- What is DevSecOps?
DevSecOps enables integration of security testing earlier in the software development lifecycle (SDLC). This is commonly referred to as “shifting security left” or “shift left.” DevSecOps enables seamless application security earlier in the software development lifecycle, rather than at the end when vulnerability findings requiring mitigation are more difficult and costly to implement.
DevSecOps is an extension of DevOps, and is sometimes referred to as Secure DevOps.
DevSecOps requires planning application and infrastructure security from the start
Benefits of DevSecOps
DevSecOps enables enhanced automation throughout the software delivery pipeline to eliminate coding mistakes and ultimately reduce breaches.
Teams that implement DevSecOps tools and processes to integrate security into their DevOps framework will be able to release secure software faster. Developers can test code for security and detect security flaws as code is written.
What are key components of DevSecOps
Application/API Inventory
Automate the discovery, profiling, and continuous monitoring of the code across the portfolio. This may include production code in data centers, virtual environments, private clouds, public clouds, containers, serverless, and more. Use a combination of automated discovery and self-inventory tools
Custom Code Security
Continuously monitor software for vulnerabilities throughout development, test, and operations. Deliver code frequently so vulnerabilities can be identified quickly with each code update
Static Application Security Testing (SAST) scans the application source files, accurately identifies the root cause and helps remediate the underlying security flaws.
Dynamic Application Security Testing (DAST) simulates controlled attacks on a running web application or service to identify exploitable vulnerabilities in a running environment.
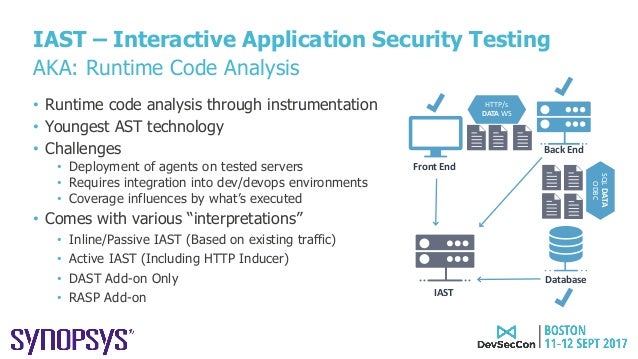
Interactive Application Security Testing (IAST) provides a deep scan by instrumenting the application using agents and sensors to continuously analyze the application, its infrastructure, dependencies, dataflow, as well as all the code.
Open Source Security
Open source software (OSS) often times includes security vulnerabilities, so a complete security approach includes a solution that tracks OSS libraries, and reports vulnerabilities and license violations.
Software Composition Analysis (SCA) automates the visibility into open source software (OSS) for the purpose of risk management, security and license compliance.
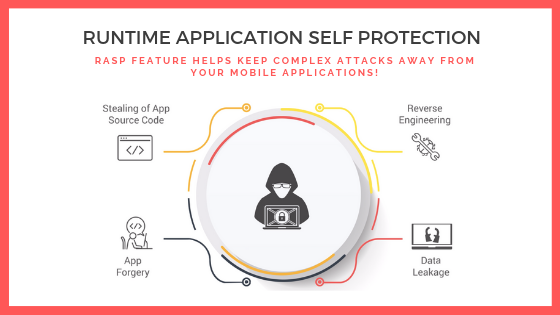
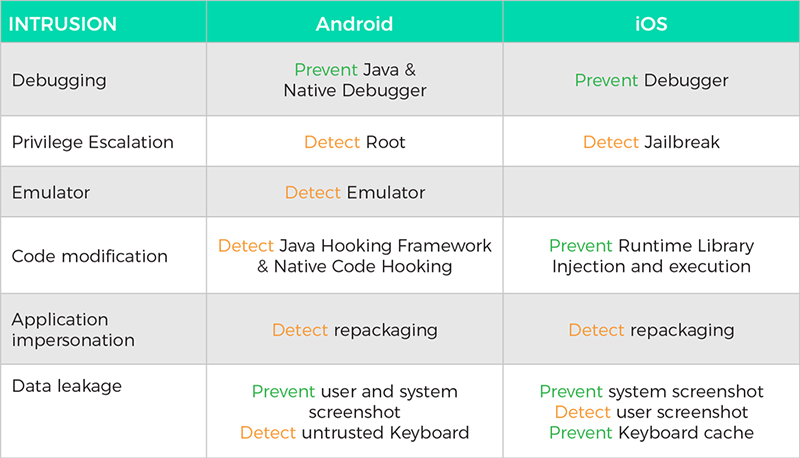
Runtime Prevention
Protect applications in production – new vulnerabilities may be discovered, or legacy applications may not be in development.
