- Cloud compliance engine
Dome9
The Dome9 Arc agentless SaaS platform delivers full visibility and control of security and compliance in AWS, Azure and Google Cloud environments.
https://dome9.com/
Public cloud threat protection, governance & compliance
https://www.paloaltonetworks.com/cloud-security/prisma-public-cloud
Custodian
Cloud Custodian is a rules engine for managing public cloud accounts and resources
It allows users to define policies to enable a well managed cloud
https://github.com/cloud-custodian/cloud-custodian
- AWS cloud security
IAM
AWS Identity and Access Management (IAM) - Securely manage access to AWS services and resources
https://aws.amazon.com/iam/
KMS
AWS Key Management Service (KMS)- Easily create and control the keys used to encrypt your data
https://aws.amazon.com/kms
GuardDuty
Protect your AWS accounts and workloads with intelligent threat detection and continuous monitoring
https://aws.amazon.com/guardduty/
GuardRails
A guardrail is a high-level rule that provides ongoing governance for your overall AWS environment.
https://docs.aws.amazon.com/controltower/latest/userguide/guardrails.html
Amazon Route 53 is a highly available and scalable cloud Domain Name System (DNS) web service. It is designed to give developers and businesses an extremely reliable and cost effective way to route end users to Internet applications by translating names like www. example.com into the numeric IP addresses like 192.0.2.1 that computers use to connect to each other. Amazon Route 53 is fully compliant with IPv6 as well .
https://aws.amazon.com/route53/
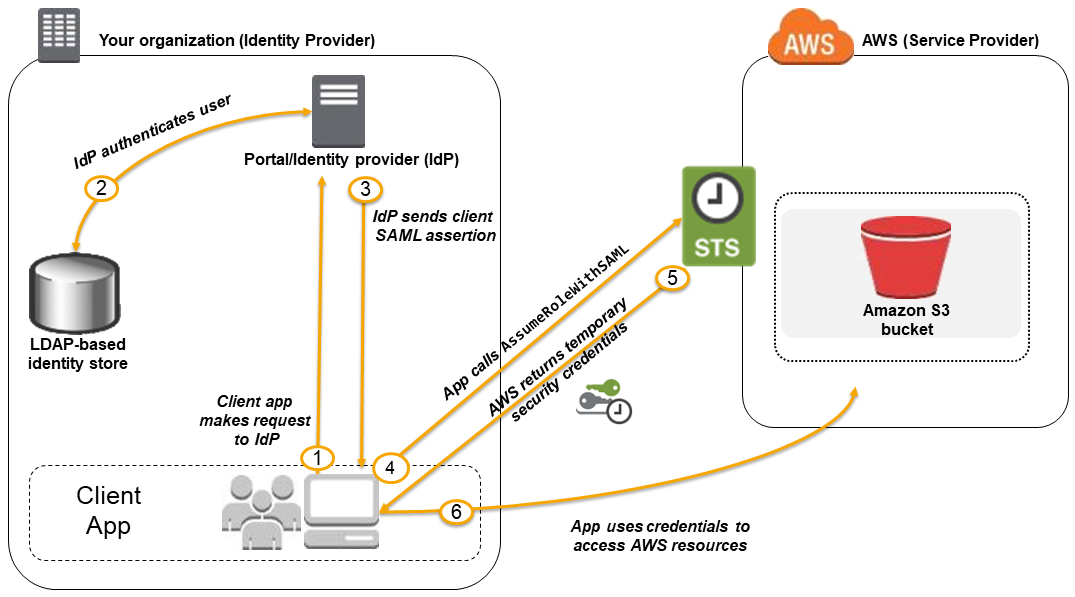
About SAML 2.0-based Federation
Using SAML-Based Federation for API Access to AWS
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_saml.html
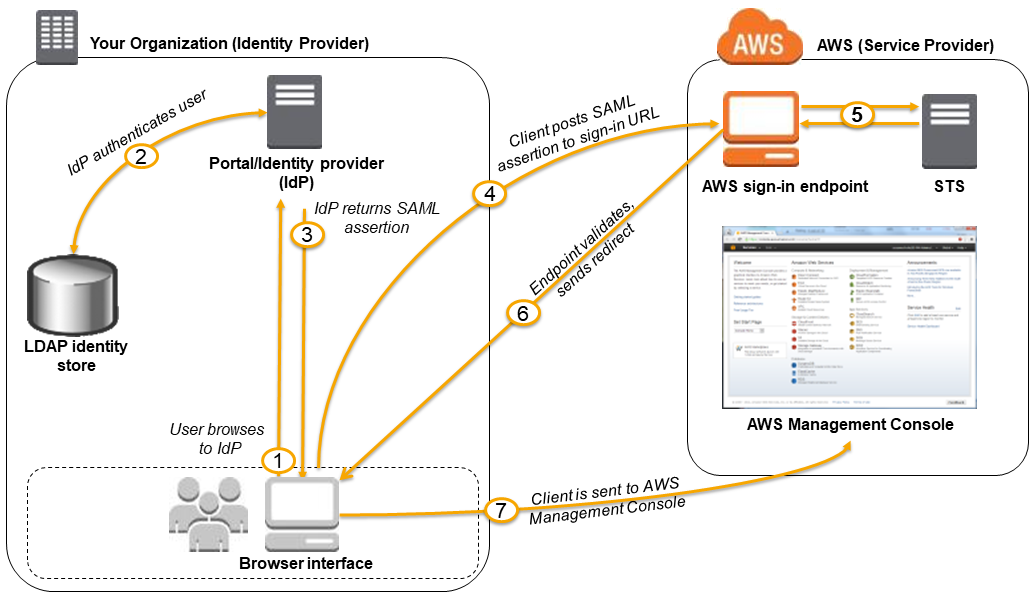
Enabling SAML 2.0 Federated Users to Access the AWS Management Console
