization by
demonstrating a quantifiable standard of knowledge, pursuing continuing education, and adhering to a standard of ethical conduct established by ISACA.
CRISC employees:
Build greater understanding about the impact of IT risk and how it relates to the overall organization
Assure development of more effective plans to mitigate risk
Establish a common perspective and language about IT
risk that can set the standard for the enterprise
ISACA draws on a global network of leading professionals to develop its certification programs. With access to experts around the world, ISACA is defining how IT risk
is managed in current and future business environments.
http://www.isaca.org/Certification/CRISC-Certified-in-Risk-and-Information-Systems-Control/What-is-CRISC/Pages/The-Benefits-of-CRISC.aspx
Certified Information Systems Security Professional (CISSP) is an independent information security certification governed by International Information Systems Security Certification Consortium
- Global Information Assurance Certification (GIAC) is the leading provider and developer of Cyber Security Certifications.
Global Information Assurance Certification (GIAC) is the leading provider and developer of Cyber Security Certifications. GIAC tests and validates the ability of practitioners in information security, forensics, and software security
https://www.giac.org
ISO/IEC 27001, part of the growing ISO/IEC 27000 family of standards, is an information security management system (ISMS) standard published in October 2005 by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). Its full name is ISO/IEC 27001:2005 – Information technology – Security techniques – Information security management systems – Requirements.
http://en.wikipedia.org/wiki/ISO/IEC_27001
The Federal Information Processing Standard (FIPS) Publication 140-2 is a U.S. government computer security standard used to accredit cryptographic modules
The National Institute of Standards and Technology (NIST) issued the FIPS 140 Publication Series to coordinate the requirements and standards for cryptography modules that include both hardware and software components
Protection of a cryptographic module within a security system is necessary to maintain the confidentiality and integrity of the information protected by the module.
http://en.wikipedia.org/wiki/FIPS_140-2
- what is PCI-DSS certification?
The Payment Card Industry (PCI) Data Security Standard (DSS) is an information security standard defined by the Payment Card Industry Security Standards Council.
PCI certification is required for organizations (merchants) that process credit card payments.
The certification is designed to prevent credit card fraud through increased controls around data and its exposure to compromise
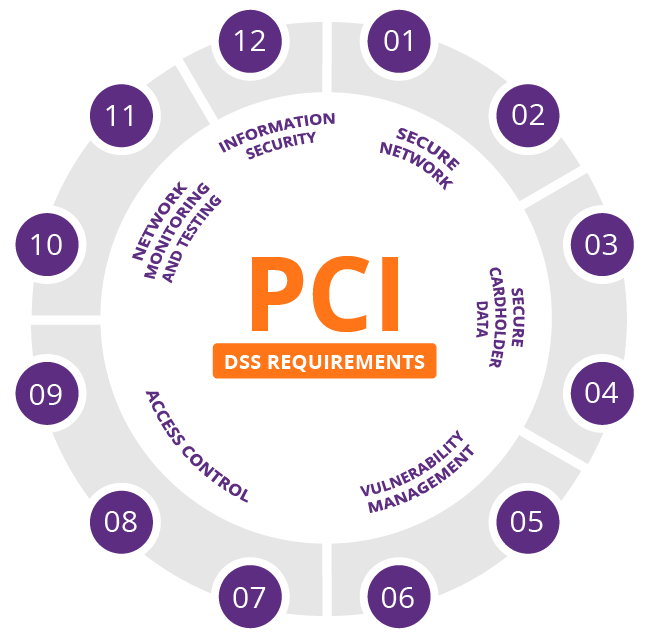
- The PCI Data Security Standard specifies twelve requirements for compliance, organized into six logically related groups called "control objectives".
