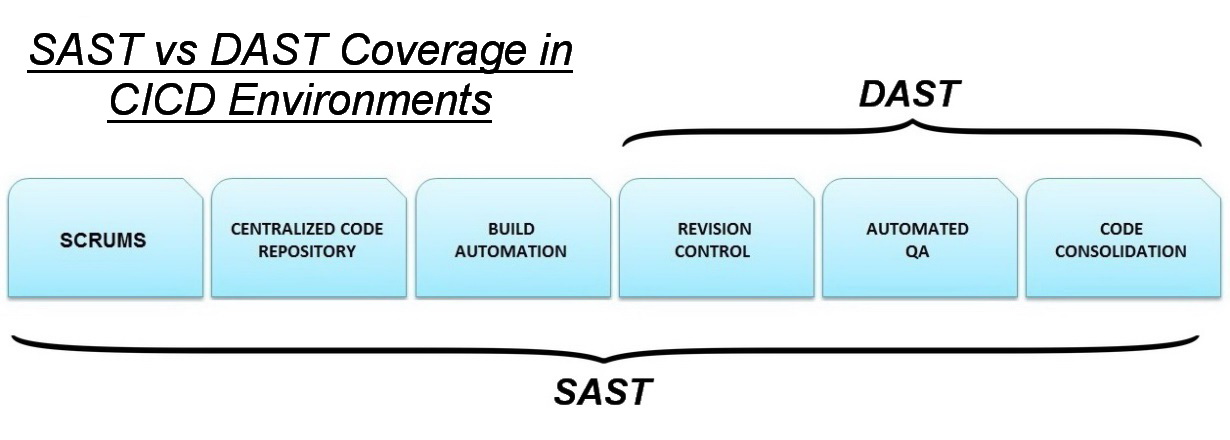
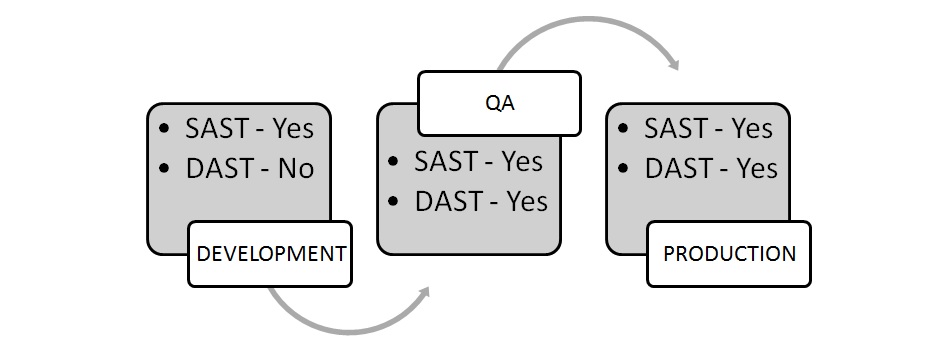
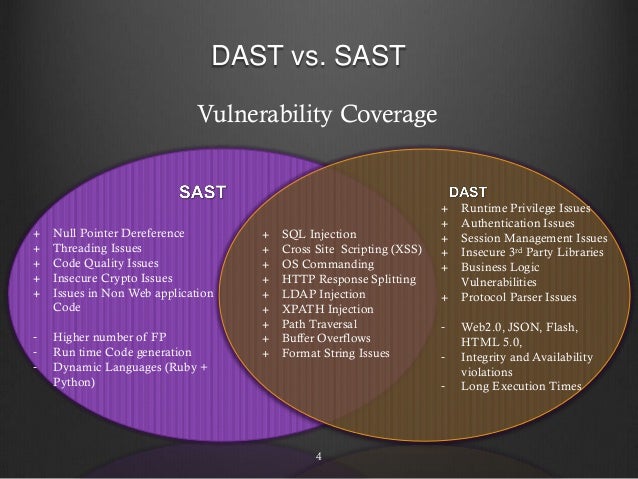
tools that scan web applications, normally from the outside, to look for security vulnerabilities such as Cross-site scripting, SQL Injection, Command Injection, Path Traversal and insecure server configuration.
to as Dynamic Application Security Testing (DAST) Tools.
detect conditions indicative of a security vulnerability in an application in its running state. Most DAST solutions test only the exposed HTTP and HTML interfaces of Web-enabled applications; however, some solutions
specifically for non-Web protocol and data malformation (for example, remote procedure call, Session Initiation Protocol [SIP] and so on).
http://www.gartner.com/it-glossary/dynamic-application-security-testing-dast/
- Application security can help organizations protect all kinds of applications (such as legacy, desktop, web, mobile, micro services) used by internal and external stakeholders including customers, business partners and employees
Why Application Security?
