- WAN Optimization Protocol Spoofing
Protocol Spoofing is an essential part of data communications that helps to enhance performance
Protocol spoofing evolved in the 1980s and is used as a data compression technique to improve throughput levels and
thereby increase performance.
While used as a data compression technique, the protocol headers and trailers are
either removed completely or cut down, and finally reconstructed at the end points
The technique of protocol spoofing involves communication devices (modem, router), host machines, compatible remote devices and communication links
Spoofing, in computer security, pertains to different
forms of data falsification or misrepresentation. The forgery of headers to send out misleading information is a form of spoofing. While protocol spoofing
generally refers to the method of enhancing performance, there are many other types of protocol spoofing that perform different functions
â€
“ both
advantageous and disadvantageous
Transmission Control Protocol (TCP) Spoofing
TCP spoofing enables to reduce transmission delays and performance limitation due to
higher bandwidth. The algorithm used by TCP
greatly causes delays in connections during startup. TCP spoofing involves a spoofing router, which
terminates the local TCP connection and interprets the TCP to protocols that
have the capacity to reduce long delays across satellite links.
File Transfer Spoofing
File Transfer Protocols and Error Correction Protocols operate through computing and assigning a checksum for a data packet
RIP/SAP Spoofing
RIP and SAP are used for broadcasting network information
in a periodic way.
The other
types of spoofing techniques that
are involved in misrepresentation of information are Address Resolution Protocol (ADP) Spoofing, Internet Protocol (IP) Address Spoofing, etc.
Those protocol spoofing techniques that adversely affect the users can
be controlled by using counter methods such as packet filtering, egress filtering,
data authorization and other techniques.
https://www.wanoptimization.org/protocol_spoofing.php
- WAN optimization (WAN acceleration)
WAN optimization, also known as WAN acceleration, is the category of technologies and techniques used to maximize the efficiency of data flow across a wide area network (WAN).
WAN optimization encompasses:
traffic shaping, in which traffic
is prioritized and bandwidth
is allotted accordingly.
data
deduplication, which reduces the data that must
be sent across a WAN for remote backups, replication, and disaster recovery.
compression, which shrinks the size of data to limit bandwidth use.
data caching, in which frequently used data
is hosted locally or on a local server for faster access.
monitoring the network to detect non-essential traffic.
creating and enforcing rules about downloads and Internet use.
protocol spoofing, which is a method of bundling chatty protocols so they are
, in effect, a single protocol.
https://searchnetworking.techtarget.com/definition/WAN-optimization-WAN-acceleration
- How WAN Optimization Works
WAN performance issues
Latency: This is the back-and-forth time resulting from chatty applications and protocols, made worse by
distance over the WAN. One server sends packets, asks if the other server received it, the other server answers, and back and forth they go. This
type of repeated communications can happen 2,000 to 3,000 times just to send a single 60MB Microsoft PowerPoint file. A somewhat simple transaction can introduce latency from 20 ms to 1,200 ms per single file transaction.
TCP window size: Adding more bandwidth won’t
necessarily improve WAN performance. Your TCP window size limits throughput for each packet transmission. While more bandwidth may give you a bigger overall pipe to handle more transactions, each specific transaction can only go through a smaller pipe, and that often slows application performance over the WAN.
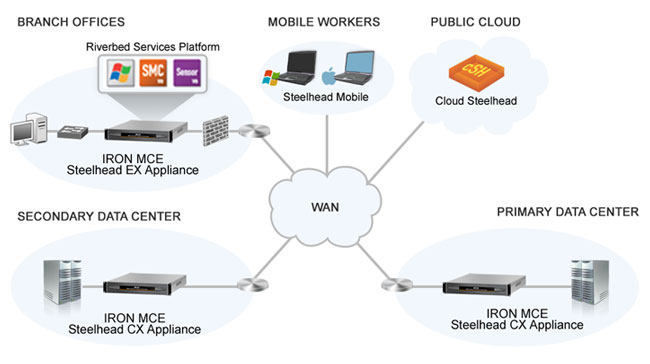
SteelHead is a bookend technology in which one Steelhead sits at the data center and another at the edge. SteelHead works with any WAN because it sits behind routers, which
terminate the WAN at each end.
The
bookended SteelHead analyzes each packet as it
goes on and off the routers.
SteelHead,
utilizes a combination of three technologies to boost WAN performance.
#1. Data streamlining
Don’t resend redundant data: A process known as data de-duplication removes bytes from the WAN. Data that
is accessed repeatedly by users over the WAN is not repeatedly resent
Scalable data referencing looks at data packets: Let’s say a user downloads a document from a file server. At the sending and receiving locations, SteelHead sees the file and breaks the document into packets and stores them. Then the user
modifies the document and emails it back to 10 colleagues at the file’s original location.
In this case the only data sent over the WAN are the small changes made to the document and the 16-byte references that tells the SteelHead device at the other end how to reassemble the document.
SteelHead cares about data: Data is data to SteelHead, no matter what format or application it comes from. That means far less of it needs to
be sent across the WAN. As an example, imagine how many times the words “the” and “a” appear in files from various applications. SteelHead doesn’t care; these bytes look the same and therefore need not
be sent. This
type of de-duplication can remove 65–95% of bytes from being transmitted over the WAN.
#2. Transport streamlining
The fastest round trip is the one you never make: Transport streamlining makes TCP more efficient, which means fewer round trips and data per trip. For example, traditional TCP does what’s known as a “slow start process,” where it sends information in small chunks and keeps sending increasingly larger chunks until the receiving server can’t handle the chunk size. Then it starts again back at square one and repeats the process. Transport streamlining avoids the restart and just looks for the optimal packet size and sends packets only in that size
#3. Application streamlining
Lastly, application streamlining
is specially tuned for a growing list of application protocols including CIFS, HTTP, HTTPS, MAPI, NFS, and SQL.
https://www.riverbed.com/newsletter/how-wan-optimization-works.html
+(Study+Figure).jpg)