we can use Jenkins for building a project's documentation using Doxygen.
how to configure a Jenkins job for generating a project's documentation using the Jenkins Doxygen Plugin.
we will see another way of building Doxygen documentation using Jenkins, but this time using the Jenkins HTML Publisher Plugin.
http://unix-heaven.org/building-documentation-with-jenkins
Tuesday, December 10, 2013
how to count rows in eclipse
how to count rows in eclipse
\n[\s]*
counting empty lines
\n
\n[\s]*
counting empty lines
\n
Labels:
java interview questions
data storage, data transmission byte/bit conversions
data storage bits/bytes are calculated as follows:
1 byte = 8 bits
1 kilobyte (K / Kb) = 2^10 bytes = 1,024 bytes
1 megabyte (M / MB) = 2^20 bytes = 1,048,576 bytes
1 gigabyte (G / GB) = 2^30 bytes = 1,073,741,824 bytes
1 terabyte (T / TB) = 2^40 bytes = 1,099,511,627,776 bytes
1 petabyte (P / PB) = 2^50 bytes = 1,125,899,906,842,624 bytes
1 exabyte (E / EB) = 2^60 bytes = 1,152,921,504,606,846,976 bytes
Data Transmission conversion (kilobit)
a kilobit is a thousand bits, or 1,000 bits. It's commonly used for measuring the amount of data that is transferred in a second between two telecommunication points. Kilobits per second is usually shortened to Kbps
http://www.beesky.com/newsite/bit_byte.htm
1 byte = 8 bits
1 kilobyte (K / Kb) = 2^10 bytes = 1,024 bytes
1 megabyte (M / MB) = 2^20 bytes = 1,048,576 bytes
1 gigabyte (G / GB) = 2^30 bytes = 1,073,741,824 bytes
1 terabyte (T / TB) = 2^40 bytes = 1,099,511,627,776 bytes
1 petabyte (P / PB) = 2^50 bytes = 1,125,899,906,842,624 bytes
1 exabyte (E / EB) = 2^60 bytes = 1,152,921,504,606,846,976 bytes
Data Transmission conversion (kilobit)
a kilobit is a thousand bits, or 1,000 bits. It's commonly used for measuring the amount of data that is transferred in a second between two telecommunication points. Kilobits per second is usually shortened to Kbps
http://www.beesky.com/newsite/bit_byte.htm
Labels:
Computer Networks
Virtualization
- Desktop Virtualization, VDI
VDI or Virtual Desktop Infrastructure refers to
http://www.citrix.com/virtualization/vdi.html
- virtualization
multiple operating systems on one physical machine
virtual guest machines exist as a file
memory management
availability for disaster recovery
hot migration: move guest
why virtualize? cost
- virtual machine monitor (VMM)
http://searchservervirtualization.techtarget.com/definition/virtual-machine-monitor
What is a VMM?
A VMM virtualizes an entire physical machine
Interface supported is the hardware
OS defines a higher-level interface
VMM provides the illusion that software has full control over the hardware (
VMM “applications” run in virtual machines (c
Implications
You can boot an operating system in a virtual machine
Run multiple instances of an OS on same physical machine
Run different
Linux on Windows, Windows on Mac, etc.
https://www.cs.cmu.edu/~
Paravirtualization
The
https://en.wikipedia.org/wiki/Paravirtualization
Paravirtualization is virtualization in which the guest operating system (the one being virtualized)is aware that it is a guest and accordingly has drivers that, instead of issuing hardware commands, simply issue commands directly to the host operating system. This also includes memory and thread managementas well , which usually require unavailable privileged instructions in the processor.
Full Virtualization is virtualization in which the guest operating system is unaware that it is in a virtualized environment, and therefore hardware
Hardware Assisted Virtualization is a
There is also a combination of Para Virtualization and Full Virtualization called Hybrid Virtualization where parts of the guest operating system use
http://stackoverflow.com/questions/21462581/what-is-the-difference-between-full-para-and-hardware-assisted-virtualiazation
- Desktop virtualization
1.1 Remote desktop virtualization
1.1.1 Virtual desktop infrastructure
1.1.2 Remote desktop services
1.2 Application virtualization
1.3 User virtualization
1.4 Layering
1.4.1 Desktop as a Service
1.5 Local desktop virtualization
Remote desktop virtualization
Remote desktop virtualization implementations operate as a client/server computing environment
Virtual desktop infrastructure
Virtual Desktop Infrastructure (VDI) is a desktop-centric service that hosts user desktop environments on remote servers and/or blade PCs, which
Remote desktop services
Remote Desktop Services (also called terminal services, server based computing, and presentation virtualization) is a component of Microsoft Windows that allows a user to access applications and data on a remote computer over a network using a remote display protocol. Another leading example of presentation virtualization is Citrix XenApp.
