- CISSP Training - Cryptography
Cryptography: the science of hiding information in plain sight
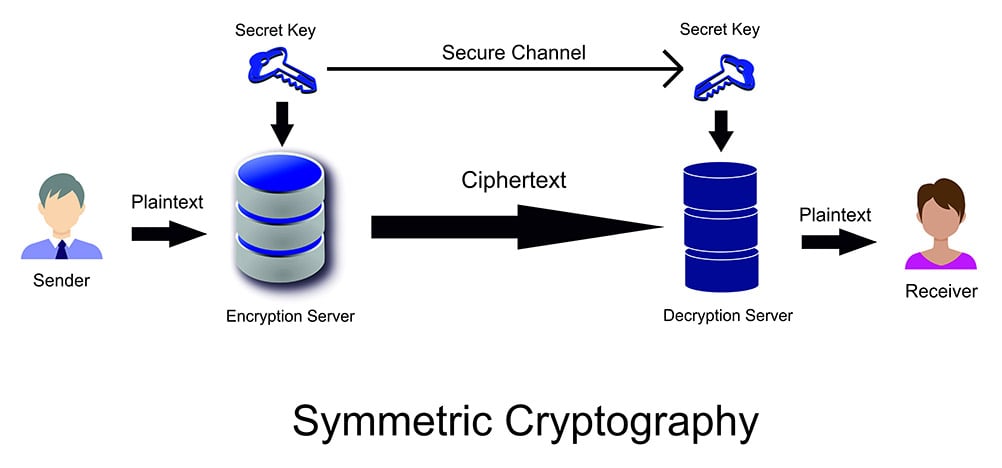
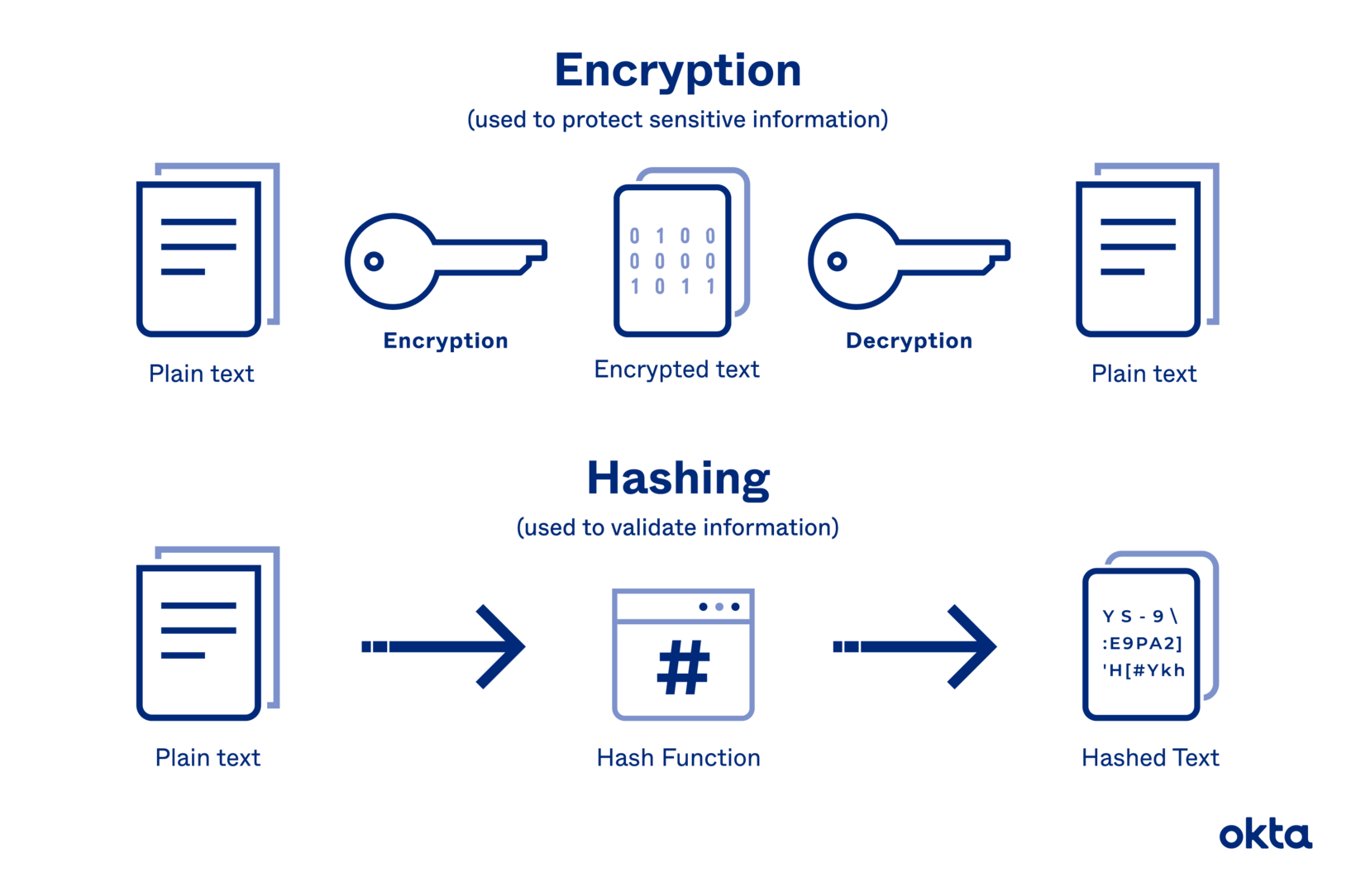
encryption-ciphertext-decryption
encryption-transforming data into an unreadable format
plaintext-readable data
the ciphertext-scrambled format of data after encryption
- Java Cryptography
Cryptography is a field looking at techniques for "encoding and verifying things securely". It
computer protocols for using the previous two techniques correctly and in a way that allows all parties to know how they're being used (e.g. the TLS protocol allows a client to connect to a server over the Internet without the two machines previously knowing things such as
http://www.javamex.com/tutorials/cryptography/
- Lesson 3: Cryptography
Encryption is
http://www.oracle.com/technetwork/java/crypto-142375.html
- Homomorphic encryption is a method of performing calculations on encrypted information without decrypting it first.
- Storing User Passwords Securely: hashing, salting, and
Bcrypt
Bad Solution #1: plain text password
It would be very insecure to store each user's "plain text" password in your database:
This is insecure because if a hacker gains access to your database, they'll be able to use that password to log in as that user on your system.
Or even worse, if that user uses the same password for other sites on the internet, the hacker can now login there as well
Bad Solution #2: sha1(password)
A better solution is to store a "one-way hash" of the password, typically using a function like md5(
in theory, it should be impossible to "undo" a one-way hash function and find an input string that outputs the same hash value
storing a simple hash (with no salt) is not secure
Bad Solution #3: sha1(FIXED_SALT + password)
One attempt to make things more secure is to "salt" the password before hashing it:
If the hacker gains access to these new password hashes (but not the salt), it will make it much more difficult for the hacker to guess the passwords because they would also need to know the salt
However, if the hacker has broken into your server, they probably also have access to your source code
Bad Solution #4: sha1(PER_USER_SALT + password)
create a new column in the database and store a different salt for each user.