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_enable-console-saml.html
How to automate SAML federation to multiple AWS accounts from Microsoft Azure Active Directory
https://aws.amazon.com/blogs/security/how-to-automate-saml-federation-to-multiple-aws-accounts-from-microsoft-azure-active-directory/
Option 2: SAML-Based Authentication
You can set up the management portal to authenticate users using your identity provider (IdP).
Your users don't have direct access to AWS resources. Instead, the vSphere a SAML vCenter
https://docs.aws.amazon.com/amp/latest/userguide/install-option-saml.html
Option 1: Federation Authentication Proxy
You can set up the management portal to authenticate users using the AWS Connector for vCenter
Your users don't have direct access to AWS resources. Instead, the vSphere vCenter
https://docs.aws.amazon.com/amp/latest/userguide/install-option-connector.html
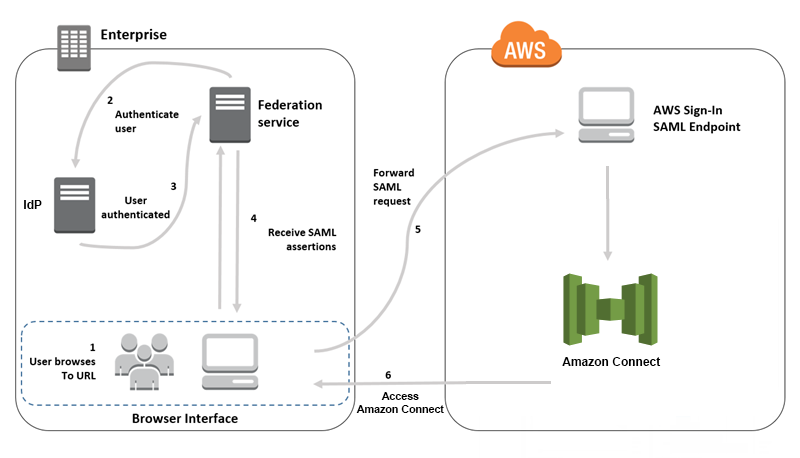
Configure SAML for Identity Management in Amazon Connect
https://docs.aws.amazon.com/connect/latest/adminguide/configure-saml.html
https://cloud.google.com/blog/products/gcp/cloud-kms-ga-new-partners-expand-encryption-options
Customer-Supplied Encryption Keys
https://cloud.google.com/security/encryption-at-rest/customer-supplied-encryption-keys/
Host Your Own Keys and Keep Control of Your Data
https://www.virtru.com/encryption-key-management
Use Your own Encryption Keys with S3’s Server-Side Encryption
https://aws.amazon.com/blogs/aws/s3-encryption-with-your-keys
Data Encryption in the Cloud, Part 4: AWS, Azure and Google Cloud
https://cloudarchitectmusings.com/2018/03/09/data-encryption-in-the-cloud-part-4-aws-azure-and-google-cloud/
- Gemalto's SafeNet Luna Hardware Security Module (HSM) and SafeNet
KeySecure
Many cloud service providers are offering variations of flexible key management such as bring-your-own-key (BYOK) and hold-your-own-key (HYOK).
