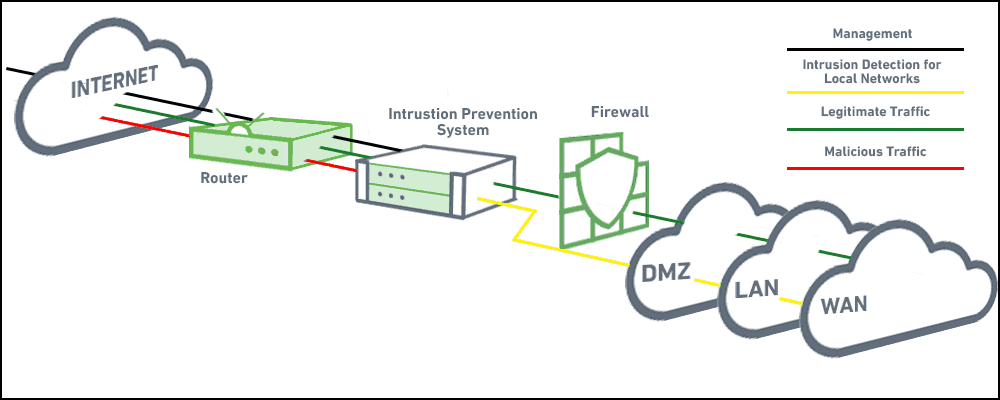
- Layer 7 DDoS attack (L7 DDoS attack)
Layer 7 DDoS attacks are some of the most difficult attacks to mitigate against because they mimic human behavior as they interact with the user interface. For example, some types of Layer 7 DDoS attacks will target website elements, like your logo or a button, and repeatedly download resources hoping to exhaust the server.
Here are some of the ways to stop a DDoS attack:
Block spoofed TCP attacks before they enter your network.
Don’t let dark address packets pass your perimeter.
Block unused protocols and ports.
Limit the number of access per second per source IP.
Limit numbers of concurrent connections per source IP.
Filter foreign TCP packets.
Do not forward packets with header anomalies.
Monitor self-similarity in traffic.
Keep unwanted guests away.
Use specialized DDoS mitigation equipment.
http://ddosattackprotection.org/blog/layer-7-ddos-attack/
- To understand what a layer 7 DDoS attack is you must first understand what is meant by the application layer.
There are seven layers in total, each fulfilling its own purpose in a connected networking framework called the Open System Interconnection Model. The short version being referred to as the OSI Model.
http://ddosattackprotection.org/blog/wp-content/uploads/2013/12/OSI-Model.jpg
the breakdown of the function of each layer
http://ddosattackprotection.org/blog/wp-content/uploads/2013/12/OSI-Layer-Functions.jpg
- There are three types of DDoS attacks
Layer 3 / 4 DDoS attacks
The majority of DDoS attacks focus on targeting the transport and network layers. These types of attacks are usually comprised of volumetric attacks that aim to overwhelm the target machine, denying or consuming resources until the server goes offline. In these types of DDoS attacks, malicious traffic (TCP / UDP) is used to flood the victim. Taking it one step further, these attacks also drive to saturate the entire network with malicious traffic until it is rendered temporarily obsolete. While these types of attacks can be a disruptive force for businesses, once the attack ceases or has been mitigated, there is no lasting damage.
http://ddosattackprotection.org/blog/layer-7-ddos-attack/
Websites are vulnerable to DDoS because of the way machines communicate online.
SYN Flood
UDP Flood
Reflected Attack
Nuke
Slowloris
Peer-to-Peer Attacks
Unintentional DDoS
Degradation of Service Attacks
Application Level Attacks
Multi-Vector Attacks
Zero Day DDoS
http://ddosattackprotection.org/blog/types-of-ddos-attacks/
- Layer 4 vs Layer 7 DoS Attack
A Layer 7 DoS attack is often perpetrated through the use of HTTP GET. This means that the 3-way TCP handshake has been completed, thus fooling devices and solutions which are only examining layer 4 and TCP communications. The attacker looks like a legitimate connection and is therefore passed on to the web or application server. At that point, the attacker begins requesting large numbers of files/objects using HTTP GET.