As validated by multiple studies, the majority of successful breaches target exploitable vulnerabilities residing in the application layer, indicating the need for enterprise IT departments to be extra vigilant about application security.Now, the software supply chain is much more complicated considering the outsourced development, the number of legacy applications, coupled with in-house development that takes advantage of 3rd party, open source and commercial, off-the-shelf software components.
Organizations need application security solutions that cover all of their applications, from those used internally to popular external apps used on customers’ mobile phones.
These solutions must cover the entire development stage and offer testing after an application is put into use to monitor for potential problems.
What is SAST?
Static Application Security Testing (SAST) scans the application source files, accurately identifies the root cause and helps remediate the underlying security flaws.
Developer Benefits of Static Application Security Testing:
Fully integrated with the Integrated Developer Environment (IDE)
What is DAST?
Dynamic Application Security Testing (DAST) simulates controlled attacks on a running web application or service to identify exploitable vulnerabilities in a running environment.
Benefits of Dynamic Application Security Testing:
Provides a comprehensive view of application security by focusing on what’s exploitable and covering all components (server, custom code, open source, services)
Can be integrated into Dev, QA and Production to offer a continuous holistic view
Tests functional app, so unlike SAST, is not language constrained and runtime and environment-related issues can be discovered
https://www.microfocus.com/en-us/what-is/application-security
- What is Dynamic Application Security Testing (DAST)?
Dynamic Application Security Testing (DAST) is the process of analyzing a web application through the front-end to find vulnerabilities through simulated attacks.This type of approach evaluates the application from the “outside in” by attacking an application like a malicious user would.
Pros of DAST
Independent of the application
Immediately finds vulnerabilities that could be exploited
Does not require access to the source code
Cons of DAST
Does not find the exact location of a vulnerability in the code
Security knowledge is needed to interpret reports
Test can be time-consuming
There are many ways to test application security, including:
Static Application Security Testing (SAST)
Dynamic Application Security Testing (DAST)
Mobile Application Security Testing (MAST)
Interactive Application Security Testing (IAST)
Why is DAST Important?
Human error will inevitably play a part at some point in the Software Development Life Cycle (SDLC), and the sooner a vulnerability is caught during the SDLC, the cheaper it is to fix.
When DAST is included as part of the Continuous Integration/Continuous Development (CI/CD) pipeline, this is referred to as “Secure DevOps,” or “DevSecOps.”
How does DAST work?
A DAST scanner searches for vulnerabilities in a running application and then sends automated alerts if it finds flaws that allow for attacks like SQL injections, Cross-Site Scripting (XSS), and more. Since DAST tools are equipped to function in a dynamic environment, they can detect runtime flaws which SAST tools can’t identify.
What is the difference between SAST and DAST?
SAST, on the other hand, analyzes static environments, meaning the source code of an application. It looks at the application from the “inside out,” searching for vulnerabilities in the code.
To maximize the strength of your security posture, it’s a best practice to use both SAST and DAST. Having this unified taxonomy across testing methods enables you to have a complete view of vulnerabilities.
https://www.microfocus.com/en-us/what-is/dast
- ZAPGETTINGSTARTEDGUIDE-2.7
Software security testing is
the process of assessing and testing a system to discover security risks and vulnerabilities of the system and its data.
we
defne assessments as the analysis and discovery of vulnerabilities without attempting
to actually exploit those vulnerabilities.
At its core, ZAP is
what is known as a “man-in-the-middle proxy.”
It stands between the tester’s browser and the web application so
that it can intercept and inspect messages sent between browser and web application,
modify the contents if needed, and then forward those packets on to the destination.
It can be used as a stand-alone application, and as a daemon process.
When you
frst start ZAP,
you will be asked if you want to persist the ZAP session. By
default,ZAP sessions
are always recorded to disk in a HSQLDB database with a default name and
location. If you do not persist the session, those
fles are deleted when you exit ZAP If you
choose to persist a session, the session information will
be saved in the local database so you can access it later, and you will
be able to provide custom names and locations for
saving the
fles.
Expand Your
Pentesting with ZAP
Any pages protected by a login page are not discoverable during a passive scan because, unless you’ve
confgured ZAP’s authentication functionality, ZAP will not
handle the required authentication Any pages that are not
fndable with ZAP’s default spider are not testable during a passive scan. ZAP
does provide additional options for discovery and coverage outside
of passive scanning.
Quick Scan uses the traditional ZAP spider, which discovers links by examining the HTML in responses from the web application. This spider is fast, but it is not
always
effective when exploring an AJAX web application that generates links using JavaScript.
Spiders are a great way to explore your basic site, but
they should be combined with manual exploration to be more
effective.
Spiders, for example, will only enter basic default data into forms in your web application but a user can enter more relevant information which can, in
turn, expose more of the web application to ZAP.
This is especially true with things like
registration forms where a valid email address
is required. The spider may enter a random string, which will cause an error. A user will
be able to react to that error and supply a
correctly formatted string, which may cause more of the application to
be exposed when the form
is submitted and accepted.