Each version of PCI DSS has divided these twelve requirements into
a number of sub-requirements differently, but the twelve high-level requirements have not changed since the inception of the standard.
https://en.wikipedia.org/wiki/Payment_Card_Industry_Data_Security_Standard
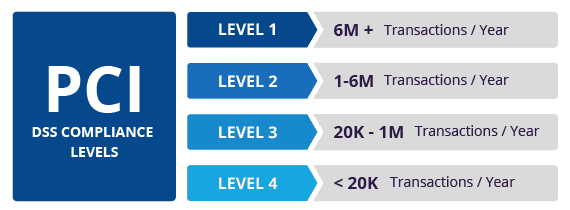
- What is a PCI Validated Service Provider?
Service providers are organizations that process, store, or transmit cardholder data on behalf of clients, merchants, or other service providers.
http://www.commercev3.com/3232/pci-dss-level-1-certification-faq#1
- The PCI Security Standards Council offers robust and comprehensive standards and supporting materials to enhance payment card data security. These materials include a framework of specifications, tools, measurements and support resources to help organizations ensure the safe handling of cardholder information at every step.
www.pcisecuritystandards.org
- The Payment Card Industry Data Security Standard (PCI DSS) is a widely accepted set of policies and procedures intended to optimize the security of credit, debit and cash card transactions and protect cardholders against misuse of their personal information. The PCI DSS was created jointly in 2004 by four major credit-card companies: Visa, MasterCard, Discover and American Express.
- the Critical Infrastructure Protection in the Information Age, re-designating the National Security Telecommunications and Information Systems Security Committee (NSTISSC) as the Committee on National Security Systems
The CNSS defines several standards, which include standards on training in IT security. Current certifications include:
NSTISSI-4011 National Training Standard for Information Systems Security (INFOSEC) Professionals
CNSSI-4012 National Information Assurance Training Standard for Senior Systems Managers
CNSSI-4013 National Information Assurance Training Standard For System Administrators
CNSSI-4014 Information Assurance Training Standard for Information Systems Security Officers
NSTISSI-4015 National Training Standard for Systems Certifiers
CNSSI-4016 National Information Assurance Training Standard For Risk Analysts
https://en.wikipedia.org/wiki/Committee_on_National_Security_Systems
- The Gramm-Leach-Bliley Act (GLB Act or GLBA) is also known as the Financial Modernization Act of 1999. It is a United States federal law that requires financial institutions to explain how they share and protect their customers’ private information. To be GLBA compliant, financial institutions must communicate to their customers how they share the customers’ sensitive data, inform customers of their right to opt-out if they prefer that their personal data not be shared with third parties, and apply specific protections to customers’ private data in accordance with a written information security plan created by the institution
BENEFITS OF GLBA COMPLIANCE
Private information must be secured against unauthorized access.
Customers must be notified of private information sharing between financial institutions and third parties and
have the ability to opt out of private information sharing.
User activity must be tracked, including any attempts to access protected records.
https://digitalguardian.com/blog/what-glba-compliance-understanding-data-protection-requirements-gramm-leach-bliley-act
- Recapping the End of Safe Harbor
Safe Harbor refers to the set of principles developed between 1998 and 2000, which
were designed to ensure the EU sufficient data security while maintaining open transport for data and commerce for the U.S. There were 7 principles outlined in this agreement that U.S. companies
were required to comply with, and they included:
Notice:
The purpose behind data collection and usage must be fully disclosed.
Choice: Opt-out opportunities must
be provided to all individuals, and sensitive information must require an opt-in.
Onward Transfer: All future data transfers must follow Safe Harbor Privacy Principles or another comparable directive.
Security: Information must
be adequately protected.
Data Integrity: All personal data gathered must be relevant, and the data’s reliability should
be verified.
Access: If an individual’s personal information has
been gathered, they must
have the right to access and
modify or remove inaccurate information.
Enforcement: The compliance of these rules by each organization must be
feasible – with sanctions readily available to
be handed out to those who do not follow through on their data privacy commitments.