https://www.globenewswire.com/news-release/2017/12/04/1219683/0/en/Gemalto-Gives-Google-Cloud-Platform-Customers-Flexible-Encryption-and-Key-Management-Capabilities.html
- Customer-Supplied Encryption Key partners
Customer-Supplied Encryption Keys (or CSEK, available for Google Cloud Storage and Compute Engine) allow you to provide a 256-bit string, such as an AES encryption key, to protect your data at rest.
To simplify the use of this unique functionality, our partners Gemalto, Ionic, KeyNexus appropriate
https://cloud.google.com/security/encryption-at-rest/customer-supplied-encryption-keys/
Host Your Own Keys and Keep Control of Your Data
https://www.virtru.com/encryption-key-management
Use Your own Encryption Keys with S3’s Server-Side Encryption
https://aws.amazon.com/blogs/aws/s3-encryption-with-your-keys
Data Encryption in the Cloud, Part 4: AWS, Azure and Google Cloud
https://cloudarchitectmusings.com/2018/03/09/data-encryption-in-the-cloud-part-4-aws-azure-and-google-cloud/
- What is Amazon S3?
Amazon S3 stores data as objects in a flat environment (without a hierarchy). Each object (file) in the storage contains a header with an associated sequence of bytes from 0 bytes to 5 TB. Objects in Amazon S3 are associated be obtained datacenter
What is Amazon EBS?
Every computer needs a drive and virtual machine is not an exception. Amazon EBS is a storage for the drives of your virtual machines. It stores data as blocks of the same size and organizes them through the hierarchy similar to a traditional file system. EBS is not a standalone storage service like Amazon S3 so you can use it only in combination with Amazon EC2, a cloud computing service by AWS.
There are three types of volumes in Amazon EBS.
General Purpose (SSD) Volumes
Provisioned IOPS (SSD) Volumes
Magnetic Volumes
What is Amazon EFS?
At some point, it became clear that Amazon Elastic File System was created
You can mount EFS to various AWS services and access it from various virtual machines. Amazon EFS is especially helpful for running servers, shared volumes (like NAS devices), big data analysis, and any scalable workload you can think of.
Amazon S3 vs EFS vs EBS Comparison
https://www.cloudberrylab.com/resources/blog/amazon-s3-vs-ebs-vs-efs/
a diagram of how Amazon Web Services leverages envelope encryption
Encryption can be defined in order
In short, the
The same key is used
A different key is used The encryption key is known is typically made is paired was encrypted
However due to are used
A hybrid approach is used
The encrypted DEK is decrypted
two
The public key can be made that can only be seen by the owner of the private key
- Given its capability to make data unreadable to those who do not have the key to unlock it, encryption can
actually
We are now moving to a world where every piece of data will be encrypted
Note that while the series is focused
Decryption transforms the disguised data back into readable data.
Plaintext is the unencrypted been decrypted
Ciphertext is the
A Cipher Is the mathematical function/algorithm that does the actual encryption and decryption.
A Key is a value that serves as input to the cipher and must used
The decryption process is essentially the inverse with the key (K) being used as
While early data encryption relied on the secrecy of the cipher to maintain the security of the system, that has changed over time as it has been shown be cracked
“A cryptosystem should be secure even if everything about the system, except the key, is public knowledge.”
Today, cipher algorithms are largely it is generally acknowledged
Ciphers such as AEs-256 and RSA-2048 can potentially ciphertext
Symmetric or Secret Key Encryption
Here’s an example of how to create a plaintext file and then encrypt it with a 128-bit symmetric key; the openssl
To decrypt the ciphertext, you just use the decrypt -d option and supply the same symmetric key used to encrypt the original plaintext file.
The challenge with the symmetric key encryption approach is around key storage and management. The secret key has to be carefully protected the key is lost
The most widely used symmetric key encryption standard today is Advanced Encryption Standard (AES). AES can use keys of different sizes including 128-bit, 192-bit and 256 bit with AES-256 being the most commonly used key size for data encryption at rest
It would require a supercomputer >1 quadrillion years to brute-force decrypt the resulting ciphertext, without the key.