When rate-limiting was used to stop this type of attack, the bad guys moved to use a distributed system of bots (zombies) to ensure that the requests (attack) was coming from myriad IP addresses and was therefore not only more difficult to detect, but more difficult to stop. The attacker uses malware and trojans to deposit a bot on servers and clients, and then remotely includes them in his attack by instructing the bots to request a list of objects from a specific site or server. The attacker might not use bots but instead might gather enough evil friends to launch an attack against a site that has annoyed them for some reason.
Layer 7 DoS attacks are more difficult to detect because the TCP connection is valid and so are the requests. The trick is to realize when there are multiple clients requesting large numbers of objects at the same time and to recognize that it is, in fact, an attack.
Defending against Layer 7 DoS attacks usually involves some sort of rate-shaping algorithm that watches clients and ensures that they request no more than a configurable number of objects per time period, usually measured in seconds or minutes. If the client requests more than the configurable number, the client's IP address is blacklisted for a specified time period and subsequent requests are denied until the address has been freed from the blacklist.
https://devcentral.f5.com/articles/layer-4-vs-layer-7-dos-attack
- these types of DDoS attacks require less bandwidth to take the site down and are harder to detect and block.
To be more exact, he was getting 5,233 HTTP requests every single second. From different IP addresses around the world. The client’s website was built on WordPress. The uniqueness of the requests was bypassing the caching system, forcing the system to render and respond to every request.
here is a quick geographic distribution of the IP’s hitting the site. This is for 1 second in the attack. Yes, every second these IP’s were changing.
By default, they were not passing our anomaly check, causing the requests to get blocked at the firewall. One of the many anomalies we look for are valid user agents, and if you look carefully you see that the requests didn’t have one. Hopefully, you’ll also notice that the referrers were dynamic and the packets were the same size, another very interesting signature. This triggered one of our rules, and within minutes his site was back and the attack blocked.
After we blocked the original requests and banned the IP addresses involved, everything went quiet, at least for a day. In less than 24 hours though, the attacks resumed with a higher intensity. Remember the caching bypass discussion above? Well, it happened again, and this time it wasn’t blocked automatically as it was operating as a wolf in sheep’s skin.
What the logs show us is that the attack was doing random searches for dictionary keywords (eg: news, gov, faith, etc ). This time they were using a valid browser (Firefox, Chrome, Safari, etc), user agents, and a valid referrer.
You see, they were leveraging normal user search habits. How do you block valid search requests without blocking valid users?
we noticed another anomaly, or what we’d classify as a signature in the new DDoS pattern. The attacker was rotating IP’s within a few seconds of each other, rotating referrers and user agents, all the while performing search requests. Finally, something we could build a rule for, thanks for that. Now each time we see the same IP with a different user agent/referrer within a small period of time, we’re able to block access. Within minutes, the attack was contained.
How we’re able to do this comes down to the technology around our Website Firewall. Just in the block list created by our log correlation tool, we banned 9,673 IP Addresses in the first few hours. During the following days, the list grew to almost 40,000 different IP addresses. That’s quite a respectable botnet.
https://blog.sucuri.net/2014/02/layer-7-ddos-blocking-http-flood-attacks.html
Attack Possibilities by OSI Layer
possible DDoS Traffic Types
Some DDoS Mitigation Actions and Hardware
Stateful inspection firewalls
Stateful SYN Proxy Mechanisms
Limiting the number of SYNs per second per IP
Limiting the number of SYNs per second per destination IP
Set ICMP flood SCREEN settings (thresholds) in the firewall
Set UDP flood SCREEN settings (thresholds) in the firewall
Rate limit routers adjacent to the firewall and network
https://www.us-cert.gov/sites/default/files/publications/DDoS%20Quick%20Guide.pdf
- a valuable part of a DDoS attack mitigation solution. These features address a DDoS attack both by regulating the incoming traffic and by controlling the traffic as it is proxied to backend servers. It’s important not to assume that this traffic pattern always represents a DDoS attack. The use of forwarding proxies can also create this pattern because the forward proxy server’s IP address is used as the client address for requests from all the real clients it serves. However, the number of connections and requests from a forward proxy is typically much lower than in a DDoS attack
Because the traffic is generated by bots and is meant to overwhelm the server, the rate of traffic is much higher than a human user can generate.
