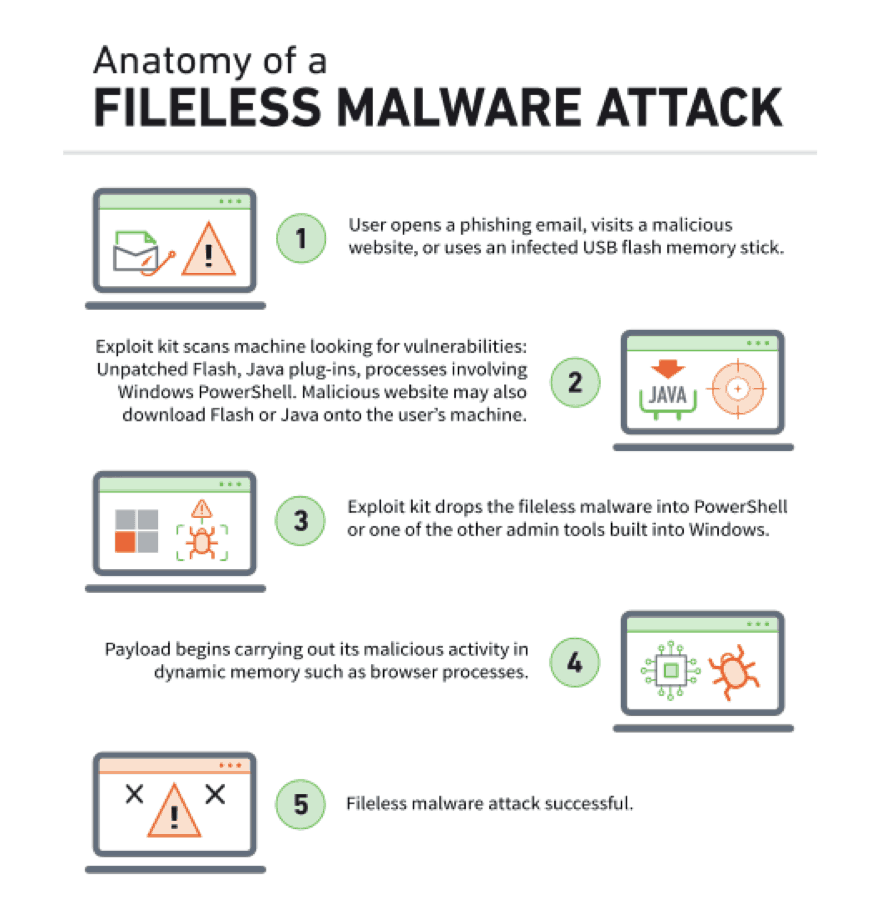
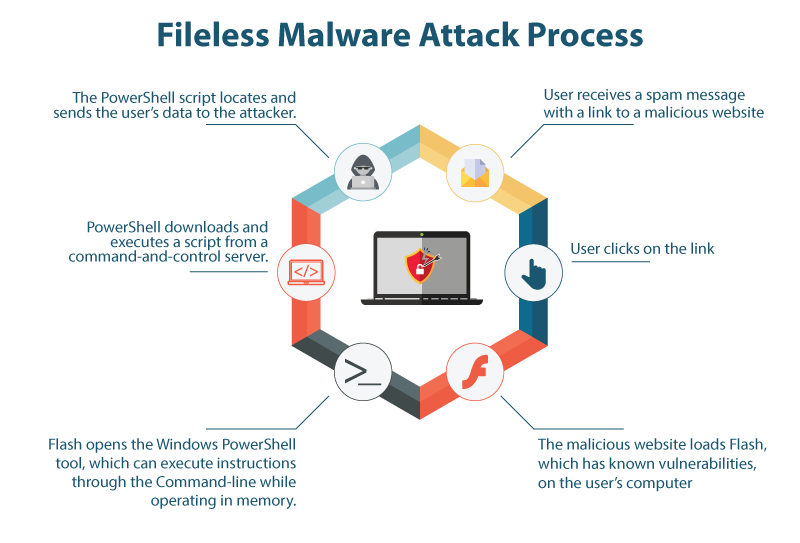
- a new breed of malicious operations utilizing inherent features built into Windows that allow a clever hacker to turn the operating system against itself and compromise entire networks without needing a single piece of software to be installed.