Runtime Application Self-Protection (RASP) instruments applications, directly measures attacks from the inside, and prevents exploits from within.
Compliance monitoring
Enable audit readiness and a constant state of compliance for GDPR, CCPA, PCI, etc.
Making DevSecOps work for you
Step 1: Build Security into Software Requirements
Step 2: Test Early, Often and Fast
Step 3: Leverage Integrations to Make Application Security a Natural Part of the Lifecycle
Step 4: Automate Security as Part of the Development and Testing Processes
Step 5: Monitor and Protect Once Released
Automation in CI/CD pipelines
SAST with Fortify Static Code Analyzer
DAST with Fortify WebInspect
RASP with Fortify Application Defender
Software Composition Analysis (SCA) / Open Source Security (OSS) with Sonatype and Fortify
https://www.microfocus.com/en-us/what-is/devsecops
- DevOps isn’t just about development and operations teams. If you want to take full advantage of the agility and responsiveness of a DevOps approach, IT security must also play an integrated role in the full life cycle of your apps.
In the past, the role of security was isolated to a specific team in the final stage of development.
DevSecOps means thinking about application and infrastructure security from the start. It also means automating some security gates to keep the DevOps workflow from slowing down. Selecting the right tools to continuously integrate security can help meet your security goals, but effective DevOps security requires more than new tools—it builds on the cultural changes of DevOps to integrate the work of security teams sooner rather than later.
it has always been ideal to include security as an integral part of the entire app life cycle
DevSecOps is about built-in security, not security that functions as a perimeter around apps and data.
In part, DevSecOps highlights the need to invite security teams at the outset of DevOps initiatives to build in information security and set a plan for security automation.
It also underscores the need to help developers code with security in mind, a process that involves security teams sharing visibility, feedback, and insights on known threats.
For starters, a good DevSecOps strategy is to determine risk tolerance and conduct a risk/benefit analysis.
Automating repeated tasks is key to DevSecOps, since running manual security checks in the pipeline can be time intensive.
DevOps security is built for containers and microservices
DevSecOps means building security into app development from end to end.
DevOps teams should automate security to protect the overall environment and data, as well as the continuous integration/continuous delivery process—a goal that will likely include the security of microservices in containers.
Environment and data security:
Standardize and automate the environment.
Centralize user identity and access control capabilities.
Isolate containers running microservices from each other and the network.
Encrypt data between apps and services.
Introduce secure API gateways.
CI/CD process security:
Integrate security scanners for containers.
Automate security testing in the CI process.
Add automated tests for security capabilities into the acceptance test process.
Automate security updates, such as patches for known vulnerabilities.
Automate system and service configuration management capabilities.
https://www.redhat.com/en/topics/devops/what-is-devsecops
- DevSecOps is the philosophy of integrating security practices within the DevOps process.
DevSecOps involves creating a ‘Security as Code’ culture with ongoing, flexible collaboration between release engineers and security teams.
In DevSecOps, two seemingly opposing goals —“speed of delivery” and “secure code”—are merged into one streamlined process
In alignment with lean practices in agile, security testing is done in iterations without slowing down delivery cycles. Critical security issues are dealt with as they become apparent, not after a threat or compromise has occurred.
Security protocols that are baked into the development process rather than added as a “layer on top” allows DevOps and security professionals to harness the power of agile methodologies.
As more organizations rely on cloud applications to keep operations up and running, security efforts independent of those performed by AWS are crucial to prevent costly downtimes.
DevSecOps vs. Rugged DevOps
Adding the term “rugged” to DevOps means adding increased trust, transparency, and a clearer understanding of probable risks. It is an accelerated approach where security parameters are put into practice at the start of the project and penetration tests applied throughout the development cycle.
In a DevSecOps environment, automated testing is performed throughout the development cycle. Ruggedizing the process means making security a higher priority. This includes incremental safety improvements in the continuous delivery pipeline (AWS or other), regular threat assessment using security games, and adding security testing to automated processes.
A cultural and technical shift towards a DevSecOps approach helps enterprises address security threats more effectively, in real-time
six important components of a DevSecOps approach
Code analysis – deliver code in small chunks so vulnerabilities can be identified quickly.
Change management – increase speed and efficiency by allowing anyone to submit changes, then determine whether the change is good or bad.