Obscurity is not
security, and hidden pages sometimes go live without warning or notice. So be as thorough as you can when exploring your site.
Passive scanning is good at
fnding some vulnerabilities and
as a way to get a feel for the basic security state of a web application and locate where more investigation may
be warranted
Active scanning, however,
att empts to
fnd other vulnerabilities by using known attacks against the selected targets.
- The OWASP Top Ten Proactive Controls 2016 is a list of security techniques that should be included in every software development project
Verify for Security Early and Often
Parameterize Queries
Encode Data
Validate All Inputs
Implement Identity and Authentication Controls
Implement
Appropriate Access Controls
Protect Data
Implement Logging and Intrusion Detection
Leverage Security Frameworks and Libraries
Error and Exception Handling
https://www.owasp.org/index.php/OWASP_Proactive_Controls
OWTF aims to make pen testing:
Aligned with OWASP Testing Guide + PTES + NIST
https://www.owasp.org/index.php/OWASP_OWTF
- Vega is a free and open source web security scanner and web security testing platform to test the security of web applications. Vega can help you find and validate SQL Injection, Cross-Site Scripting (XSS), inadvertently disclosed sensitive information, and other vulnerabilities
https://subgraph.com/vega/
- Arachni is a feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of modern web applications
http://www.arachni-scanner.com/
- w3af is a Web Application Attack and Audit Framework. The project’s goal is to create a framework to help you secure your web applications by finding and exploiting all web application vulnerabilities.W3af is known as most powerful and flexible tool for finding web application’s vulnerability. It’s easy to use feature made it popular among the security professionals like ethical hackers. W3af contains many web assessment and exploitation plugins as well.
http://w3af.org/
- Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers .Nikto is sponsored by Netsparker, a false positive free web application security scanner.
https://cirt.net/Nikto2
- Burp Suite is an integrated platform for performing security testing of web applications
https://portswigger.net/burp/
- Spider - This can be used for automatically crawling an application, to discover its content and functionality. Scanner - This is used to automatically scan HTTP requests to find security vulnerabilities.
Intruder - This allows you to perform customized automated attacks, to carry out all kinds of testing tasks.
Repeater - This is used
to manually modify and reissue individual HTTP requests over and over.
Sequencer -
This is used to analyze the quality of randomness in an application's session tokens.
Decoder - This lets you transform bits of application data using common encoding and decoding schemes.
Comparer -
This is used to perform a visual comparison of bits of application data to find interesting differences.
https://portswigger.net/burp/help/suite_gettingstarted
- Firefox - Go to the Firefox menu, click on Options, click on Advanced, go to the Network tab, and click on the Settings button in the Connection section. Select the "Manual proxy configuration" radio button. Enter your Burp Proxy listener address in the "HTTP proxy" field (by default, 127.0.0.1). Enter your Burp Proxy listener port in the "Port" field (by default, 8080). Make sure the "Use this proxy server for all protocols" box is checked. Delete anything that appears in the "No proxy for" field. Then click "OK" to close all of the options dialogs.
https://portswigger.net/burp/help/suite_gettingstarted#browser
The intercept feature will intercept ALL traffic sent from the browser, additional extensions such as
FoxyProxy can
be used to specify which
URLs and IPs are blacklisted/whitelisted and therefore bypass the Burp intercept.
http://www.primalsecurity.net/0x2-exploit-tutorial-web-hacking-with-burp-suite/
- Two ways to go about this are static application security testing (SAST) and dynamic application security testing (DAST). These application security testing methodologies are used to find the security vulnerabilities that make your organization’s applications susceptible to attack.The two methodologies approach applications very differently. They are most effective at different phases of the software development life cycle (SDLC) and find different types of vulnerabilities. For example, SAST detects critical vulnerabilities such as cross-site scripting (XSS), SQL injection, and buffer overflow earlier in the SDLC. DAST, on the other hand, uses an outside-in penetration testing approach to identify security vulnerabilities while web applications are running.
https://www.cigital.com/blog/sast-vs-dast
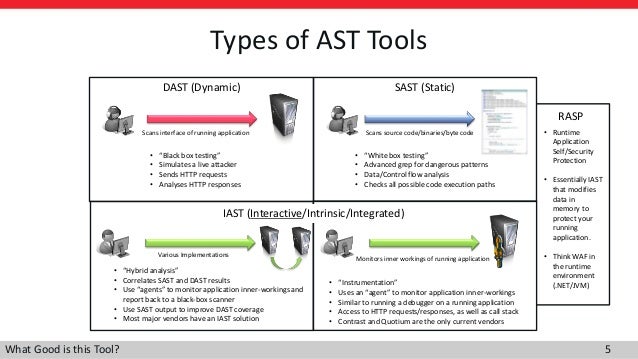
- SAST, DAST, IAST, and RASP: Pros, cons and how to choose
Some organizations need to focus on their developers, adding static application security testing (SAST) to the development cycle to catch potential flaws early
Other organizations may want to prove their need by using dynamic application security testing (DAST) or penetration testing to show how vulnerable their applications are.
there's interactive application security testing (IAST), which uses agents and additional software libraries to collect data from running applications that can then reveal vulnerabilities.