Asymmetric or Public Key Encryption
A common analogy for asymmetric key encryption is the use of mailboxes for postal mail. The secret message can dropped
This solves the issue of it can be made be compromised the private key may be cracked
In fact, symmetric encryption is ~1000x faster and requires 1/10th the key size of asymmetric encryption to encrypt the same data with the same level of security.
The most widely used asymmetric key encryption standard today is Rivest-Shamir-Adleman (RSA)
RSA can use keys of different sizes with RSA-1024 and RSA-2048 being the most commonly used key size for data encryption at rest.
Envelope Encryption
A one-time symmetric key, called a Date Encryption Key (DEK) is generated
A separate symmetric key or public key, called a Key Encryption Key (KEK), is generated
The encrypted DEK is appended
The encrypted DEK is appended
For the decryption process, the reverse is done
An application retrieves the ciphertext and associated DEK
The application retrieves the KEK if it is a symmetric key or the associated private key if the KEK is an asymmetric public key
The ciphertext is then decrypted
Envelope encryption has a number of
Easier data key protection – to securely store the keys are encrypted They can be stored
Easier key management – choose to
Combines the strengths of both symmetric and asymmetric key encryption methods – In this case
https://cloudarchitectmusings.com/2018/02/08/encrypting-your-data-in-the-cloud-part-2-encryption-101/
Typically long term is held
Typically long term is held
When you need to encrypt some message :
A request is sent key based
KMS returns a data key, which usually contains both theplain text
The message is encrypted
Then both the encrypted message and are packaged
The plain text key is immediately removed
When it comes time to decrypt the message:
The encrypted data key is extracted
KMS is requested
Once the plain text version of the data keyis obtained itself is decrypted
https://devender.me/2016/07/13/envelope-encryption/
- Envelope Encryption
When you need to encrypt some message
KMS returns a data key, which usually contains both the
Then both the encrypted message
When it comes time to decrypt the message:
Once the plain text version of the data key
https://devender.me/2016/07/13/envelope-encryption/
- The best security posture takes a multi-layer approach where data
is secured end end
Encryption can and should be leveraged a number of data
It is important that data be encrypted
https://cloudarchitectmusings.com/2018/01/25/data-encryption-in-the-cloud-part-1-why-you-should-care/
How each provider implements their cryptographic system, including encryption methods, ciphers and key management.
There are a number of
Key Generation – pseudo random
Key Storage – are generated be securely stored that they cannot be lost passphrase passphrases be securely stored as well
Key Activation – be activated are created needs be stored
Key Distribution – authorized
Key Rotation – is recommended be rotated on a periodic basis is created be deactivated used purposes
Key Expiration – be created be used are generated it must be retained purposes
Key Revocation – be revoked it has been compromised it can no longer be used be retained it has already been used In some cases be reactivated period of time
Key Destruction – be completely removed every instance of that key, must be deleted
there are three type
Software-based KMS – be software downloaded . Hashicorp
Hardware-Based KMS - A HSM is specialized designed specifically tamper are properly secured be used in conjunction be embedded
Cloud-Based KMS – – .
Key Generation
Entropy
In Cryptography, entropy is the measure of uncertainty or randomness in a system.
Entropy refers to the randomness of the cipher and of the encryption key.
The higher the entropy, the more random the results and the more secure the ciphertext.
Since encryption depends so heavily on entropy, you need a component that can reliably generate random bits which can then be used to
The RNG samples data from the analog world, such as temperature measurements, hard drive activity and mouse clicks, as its source of entropy for generating random bits
The PRNG/DRNG takes these random bits from the RNG and stores them in a memory buffer called the entropy pool
The PRNG/DRNG applies a mathematical algorithm to the content of the entropy pool to generate pseudo random be used
The reason that an RNG needs to sample analog data is that computers aren’t capable of generating truly truly a RNG keyboard
When an RNG runs out of entropy, it will no longer be able to . is abstracted an a a RNG
Symmetric Key Generation
Direct Key Generation – A key generation algorithm is invoked
Password/Passphrase – passphrase
There are a number of passphrases
Asymmetric Key Generation
Unlike symmetric keys which are derived is created .