The User‑Agent header is sometimes set to a non‑standard value.
The Referer header is sometimes set to a value you can associate with the attack.
https://www.nginx.com/blog/mitigating-ddos-attacks-with-nginx-and-nginx-plus/
- Layer 7 HTTP/HTTPS attacks. Hoping to exhaust the server, the attackers flooded the target organization with a large number of HTTPS GET/POST requests using the following methods, amongst others:
Basic HTTP Floods: Requests for URLs with an old version of HTTP no longer used by the latest browsers or proxies
WordPress Floods: WordPress pingback attacks where the requests bypassed all caching by including a random number in the URL to make each request appear unique
Randomized HTTP Floods: Requests for random URLs that do not exist – for example, if example.com is the valid URL, the attackers were abusing this by requesting pages like www.example.com/loc id=12345, etc.
https://blog.verisign.com/security/defending-against-layer-7-ddos-attacks/
- The challenge with a Layer 7 DDoS attack lies in the ability to distinguish human traffic from bot traffic. Layer 7 attacks continue to grow in complexity with ever-changing attack signatures and patterns, organizations and DDoS mitigation providers will need to have a dynamic mitigation strategy in place. Layer 7 visibility along with proactive monitoring and advanced alerting are critical to effectively defend against increasing Layer 7 threats.
https://blog.verisign.com/security/defending-against-layer-7-ddos-attacks/
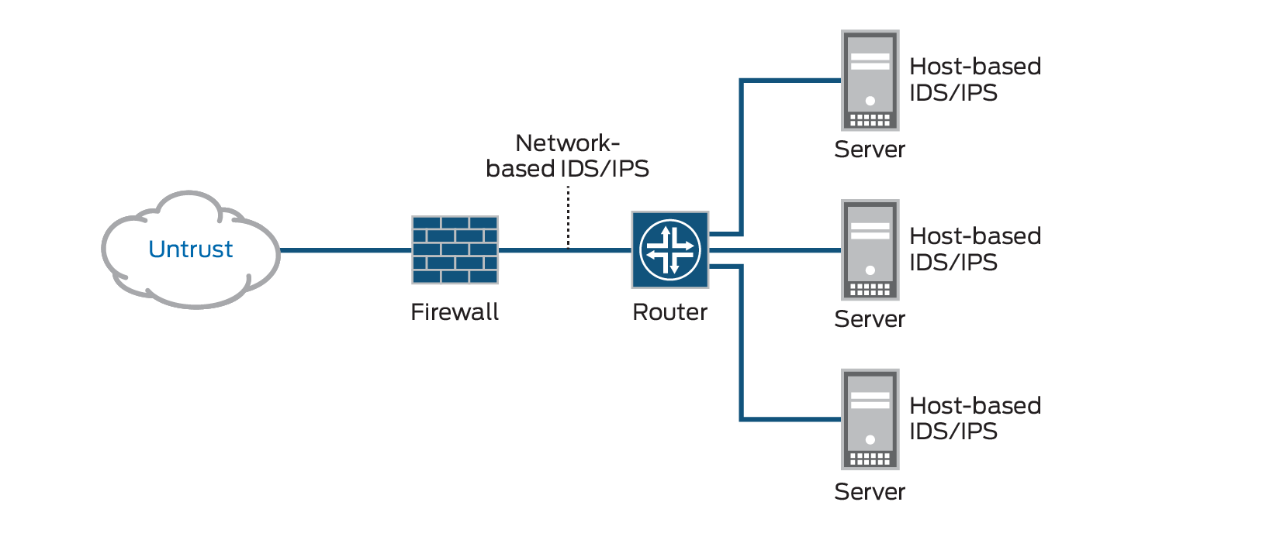
- a stateful firewall is a network firewall that tracks the operating state and characteristics of network connections traversing it.
