- TOGAF
http://pubs.opengroup.org/architecture/togaf8-doc/arch/
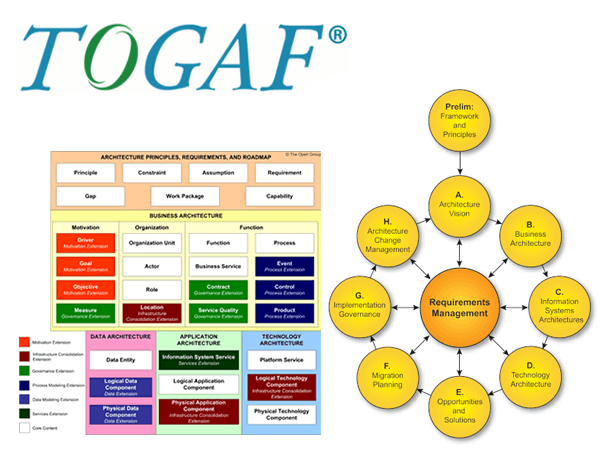
The Open Group Architecture Framework (TOGAF) is a framework for enterprise architecture that provides an approach for designing, planning, implementing, and governing an enterprise information technology architecture
https://en.wikipedia.org/wiki/The_Open_Group_Architecture_Framework
-
TOGAF® is the de facto global standard for Enterprise Architecture. The Open Group Architecture Forum,
comprised of more than 200 enterprises, develops and maintains the TOGAF standard and publishes successive versions at regular intervals
- TOGAF Version 9.1 10th New edition Edition
TOGAF Yönetim Mimarisinin Faydaları
İşletmenin bütünüyle ilgili bir bakış açısı sağlayarak gerçekçi ve sürdürülebilir kararlar verilmesini sağlar.
Ticari stratejilerin temelindeki önceliklere göre, ticari gelişim ile bilişim stratejilerinin ve ona yön veren parametrelerin birbirleriyle ilişkilenmelerini sağlar.
İşletmenin var olan komponentlerine etkisinin kolaylıkla değerlendirilebileceği efektif bir Değişim Yönetimi sağlar.
İşletmenin farklı bölümleri veya farklı uygulamalar arası koordinasyonu ve iletişimi standartlara oturtarak ortak bir
Teknolojik modernizasyonun yapılabilmesi için mimari yapının kurulması, teknolojik gelişim yol haritasının çıkarılması, standardizasyonu ve modernizasyonun yapılabilmesini sağlar.
Ürün veya hizmet teslimat zamanlarını, halihazırda var olan komponentlerin çözüme en uygun olanlarının tespit edilmesi ve tekrar kullanılmasının sağlanmasıyla, en kısa hale getirir.
http://www.proya.com.tr/togaf/
- MODAF
https://en.wikipedia.org/wiki/MODAF
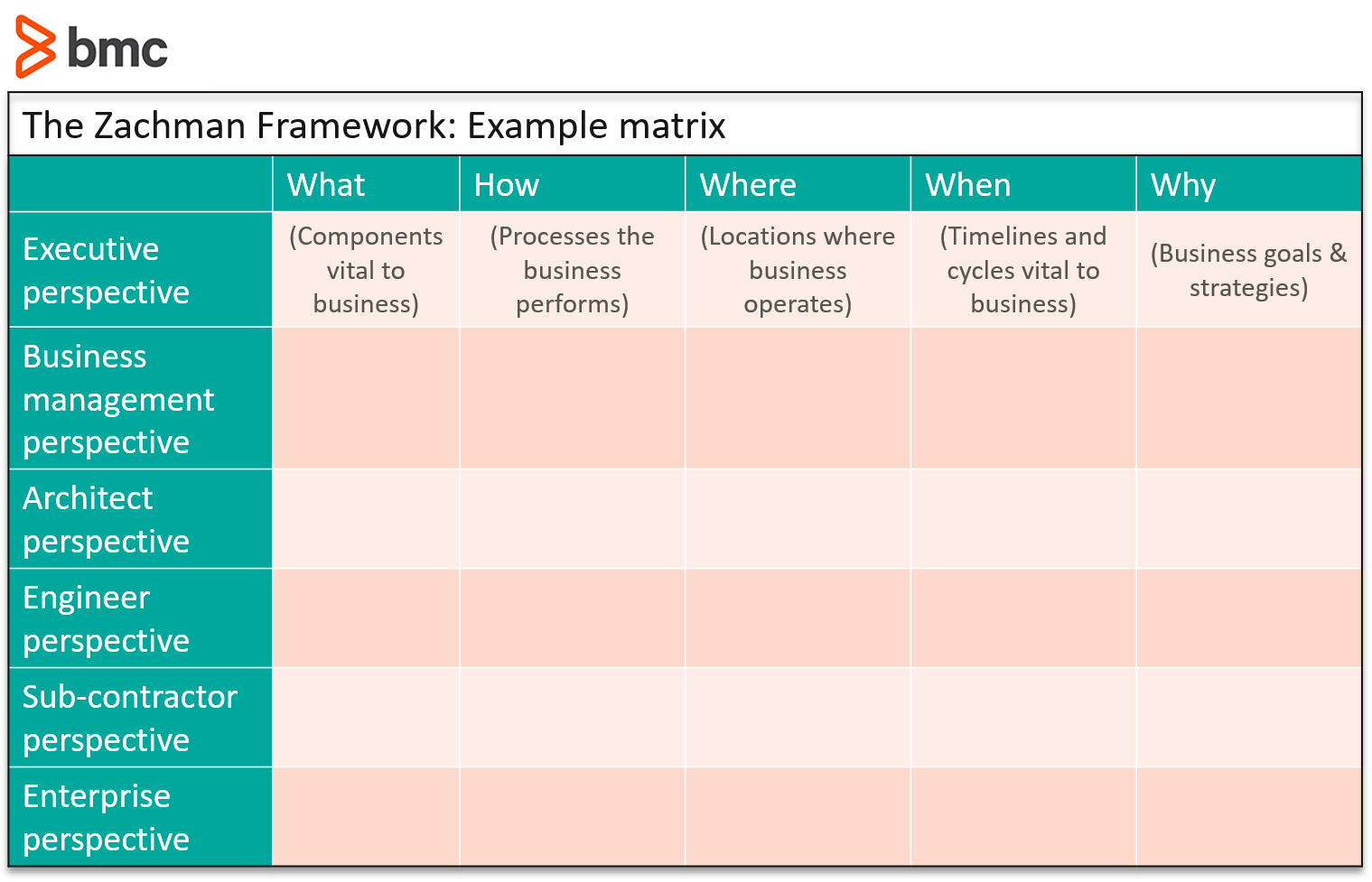
- The Concise Definition of The Zachman Framework by: John A. Zachman