Compliance monitoring – be ready for an audit at any time (which means being in a constant state of compliance, including gathering evidence of GDPR compliance, PCI compliance, etc.).
Threat investigation – identify potential emerging threats with each code update and be able to respond quickly.
Vulnerability assessment – identify new vulnerabilities with code analysis, then analyze how quickly they are being responded to and patched.
Security training – train software and IT engineers with guidelines for set routines.
https://www.sumologic.com/devops/devsecops-rugged-devops/
- Security Assurance Requirements for Linux Application Container Deployments
https://nvlpubs.nist.gov/nistpubs/ir/2017/NIST.IR.8176.pdf
- An Unlikely Union: DevOps and Audit
https://itrevolution.com/book/devops-and-audit/
- Secure coding is a set of technologies and best practices for making software as secure and stable as possible. It encompasses everything from encryption, certificates, and federated identity to recommendations for moving sensitive data, accessing a file system, and managing memory.
The Fedora Project's Defensive Coding Guide provides guidelines for improving software security through secure coding
https://developers.redhat.com/topics/secure-coding/
- Open Source Identity and Access Management For Modern Applications and Services
User Federation, Identity Brokering and Social Login.
Add authentication to applications and secure services
https://www.keycloak.org/
- Is it DevSecOps or SecDevOps?
What Security Looks Like With SecDevOps
Security controls, guidelines, coding standards, and policies must be integrated completely into the software development process. This is done by making security part of the process and pipeline from the beginning — "Sec" then "Dev" then "Ops." The security team (or perhaps an architecture or senior developer specialized in security) defines the necessary policies upfront for the team.
These policies might consist of secure coding standards, rules for avoiding insecure APIs and poor encryption, instructions for using static and dynamic analysis, and testing guidelines. The goal is to have the developers working towards more secure software as part of their daily routine and automation helps make this a reality.
Security is often left as add-on or a gating process before releasing a product, but it's difficult to fix security issues when a product is halfway out the door. Shifting security to the left, as in SecDevOps, is the key to success.
https://dzone.com/articles/is-it-devsecops-or-secdevops
- What is SecDevOps and why should you care?
SecDevOps (also known as DevSecOps and DevOpsSec) is the process of integrating secure development best practices and methodologies into development and deployment processes which DevOps makes possible.
SecDevOps — sometimes called “Rugged DevOps” or “security at speed” — as a set of best practices designed to help organizations implant secure coding deep in the heart of their DevOps development and deployment processes. …It seeks to embed security inside the development process as deeply as DevOps has done with operations.
1. Security as Code (SaC): which refers to the building of security into the tools that exist in the DevOps pipeline. This means automation over manual processes. It means the use of static analysis tools that check the portions of code that have changed, versus scanning the entire code base.
2. Infrastructure as Code (IaC): defines the set of DevOps tools used to setup and update infrastructure components. Examples include Ansible, Chef, and Puppet. …With IaC, if a system has a problem, it is disintegrated, and a new one (or two) are created to fill the spot.
How Can SecDevOps Be Implemented?
Tooling
Automate security audits. Use scripts, static and dynamic analysis, composition analysis, and integration of testing within existing tools
Detect security flaws as soon as possible. The sooner a security flaw can be detected, and the further away they are done from production (or the client’s computer), the better it is, and the cheaper it is to resolve
Regularly break the build. Ensure that tools can spot and flag security flaws which result in broken builds, just like how failing tests already work.
Have accurate audit report results. Ensure that reports of security flaws are accurate; otherwise, faith and trust will rapidly erode.
Use composition analysis. Ensure that you know the security, reliability, and exposure of the packages that you’re building your software on, as well as when they need to be avoided or replaced. Use tools that automatically validate them.
Focus on instrumentation. Ensure that infrastructure, not just code, can be verified as working and secure; and that it’s replaceable when it’s isn’t.
Use real-time protection. Ensure that production applications are protected against vulnerabilities that weren’t caught earlier. No software is 100% secure. Avoid solutions that create alert fatigue, false positives or that aren’t integrated into the DevOps tools.
Processes
Establish strong feedback loops. As with any successful process or organization, you need to engender the ability to provide reliable feedback, even if the information delivered isn’t encouraging, or what the team wants to hear.
Perform regular code audits. Just as with any other code review, such as for quality and standards compliance, security also needs to be reviewed, assessed, and corrected as transparently — and as quickly — as possible.