The salt
By having a per-user-salt, we get one huge benefit: the hacker can't attack all of your user's passwords at the same time
Good Solution:
how
http://dustwell.com/how-to-handle-passwords-bcrypt.html
- If you want to find a
given hash
- Hash each plaintext one by one, but store each generated hash in a sorted table so
Going one by one takes a
It's important to note that it does the reverse of a hash function (mapping hashes to plaintexts), but it is /not/ an inverse hash function. The whole purpose of hash functions is that inverse hash functions can't
If the set of plaintexts is [0123456789]{6} (we want a rainbow table of all numeric passwords of length 6), and the hashing function is MD5(
We now have generated another plaintext from the hash of the previous plaintext, this is the purpose of the reduction function.
The algorithm is:
Look for the hash in the list of final hashes, if it is there break out of the loop.
If it isn't there reduce the
Goto the start.
If the hash matches one of the final hashes, the chain for which the hash matches the final hash contains the original hash.
http://kestas.kuliukas.com/RainbowTables/
bcrypt which is
Its slowness and multiple rounds ensure that an attacker must deploy massive funds and hardware to
Add to that per-password salts (
While the encryption phase of Eksblowfish and Blowfish are exactly the same, the key schedule phase of Eksblowfish ensures that any subsequent state depends on both salt and key (user password), and no state can be
Because of this key difference,
You cannot retrieve the
http://stackoverflow.com/questions/4795385/how-do-you-use-bcrypt-for-hashing-passwords-in-php
- what exactly is a good option for secure password hashing?
It uses a Key Factor (or
The ability to increase the cost (time and processing power) of hashing
Changing the Key Factor also influences the hash output, so this makes
it comes to hashing and encryption, faster is never better.
The longer it takes to encode something, the longer it takes a computer to
How much slower is
Depends on the work factor.
Using a work factor of 12,
SHA-2 also isn’t adaptive like
http://www.sitepoint.com/why-you-should-use-bcrypt-to-hash-stored-passwords/
- org
. springframework . . . bcrypt . BCrypt
This password hashing system tries to thwart off-line password cracking using a
To hash a password for the first time, call the
String
To check whether a plaintext password matches one that has
if (
System
else
System
The
String
String
The amount of work increases exponentially (2**log_rounds), so each increment is twice as much work.
The default
http://docs.spring.io/autorepo/docs/spring-security/3.2.x/apidocs/org/springframework/security/crypto/bcrypt/BCrypt.html
- org
. springframework . . . bcrypt . BCryptPasswordEncoder
Implementation of
Clients can optionally supply a "strength" (a
The larger the strength parameter the more work will have to
The default value is 10.
public
Parameters:
strength - the log rounds to use
random - the secure random instance to use
http://docs.spring.io/autorepo/docs/spring-security/3.2.x/apidocs/org/springframework/security/crypto/bcrypt/BCryptPasswordEncoder.html
- The file name is Windows-KB841290-x86-ENU.exe in case you're looking for it in whatever folder you downloaded it to.
Now that FCIV has
Locate the just extracted
copy
Now that File Checksum Integrity Verifier
Some types of files you download, like ISO images, service packs, and even entire software programs or operating systems, are often large and high-profile, making them prone to downloading errors and even alteration by malicious third parties
Fortunately, many websites offer a piece of data called a checksum that can
A checksum, also called a hash or hash value,
Comparing the checksum produced by running a hash function on your version of the file, with the one published by the download provider, can prove with near certainty that both files are identical.
http://pcsupport.
- Verifying File Copy/Move Operations With Microsoft File Checksum Integrity Verifier
- While MD5 is no longer considered cryptographically secure and is being replaced by the SHA-2 family of hash functions, it
is to provide a hash value for files thatnevertheless are downloaded
FCIV can also recursively generate hash values for all the files in a folder and its
to calculate a checksum for each system file and store them in
the following command will calculate and store the hash value for every file in the
http://www.computerweekly.com/tip/How-to-use-the-Microsoft-FCIV-command-line-checksum-tool
- Availability and description of the File Checksum Integrity Verifier utility
generate hash
//
// File Checksum Integrity Verifier version 2.05.
//
336b0a1e9227648b45be68b31761bce7
check hash
//
// File Checksum Integrity Verifier version 2.05.
//
7c23a18aa23cf4ba0b8ca62985152c14
- The popular argument for storing passwords in plain text is that it reduces the required labor for help desk staff in that they'll easily be able to tell a person what their password is if they
happen to like plain text )
A one-way hash function is a series of mathematical operations that transform some input into a
As the name implies, these functions are one-way, meaning you can turn something into a
When a user creates an account, the system stores their account information, but instead of storing their password on the disk, it runs the password through the one-way hash function and stores the digest instead.
When a user wants to log in to the system
The system only needs to
A good cryptographic hash function-the
Recognizability
What is the major downside of the fact that a digest of a certain message always returns the same digest? Well, if an attacker spends a lot of resources pre-computing digests for as many passwords as possible, and they get access to your user database, they can check all of those digests against the ones you've stored.
What's even worse is that, if the attacker guesses, or "cracks", a password, they can
Speed
Hash functions
For something like MD5, it's possible to make up to, and more than, 5.6 billion guesses per second using commodity hardware.
there are solutions to these problems
A salt is a random sequence of bytes
If each user has their own salt, there is no easy way to group users with identical digests to find users with the same passwords. This largely solves the recognizability problem.
Every password should have its own salt, and that salt should be at least 32 bytes or more to make it much harder to guess both the correct salt and digest.
Stretching
If you create a digest of a password, then create a digest of the digest, and a digest of that digest, and a digest of that digest, you've made a digest that
Adaptive Key Derivation Functions
Adaptive key derivation functions are exactly the functions that generate digests from passwords whilst applying salting and stretching
key derivation functions derive strong keys to
It uses a
its "work factor" which determines how much processing
Its major limitation is that, unlike PBKDF2 and
MD5, SHA-1, SHA-256, SHA-512,
If you are a government contractor, want to
If you want very strong password digests, and a system that is
If you are designing a new system which either relies on encryption to store very sensitive information using a weak secret (user passwords), or where it is
http://throwingfire.com/storing-passwords-securely
- ROT13 ("rotate by 13 places", sometimes hyphenated ROT-13) is a simple letter substitution cipher that replaces a letter with the letter 13 letters after it in the alphabet.