Application virtualization
Application virtualization improves delivery and compatibility of applications by encapsulating them from the underlying operating system on which
User virtualization
User virtualization separates
Layering
Desktop layering is a method of desktop virtualization that divides a disk image into logical parts to
Local desktop virtualization
Local desktop virtualization implementations run the desktop environment on the client device using hardware virtualization or emulation
http://en.wikipedia.org/wiki/Desktop_virtualization
- Virtualization
Users don't see the difference between customary computer and terminal, on the contrary all applications usually run faster than on PC.
Thin clients
Desktop virtualization offers an economic gain for business and
More security for corporate data
New work place within 10 minutes
Centralized administration
Decrease in aggregate value
Fewer expenses on upgrades
Energy saving
http://hardpoint.eu/virtualization
- A hypervisor is a thin software layer that intercepts operating system calls to the hardware.
Hypervisors are two types:
Native of Bare Metal Hypervisor and
Hosted Hypervisor
Native or Bare Metal Hypervisor
Native hypervisors are software systems that run directly on the host's hardware to control the hardware and to monitor the Guest Operating Systems.
The guest operating system runs on a separate level above the hypervisor.
Examples of this virtual machine architecture are Oracle VM, Microsoft Hyper-V,
Hosted Hypervisor
While, the guest operating system becomes a third software level above the hardware.
A well-known example of a hosted hypervisor is Oracle VM
https://www.tutorialspoint.com/virtualization2.0/virtualization2.0_overview.htm
- Bare Metal Server
A hypervisor is an operating system that can create virtual machines (VM) within a bare-metal server.
a traditional bare-metal server. The operating system (CentOS,
a bare-metal server installed with a hypervisor provides the user with a management suite to create virtual machines on the server. The hypervisor should not run applications natively; rather, its purpose is to virtualize your workloads into separate virtual machines to gain the flexibility and reliability of virtualization.
http://www.inap.com/2015/02/26/bare-metal-vs-hypervisor/
The term is used
Bare-metal servers are 'physical' servers. Each logical server offered for rental is a distinct physical piece of hardware that is a functional server on its own. They are not virtual servers running in multiple on shared hardware
- Hosted Architecture
• Relies on host OS for device support and physical resource management
Bare-Metal (Hypervisor) Architecture
• Lean virtualization-centric kernel
• Service Console for agents and
https://www.vmware.com/pdf/virtualization.pdf
VMware Compliance Checker for PCI
vCenter Converter
https://www.youtube.com/watch?v=VepgExB_39E
vSphere Hypervisor
- KVM (for Kernel-based Virtual Machine) is a full virtualization solution for Linux on x86 hardware containing virtualization extensions (Intel VT or AMD-V).
KVM (for Kernel-based Virtual Machine) is a full virtualization solution for Linux on x86 hardware containing virtualization extensions (Intel VT or AMD-V). It
Using KVM, one can run multiple virtual machines running unmodified Linux or Windows images. Each virtual machine has private virtualized hardware: a network card, disk, graphics
KVM is
https://www.linux-kvm.org/page/Main_Page
- What is a
VMware vApp ?
A
Container for multiple virtual machines
Resource controls for the VMs inside the container
Network configurations contained inside
Portability of the
Entire
http://www.virtualizationadmin.com/articles-tutorials/vmware-esx-and-vsphere-articles/general/understanding-power-vmware-vapps.html
oVirt is a complete virtualization management platform, licensed and developed as open source software.oVirt builds on the powerful kernel based virtual machine (KVM hypervisor) and on the RHEV-M management server, released by Red Hat to the open source community.
https://www.ovirt.org/
Proxmox VE is acomplete open-source platform for enterprise virtualization.