The Zachman Framework™ is a schema - the intersection between two historical classifications that have been in use for literally thousands of years. The first is the fundamentals of communication found in the primitive interrogatives: What, How, When, Who, Where, and Why. It is the integration of answers to these questions that enables the comprehensive, composite description of complex ideas. The second is derived from reification, the transformation of an abstract idea into an instantiation that was initially postulated by ancient Greek philosophers and is labeled in the Zachman Framework™: Identification, Definition, Representation, Specification, Configuration and Instantiation.
https://www.zachman.com/about-the-zachman-framework
- ZACHMAN
http://en.wikipedia.org/wiki/Zachman_Framework
- TOGAF vs Zachman: What’s The Difference?
What’s an enterprise architecture?
An enterprise architecture (EA) is a construct that communicates an organization’s entire enterprise system, consisting of:
Technologies
Processes
Information assets
Your enterprise architecture provides various perspectives from a technology and business standpoint, allowing you to take a disciplined approach to managing those systems. In other words, your enterprise architecture defines the choice constraints that can be applied to enterprise IT and business systems and can have three core components: framework, methodology, and tooling.
Utilizing an EA solves two key problems facing technology-driven business organizations:
Developing a thorough understanding between highly dependent subsets of enterprise systems allows organizations to reduce the overall complexity of the architecture.
Helping establish a structured and well-informed decision-making process aligns technology with business goals.
TOGAF: The Open Group Architecture Framework
TOGAF is the de facto industry standard framework, offering a methodological approach to Enterprise Architecture design, planning, implementation, and governance.