In the basic Latin alphabet, ROT13 is its own inverse;
Applying ROT13 to a piece of text merely requires examining its alphabetic characters and replacing each one by the letter 13 places further along in the alphabet, wrapping back to the beginning if necessary
A becomes N, B becomes O, and so on up to M, which becomes Z,
then the sequence continues at the beginning of the alphabet: N becomes A, O becomes B, and so on to Z, which becomes M
Because there are 26 letters in the English alphabet and 26 = 2 × 13, the ROT13 function is its own inverse
For example, in the following joke, the punchline has
How can you tell an extrovert from an
introvert at NSA? Va
Transforming the entire text via ROT13 form,
the extrovert looks at the OTHER guy's shoes.
http://en.wikipedia.org/wiki/ROT13
- A pseudo-random number generator (PRNG) is a program written for, and used in, probability and statistics applications when large quantities of random digits
are needed are taken are not evenly distributed
the
The digits in the decimal expansions of
But
However, again, the existence of an algorithm to determine the digits in such numbers
The question then becomes, Is the algorithm accurate (that is, random) to infinity, or not?
and because no one can answer such a question definitively because it is impossible to travel to infinity and find out, the matter becomes philosophical.
http://whatis.techtarget.com/definition/pseudo-random-number-generator-PRNG
- A pseudo-random number generator (PRNG) refers to an algorithm that uses mathematical formulas to produce sequences of random numbers. PRNGs generate a sequence of numbers approximating the properties of random numbers. This
is determined is determined
Widely used PRNG algorithms include: linear
A pseudo-random number generator starts from an arbitrary starting state using a seed state. Many numbers
http://www.techopedia.com/definition/25842/pseudo-random-number-generator-prng
- pseudo-
false or not real:
determinism [uncountable]
the belief
—deterministic adjective
arbitrary
decided or arranged
- A
pseudorandom [ truly in that is completely determined Although sequences that are closer to truly random can be generated pseudorandom
http://www.princeton.edu/~
- Hashing is a one-way algorithm; cannot be reversed
Hashing is a technique of creating semi-unique keys based on larger pieces of data.
A hash is a one-way algorithm used to compare input with a reference without compromising the reference.
if you shop using credit-card.
There you will find your credit-card-number with some numbers hidden, this way you can prove with high probability that your card
A
That means the hash of "
This function can obviously not be reversed which is the entire purpose of a hash.
However, note that "
a
Another
Modern hash-algorithms
A rule of thumb is the longer your hash is, the fewer collisions it has.
Hashing typically reduces a large amount of data to a much smaller size. This is useful for verifying the contents of a file without having to have two copies to compare, for example.
Hashing is a one-way task of creating one value from another. The algorithm should try to create a value
Hashing takes an input, runs it through a function, and generates an output that can be a reference to the input.
It is not necessarily unique, a function can generate the same output for different inputs.
Obfuscation is
Obfuscation is hiding some information without a separate key (or with a fixed key).
Encryption is reversible but a "secret"
Encryption can follow several models, one of which is the "secret" method, called private key encryption where both parties have a secret key.
Public key encryption uses a shared one-way key to encrypt and a private recipient key to decrypt. With
Encryption involves storing some secret data, and the security of the secret data depends on keeping a separate "key" safe from the bad guys.
encryption is
Encryption transforms the input into an output
Encryption - using a key to transform data so that only those with the correct key can understand it. The encrypted data can
http://stackoverflow.com/questions/184328/what-is-the-difference-between-obfuscation-hashing-and-encryption
- Spring Security is a Java/Java EE framework that provides authentication, authorization and other security features for enterprise applications. The project
was started [ was incorporated
http://en.wikipedia.org/wiki/Spring_Security
- MAVEN ARTIFACTS
http://www.springsource.org/spring-security#maven
- Specifically, we will see how you can use techniques from cryptography—hashing and salting your passwords
Problem
You want to store passwords securely to prevent anybody—even yourself and other technical staff—from being able to view them.
Solution
In this recipe, we
Spring Security makes it fairly easy to store passwords securely. The actual storage mechanism (database, LDAP or other) doesn’t really matter since that’s abstracted away, which is nice.
Understanding hash functions
The idea behind this recipe is that we want to store passwords in encrypted form in the persistent store.
There are
The two are similar in that each provides a way to encrypt data, but they differ in that only ciphers provide an easy way (assuming you know a secret key) to decrypt the data.
Hash functions don’t provide for easy decryption;
All hash functions, however, are one-way.
When storing encrypted passwords, the typical practice is to use a hash function, such as MD5 or SHA-1, to encrypt the password before saving it.
The reason for preferring a hash function to a cipher is that we
we never (or should never) display it on the screen or in e-mails, for example.
You might ask how we can use stored password hashes to authenticate users if we can’t recover the plaintext password from the hash. The answer is that we don’t compare plaintext passwords, but
Your app has an existing user account model
You also have a service
Meet the dictionary attack
To understand how it works, recall that hashing different strings
As luck would have it, we don’t even have to create our own lookup table. Helpful folks on the Internet have already done it for us. For instance, go to
http://tools.benramsey.com/md5/
3af00c6cad11f7ab5db4467b66ce503e
Voilà! You’ve unhashed a hash.
If an attacker were to
Add a little salt to that hash
The strategy behind salt is to make it much more painful for the attacker to recover hashed passwords.
Instead of allowing
Can he still do it? Sure. But it’s just a lot more work now.
Instead of hashing passwords, we concatenate a string—called a salt—to the plaintext password, and then
Instead of using a common salt across all users, we want the salt to be different for each user. That way, the attacker has to create a new dictionary for every single user he wants to attack. Again, he can do it, but it’s much more time-consuming.
One good way to create a salt is to use some property of the user. It is better to choose something that won’t change, such as a numeric primary key, than it is to choose something that might change, such as an e-mail address. If you use (say) e-mail addresses for salt, and a user changes his e-mail address, he won’t be able to log in anymore because the authentication system won’t be able to create the correct hash.
Usernames are a reasonable choice as they
For example, if my password/salt is
http://springinpractice.com/2008/10/11/hashing-and-salting-passwords-with-spring-security-2/
- The Dos
Okay, enough lecturing on what not to do. Here are the things you need to focus on:
Choose a one-way encryption algorithm. As I mentioned above, once you’ve encrypted and stored a user’s password, you never need to know the real value again. When a user attempts to authenticate, you’ll just apply the same algorithm to the password they entered, and compare that to the encrypted password
Make the encryption as slow as your application can tolerate. Any modern password encryption algorithm should allow you to provide parameters that increase the time needed to encrypt a password (i.e. in PBKDF2, specifying the number of iterations). Why is slow good? Your users won’t notice if it takes an extra 100ms to encrypt their password, but a hacker trying a brute-force attack will notice the difference as they run the algorithm billions of times.
Pick a well-known algorithm. The National Institute of Standards and Technology (NIST) recommends PBKDF2 for passwords.
- PBKDF2
- Cryptographic hash functions
- The SHA hash functions are a set of cryptographic hash functions designed by the National Security Agency (NSA) and published by the NIST as a U.S. Federal Information Processing Standard
- The MD5 message-digest algorithm is a widely used cryptographic hash function producing a 128-bit (16-byte)
hash
- Cryptography Goals
- what is cipher?