The private key needs to be stored
https://cloudarchitectmusings.com/2018/02/21/data-encryption-in-the-cloud-part-3-key-management-and-key-generation/
When it comes to lifecycle
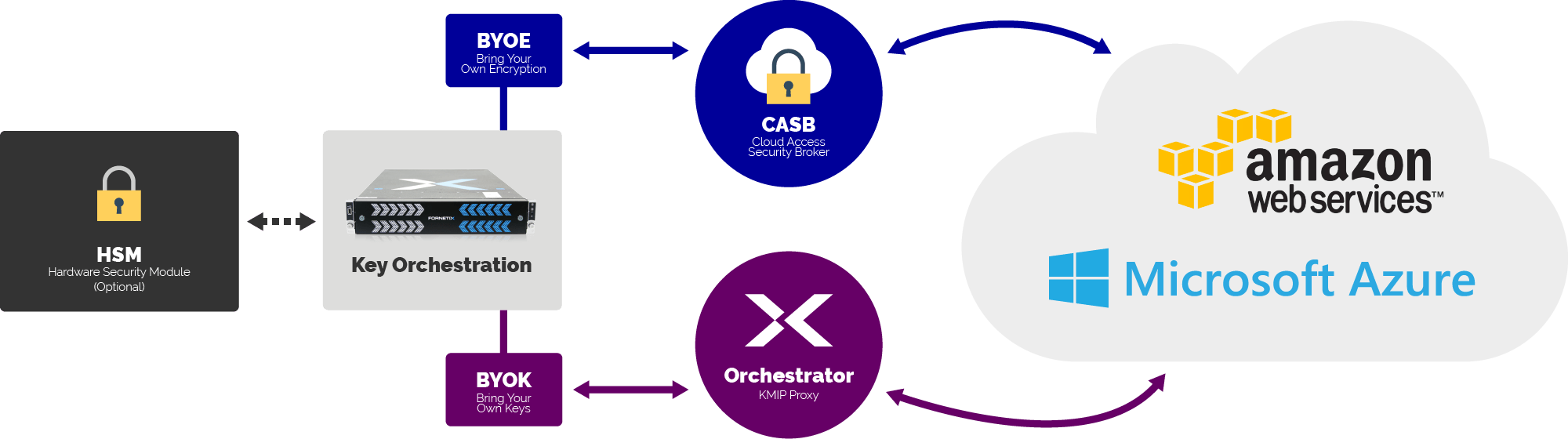
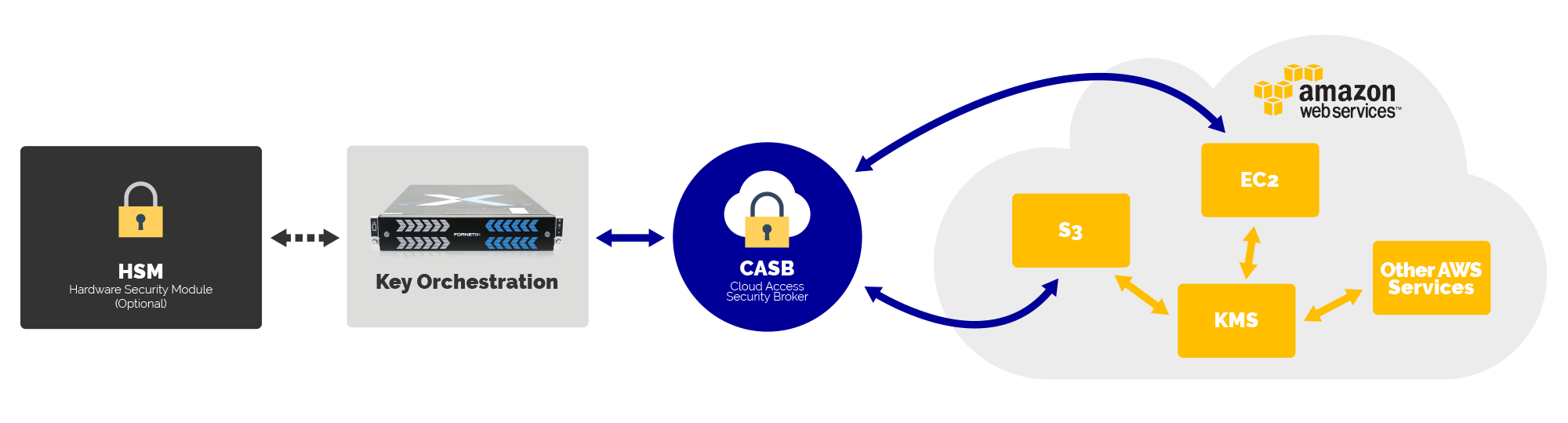
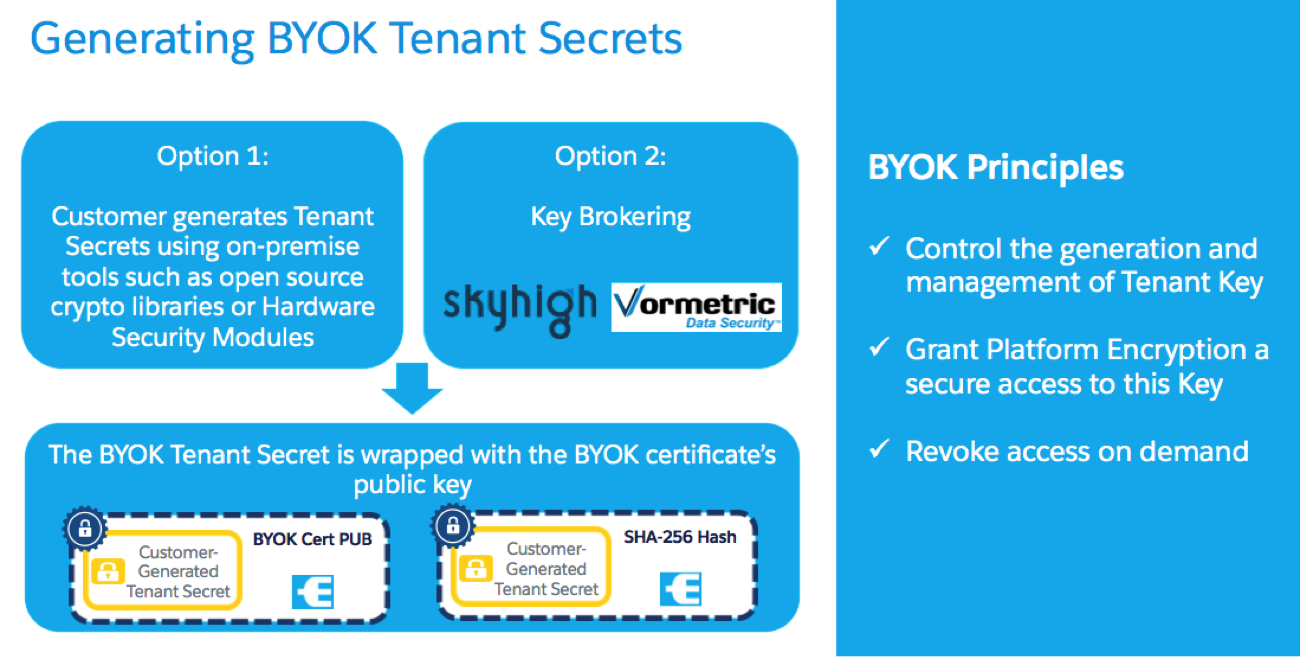
Bring-Your-Own Key (BYOK) and Bring-Your-Own-Encryption (BYOE)
https://www.fornetix.com/encryption-solutions-for-bring-your-own-key-encryption-byok-byoe/
UpCRM :
Envelope encryption is used for all client-side options and for all server-side options except when the customer provides the encryption key.
the relationship between an application, file system, and dm-crypt. Dm-crypt sits between the physical disk and the file system, and data written from the operating system to the disk is encrypted . The application is unaware of such disk-level encryption. Applications use a specific mount point in order to store and retrieve files, and these files are encrypted when stored to disk. If the disk is lost or stolen, the data on the disk is useless.
