- Security information and event management
Security Information and Event Management (SIEM) solutions are a combination of the formerly disparate product categories of SIM (security information management) and SEM (security event manager).
SIEM technology provides real-time analysis of security alerts generated by network hardware and applications.
SIEM solutions come as software, appliances or managed services, and
http://en.wikipedia.org/wiki/Security_information_and_event_management
- Security event manager
A security event manager (SEM) is a computerized tool used on enterprise data networks to centralize the storage and interpretation of logs, or events, generated by other software running on the network
Many systems and applications which run on a computer network generate events
http://en.wikipedia.org/wiki/Security_event_manager
- Security information management
Security information management (SIM) is the industry-specific term in computer security referring to the collection of data (typically log files; e.g.
Most famous editors and solutions in the SIM/SEM Marketplace
Alcatel-Lucent OA Safeguard
Cisco Cisco Security Manager
CS Prelude/
EMC2 RSA Security
HP ArcSight
LogLogic Enterprise Virtual Appliance (formerly
LogRhythm SIEM 2.0 Security Intelligence
NetIQ Security Manager
NitroSecurity McAfee Enterprise Security Manager
Novell Sentinel
Q1 Labs
SenSage Advanced SIEM and Log Management
Splunk Splunk
Symantec Security Information Manager
http://en.wikipedia.org/wiki/Security_information_management
- OSSIM, the Open Source SIEM
OSSIM is the most widely used SIEM offering, thanks
http://communities.alienvault.com/
- OSSIM
Open Source Security Information Management (OSSIM) provides a Security Information and Event Management (SIEM) solution. It is a one-stop solution and integrated the open source
OSSIM,
https://www.alienvault.com/products/ossim
- Security Information and Event Management (SIEM) solutions
Security Information and Event Management (SIEM) solutions are a combination of the formerly disparate product categories of SIM (security information management) and SEM (security event manager)
SIEM technology provides real-time analysis of security alerts generated by network hardware and applications
http://en.wikipedia.org/wiki/Security_information_and_event_management
- Eyes on Glass: End to End Monitoring
Organizations’ IT Infrastructure will function best when a continuous set of “eyes” are closely analyzing its health and availability; and proactively identifying the issues that keep the business up and running.
What plays a pivotal role in defining an overall IT monitoring strategy is ensuring a healthy data center along with end user experience coverage.
https://www.zensar.com/blogs/2015/12/eyes-on-glass-end-to-end-monitoring/
- Next Generation SOC
The Techniques, Tactics and Procedures
real-time “eyes on glass” monitoring
http://www.itip.ph/uploads/events_files/IBM_SOC.
- WHAT IS
A MSSP (
A managed security service provider (MSSP) is an IT service provider that provides an organization with information security, cybersecurity monitoring and management, which may include policy development, security operation center, compliance services, incident response service, Virtual CISO,
MSSP technology offerings may include deploying, configuring, and/or managing the following technologies:
Intrusion prevention systems (IPS)
Web content filtering
Anti-virus (AV),
Anti-spam
Firewalls (UTMs, NGFWs, etc.)
VPN
Vulnerability scanning
Patch management
Data loss prevention (DLP)
Threat intelligence
Identity access management (IAM)
Privileged access management (PAM)
MSSP services may include:
Risk assessments and gap analysis
Policy development and risk management
Solution scoping
Solution/tool research and requisition
Solution implementation
Management of security systems
Configuration management
Security updates
Reporting, auditing, and compliance
Training and education
“Traditionally, MSSPs have
Another differentiation between MSPs versus MSSPs is NOCs versus SOCs. MSPs frequently establish their own network operation center (NOC) from which they monitor and administrate over customer operations, MSSPs
https://cybersecop.com/news/2018/10/4/what-is-an-mssp-managed-security-services-provider
- Managed
Security Services
“Eyes on Glass” is a common saying
Technically “eyes on glass” requires
SIEM vs. MSSP
A Security Information and Event Management (SIEM) solution
The MSSP does not
Scale and Efficiency
True “eyes on glass” is not a scalable service
It is far more efficient to configure logs to submit as much data as possible
“Eyes on Glass”
https://www.optiv.com/blog/managed-security-services-mss-and-eyes-glass-real-world
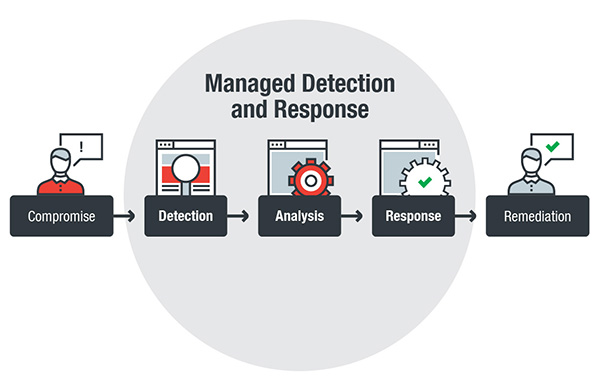
What is Managed
Managed detection and response is a service that arose from the need for organizations, who lack the resources, to be more cognizant of risks and improve their ability to detect and respond to threats.
MDR is more focused on threat detection, rather than compliance.
Managed detection and response relies heavily on security event management and advanced analytics.