The firewall is configured to distinguish legitimate packets for different types of connections. Only packets matching a known active connection are allowed to pass the firewall.
- https://en.wikipedia.org/wiki/Stateful_firewall
- How a Stateful Firewall Works
The stateful firewall spends most of its cycles examining packet information in Layer 4 (transport) and lower. However, it also offers more advanced inspection capabilities by targeting vital packets for Layer 7 (application) examination, such as the packet that initializes a connection. If the inspected packet matches an existing firewall rule that permits it, the packet is passed and an entry is added to the state table. From that point forward, because the packets in that particular communication session match an existing state table entry, they are allowed access without a call for further application layer inspection. Those packets only need to have their Layer 3 and 4 information (IP address and TCP/UDP port number) verified against the information stored in the state table to confirm that they are indeed part of the current exchange. This method increases overall firewall performance (versus proxy-type systems, which examine all packets) because only initiating packets need to be unencapsulated the whole way to the application layer.
Conversely, because these firewalls use such filtering techniques, they don't consider the application layer commands for the entire communications session, as a proxy firewall would. This equates to an inability to really control sessions based on application-level traffic, making it a less secure alternative to a proxy.
http://www.informit.com/articles/article.aspx?p=373120
- Unlike a Denial of Service (DoS) attack, in which one computer and one internet connection is used to flood targeted resource with packets, a DDoS attack uses many computers and many Internet connections, often distributed globally in what is referred to as a botnet.
DDoS attacks can be broadly divided into three types:
Volume Based Attacks
Includes UDP floods, ICMP floods, and other spoofed-packet floods. The attack’s goal is to saturate the bandwidth of the attacked site, and
magnitude is measured in bits per second (Bps).
Protocol Attacks
Includes SYN floods, fragmented packet attacks, Ping of Death, Smurf
DDoS and more. This
type of attack consumes actual server resources, or those of intermediate communication equipment, such as firewalls and load balancers, and
is measured in Packets per second.
Application Layer Attacks
Includes
Slowloris, Zero-day DDoS attacks, DDoS attacks that target Apache, Windows or
OpenBSD vulnerabilities and more.
Comprised of seemingly legitimate and innocent requests, the goal of these attacks is to crash the web server, and
the magnitude is measured in Requests per second.
Specific
DDoS Attacks Types
Some specific and particularly popular and dangerous types of
DDoS attacks include:
UDP Flood
This
DDoS attack leverages the User
Datagram Protocol (UDP), a
sessionless networking protocol. This
type of attack floods random ports on a remote host with
numerous UDP packets, causing the host
to repeatedly check for the application listening at that port, and (when no application
is found) reply with an ICMP Destination Unreachable packet. This process saps host resources, and can ultimately lead to inaccessibility.
ICMP (Ping) Flood
Similar in principle to the UDP flood attack, an ICMP flood overwhelms the target resource with ICMP Echo Request (ping) packets
, generally sending packets as fast as possible without waiting for replies. This
type of attack can consume both outgoing and incoming bandwidth, since the victim’s servers will often attempt to respond with ICMP Echo Reply packets, resulting in a significant overall system slowdown.
SYN Flood
A SYN flood
DDoS attack exploits a known weakness in the TCP connection sequence (the “three-way handshake”), wherein
a SYN request to
initiate a TCP connection with a host must
be answered by
a SYN-ACK response from that host, and then confirmed by an ACK response from the requester. In
a SYN flood scenario, the requester sends multiple SYN requests, but either does not respond to the host’s SYN-ACK response or sends the SYN requests from a spoofed IP address. Either way, the host system continues to wait for an acknowledgment for each of the requests, binding resources until
no new connections can be made, and ultimately resulting in a denial of service.
Ping of Death
A ping of death ("POD") attack involves the attacker sending multiple malformed or malicious pings to a computer. The maximum packet length of an IP packet (including header) is 65,535 bytes. However, the Data Link Layer usually poses limits to the maximum frame size - for example, 1500 bytes over an Ethernet network.