Zachman Enterprise Architecture
John Zachman was an IT pioneer who understood the problems facing IT-driven businesses. To solve these problems, he developed an early enterprise-architectural methodology in 1987—the Zachman Framework.
The Zachman Framework offers a model-based approach that:
Specifies the deliverables
Categorizes various aspects of enterprise system subsets into a matrix form
Associates them with the decision choices of the business-I environment
Choosing TOGAF or Zachman
Which enterprise architecture you choose depends on your approach.
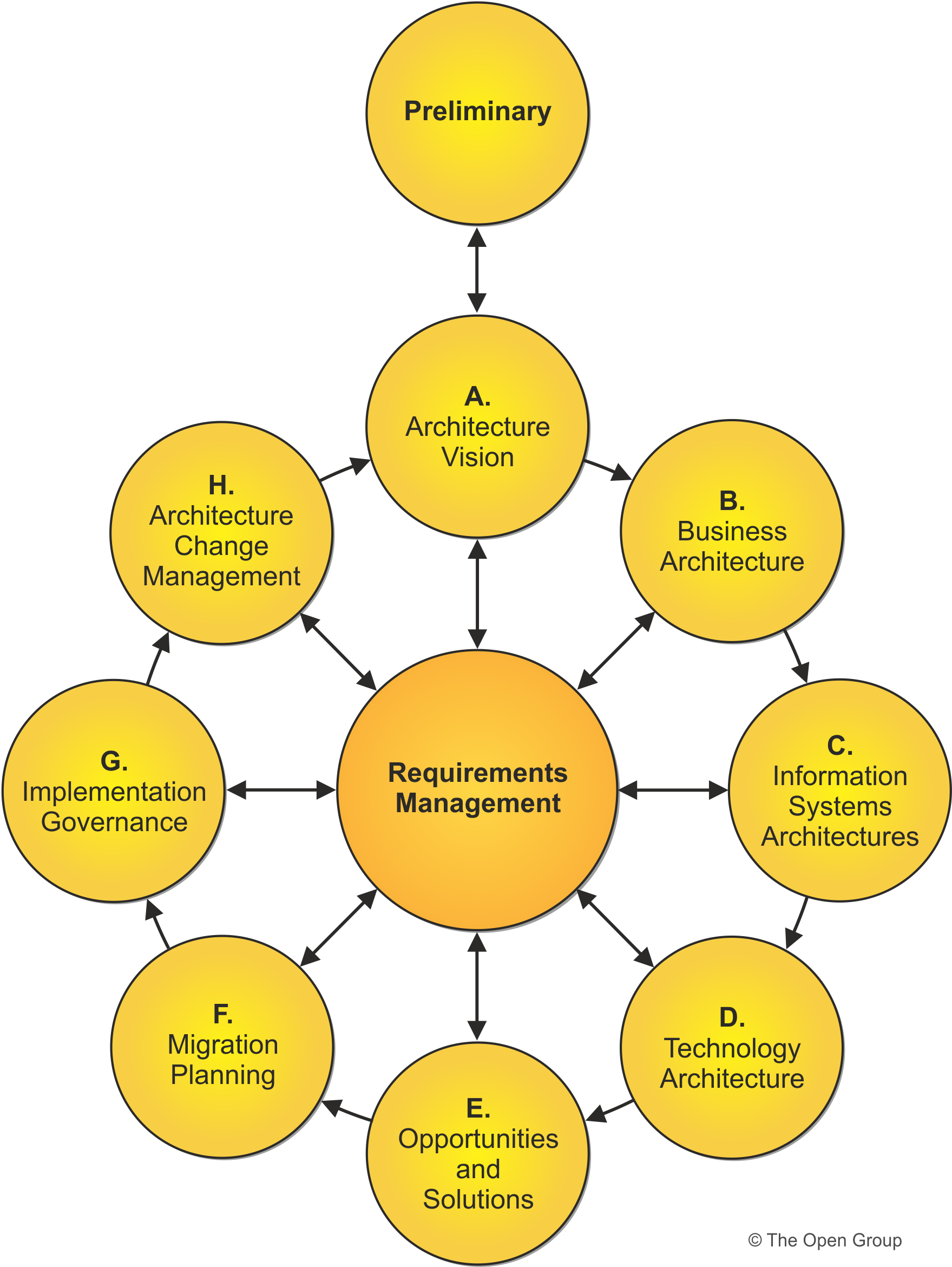
The TOGAF framework provides a systematic approach for defining the process of creating or improving an Enterprise Architecture. With its ADM, the framework offers a process for implementing the decision choices in order to produce your desired model.