- ChatGPT
- substitution cipher
- Transposition cipher
- Caesar cipher
- Bijection
- Compared Algorithms
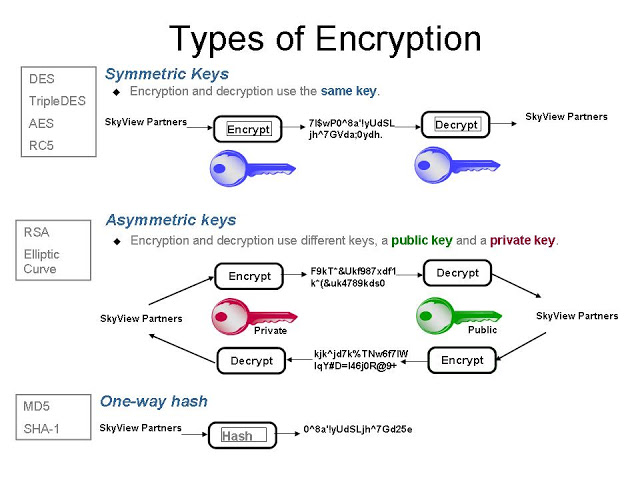
- Symmetric and Asymmetric encryptions
Both of this cryptography,
https://mindmajix.com/cyber-security-interview-questions
- Symmetric and Asymmetric Encryption
- Gemini
- ChatGPT
- ChatGPT
Symmetric Encryption and Asymmetric Encryption are two fundamental approaches to encryption, each with distinct characteristics and use cases. Here’s an explanation of their differences and best use cases:
Symmetric Encryption
Definition: Symmetric encryption uses the same key for both encryption and decryption. This means that the sender and the recipient must both have the same secret key.
Characteristics:
- Single Key: The same key is used to encrypt and decrypt the data.
- Speed: Typically faster and more efficient for encrypting large amounts of data compared to asymmetric encryption.
- Key Management: Secure distribution and management of the key are crucial, as anyone with the key can decrypt the data.
Best Use Cases:
- Data at Rest: Encrypting files or databases where data is stored and needs to be accessed only by authorized users.
- Secure Communication Channels: Used in conjunction with asymmetric encryption for securely exchanging symmetric keys (e.g., SSL/TLS).
- Disk Encryption: Encrypting entire disks or partitions (e.g., BitLocker).
Examples:
- AES (Advanced Encryption Standard): Widely used symmetric cipher known for its security and efficiency.
- DES (Data Encryption Standard): An older cipher, now considered insecure for many applications due to its short key length.
Example Scenario:
- Encrypting sensitive data files on a hard drive to ensure that only authorized users can access them.
Asymmetric Encryption
Definition: Asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. The public key is shared openly, while the private key is kept secret.
Characteristics:
- Key Pair: Utilizes a pair of keys (public and private). Data encrypted with the public key can only be decrypted with the corresponding private key.
- Security: Provides secure communication without needing to share a secret key, addressing the key distribution problem.
- Performance: Generally slower than symmetric encryption, especially for large amounts of data, due to the complexity of the algorithms.
Best Use Cases:
- Secure Key Exchange: Used to exchange symmetric keys securely over an insecure channel (e.g., during the initial handshake in SSL/TLS).
- Digital Signatures: Ensures the authenticity and integrity of data, allowing verification of the sender’s identity and data integrity.
- Public Key Infrastructure (PKI): Manages digital certificates and encryption keys to secure communications and authenticate users.
Examples:
- RSA (Rivest-Shamir-Adleman): A widely used asymmetric encryption algorithm, commonly used for secure data transmission and digital signatures.
- ECC (Elliptic Curve Cryptography): Provides strong security with smaller key sizes, used in modern secure communication protocols.
Example Scenario:
- Encrypting an email with the recipient’s public key, so only the recipient can decrypt it with their private key.
Summary of Differences:
Key Usage:
- Symmetric Encryption: Uses a single shared key for both encryption and decryption.
- Asymmetric Encryption: Uses a pair of keys (public and private) for encryption and decryption.
Performance:
- Symmetric Encryption: Generally faster and more efficient for large data volumes.
- Asymmetric Encryption: Slower, typically used for encrypting small amounts of data or for key exchange.
Key Management:
- Symmetric Encryption: Requires secure key distribution and management.
- Asymmetric Encryption: Solves key distribution issues by using public keys for encryption and private keys for decryption.
Use Cases:
- Symmetric Encryption: Best for encrypting data at rest or within secure channels where key management is feasible.
- Asymmetric Encryption: Ideal for secure key exchange, digital signatures, and scenarios where key distribution and management are challenging.
Both encryption types are often used together in modern security systems. Asymmetric encryption is used to securely exchange symmetric keys, which are then used to encrypt the actual data due to their efficiency.
-
Asymmetric encryption is used a large number of
- Symmetric encryption
- As a general rule, one can say that asymmetric algorithms are much more computing intensive than symmetric algorithms. Thus it is
very an asymmetric algorithms be used to It is also considered
Asymmetric
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
- In cryptography, the
ElGamal which on the Diffie–Hellman key exchange.is based
PGP is commonly used
- With PGP you must maintain both your public and private keys.
A Information GpgOL
- Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication.
PGP is often used
- OpenPGP is the most widely used email encryption standard in the world. It
by the OpenPGP Working Group of the Internet Engineering Task Force (IETF) Proposed Standard RFC 4880. is defined from PGP (Pretty Good Privacy), first created by Phil Zimmermann in 1991. The OpenPGP standard was originally derived
- Pretty Good Privacy (PGP) is a way to protect your email communications from being read by anyone except their intended recipients. It can protect against companies, governments, or criminals spying on your Internet connection, and, to a lesser extent, it can save your email from being read if the computer on which
they are stored is stolen
- Using PGP doesn't completely encrypt your email: the sender and receiver information is still
unencrypted
Enigmail Seamonkey OpenPGP
- Windows installers of GnuPG 2.0 are available from Gpg4win, a sibling project to GnuPG. This is the recommended installer for
Enigmail
for file and email encryption. Gpg4win (GNU Privacy Guard for Windows) is Free Software and canbe installed mice
- How to enable Email Encryption in Outlook 2013
- How to Encrypt Gmail, Outlook, or Yahoo
Webmail
- How to: Use PGP for Windows
ExQuilla
- Exchange with Thunderbird
- PGP Tutorial For Windows (Kleopatra
–
- Secure your email with Gpg4win. Part 1: introduction and installation
- E-mail Encryption for Beginners: Gpg4Win, Outlook Privacy Plugin, and
Mailvelope
- How to verify signatures for packages
Digital signature is a process ensuring that a certain package
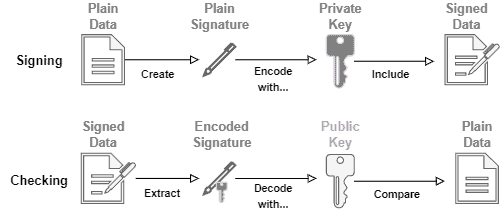
Digital signature is a cryptographic mechanism. If you want to learn more about how it works see https://en.wikipedia.org/wiki/Digital_signature.
What is a signature and why should I check it?
How do you know that the Tor program you have is really the one we made? Digital signatures ensure that
For many Tor users it is important to verify that the Tor software is authentic as they have
If the Tor package has
Before you
Always download Tor from
There are a variety of attacks that can
Always make sure you are browsing over
https://www.torproject.org/ uses
Large companies sometimes force employees to use a
Always verify signatures of packages you have downloaded
Some software sites list sha1 hashes alongside the software on their website, so users can verify that they downloaded the file
Where do I get the signatures and the keys that made them?