There are two different tools that hackers are
beginning to utilize as a foundation for
fileless malware: Windows Management Instrumentation and
Powershell
The same way an admin uses WMI to query metrics and execute code, a hacker can use it to run malicious code across an entire network of machines. This can
be done silently, instantly, and is undetectable by standard anti-virus as an undesired action.
WMI cannot be uninstalled, it can only
be disabled
This allows attackers
to easily hide by dropping Base64 scrambled or encrypted code directly into
Powershell, automatically decoding it and running it from memory
What makes Powershell even scarier as a tool for hackers is that it can
be run remotely through WinRM, legitimately, allowing attackers
to instantly punch a hole through the Windows Firewall on that compromised endpoint. if
WinRM is turned off it can
be turned on remotely through WMI using a single line of code. Because Powershell is an inherent part of Windows, it
is completely trusted by the machine, ignored by antivirus software and other defense mechanisms. All the attacker needs is access to the
machine, which can be achieved using WMI as shown above
http://www.cybereason.com/fileless-malware-an-evolving-threat-on-the-horizon
- In-Memory Malware is Difficult to Detect
Fileless malware, is reaping a great benefit for hackers and
cyber-criminals and great risk for your business.
Fileless infections are exactly what they seem to be: malware or virus infections that
don’t use any files
in the process.
The malware is written directly into the physical memory (or RAM) and
is capable of eluding most detection technologies such as desktop firewalls and anti-virus programs.
https://digitalguardian.com/solutions/use-case/memory-forensics
- A fileless infection (fileless malware) is malicious coding that exists only in memory rather than installed to the target computer's hard drive.
A tactic we have spotted would
be using fileless malware. Unlike most malware,
fileless malware hides itself in locations
that are difficult to scan or detect.
Fileless malware exists only in memory and
is written directly to RAM instead of being installed in the target computer’s hard drive. POWELIKS is an example of
fileless malware that
is able to hide its malicious code in the Windows Registry. These use a conventional malware file to add the entries with its malicious code in the registry.
http://blog.trendmicro.com/trendlabs-security-intelligence/without-a-trace-fileless-malware-spotted-in-the-wild/
- FILELESS MALWARE 101: UNDERSTANDING NON-MALWARE ATTACKS
Unlike file-based attacks,
fileless malware does not leverage traditional executable files.
Fileless attacks abuses tools that are built-in to the operating system to carry out attacks.
Essentially, Windows is turned against itself.
Without an executable, there is no signature for antivirus software to detect. This is part of what makes
fileless attacks so dangerous - they
are able to easily evade antivirus products.
Fileless attacks use a technique called living-off-the-land. Living-off-the-land is when attackers use legitimate tools for malicious purposes
The abused, legitimate tools
are known as
LOLBins, and can include Microsoft Office Macros,
PowerShell, WMI, and many more system tools.
HOW DOES FILELESS MALWARE WORK?
Fileless malware leverages trusted, legitimate processes (
LOLBins) running on the operating system to perform malicious activities like
lateral movement,
privilege escalation,
evasion,
reconnaissance,
and the delivery of payloads.
REASONS TO USE FILELESS MALWARE IN AN ATTACK
Stealthy:
Fileless malware uses legitimate tools, which means it is almost impossible to
blocklist the tools used in a
fileless attack.
Living-off-the-land: The legitimate tools used for
fileless malware
are installed by default. The attacker
does not need to create or install any custom tools to use them.
Trusted and Frequented: These tools
are frequently used and trusted. It is not unusual to see the tools used in
fileless malware running in an enterprise environment for a legitimate purpose.
LOLBINS LEVERAGED BY FILELESS MALWARE
POWERSHELL
PowerShell is a cross-platform, open source task automation and configuration management framework created by Microsoft.
sThe PowerShell framework, based on
.NET,
is made up of a command-line shell and scripting language.
PowerShell gives full access to many Windows system functions, including WMI and component object model (COM) objects,
as well as management features for the Microsoft Exchange server and others. Further, it
is able to execute payloads directly from memory, which is what enables attackers to leverage it for
fileless malware.
WINDOWS MANAGEMENT INSTRUMENTATION (WMI)
Windows Management Instrumentation (WMI) is a Microsoft standard for accessing management information about devices in an enterprise environment
WHAT IS WMI LEGITIMATELY USED FOR?
WMI is all about the management of Windows devices on a network. It can give you information about the status of local or remote machines, and can
be used to configure security settings like system properties, user groups, scheduling processes, or disabling error logging. WMI is valuable to administrators that need
to easily manage all machines on the network - a task that happens regularly in an enterprise.