- Microsoft Hyper-V Server
http://www.microsoft.com/en-us/server-cloud/hyper-v-server/default.aspx
VMware ESX
http://www.vmware.com/products/vsphere/esxi-and-esx/overview.html
- Citrix
XenServer
As a true virtual computing solution,
http://www.citrix.com/English/ps2/products/product.asp?contentID=683148
XenServer is the leading open source virtualization platform, powered by theXen Project hypervisor and the XAPItoolstack . I
https://xenserver.org/
- Parallels Desktop for Mac
Parallels Desktop for Mac is the most tested, trusted and talked-about
http://www.parallels.com/products/desktop/
- Veeam Backup & Replication for
VMware and Hyper-V
Veeam® Backup & Replication™ provides
http://www.veeam.com/vmware-esx-backup.html
- Virtual Machines (VMs)
What is a virtual machine (VM)?
virtual machines (VMs)—virtualized, software representations of a computer that can offer increased portability, flexibility, and security.
VMs changed all that by imitating a physical computer in software
A VM cannot interact directly with a physical computer. Instead, it needs a lightweight software layer called a hypervisor to coordinate between it and the underlying physical hardware. The hypervisor allocates physical computing resources—such as processors, memory, and storage—to each VM. It keeps each VM separate from others so they don’t interfere with each other.
Advantages and benefits
Lower hardware costs and improved ROI
Portability
Flexibility
Security
Hypervisors
There are two types of hypervisors.
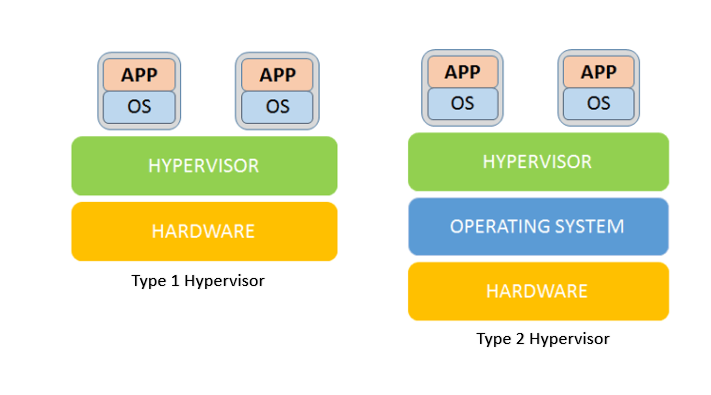
Type 1 hypervisors
Type 1 hypervisors run directly on the physical hardware (usually a server), taking the place of the OS.
Typically, you use a separate software product to create and manipulate VMs on the hypervisor. Some management tools, like
Type 2 hypervisors
Type 2 hypervisors run as an application within a host OS and usually target single-user desktop or notebook platforms.
With a Type 2 hypervisor, you manually create a VM and then install a guest OS in it. You can use the hypervisor to allocate physical resources to your VM, manually setting the amount of processor cores and memory it can use.
Types of VMs
Windows virtual machines
Most hypervisors support VMs running the Windows OS as a guest. Microsoft’s Hyper-V hypervisor comes as part of the Windows operating system.
When installed, it creates a parent partition containing both itself and the primary Windows OS, each of which gets privileged access to the hardware. Other operating systems, including Windows guests, run in child partitions that communicate with the hardware via the parent partition.
Android virtual machines
Google’s open-source Android OS is common on mobile devices and connected home devices such as home entertainment devices. The Android OS runs only on the ARM processor architecture
This is problematic because PCs run on an entirely different x86 processor architecture
Some projects, such as Shashlik or
the Android-x86 project,
Another alternative,
Mac virtual machines
Apple only allows its
iOS virtual machines
It is not possible to run iOS in a VM today because Apple strictly controls its iOS OS and doesn’t allow it to run on anything other than iOS devices
Java virtual machines
The JVM, therefore, doesn’t run an entire OS and doesn’t use a hypervisor as other VMs do. Instead, it translates application-level software programs to run on particular hardware.