Each file on our download page
We now show how you can verify the downloaded file's digital signature on different operating systems. Please notice that
Windows
First
Once it's installed, use
Unless you edit your PATH environment variable, you will need to tell Windows the full path to the GnuPG program. If you installed GnuPG with the default values, the path should be something like this: C:\Program Files\Gnu\
The Tor Browser team signs Tor Browser releases. Import its key (0x4E2C6E8793298290) by starting cmd.exe and typing:
"C:\Program Files\Gnu\
After importing the key, you can verify that the fingerprint is correct:
"C:\Program Files\Gnu\
You should see:
pub 4096R/93298290 2014-12-15
Key fingerprint = EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
sub 4096R/F65C2036 2014-12-15
sub 4096R/D40814E0 2014-12-15
sub 4096R/C3C07136 2016-08-24
To verify the signature of the package you downloaded, you will need to download the "
"C:\Program Files\Gnu\
Please substitute "Alice" with your own username.
The output should say "Good signature":
Primary key fingerprint: EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
5242 013F 02AF C851 B1C7 36B8 7017 ADCE F65C 2036
BA1E E421 BBB4 5263 180E 1FC7 2E1A C68E D408 14E0
A430 0A6B C93C 0877 A445 1486 D148 3FA6 C3C0 7136
Notice that there is a warning because you haven't assigned a trust index to this person. This means that
The next step is to use
After importing the key, you can verify that the fingerprint is correct:
You should see:
pub 4096R/93298290 2014-12-15
Key fingerprint = EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
sub 4096R/F65C2036 2014-12-15
sub 4096R/D40814E0 2014-12-15
sub 4096R/C3C07136 2016-08-24
To verify the signature of the package you downloaded, you will need to download the "
For Linux users (change 64 to 32 if you have the 32-bit package):
The output should say "Good signature":
Primary key fingerprint: EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
https://www.torproject.org/docs/verifying-signatures.html.en
- Verify on Windows
How to verify with PGP/ASC signatures
There are a few tools available like "Gpg4win", "GnuPG" just to name a few and not to prefer a specific tool. For the following instructions "
For verifying signatures you need the software "GnuPg". This is a tool that runs not in the graphical mode but in the command prompt of Windows.
Save the following file with your Internet browser to the location where the downloaded AOO and PGP/ASC file
https://www.apache.org/dist/openoffice/KEYS
Open the start menu and enter cmd.exe into the search box.
Now change to the directory with the downloaded AOO, KEYS and PGP/ASC file, import and verify with the following commands:
cd <
C:\Program Files\Gnu\
C:\Program Files\Gnu\
If the signature matches the
Otherwise with "BAD signature from ...".
Verify on Linux
How to verify with PGP/ASC signatures
Open a terminal and change to the directory with the downloaded AOO and PGP/ASC file.
Type in the following commands:
cd <
https://www.openoffice.org/download/checksums.html
GnuPG OpenPGP GnuPG as well as GnuPG command line
https://gnupg.org/download/
- Diffie–Hellman key exchange is a specific method of exchanging cryptographic keys.
- Benefits/Drawbacks
- Public-key cryptography, also known as asymmetric cryptography, is a class of cryptographic protocols based on algorithms that require two separate keys, one of which is secret (or private) and one of which is public. Although different, the two parts of this key pair
are mathematically linked The public key is used whereas the private key is used –
- Because the key pair
is mathematically related whatever is encrypted be decrypted
- PKI (public key infrastructure)
- In cryptography, a PKI is an arrangement that binds public keys with respective user identities
by means of
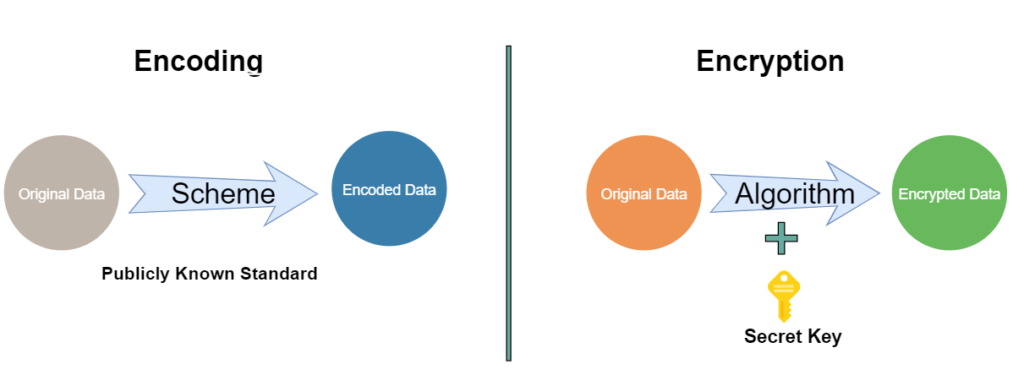
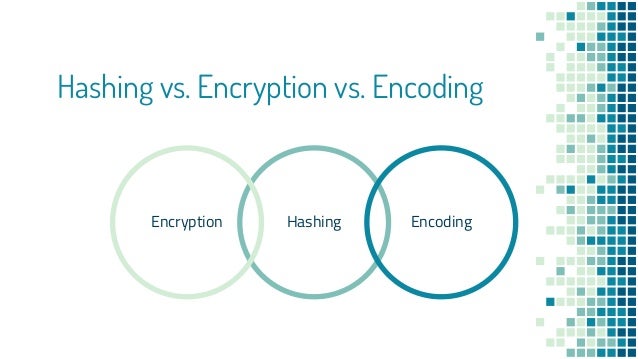
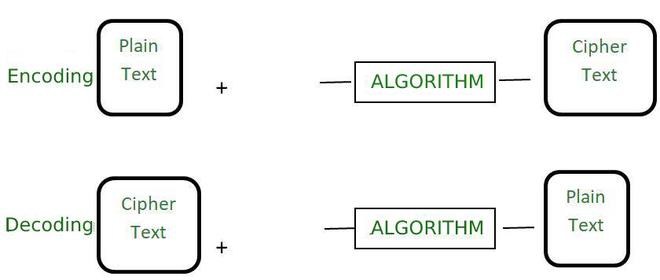
- Encoding, encryption, and hashing are all techniques used to transform data, but they have different purposes.
Encoding is the process of converting data from one format to another. For example, encoding text into ASCII or Unicode allows it to be displayed on a computer screen. Encoding can also be used to compress data, such as when using a JPEG or PNG image format.
Encryption is the process of converting data into a format that cannot be read by unauthorized users. This is done by using a mathematical algorithm and a secret key. Encryption is used to protect sensitive data, such as credit card numbers and passwords.
Hashing is the process of converting data into a fixed-length string of characters. This is done by using a mathematical algorithm. Hashing is often used to verify the integrity of data, such as when checking for file corruption or downloading a software update.
Here is a table that summarizes the key differences between encoding, encryption, and hashing:
Here are some examples of how encoding, encryption, and hashing are used in the real world:
- Encoding: When you type a web address into your browser, the browser encodes it into a format that can be understood by the web server. When you send an email, the email client encodes the message into a format that can be transmitted over the internet.
- Encryption: When you use a credit card to make an online purchase, the credit card number is encrypted before it is transmitted to the merchant. When you use a password to log into a website, your password is encrypted before it is stored on the website's server.