.NET is an open source framework, or set of generic, commonly used and editable functionality, made by Microsoft. It has two main components that developers use together to create applications: the Common Language Runtime and the
.NET Framework Class Library.
MACROS
In Microsoft Office, Macros are used to automate frequent tasks.
They are typically created in Word documents or Excel spreadsheets as a series of commands grouped together to complete a task automatically. Many macros
are made using Visual Basic for Applications and can
be written by anyone, including software developer
WHY USE MACROS FOR FILELESS ATTACKS?
Using macros for
fileless attacks is convenient, because
they can easily be combined with phishing campaigns and social engineering techniques to trick a user
WHY IS DETECTION AND PREVENTION OF FILELESS MALWARE CHALLENGING?
Fileless malware depends on tools that are part of the daily workflow of enterprise professionals. Attackers know they can rely on a set of tools that are pre-installed on every Windows machine and are vital for the daily operations of the enterprise.
Fileless malware also decreases the number of files on disk, which means signature-based prevention and detection methods
will not be able to identify them. This makes it
incredibly difficult for an analyst or security product to identify whether the tool is being used for malicious purposes or normal, day-to-day actions. Analysts must have an intimate understanding of their environment to
be able to identify
LOLBins at work.
https://www.cybereason.com/blog/fileless-malware
- What is Fileless Malware?
Fileless malware is a
type of malicious software that uses legitimate programs to infect a computer.
It does not rely on files and leaves no footprint, making it challenging to detect and remove.
it just means that
fileless attacks are often undetectable by antivirus, whitelisting, and other traditional endpoint security solutions.
Fileless attacks fall into the broader category of low-observable characteristics (LOC) attacks, a
type of stealth attack that evades detection by most security solutions and frustrates forensic analysis efforts.
While not considered a traditional virus,
fileless malware
does work in a similar way—it operates in memory.
Without being stored in a file or installed directly on a machine,
fileless infections go straight into memory and the malicious content never touches the hard drive.
How does a
fileless attack happen?
Fileless attacks fall into the broader category of low-observable characteristics (LOC) attacks, a
type of stealth attack that evades detection by most security solutions and frustrates forensic analysis efforts. While not considered a traditional virus,
fileless malware
does work in a similar way—it operates in memory. Without being stored in a file or installed directly on a machine,
fileless infections go straight into memory and the malicious content never touches the hard drive. Many LOC attacks take advantage of Microsoft Windows
PowerShell, a legitimate and useful tool used by administrators for task automation and configuration management.
PowerShell consists of a command-line shell and associated scripting language, providing adversaries with access to just about everything and anything in Windows.
fileless attacks often use social engineering to get users to click on a link or an attachment in a phishing email.
Fileless attacks are typically used for lateral movement, meaning they make their way from one device to the next with the
objective of gaining access rights to valuable data across the enterprise network. To avoid suspicion,
fileless malware gets into the inner recesses of trusted, whitelisted applications (like
PowerShell and Windows script host executables such as
wscript.exe and
cscript.exe) or the operating system to
initiate malicious processes. These attacks abuse the trust model used by security applications to not monitor whitelisted programs.
How can you defend against
fileless attacks?
Microsoft has also upgraded its Windows Defender package to detect irregular activity from
PowerShell.
The real key to successfully counteracting
fileless attacks is an integrated approach that addresses the entire threat
lifecycle. By having a multi-layered defense, you gain an advantage over attackers by being able to investigate every phase of a campaign before, during, and after an attack.
Two things are especially important:
The ability to see and measure what’s happening: discovering the techniques used by the attack, monitoring activities in
PowerShell or other scripting engines, accessing aggregated threat data, and gaining visibility into user activities.
The ability to control the state of the targeted system: halting arbitrary processes, remediating processes that are part of the attack, and isolating infected devices.
Endpoint hardening:
defenses like vulnerability assessment, exploit/memory protection, desktop firewall, and URL filtering.
Machine learning:
security analytic solutions using advanced, adaptive, and state-of-the-art machine learning, deep learning, and artificial intelligence techniques.
Application containment:
whitelisting solution that blocks unauthorized applications and code from running on servers, desktops, and fixed-function devices.