In this case,
a large IP packet is split across multiple IP packets (known as fragments), and the recipient host reassembles the IP fragments into the complete packet. In a Ping of Death scenario, following malicious manipulation of fragment content, the recipient ends up with an IP packet which is larger than 65,535 bytes when reassembled. This can overflow memory buffers allocated for the packet, causing a denial of service for legitimate packets.
Slowloris
Slowloris is a
highly-targeted attack, enabling one web server to take down another server, without affecting other services or ports on the target network.
Slowloris does this by holding as many connections to the target web server open for as long as possible. It accomplishes this by creating connections to the target server but sending only a partial request.
Slowloris constantly sends more HTTP headers, but never completes a request. The targeted server keeps each of these false connections open. This eventually overflows the maximum concurrent connection pool and leads to a denial of additional connections from legitimate clients.
Zero-day
DDoS
“Zero-day” are
simply unknown or new attacks, exploiting vulnerabilities for which no patch has yet
been released. The term is well-known amongst the members of the hacker community, where the practice of trading Zero-day vulnerabilities has become a popular activity.
http://www.incapsula.com/ddos/ddos-attacks/
In computing, a denial-of-service attack (DoS attack) or distributed denial-of-service attack (
DDoS attack) is an attempt to make a machine or network resource unavailable to its intended users.
It
generally consists of the efforts of one or more people to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet.
Methods of attack
There are two general forms of DoS attacks: those that crash services and those that flood services.
A DoS attack can
be perpetrated in
a number of ways. The five basic types of attack are:
Consumption of computational resources, such as
bandwidth, disk space, or processor time.
Disruption of configuration information, such as routing information.
Disruption of state information, such as unsolicited resetting of TCP sessions.
Disruption of physical network components.
Obstructing the communication media between the intended users and the victim so
that they can no longer communicate adequately.
A DoS attack may include execution of malware intended to:
Max out the processor's usage, preventing any work from occurring.
Trigger errors in the
microcode of the machine.
Trigger errors in the sequencing of instructions,
so as to force the computer into an unstable state or lock-up.
Exploit errors in the operating system, causing resource starvation and/or thrashing, i.e. to use up all available facilities so no real work can be accomplished or it can crash the system itself
Crash the operating system itself.
Methods of attack of Denial-of-service attack
ICMP flood
A
smurf attack is one particular variant of a flooding DoS attack on the public Internet
Ping of death is based on sending the victim a malformed ping packet, which might lead to a system crash.
Ping flood is based on sending the victim an overwhelming number of ping packets, usually using the "ping" command from unix-like hosts
(S
)SYN flood
A SYN flood occurs when a host sends a flood of TCP/SYN packets, often with a forged sender address
Teardrop attacks
A Teardrop attack involves sending mangled IP fragments with overlapping, over-sized payloads to the target machine.
Low-rate Denial-of-Service attacks
The Low-rate DoS (
LDoS) attack exploits TCP’s slow-time-scale dynamics of retransmission time-out (RTO) mechanisms to reduce TCP
throughput
Peer-to-peer attacks
Attackers have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks.
Asymmetry of resource utilization in starvation attacks
An attack which is successful in consuming resources on the victim computer
Permanent denial-of-service attacks
A permanent denial-of-service (PDoS), also known loosely as flashing, is an attack that damages a system so badly that it requires replacement or reinstallation of hardware
Application-level floods
Various DoS-causing exploits such as buffer overflow can cause server-running software to get confused and fill the disk space or consume all available memory or CPU time.
Nuke
A Nuke is an old denial-of-service attack against computer networks consisting of fragmented or otherwise invalid ICMP packets sent to the target, achieved by using a modified ping utility to repeatedly send this corrupt data, thus slowing down the affected computer until it comes to a complete stop.
R-U-Dead-Yet? (RUDY)
This attack is one of many web application DoS tools available to directly attack web applications by starvation of available sessions on the web server.
Slow Read attack
Slow Read attack sends legitimate application layer requests but reads responses very slowly, thus trying to exhaust server's connection pool
Distributed attack
A distributed denial of service attack (DDoS) occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. This is the result of multiple compromised systems (for example a botnet) flooding the targeted system(s) with traffic. When a server is overloaded with connections, new connections can no longer be accepted
Reflected / Spoofed attack
A distributed reflected denial of service attack (DRDoS) involves sending forged requests of some type to a very large number of computers that will reply to the requests.