- Hashing: When you download a software update, the update file is typically hashed and the hash is compared to a known hash to verify that the file is not corrupted. When you create a password for a website, the website typically hashes the password and stores the hash instead of the plain text password.
- WHAT’S THE DIFFERENCE BETWEEN ENCODING, ENCRYPTION, AND HASHING?
Encoding, encryption, and hashing are three distinct techniques used in information security and data representation. They serve different purposes and have unique characteristics:
Encoding:
- Purpose: Encoding is primarily used for data transformation, not security. It's a way to represent data in a different format while ensuring it remains readable and easily reversible.
- Reversibility: Encoding is generally reversible; you can decode the data to its original form.
- Example: Base64 encoding is commonly used to represent binary data as text.
Encryption:
- Purpose: Encryption is used for data security. It transforms data into an unreadable format to protect its confidentiality. Only authorized parties with the decryption key can revert it to the original form.
- Reversibility: Encryption is reversible with the decryption key.
- Example: AES (Advanced Encryption Standard) is a widely-used encryption algorithm.
Hashing:
- Purpose: Hashing is used for data integrity and verification, not for encryption. It converts data into a fixed-size hash value (digest) that represents the original data. Hashing is a one-way process; you cannot reverse it to retrieve the original data.
- Reversibility: Hashing is not reversible. The same input will always produce the same hash value, but you cannot determine the original input from the hash value.
- Example: The SHA-256 (Secure Hash Algorithm 256-bit) produces a 256-bit hash value.
In summary, encoding transforms data into a different format for various purposes, encryption is used to secure data by making it unreadable, and hashing creates a fixed-size representation of data to verify its integrity without revealing the original content. Each technique serves a specific role in information security and data processing.
- “What is the difference between a threat, vulnerability, and a risk
?
https://www.simplilearn.com/cyber-security-interview-questions-and-answers-article
- WHAT’S THE DIFFERENCE BETWEEN ENCODING, ENCRYPTION, AND HASHING?
https://danielmiessler.com/study/infosec_interview_questions/#gs
1. Encoding: Encoding converts the data in a desired format required for exchange between different systems. This doesn’t convert it into a secret data, but usable data. It can
2. Hashing: This serves for maintaining the integrity of a message or data. This way if any day it
3. Encryption: Encryption ensures that the data is secure and one needs a digital verification code or image
https://mindmajix.com/cyber-security-interview-questions
5. What is the difference between encryption and hashing?
Point 1: Encryption is reversible whereas hashing is irreversible.
Point 2: Encryption ensures confidentiality whereas hashing ensures Integrity.
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
- Elliptic curve cryptography
https://en.wikipedia.org/wiki/Elliptic_curve_cryptography
When you create a bitcoin address for yourself (or an address/account for any other cryptocurrency), you generate the private key first. From the private key, you compute the corresponding public key and by hashing that public key you get your address.
Public-key cryptography
Public keys, private keys, and digital signatures form the basic components of public-key cryptography.
It is computationally infeasible to derive the private key corresponding to a
It is possible to prove that one knows the private key corresponding to a public key
One way to do public-key cryptography is with elliptic curves. Another way is with RSA, which revolves around prime numbers. Most cryptocurrencies — Bitcoin and Ethereum included — use elliptic curves, because a 256-bit elliptic curve private key is just as secure as a 3072-bit RSA private key
Conclusion
If you want to obtain a Bitcoin address or Ethereum account, you generate a random 256-bit integer x.
x is then your private key.
Then you compute X=
X will be your public key.
Your public key is safe to give out and cannot
If you
https://hackernoon.com/what-is-the-math-behind-elliptic-curve-cryptography-f61b25253da3
- What is Elliptic Curve Cryptography?#
it’s ability to provide the same level of security as RSA with a much smaller key size.
ECC vs RSA#
The difference in size to yield the same amount of security between RSA and ECC keys is
Why is ECC Important?
For keys of the same size, solving for an elliptic curve discrete logarithm is significantly harder than factoring, which is how RSA encrypts keys.
https://www.keycdn.com/support/elliptic-curve-cryptography
- A cryptographic accumulator is a one-way membership function. It answers a query
as to
- After much debate,
the Skipjack algorithm was finally declassified and published by the NSA
It used an 80-bit key and a symmetric cipher algorithm, similar to DES.
Skipjack is an encryption algorithm for the transmission of information (voice data in particular), developed by the National Security Agency (NSA) in the USA. It uses the Diffie-Hellman key exchange algorithm for the distribution of the cryptographic session keys between peers.
https://www.cryptomuseum.com/crypto/usa/skipjack.htm
- In cryptography, Skipjack is a block cipher—an algorithm for encryption—developed by the U.S. National Security Agency (NSA). Initially classified,
it was originally intended use in was declassified
https://en.wikipedia.org/wiki/Skipjack_(cipher)
sMPC
Secure multi-party computation
a subfield of cryptography with the goal of creating methods for parties
traditional cryptographic tasks where cryptography
the adversary in this model controls actual participants.
traditionally, cryptography was about concealing content
this new
mental poker, cryptographic work that simulates game playing/ computational tasks over distances without requiring a trusted third party
https://en.wikipedia.org/wiki/Secure_multi-party_computation
- S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard for public key encryption and signing of MIME data.
https://en.wikipedia.org/wiki/S/MIME
TrueCrypt
http://truecrypt.sourceforge.net/
BitLocker
http://blogs.technet.com/b/uspartner_ts2team/archive/2010/03/17/what-is-bitlocker-what-does-it-do-what-does-it-not-do.aspx
- X.509 certificate
An X.509 certificate is a digital certificate that uses the widely accepted international X.509 public key infrastructure (PKI) standard to verify that a public key belongs to the user, computer or service identity contained within the certificate.
Many of the certificates that people refer to as Secure Sockets Layer (SSL) certificates are in fact X.509 certificates.
http://searchsecurity.techtarget.com/definition/X509-certificate
- x.509 “client certificate” vs a normal SSL certificate
On the web, with HTTPS, usually the server has a server
However, in many programmatic contexts, you will typically want both endpoints to authenticate each other. Therefore, you will want to use both server certs and client certs.
In TLS, all certificates are x.509 certificates. x.509 is just the format of the data.
https://security.stackexchange.com/questions/1438/what-is-the-difference-between-an-x-509-client-certificate-and-a-normal-ssl-ce
- What is an SSL Certificate?
TLS (Transport Layer Security) is just an updated, more secure, version of SSL. We still refer to our security certificates as SSL because it is a more commonly used term, but when you are buying SSL from
https://www.websecurity.symantec.com/security-topics/what-is-ssl-tls-https
- What is an SSL Certificate and How Does it Work?
SSL certificates create an encrypted connection and establish trust.
SSL certificates have a key pair: a public and a private key. These keys work together to establish an encrypted connection.
The certificate also contains
To get a certificate, you must create a Certificate Signing Request (CSR) on your server.
This process creates a private key and public key on your server.
The CSR data file
The CA uses the CSR data file to create a data structure to match your private key without compromising the key itself.
The CA never sees the private key.
Once you receive the SSL certificate, you install it on your server. You also install an intermediate certificate that establishes the credibility of your SSL Certificate by tying it to your CA’s root certificate. The instructions for installing and testing your certificate will be different depending on your server.