Managed Detection and Response vs. Managed
Coverage. Managed security services can work with different
Compliance reporting. If you need compliance reporting, go for a managed security service, as managed detection and response services rarely do compliance reports.
The human touch. One
Incident response. With managed detection and response, you only need a separate retainer if you want on-site incident response.
https://digitalguardian.com/blog/what-managed-detection-and-response-definition-benefits-how-choose-vendor-and-more
- Managed Detection and Response
managed service detects and responds to threats with complete root-cause and kill chain visibility to deliver more effective security.
https://www.ibm.com/security/services/managed-detection-response
- Managed Detection and Response
Managed detection and response (MDR) is an outsourced service that provides organizations with threat hunting services and responds to threats once they
What challenges can MDR address?
While training and setting up dedicated security teams that can
MDR integrates EDR tools in its security implementation, making them an integral part of the detection, analysis, and response roles.
MDR aims to address this problem not only by detecting threats but also by analyzing all the factors and indicators involved in an alert.
One of the most important skills that security professionals need is the ability to contextualize and analyze indicators of compromise
How do MDR providers compare with MSSPs?
In contrast with MDR providers, which can detect lateral movement within a network, MSSPs typically work with perimeter-based technology
MSSPs have security professionals who perform log management, monitoring, and analysis, but often not at a very in-depth level.
In terms of service, MSSPs usually communicate via email or phone, with security professionals as a secondary access, while MDR providers carry out 24/7 continuous monitoring,
However, MSSPs still provide value to organizations. For example, managing firewalls and other day-to-day security needs of an organization’s network is a task that is more apt for an MSSP than an MDR provider, which offers a more specialized service.
How does Trend Micro’s MDR work?
Trend Micro’s MDR provides
https://www.trendmicro.com/vinfo/us/security/definition/managed-detection-and-response
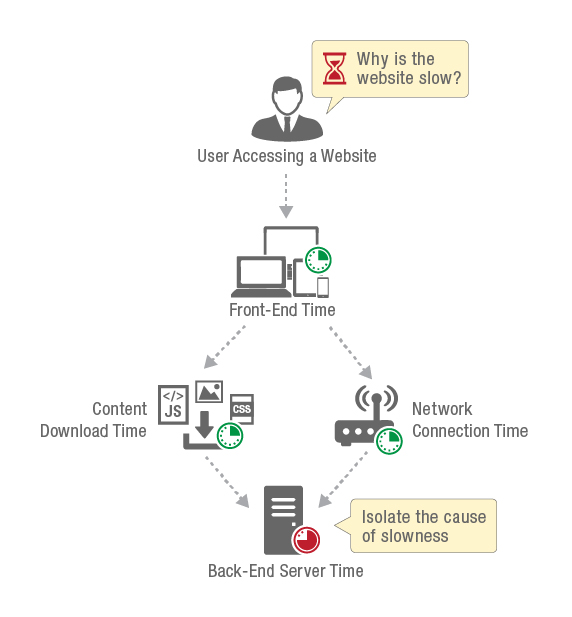
- What is Real User Monitoring? How It Works, Examples, Best Practices, and More
Real User Monitoring is a
It’s used to gauge user experience, including key metrics like load time and transaction paths, and it’s an important component of application performance management (APM).
Real User Monitoring vs. Synthetic Monitoring
Real User Monitoring is
Examples of RUM
Constant monitoring of a blog in the background to see when and where page load times increase
An end-user portal like a bank software system may use it to spot intermittent issues, like login failures that only occur under specific, rare conditions.
An app developer may use it to highlight failures in different platforms that don’t show up during pre-deployment testing.
Benefits of RUM
Measure service level targets easily. It offers real-world measurement of key targets by tracking actual visits and delivering top-level data on actual use cases.
Easily identify problems and better prioritize issues. It can replay user sessions and track transaction paths to surface hidden problems.
Determine hitches at the network and page level. Problems at the lower levels of a website can hide like needles in a haystack. It can spotlight these problems even when they’re intermittent
Best Practices for RUM
Assess the Current Speed of the Website. F
Improve Mobile Testing Strategy.
Relate Performance to the Business.
https://stackify.com/what-is-real-user-monitoring/
- SIEM Analyzes security alerts in real-time
SIEMs do three things:
One: Collect, normalize, and store log events and alerts from the organization’s network and
security devices, servers, databases, applications, and endpoints in a secure, central location
Investigators had determined that logging in to every system to
check for relevant log events was increasingly impossible. Also, if your logs were not secure,
you had no guarantee that an attacker hadn’t just deleted the entries to hide their activities
Two: Run advanced analytics on the data, both in real-time and across historical data, to
Identify potential security incidents that should be investigated by a human
The potential
incidents are prioritized by risk, severity, and impact.
these security analytics have
grown from employing Simple cross-correlation rules to monitoring for User-behavioral
anomalies, watching for known Indicators of Compromise IoC, and applying sophisticated
Machine learning models
Three: Prove that all of the security controls under the purview of the SIEM are in place and
effective
SIEM has evolved from an information platform, to a threat
intelligence center, to a fully integrated and automated center for security and network
operations.
https://training.fortinet.com/pluginfile.php/1625608/mod_scorm/content/1/story_content/external_files/NSE%202%20SIEM%20Script_EN.pdf