The Zachman Framework is more of an ontology—a structured set of expressions that describe how artifacts can be categorized, and thus created, operated, and changed. Unlike TOGAF, Zachman uses various enterprise perspectives in order to scope, define, and plan details regarding individual subsets of your enterprise system.
Your organization may choose to use one—or you can opt for both. Together, the frameworks can complement each other, with TOGAF describing the detailed process for creating the Enterprise Architecture, and Zachman categorizing the artefacts.
https://www.bmc.com/blogs/togaf-vs-zachman/#
- SBVR/ORM
- ArchiMate
http://www3.opengroup.org/subjectareas/enterprise/archimatehttp://www3
- Archi is a free, open source, cross-platform tool and editor to create
ArchiMate models.
- Enterprise Architect
- Where SABSA differs from other approaches, is that it defines a conceptual layered model which enables the provision of
an holistic , strategic architectural approach as opposed to the more typically seenapplication of technology and process stand-alone and point solutions to tactical security objectives. For those familiar with, it also leverages the Zachman Framework and is compatible with TOGAF, ISO 27001, Agile and other methodologies.
SABSA ensures that different Views of security
https://medium.com/@marioplatt/what-is-sabsa-enterprise-security-architecture-and-why-should-you-care-a649418b2742
- SABSA stands for the Sherwood Applied Business Security Architecture. It provides a framework for developing risk-driven enterprise information security and information assurance architectures. It also aids in delivering security infrastructure solutions that support critical business initiatives.
https://www.orbussoftware.com/us/governance-risk-and-compliance/sabsa/what-is-sabsa/
- Enterprise Architecture Frameworks (EAF): The Basics
Defining the Enterprise Architecture Framework
Simply stated, enterprise architecture framework (EAF) refers to any framework, process, or methodology which informs how to create and use an enterprise architecture.
So, what is enterprise architecture?
At a high level, enterprise architecture offers a comprehensive approach and holistic view of IT throughout an enterprise. An enterprise is a business, company, firm, or group of any size that provides consumers with goods and/or services. This can also include any organized unit that has a common goal, such as an industry consortium or non-profit group. An enterprise requires collaboration to achieve its goal or strategy while providing the good or service as best as it can to ensure customer satisfaction.
History of EAF
A commonly held tenet is that enterprise architecture frameworks date to the mid-1980s, in accordance with the publication of the Zachman Framework, developed by then-IBMer John Zachman
Benefits
Some enterprises look to adopt service-oriented architecture (SOA) or microservices architecture (MSA) (often a key component of establishing a digital transformation) which has an impact on both IT and business processes. These may be the best candidates for enterprise architecture.
At its most helpful, an enterprise architecture framework makes sense of the complexities of achieving business strategy via IT strategy, technology, and business needs across all silos of the company. When performed at its best, an enterprise architecture translates the vague and intangible business strategy to practical, concrete plans and actions. Then, these designs are translated into solutions that achieve business strategy
Types of Enterprise Architecture Frameworks
The types of enterprise architecture frameworks are often categorized by who created and released them. Today’s EA frameworks fall into a few types:
Those developed by consortiums, of which The Open Group Architecture Framework (TOGAF) is most known.
Those intended for defense industry use, such as the U.S.’s own Departure of Defense Architecture Framework.
Those intended for wider government use, including the FDIC Enterprise Architecture Framework, the Federal Enterprise Architecture Framework (FEAF), and the NIST Enterprise Architecture Model.
Those developed and released as open source.
Those developed by private companies or universities and released as proprietary material, like those from IBM or Gartner
https://www.bmc.com/blogs/enterprise-architecture-frameworks/