The most important part of an SSL certificate is that it
What is Secure Sockets Layer (SSL)?
Secure Sockets Layer (SSL) is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser, or a mail server and a mail client (e.g., Outlook).
All browsers
How Does the SSL Certificate Create a Secure Connection?
When a browser attempts to access a website that
Essentially, three keys
Because encrypting and decrypting with private and public key takes a lot of processing power,
After
Browser connects to a web server (website) secured with SSL (
Server sends a copy of its SSL Certificate, including the server’s public key.
Browser checks the certificate root against a list of trusted CAs and that the certificate is unexpired, unrevoked, and that its common name is valid for the website
Server decrypts the symmetric session key using its private key and sends back an acknowledgement encrypted with the session key to start the encrypted session.
Server and Browser now encrypt all transmitted data with the session key.
Is My Certificate SSL or TLS?
However, when the time came to update from SSLv3.0, instead of calling the new version SSLv4.0, it
When you purchase an SSL Certificate from us (e.g., Standard SSL, Extended Validation SSL, etc.), you are
https://www.digicert.com/ssl/
- Behind the Scenes of SSL Cryptography
Asymmetric Encryption
Asymmetric encryption (or public-key cryptography) uses a separate key for encryption and decryption.
The most common asymmetric encryption algorithm is RSA
Symmetric Encryption
Symmetric encryption (or pre-shared key encryption) uses a single key to both encrypt and decrypt data.
Public-Key Encryption Algorithms
RSA
ECC
Elliptic curve cryptography (ECC) relies on the algebraic structure of elliptic curves over finite fields.
Pre-Shared Key Encryption Algorithms
Pre-shared key encryption (symmetric) uses algorithms like
https://www.digicert.com/ssl-cryptography.htm
- There are two distinct ways that a program can
initiate
By Port (a
By Protocol (a
The “By Port” method
the POODLE vulnerability
Even before the POODLE
the BEAST attack that can completely break web sites running on older SSL v3.0 and TLS v1.0 protocols.
In email programs and other systems where you can select from SSL or
SSL means a “by port” explicit connection to a port that expects to the session to start with security negotiation
TLS means a “by
Use of either could
Both methods of connection (implicit and explicit) result in equally secure communications.
https://luxsci.com/blog/ssl-versus-tls-whats-the-difference.html
- HTTPS and SSL tutorial
SSL lets an application
to establish a secure connection
types of
server sends a digital certificate which includes
- How SSL works tutorial - with HTTPS example
Encryption and identification
identification
Why SSL exists?
- SSL
SSL (Secure Sockets Layer) is the standard security technology for establishing an encrypted link between a web server and a browser.
This link ensures that all data passed between the web server and browsers remain private and integral. SSL is an industry standard and
http://info.ssl.com/article.aspx?id=10241
- SSL Handshake
Essentially, three keys
Because encrypting and decrypting with private and public key takes a lot of processing power,
Browser connects to a web server (website) secured with SSL (
Server sends a copy of its SSL Certificate, including the server’s public key.
Browser checks the certificate root against a list of trusted CAs and that the certificate is unexpired, unrevoked, and that its common name is valid for the website
Server decrypts the symmetric session key using its private key and sends back an acknowledgement encrypted with the session key to start the encrypted session.
Server and Browser now encrypt all transmitted data with the session key.
https://www.digicert.com/ssl.htm
- That will start the SSL/TLS negotiation:
Keys and Secrets during RSA SSL negotiation
The following is a standard SSL handshake when RSA key exchange algorithm
Client Hello
- Information that the server needs to communicate with the client using SSL.
- Including SSL version number, cipher settings, session-specific data.
Server Hello
- Information that the client needs to communicate with the server using SSL.
- Including SSL version number, cipher settings, session-specific data.
- Including Server’s Certificate (Public Key)
Authentication and Pre-Master Secret
- Client authenticates the server certificate. (e.g. Common Name / Date / Issuer)
- Client (depending on the cipher) creates the pre-master secret for the session,
- Encrypts with the server's public key and sends the encrypted pre-master secret to the server.
Decryption and Master Secret
- Server uses its private key to decrypt the pre-master secret,
- Both Server and Client perform steps to generate the master secret with the agreed cipher.
Generate Session Keys
- Both the client and the server use the master secret to generate the session keys, which are symmetric keys used to encrypt and decrypt information exchanged during the SSL session
Encryption with Session Key
- Both client and server exchange messages to inform that future messages will
http://www.symantec.com/connect/blogs/how-does-ssl-work-what-ssl-handshake
- What is SSL and what are Certificates?
A browser requests a secure page (usually
The web server sends its public key with its certificate.
The browser checks that the certificate
The browser then uses the public key, to encrypt a random symmetric encryption key and sends it to the server with the encrypted URL required
The web server decrypts the symmetric encryption key using its private key and uses the symmetric key to decrypt the URL and http data.
The web server sends back the requested html document and http data encrypted with the symmetric key.
The browser decrypts the http data and html document using the symmetric key and displays the information.
http://www.tldp.org/HOWTO/SSL-Certificates-HOWTO/x64.html
- Transport Layer Security
https://en.wikipedia.org/wiki/Transport_Layer_Security
- The main difference is that, while SSL connections begin with security and proceed directly to
secured secured the connection is never created
https://security.stackexchange.com/questions/5126/whats-the-difference-between-ssl-tls-and-https
- POODLE Attack and SSLv3 Deployment
https://poodle.io/
- Tracking the FREAK Attack
https://freakattack.com/
- Weak Diffie-Hellman and the Logjam Attack
https://weakdh.org/
- All mail sent to and from Intermedia servers will attempt to make a TLS connection, using Opportunistic TLS. When sending using Opportunistic TLS, if
a TLS connection cannot be established
When a message
https://kb.intermedia.net/article/22904
- What is an X.509 Certificate?
An X.509 certificate binds a name to a public key value. The role of the certificate is to associate a public key with the identity
Authentication of a secure application depends on the integrity of the public key value in the application's certificate. If an impostor replaces the public key with its own public key, it can impersonate the true application and gain access to secure data.
To prevent this
Contents of an X.509 certificate
An X.509 certificate contains information about the certificate subject and the certificate
The role of a certificate is to associate an identity with a public key value. In more detail, a certificate includes:
A subject distinguished name (DN) that identifies the certificate owner.
The public key associated with the subject.
X.509 version information.
A serial number that uniquely identifies the certificate.
An issuer DN that identifies the CA that issued the certificate.
The digital signature of the issuer.
Information about the algorithm used to sign the certificate.
Some optional X.509 v.3 extensions; for example, an extension exists that distinguishes between CA certificates and end-entity certificates.
https://access.redhat.com/documentation/en-US/Fuse_ESB_Enterprise/7.1/html/ActiveMQ_Security_Guide/files/X509CertsWhat.html
- ChatGPT
Comparing Solutions
| Feature | Microsoft CA | Entrust | Venafi | AppViewX | Keyfactor | OpenSSL |
|---|---|---|---|---|---|---|
| Best for | Internal PKI | Enterprise PKI | Machine identity | DevOps automation | IoT security | Small setups |
| Cost | Moderate | High | High | Moderate | High | Free |
| Ease of Use | Easy (Windows) | Moderate | Complex | Easy | Moderate | Complex (CLI) |
| Automation | Moderate | Advanced | Advanced | Advanced | Advanced | Minimal |
| Cloud Integration | Limited | High | High | High | High | Minimal |
Best Practices for Using These Solutions
- Automation: Use platforms like Venafi or AppViewX to automate certificate issuance and renewal, reducing manual errors.