Benchmark and review your performance. Like reaching any goal, you have to know where you are and whether you’re improving or declining in the attainment of it. Make sure that you know how you’re doing, and where you still need to improve.
Have documented procedures for dealing with problems. Eventually, problems do occur. Ensure that you’re equipped to deal with them when they do in an organized and standardized manner.
Culture
To build a SecDevOps culture, consider the following four points:
Engender a culture of openness and continuous learning. Ensure as much transparency as possible. Ensure that everyone in the team knows what’s going on, and is constantly encouraged to learn more.
Build strong feedback loops. Ensure that information is rapidly delivered.
Employ and nurture security evangelists. Ensure that you have people within your teams whose role is to reinforce and to grow security awareness and a security culture.
Grow autonomy in every team. Ensure your teams can make the relevant decisions necessary to improve consistently.
https://blog.sqreen.com/secdevops/
- SecDevOps: Injecting Security Into DevOps Processes
As Farwell explains, a big part of SecDevOps is about empowering developers to become security experts.
Tools for SecDevOps
Stethoscope: Created by Netflix and now open source, Stethoscope helps security teams manage “user-focused security.” Security teams at companies like New Relic use Stethoscope to offer self-service end-user security to DevOps teams, so those teams can manage their own devices.
Claire: SecDevOps engineers use this open source project from CoreOS to scan for vulnerabilities in Docker containers.
Suricata: This open source tool can help detect threats against your networks. It uses rules, a signature language, and scripting tools to inspect network traffic and threats in real time. New Relic security engineers use Suricata to inspect the network traffic running through their container and cloud-based environment.
https://blog.newrelic.com/technology/what-is-secdevops/
- DevSecOps vs. SecDevOps vs. DevOpsSec: Is there really a difference in these secure DevOps terms?
Whether it is DevSecOps vs. SecDevOps vs. DevOpsSec, is there really a difference in these Secure DevOps terms? In this article, we will discuss the differences between each of these, and explain why SecDevOps is actually the correct security approach.
DevSecOps: So what is DevSecOps? If we break this down, you can see that Dev leads the pack and is given the highest level of importance.
As a result, DevSecOps represents the scenario we are in today – a situation where security doesn’t get the prioritization it deserves.
DevOpsSec: What is DevOpsSec? If taken literally, this version places security at the end of the line, after discrete development, deployment, and operations activities.
SecDevOps:SecDevOps refers to the inclusion of security efforts and best practices into the continuous integration and continuous deployment pipeline. It also suggests that security requirements are taken into account before development to ensure security is included throughout the product lifecycle.
https://www.cspi.com/devsecops-vs-secdevops-blog/
- Playbook Example: Continuous Delivery and Rolling Upgrades
What is continuous delivery?
Continuous delivery (CD) means frequently delivering updates to your software application.
Continuous delivery end-to-end
Now that you have an automated way to deploy updates to your application, how do you tie it all together? A lot of organizations use a continuous integration tool like Jenkins or Atlassian Bamboo to tie the development, test, release, and deploy steps together. You may also want to use a tool like Gerrit to add a code review step to commits to either the application code itself, or to your Ansible playbooks, or both.
https://docs.ansible.com/ansible/latest/scenario_guides/guide_rolling_upgrade.html
- Integrating Security Into the Devops Process
Ansible and Palo Alto Networks for Automation and Orchestration
Palo Alto Networks has built a series of Ansible modules that can help integrate security seamlessly into the DevOps process.
Ansible modules for Palo Alto Networks can be used to configure the entire family of next- generation firewalls, both physical virtualized form-factors as well as Panorama. The Ansible modules communicate with the next-generation firewalls and Panorama using the Palo Alto Networks XML API.
Import and load the configuration of the next-generation firewalls across virtual or physical deployments and/or integrate deployment within your existing CI/CD pipeline.
https://www.ansible.com/integrations/networks/palo-alto
- 6 reasons to use Ansible for network automation
1. Agentless
The importance of an agentless architecture cannot be stressed enough when it comes to network automation, especially as it pertains to automating existing devices.
As standalone network devices like routers, switches, and firewalls continue to add support for APIs, software-defined networking (SDN) solutions are also emerging. The one common theme with SDN solutions is that they all offer a single point of integration and policy management, usually in the form of an SDN controller. This is true for solutions such as Cisco ACI, VMware NSX, Big Switch Big Cloud Fabric, and Juniper Contrail, as well as many of the other SDN offerings from companies such as Nuage, Plexxi, Plumgrid, Midokura, and Viptela. This even includes open source controllers such as OpenDaylight.