- Securing the Cloud
Bring-Your-Own Key (BYOK) and Bring-Your-Own-Encryption (BYOE)
https://www.fornetix.com/encryption-solutions-for-bring-your-own-key-encryption-byok-byoe/
BYOK with SafeNet KeySecure and ProtectApp
https://safenet.gemalto.com/data-encryption/enterprise-key-management/bring-your-own-key-byok/
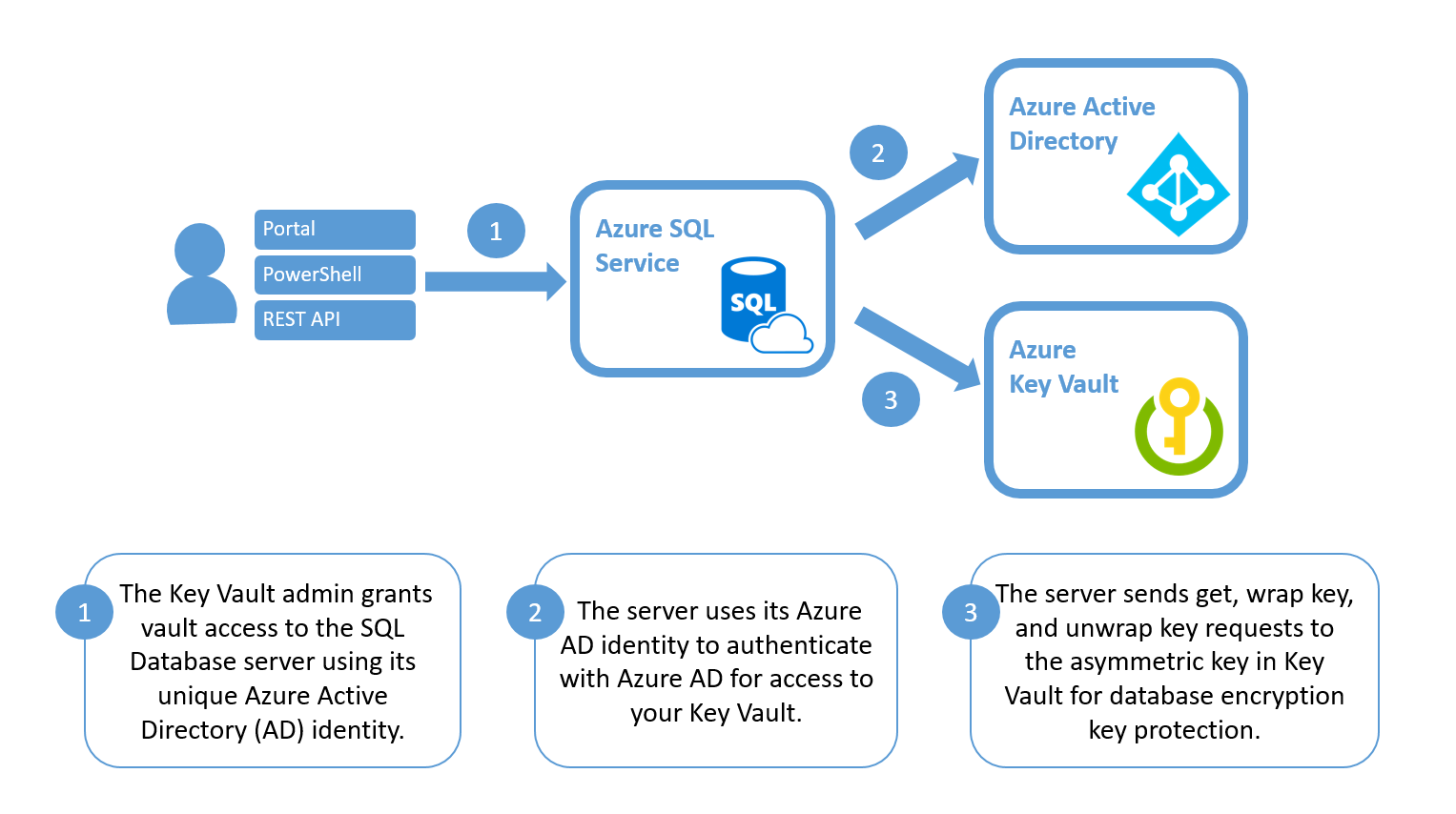
Azure SQL Transparent Data Encryption with customer-managed keys in Azure Key Vault: Bring Your Own Key support
https://docs.microsoft.com/en-us/azure/sql-database/transparent-data-encryption-byok-azure-sql
https://up-crm.com/upcrm-is-pleased-to-announce-bring-your-own-key-encryption-for-the-salesforce/
Use case –
https://subscription.packtpub.com/book/virtualization_and_cloud/9781788834308/5/ch05lvl1sec44/use-case-using-customer-supplied-encryption-keys
Use Your own Encryption Keys with S3’s Server-Side Encryption
https://aws.amazon.com/blogs/aws/s3-encryption-with-your-keys/
- the role of data encryption as a critical component of any company’s security posture and the potential pitfalls of not using encryption properly.