Moving on to GDPR
After the grace period for Safe Harbor was up, the act that
was put into place was the General Data Protection Regulation, or GDPR. The main aim of this was to give control back to European citizens over their personal data, while also simplifying the regulatory environment for international businesses.
https://www.nefiber.com/blog/gdpr-changes-safe-harbor-mean-businesses/
- NIST SP800-171 or just 800-171 is a codification of the requirements that any non-Federal computer system must follow in order to store, process, or transmit Controlled Unclassified Information (CUI) or provide security protection for such systems. This document is based on the Federal Information Security Management Act of 2002 (FISMA) Moderate level requirements.
https://www.cmu.edu/iso/compliance/800-171/index.html
- What is DFARS and NIST SP 800-171?
It was published as a Defense Federal Acquisition Regulation Supplement, or the cyber DFARS clause 252.204-7012
The NIST Special Publication 800-171 requirement
was developed to ensure that those working
in conjunction with Department of Defense would have methods in place to protect sensitive information.
https://www.cybersaint.io/the-definitive-guide-to-dfars-compliance-and-nist-sp-800-171
- All DoD contractors that process, store or transmit Controlled Unclassified Information (CUI) must meet DFARS minimum security standards or risk losing their DoD contracts.
DFARS provides a set of adequate security controls to safeguard information systems where contractor data
resides. Based on NIST Special Publication 800-171 “Protecting Controlled Unclassified Information in Non-Federal Information Systems and Organizations”, manufacturers must implement these security controls through all levels of their supply chain.
https://www.nist.gov/mep/cybersecurity-resources-manufacturers/dfars-compliance
- CMMC stands for “Cybersecurity Maturity Model Certification”. The CMMC will encompass multiple maturity levels that ranges from “Basic Cybersecurity Hygiene” to “Advanced/Progressive”. The intent is to incorporate CMMC into Defense Federal Acquisition Regulation Supplement (DFARS) and use it as a requirement for contract award.
https://www.acq.osd.mil/cmmc/faq.html
The CMMC model framework organizes processes and cybersecurity best practices into a set of domains. For each of the 17 domains, there are processes that span five levels of cybersecurity maturity. Additionally, each of the domains contain one or more capabilities spanning the five levels. And, for a given capability, there are one or more practices that must be demonstrated.
The 17 Domains
Each domain is comprised of processes and capabilities across the five levels. The domains include:
Access Control (AC)
Asset Management (AM)
Awareness and Training (AT)
Audit and Accountability (AU)
Configuration Management (CM)
Identification and Authentication (IA)
Incident Response (IR)
Maintenance (MA)
Media Protection (MP)
Personnel Security (PA)
Physical Protection (PE)
Recovery (RE)
Risk Management (RM)
Security Assessment (CA)
Situational Awareness (SA)
System and Communication Protection (SC)
https://www.mstech.com/cmmc-version-one/
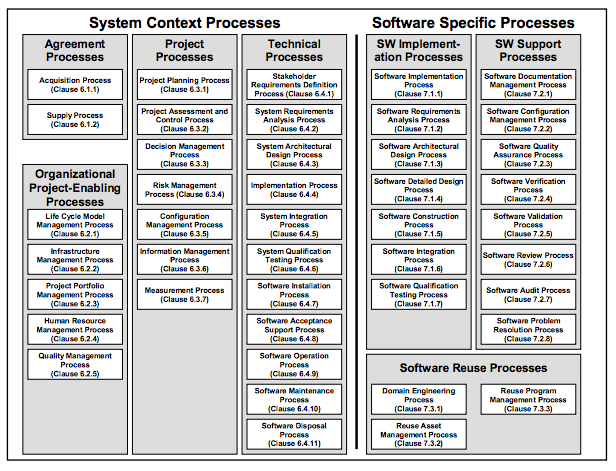
The ISO/IEC 15288 is a systems engineering standard covering processes and
lifecycle stages.
https://en.wikipedia.org/wiki/ISO/IEC_15288
- A software development process, also known as a software development life cycle (SDLC), is a structure imposed on the development of a software product.
Similar terms include software life cycle and software process
It is often considered a subset of systems development life cycle.
ISO/IEC 12207 is an international standard for software life-cycle processes
Software life cycle processes is an international standard for software
lifecycle processes.
https://en.wikipedia.org/wiki/ISO/IEC_12207