Behavior monitoring:
Understanding user behavior analytics (UBA) helps you identify threats hidden among your data, allowing you to increase security operations accuracy while shortening investigation timelines
.Rather
than focusing
exclusively on users or entities, a combination of anomaly detection and customized rules, along with other intelligent and advanced correlation models.
Interactive threat hunting:
tool that automatically and proactively investigates and responds to abnormal behavior on endpoints and searches for
fileless attack footholds
Single-console centralized management:
a unified platform that provides control, visibility, reporting, and actionable dashboards across hundreds and even thousands of nodes enterprise-wide.
Integration with partner technologies:
protection against specific types of
fileless threats
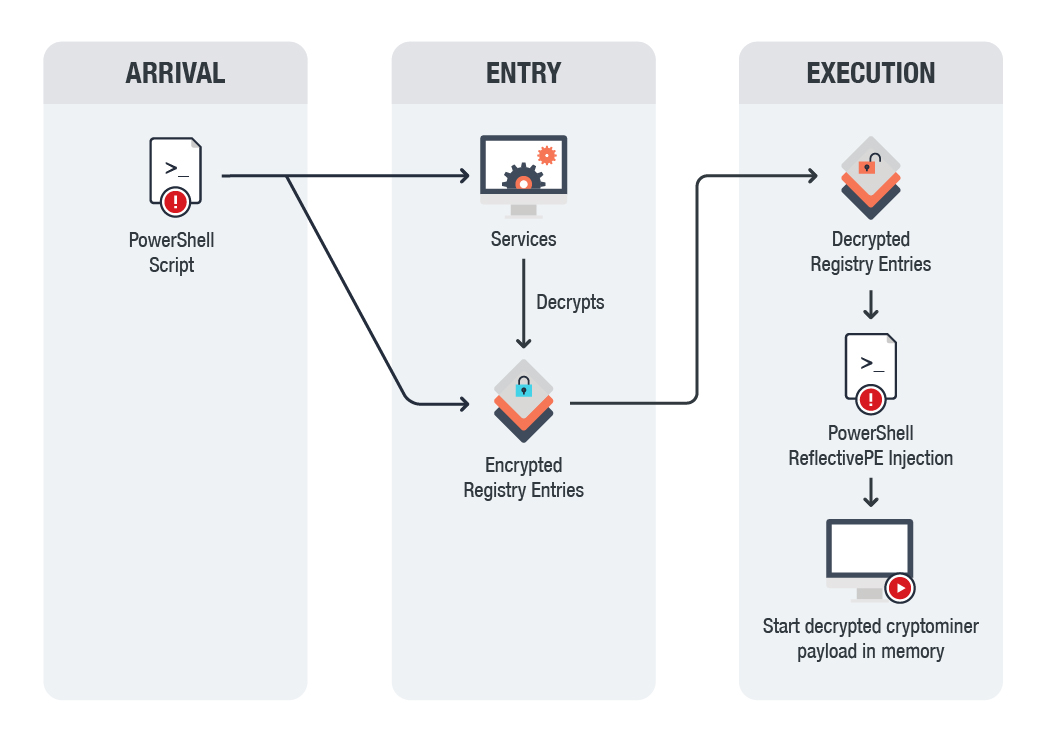
Fileless threat: Reflective self injection:
Reflective loading refers to loading a portable executable (PE) from memory rather than from disk. A crafted function/script can reflectively load portable executable without getting registered as a loaded module in the process and hence can perform actions without leaving footprints. PowerShell is one of the most widely used applications to execute these crafted scripts. This event
indicates a
fileless attack where a PowerShell script tries to inject a PE into the PowerShell process itself.
Fileless threat: Reflective EXE self injection:
This event
indicates a
fileless attack where a PowerShell script tries to inject an EXE into the PowerShell process itself.
Fileless threat: Reflective DLL remote injection:
This event
indicates a
fileless attack where a
PowerShell script tried to inject a DLL into a remote process.
Fileless threat: Malicious code execution using
DotNetToJScript technique:
This event
indicates an attempt to execute malicious
shellcode using the DotNetToJScript technique, which
is used by prevalent
fileless attacks like CACTUSTORCH. DotNetToJScript attack vectors allow loading and execution of malicious
.NET assembly (DLL, EXE, etc.) straight from memory with the help of
.NET libraries exposed via COM. Just like any other typical
fileless attack technique, DotNetToJScript does not write any part of the malicious
.NET DLL or EXE in the computer's hard drive.
https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/what-is-fileless-malware.html