As most software-defined networks are deployed with a controller, nearly all controllers expose a modern REST API. And because Ansible has an agentless architecture, it makes it extremely simple to automate not only legacy devices that may not have an API, but also software-defined networking solutions via REST APIs, all without requiring any additional software (agents) on the endpoints
2. Free and Open Source Software (FOSS)
3. Extensible
Ansible was primarily built as an automation platform for deploying Linux applications, although it has expanded to Windows since the early days
4. Integrating into Existing DevOps Workflows
Ansible is used for application deployments within IT organizations. It’s used by operations teams that need to manage the deployment, monitoring, and management of various types of applications.
5. Idempotency
The term idempotency (pronounced item-potency) is used often in the world of software development, especially when working with REST APIs, as well as in the world of DevOps automation and configuration management frameworks, including Ansible. One of Ansible’s beliefs is that all Ansible modules (integrations) should be idempotent
This is unlike most traditional custom scripts and the copy and pasting of CLI commands into a terminal window. When the same command or script is executed repeatedly on the same system, errors are (sometimes) raised.
Another example is if you have a text file or a script that configures 10 VLANs, the same commands are then entered 10 times every time the script is run. If an idempotent Ansible module is used, the existing configuration is gathered first from the network device, and each new VLAN being configured is checked against the current configuration. Only if the new VLAN needs to be added (or changed—VLAN name, as an example) is a change or command actually pushed to the device.
6. Network-Wide and Ad Hoc Changes
One of the problems solved with configuration management tools is configuration drift (when a device’s desired configuration gradually drifts, or changes, over time due to manual change and/or having multiple disparate tools being used in an environment)—in fact, this is where tools like Puppet and Chef got started
Because Ansible is agentless, there is not a default push or pull to prevent configuration drift
https://www.oreilly.com/ideas/6-reasons-to-use-ansible-for-network-automation
- Automating Cloud Security with Ansible and Palo Alto Networks
The Ansible modules for PAN-OS, our security operating system, allow our customers to embed security into the application development lifecycle, eliminating the bottleneck that change control security best practices can introduce.
In the public cloud, these collaboration efforts have become invaluable to our customers as they adopt more rapid and iterative application development methodologies (i.e., DevOps, CI/CD) on AWS, Azure and Google Cloud.
Using Ansible modules to deploy and configure Palo Alto Networks VM-Series firewalls on AWS, Azure and Google Cloud
https://blog.paloaltonetworks.com/2018/04/automating-cloud-security-ansible-palo-alto-networks/
- What is BizDevOps?
In fact, some DevOps teams could already call themselves BizDevOps. These teams have business domain owners participating from the start, they use Kanban and scrum (plus more), and are leveraging past learnings to eliminate waste
The team makeup: Business team and/or application owner, development team members, and operation team members form a single team; focus could be a product your company delivers, or a business process, business component, or business service.
Integrated value and flow of processes: You have integrated business leaders, developers, and operations folks who all are working on a streamlined flow from your company’s strategy to the deployment and ongoing operations of the product, service, or component. You understand the value stream or you are working on, and you understand the customer journey end-to-end, including all key value chain components.
Existence of key performance metrics: You have jointly established key performance indicators, which include customer-centric metrics – e.g., user behavior and feature adoption to DevOps metrics such as time-to-business-impact and speed of remediation.
Automation toolchain: You are leveraging a variety of automation platforms that allow you to collaborate and automate across the different process and data items.
https://enterprisersproject.com/article/2019/9/devops-what-is-bizdevops
- It’s proven that DevOps increases the ability of an organization to deliver services at high velocity.
But what if the same tools and practices that accelerate feature delivery can also be used to generate greater business value?
That’s where BizDevOps comes in.
BizDevOps integrates feedback from the business side of an organization into its delivery cycles, effectively ensuring features released through DevOps cycles are built specifically to serve business objectives. A streamlined workflow is created from business strategy to deployment, allowing DevOps metrics to become aligned with high-level business KPIs.
Just as DevOps overcomes silos separating development from operations, BizDevOps overcomes silos separating DevOps from the rest of the business.
BizDevOps is accomplished by encouraging the business team to work directly with product owners, developers, and operators to set priorities for sprints and backlogs.
Define metrics that measure business value, and make sure your deployment and release strategies take traditional business concerns, such as geography, community, and other internal and external factors, into account.
https://medium.com/@CloudOps_/what-is-bizdevops-642806ab6c60