Python virtual machines
Like the JVM, the Python VM doesn’t run on a hypervisor, and it doesn’t contain a guest OS. It is a tool that enables programs written in the Python programming language to run on a variety of
Similar to Java, Python translates its programs into an intermediate format called
Linux virtual machines
Linux is a common guest OS used in many VMs. It is also a common host OS used to run VMs and even has its own hypervisor called the kernel-based virtual machine (KVM)
Cloning a
Cloning a
Backing up a
Backing up a
Use cases
VMs have several uses
Support DevOps: VMs are a great way to support enterprise developers, who can configure VM templates with the settings for their software development and testing processes. They can create VMs for specific tasks such as static software tests, including these steps in an automated development workflow.
Test a new operating system:
Investigate malware:
Run incompatible
Browse securely: Using a virtual machine for browsing enables you to visit sites without worrying about infection. You can take a snapshot of your machine and then roll back to it after each browsing session. This is something that a user could set up themselves, using a Type 2 desktop hypervisor. Alternatively, an admin could provide a temporary virtual desktop
How to set up and use
Installation on a desktop-based Type 2 hypervisor involves creating a VM using the program’s application menu. Some systems, such as Parallels, use an installation assistant that will download an OS like Windows 10 or a range of Linux systems and set up the VM for you behind the scenes.
Others—like
Server-based hypervisors usually feature a management console that helps you create a VM. For example,
Use and host in the cloud
Alternatively, you can use a cloud enterprise management system like
Virtual machines as a server
When using a full-featured enterprise VM management system, you can move VM servers between different physical hosts to help balance physical resources with computing demand. It is even possible to move VMs between on-premises physical servers and cloud-based servers to take advantage of the extra computing and storage resources in the cloud when necessary.
VMs vs. containers
Like VMs, containers enable you to run many applications on a single physical server. The difference is that they don’t virtualize an entire computer, and they don’t contain an entire guest OS. Neither do they use a hypervisor, as VMs do.
All containers share the core services of a single underlying OS. They contain only the application they need to run, along with its specific software dependencies, such as software libraries and environment variables. This makes them lightweight, requiring less storage than a VM.
Containers have a downside, though. Sharing a single underlying OS makes them less secure than VMs because a compromise or failure in one container could affect the OS and other containers that rely on it. Running containers on VMs can mitigate this danger by limiting the risk to a single VM.
VMs vs. Docker
Docker Engine, the program that creates and runs Docker containers, can also run on VMs running on local Windows or
You can use the Docker Machine tool to install and coordinate Docker Engine on VMs. Docker Machine uses its own custom lightweight Linux distribution called boot2docker when creating Docker-capable VMs on
VMs vs.
offers administrators a way to define, deploy, and maintain containers in large enterprise environments.
One way to improve the security of a Kubernetes installation is to use containers developed from the ground up to offer the isolation of VMs while maintaining the small footprint and agile deployment of containers. Two projects—Kata and
Gaming
Many video gamers like to play games that run on operating systems other than their primary OS. One option is to run a guest OS on a VM in a Type 2 hypervisor that itself runs as an application within the host OS
A more promising development is cloud-based gaming, which uses a specially configured virtual desktop OS in the cloud to run desktop video games.
Security
Administrators can improve VM security by using security tools from the hypervisor vendor or a third party. For example,
https://www.ibm.com/cloud/learn/virtual-machines
- Type 1 hypervisor
A Type 1 hypervisor runs directly on the underlying computer’s physical hardware, interacting directly with its CPU, memory, and physical storage.
Type 1 (or bare-metal) hypervisor
Type 2 hypervisor
A Type 2 hypervisor doesn’t run directly on the underlying hardware. Instead, it runs as an application in an OS. Type 2 hypervisors rarely show up in server-based environments. Instead, they’re suitable for individual PC users needing to run multiple operating systems. Examples include engineers, security professionals analyzing malware, and business users that need access to applications only available on other software platforms.
Cons: A Type 2 hypervisor must access computing, memory, and network resources via the host OS, which has primary access to the physical machine. This introduces latency issues, affecting performance. It also introduces potential security risks if an attacker compromises the host OS because they could then manipulate any guest OS running in the Type 2 hypervisor.
Type 2 hypervisor
Workstation:
https://www.ibm.com/cloud/learn/hypervisors
Labels:
cloud computing
Subscribe to:
Posts (Atom)