Companies that want to “virtually patch” their applications can lock down their portfolios using
some form of application firewall or a newer technology, such as runtime application self-protection (RASP), a form of IAST.
IAST, including RASP: Protect code against exploits and known bugs
a new approach—known as
interactive application security testing (IAST), or “glass-box” testing—promises to catch attacks that the other approaches miss
IAST runs as an agent, allowing you to collect and analyze event data from running applications.
https://learn.techbeacon.com/units/sast-dast-iast-rasp-pros-cons-how-choose
Use Fiddler for security testing your web applications
-- decrypt HTTPS traffic, and display and
modify requests using a man-in-the-middle decryption technique. Configure Fiddler to decrypt all traffic, or only specific sessions.
http://www.telerik.com/fiddler
A Java-based web proxy for assessing web application vulnerability. It supports editing/viewing HTTP/HTTPS messages on-the-fly to change items such as cookies and form fields. It includes a web traffic recorder, web spider,
hash calculator, and a scanner for testing common web application attacks such as SQL injection and cross-site scripting
http://sectools.org/tool/paros/
Odysseus is a proxy
server, which acts as a man-in-the-middle during an HTTP session. A typical HTTP proxy will relay packets to and from a client browser and a web server. Odysseus will intercept an HTTP session’s data in either direction and give the user the ability to alter the data before transmission.
http://www.darknet.org.uk/2007/02/odysseus-win32-proxy-telemachus-http-transaction-analysis/
- Charles is an HTTP proxy / HTTP monitor / Reverse Proxy that enables a developer to view all of the HTTP and SSL / HTTPS traffic between their machine and the Internet.
https://www.charlesproxy.com/
- Application Security Automation
Glue is a framework for running a series of tools.
Generally, it is intended as a backbone for automating a security analysis pipeline of tools.
https://github.com/OWASP/glue
The purpose of the project is to make it easy to integrate security tools (like static or dynamic analysis) into the CI/CD pipeline.
https://www.owasp.org/index.php/OWASP_Glue_Tool_Project
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser
https://beefproject.com/
- OWASP Application Security Verification Standard Project
The OWASP Application Security Verification Standard (ASVS) Project provides a basis for testing web application technical security controls and also provides developers with a list of requirements for secure development.
https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project
- Free for Open Source Application Security Tools
the following lists of automated vulnerability detection tools
that are free
for open source projects
Static Application Security Testing (SAST) Tools
Dynamic Application Security Testing (DAST) Tools - (Primarily for web apps)
Interactive Application Security Testing (IAST) Tools - (Primarily for web apps and web APIs)
Keeping Open Source libraries up-to-date (to avoid Using Components with Known Vulnerabilities (OWASP Top 10-2017 A9))
Static Code Quality Tools
- https://www.owasp.org/index.php/Free_for_Open_Source_Application_Security_Tools
- Software Assurance Maturity Model
The Software Assurance Maturity Model (SAMM) is an open framework to help organizations
formulate and implement a strategy for software security that
is tailored to the specific risks facing the organization
https://www.opensamm.org/
Overview of Burp Suite
DAST (Dynamic Application Security Testing) / Penetration Testing Tool
Integrated platform for performing security testing of web apps
Developed to provide comprehensive solution for web app security checks.Functionality includes proxy server, scanner, intruder, spidering, a repeater, a decoder,comparer, an extender, and sequence
Desired an automated approach to running Burp Suitesecurity scanning
Manual security scanning is time consuming (bottleneck) due to applicationdiscovery/ crawling process
Used Automated UI tests for application discovery
Used protractor (selenium) UI automated tests to act as the event based trigger forapplication discovery while using Burp Proxy to intercept all Requests/Response
Used Jenkins (Cl/CD) to run the automated UI test
Burp Suite Professional (v.1.7.34) with 'Burp-REST-API
Automated the spidering, proxy, intercepts request/response from UI tests, thenkicks off security scan, then generates Burp security scan report
Development Frivironment
Angular/NodeJS Web application
Protractor/Jasmine — Automated UI tool
Jenkins Cl/CD pipeline
Burp Suite Faternal API
Using multiple approach to testing applications
Manual Penetration Testing
DAST (Web App Scanning Tools)
Burp
Accunetix
Netsparker
SAST (DevSecOps Tools)
Checkmarx
Fortify
SonarQube
https://www.osti.gov/servlets/purl/1639985