Unintentional denial of service
This describes a situation where a website ends up denied, not due to a deliberate attack by a single individual or group of individuals, but simply due to a sudden enormous spike in popularity. This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story
Denial-of-Service Level II
In case of distributed attack or IP header modification (that depends on the kind of security behavior) it will fully block the attacked network from the Internet, but without system crash.
https://en.wikipedia.org/wiki/Denial-of-service_attack
DDoS mitigation is a set of techniques for resisting distributed denial of service (DDoS) attacks on networks attached to the Internet by protecting the target and relay networks
This is done by passing network traffic addressed to the attacked network through high-capacity networks with "traffic scrubbing" filters
DDoS mitigation requires correctly identifying incoming traffic to separate human traffic from human-like bots and hijacked browsers
The process is done by comparing signatures and examining different attributes of the traffic, including IP addresses, cookie variations, http headers, and Javascript footprints
http://en.wikipedia.org/wiki/DDoS_mitigation
- DDoS mitigation techniques
dark address prevention
white/black list
granular rate limiting
anomaly recognition
active verification
dynamic filtering
source rate limiting
aggressive aging
connection limiting
syn proxy
- LOIC (Low Orbit Ion Cannon)
Low Orbit Ion Cannon (LOIC) was originally developed by Praetox Technologies as an open-source network stress testing tool. It allowed developers to subject their servers to heavy network traffic loads for diagnostic purposes, but it has since been modified in the public domain through various updates and been widely used by Anonymous as a DDoS tool.
The IRC-based “Hive Mind” mode enables a LOIC user to connect his or her copy of LOIC to an IRC channel in order to receive a target and other attack parameters via an IRC topic message. Using many copies of LOIC running in Hive Mind mode across many computers, a third party such as the “hacktivist” group Anonymous can take control of each copy of LOIC simultaneously.
http://security.radware.com/knowledge-center/DDoSPedia/loic-low-orbit-ion-cannon/
IP flooding occurs when a computer hacker floods your computer with information through your network connection and IP address. This uses up your network bandwidth and disables you from your online activities. To recover from being IP flooded, request a new IP address from your Internet Service Provider and manually configure your network connection.
- The above scan by nmap is highly reliable, but its drawback is that it's also easily detectable. Nearly every system admin will know that you're scanning their network as it creates a full TCP connection, and this is logged with your IP address in the log files.
Nmap can also be an excellent denial of service (DOS) tool. If several individuals all send packets from nmap at a target simultaneously at high speed (nmap "insane" speed or -T5), they're likely to overwhelm the target and it will be unable to process new website requests effectively, rendering it useless.
https://null-byte.wonderhowto.com/how-to/hack-like-pro-conduct-active-reconnaissance-and-dos-attacks-with-nmap-0146950
- How do NTP reflection attacks work?
Similar to DNS amplification attacks, the attacker sends a small forged packet that requests a large amount of data be sent to the target IP Address.
Monlist is a remote command in older version of NTP that sends the requester a list of the last 600 hosts who have connected to that server
For attackers the monlist query is a great reconnaissance tool
For a localized NTP server it can help to build a network profile.
as a DDoS tool, it is even better because a small query can redirect megabytes worth of traffic
Most scanning tools, such as NMAP, have a monlist module for gathering network information and many attack tools, including metasploit, have a monlist DDoS module.
[root@server ~]# ntpdc -c monlist [hostname]
https://www.symantec.com/connect/blogs/hackers-spend-christmas-break-launching-large-scale-ntp-reflection-attacks
- Skipfish is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes.
http://tools.kali.org/web-applications/skipfish
- What’s a DoS attack, what’s a DDoS attack and what’s the difference?
A DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple locations.
https://www.comparitech.com/net-admin/dos-vs-ddos-attacks-differences-prevention/#:~:text=A%20DoS%20attack%20is%20a,with%20packets%20from%20multiple%20locations.