- Monitoring: Ensure real-time monitoring of certificates to prevent expiration-related outages.
- Scalability: Choose solutions like Keyfactor or Entrust for large-scale or IoT deployments.
- Compliance: Ensure compliance with industry regulations by leveraging tools like Entrust for advanced auditing and reporting.
- Open Source: Use OpenSSL for small projects or as a supplementary tool for testing and development.
Conclusion
Choosing the right CA and certificate lifecycle management solution depends on your organization's size, infrastructure, and security needs. For example:
- Microsoft CA is ideal for Windows-centric enterprises.
- Entrust and Keyfactor are excellent for large-scale or IoT deployments.
- Venafi and AppViewX cater well to DevOps and cloud environments.
- OpenSSL is best for smaller, cost-sensitive projects or individual use.
- Gemini
- X.509 Digital Certification
X.509 digital certificates include not only a user's name and public
X.509 certificates and many other certificates have a valid time duration. A certificate can expire and no longer be valid. A CA can revoke a certificate for
https://msdn.microsoft.com/en-us/library/windows/desktop/aa388452(v=vs.85).aspx
- In cryptography, X.509 is an important standard for a public key infrastructure (PKI) to manage digital certificates
[ [
X.509 specifies formats for public key certificates, certificate revocation lists, attribute certificates, and a certification path validation algorithm.
- Sage
http://doc.sagemath.org/html/en/tutorial/index.html
- steganography
Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message,
http://en.wikipedia.org/wiki/Steganography
s teganalysis
http://en.wikipedia.org/wiki/Steganography_detection
- What is Steganography?
Steganography is the science of hiding
Some terms related to Steganography:
http://www.openstego.com/
- I shall talk about how to detect the existence of hidden information such
as innocent
The word steganography comes from the Greek name “
Steganography hides the existence of a message by transmitting information through various carriers. Its goal is to prevent the
detection of a secret message
For example, the result of information hidden within a cover image is a
n within a video is a
cover medium + hidden information +
For example, some photo agencies will use steganography to create digital “watermarks” of their pictures to protect their trademark
Steganography
allowed or would raise suspicion.
Watermarking:
-Protects copyright owners of digital documents by hiding a signature in the information in a way that even a
-Prevents discovery by marking in a hidden and unique way every copy of a confidential document.
Cover channel:
-Allows people to communicate
-Allows non-
There are two
Image domain tools include bit-wise methods that apply least significant bit (LSB) insertion and noise manipulation. The tools used in this group are
Windows 95
The transform domain tools include those groups that manage algorithms and image transforms such as Discrete Cosine Transformation (DCT)
https://www.sans.org/reading-room/whitepapers/stenganography/steganalysis-detecting-hidden-information-computer-forensic-analysis-1014
- What is Digital Watermarking?
Digital Watermarking is
http://www.openstego.com/
- Knapsack Problem
Fractional knapsack problem
The setup is same, but the thief can take fractions of items, meaning that the items can
Exhibit greedy choice property.
Greedy algorithm exists
0-1 knapsack problem
Exhibit No greedy choice property.
No greedy algorithm exists.
Exhibit optimal substructure property.
Only dynamic programming algorithm exists.
http://www.personal.kent.edu/~
- Public Key Algorithm Cryptography based on the Knapsack Problem
http://www.cs.fsu.edu/~
- Daily Tip: how to use QR codes on your iPhone or iPad
- Create your QR code for free
http://www.qr-code-generator.com/
- 5 Ways to Use QR Codes
1) QR your business card:
2) QR your print advertisements:
3) QR your business stationery and invoices:
4) QR your events:
5) QR your inventory:
http://www.waspbarcode.com/buzz/5-ways-qr-codes/
- QR code (abbreviated from Quick Response Code) is the trademark for a
type of it is attached byte to efficiently store extensions may also be used
https://en.wikipedia.org/wiki/QR_code
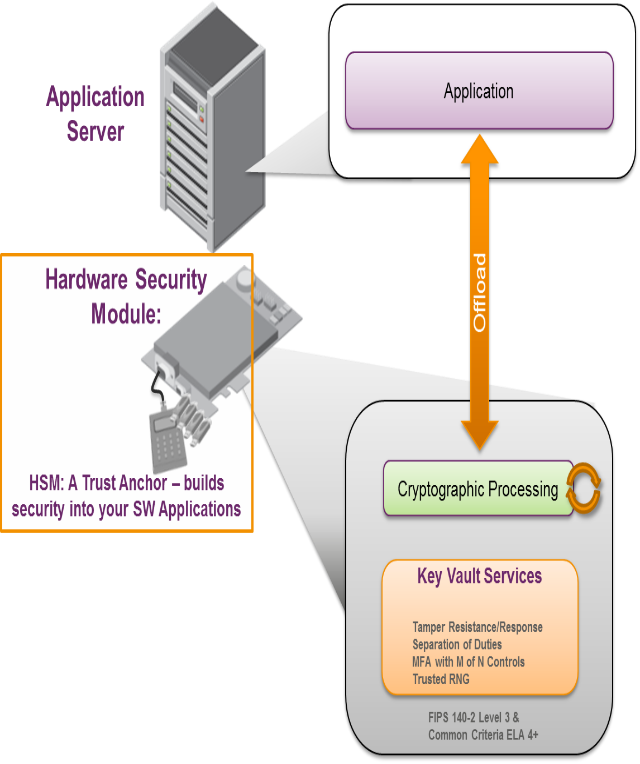
- A hardware security module (HSM) is a dedicated crypto processor that
is specifically designed the protection of lifecycle
https://safenet.gemalto.com/data-encryption/hardware-security-modules-hsms/
- TPM and HSM
TPM and HSM are two types of hardware modules used for encryption. Trusted Platform Module (TPM) and a hardware security module (HSM) can
TPM
A Trusted Platform Module (TPM) is a hardware chip on the computer’s motherboard that stores cryptographic keys used for encryption.
Once enabled, the Trusted Platform Module provides full disk encryption capabilities. It keeps hard drives locked, or sealed, until the system completes a system verification or authentication process.
The TPM includes a unique RSA key burned into it,
HSM
A hardware security module (HSM) is a security device you can add to a system to manage, generate, and securely store cryptographic keys.
High performance HSMs are external devices connected to a network using TCP/IP. Smaller HSMs come as expansion cards you install within a server, or as devices you plug into computer ports.
One of the noteworthy differences between the two is that HSMs are removable or external devices. In comparison, a TPM is a chip
https://blogs.getcertifiedgetahead.com/tpm-hsm-hardware-encryption-devices/
RedHat JBoss RedHat ProtectServer
https://safenet.gemalto.com/partners/redhat/
- Enterprises running Exchange Server have been operating under a false sense of security
with regard to