This is magnified when you are talking about storing data outside of customer data centers such as is the case when archiving data to public cloud storage repositories such as Amazon S3, Azure Blob Storage and Google Cloud Storage
It is important to understand that while public cloud providers are responsible for securing the infrastructure and provide tools for protecting the data stored in their infrastructures, the user is ultimately responsible for using those tools to secure their data.
I want to continue this blog series by giving an overview of how encryption at rest is implemented among the big three public clouds – Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP).
Data-at-rest encryption only since all three providers’ implementation of TLS for encrypting data-in-transit do not differ greatly
Encryption of object storage data since that is where the largest amount of data is stored in the cloud. I will probably be covering services such as block storage, file storage and databases in the future .
How each provider implements their cryptographic system, including encryption methods, ciphers and key management.
Server-Side vs. Client-Side Encryption
With server-side encryption, data is not encrypted until it is transferred to the target, in this case the object storage service. All three providers offer server-side encryption with some differences in implementation details, particularly in regards to key management
With client-side encryption, data is encrypted at the source and prior to it being transferred to the target, in this case the object storage service. All three public cloud providers allow for client-side encryption with some offering varying levels of integration.
Encryption Methods
Amazon S3 supports both server-side and client-side encryption with a number of options for each. Customers have the option of enabling server-side encryption by default for all uploaded objects to S3
For both server-side and client-side encryption, AWS utilizes AES-256 with Galois Counter Mode (GCM) for any symmetric key encryption operations
GCM provides authenticated encryption by adding a unique tag to the ciphertext which verifies that the encrypted data has not been tampered with in any way .
For server-side encryption, Amazon S3 supports three options:
Amazon S3-managed keys (SSE-S3)
AWS Key Management Service (KMS) managed keys (SSE-KMS)
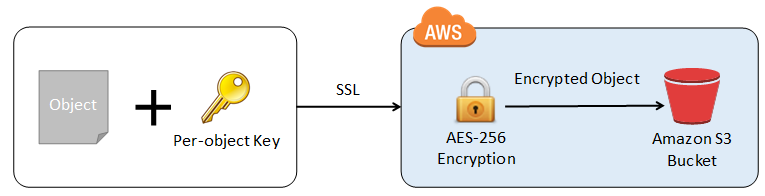
Customer-provided keys (SSE-C)
https://cloudarchitectmusings.com/2018/03/09/data-encryption-in-the-cloud-part-4-aws-azure-and-google-cloud/
- How to Protect Data at Rest with Amazon EC2 Instance Store Encryption
Encrypting data at rest is vital for regulatory compliance to ensure that sensitive data saved on disks is not readable by any user or application without a valid key. Some compliance regulations such as PCI DSS and HIPAA require that data at rest be encrypted throughout the data lifecycle . To this end, AWS provides data-at-rest options and key management to support the encryption process.
For example, you can encrypt Amazon EBS volumes and configure Amazon S3 buckets for server-side encryption (SSE) using AES-256 encryption. Additionally, Amazon RDS supports Transparent Data Encryption (TDE).
Disk and file system encryption
You can use two methods to encrypt files on instance stores.
The first method is disk encryption, in which the entire disk or block within the disk is encrypted by using one or more encryption keys. Disk encryption operates below the file-system level, is operating-system agnostic, and hides directory and file information such as name and size.
Encrypting File System, for example, is a Microsoft extension to the Windows NT operating system’s New Technology File System (NTFS) that provides disk encryption.
The second method is file -system-level encryption. Files and directories are encrypted , but not the entire disk or partition. File-system-level encryption operates on top of the file system and is portable across operating systems.
The Linux dm-crypt Infrastructure
Dm-crypt is a Linux kernel-level encryption mechanism that allows users to mount an encrypted file system.
The solution in this post uses dm-crypt in conjunction with a disk-backed file system mapped to a logical volume by the Logical Volume Manager (LVM)
https://aws.amazon.com/blogs/security/how-to-protect-data-at-rest-with-amazon-ec2-instance-store-encryption/