- The Zero Trust Model is simple: cybersecurity professionals must stop trusting packets as if they were people. Instead, they must eliminate the idea of a trusted network (usually the internal etwork) and an untrusted network (external networks). In Zero Trust, all network traffic is untrusted. The Zero Trust Model has three key concepts
1. Ensure all resources are accessed securely regardless of location.
2. Adopt the least privilege strategy and strictly enforce access control.
3. Inspect and log all traffic.
http://csrc.nist.gov/cyberframework/rfi_comments/040813_forrester_research.pdf
- WHAT IS A ZERO TRUST ARCHITECTURE?
Businesses who want
Conventional security models operate on the outdated assumption that everything on the inside of an organization’s network can
Zero Trust, rooted in the principle of “never trust, always verify,”
users in finance can have access to financial-related databases, but not HR information; and so on. It’s critical to identify who the users are, which applications they are trying to reach, and if
Zero Trust is All About Changing How You Think
Ensure all data and resources
Understanding who the users are, what applications they are using and the
Adopt
“Always verify,” meaning inspect and log all traffic.
Security rules, based on business policies, should
Add more authentication methods to counter credential based attacks.
Never trust, always keep adding context and keep your roles up-to-date.
How to Achieve a Zero Trust Architecture
Use Zero Trust to gain visibility and context for all traffic
https://www.paloaltonetworks.com/cyberpedia/what-is-a-zero-trust-architecture
- Network segmentation and segregation are highly effective strategies an organisation can implement to limit the impact of a network intrusion.
these strategies can make it significantly more difficult for an adversary to locate and gain access to an organisation’s most sensitive information
increase the likelihood of detecting an adversary’s activity
As a result, it is important for organisations to segment networks and segregate sensitive information, hosts and services from the environment in which users access external resources; in particular the Web, email and other internet services.
What is network segmentation and segregation?
Network segmentation involves partitioning a network into smaller networks; while network segregation involves developing and enforcing a
Implementing network segmentation and segregation can
Implementing demilitarised zones and gateways between networks with different security requirements (security domains) utilising technologies at various layers such as
Implementing server and domain isolation using Internet Protocol Security (
Implementing storage based segmentation and filtering using technologies such as disk and volume encryption and Logical Unit Number masking.
For
Segregating high-risk applications from a network
Users requiring internet access launched a remote desktop application on their corporate workstation to access a virtual desktop and authenticated with a user account used only for that purpose.
Users requiring access to high-risk applications launched a local virtualisation application to run a hardened virtual host which connected to a less-trusted remote environment which
Summary of example implementations
The key takeaway from both approaches was that users did not store or process potentially malicious data directly on their corporate workstation or use the corporate servers
https://www.cyber.gov.au/publications/network-segmentation-and-segregation
- With Zero Trust there is no default trust for any entity — including users, devices, applications, and packets — regardless of what it is and its location on or relative to the corporate network. By establishing Zero Trust boundaries that
effectively compartmentalize different segments of the network, you can protect critical intellectual property from unauthorized applications or users, reduce the exposure of vulnerable systems, and prevent the lateral movement of malware throughout your network.
VLANs
VLAN cannot inspect your traffic for threats
True Zero Trust network segmentation requires an enterprise security platform that understands your applications, users, and content.
Palo Alto Networks enterprise security platform addresses critical Zero Trust concepts such
Secure access —
Inspection of ALL traffic
Least privileges access control- The combination of App-ID, User-ID™, and Content-ID™ deliver a positive control model that allows organizations to control interactions with resources based on an extensive range of business-relevant attributes, including the specific application and individual functions being used, user and group identity, and the specific types or pieces of data being accessed (e.g., credit card or social security numbers).
the result is
Advanced threat protection
https://www.paloaltonetworks.com/solutions/initiatives/network-segmentation
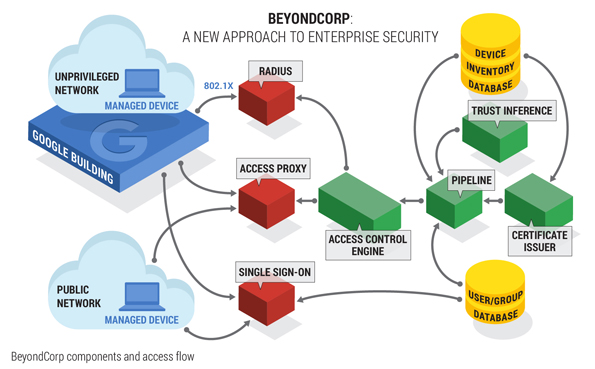
Beyond Corp
Unlike the traditional perimeter security model,
The guiding principles set forth by Google help pave the path for other organizations to realize their own implementation of a Zero Trust network.
https://www.beyondcorp.com/
- What Is a Zero Trust Network?
External and internal threats exist on the network at all times.
Network locality is not sufficient for deciding trust in a network.
Every device, user, and network flow is authenticated and authorized .
Policies must be dynamic and calculated from as many sources of data as possible.
Traditional network security architecture breaks different networks (or pieces of a single network) into zones, contained by one or more firewalls.
For example, resources deemed more risky, such as web servers that face the public internet, are placed in an exclusion zone (often termed a “DMZ”), where traffic can be tightly monitored and controlled
The zero trust model turns this diagram inside out.
There are many disadvantages:
Lack of intra-zone traffic inspection
Lack of flexibility in host placement (both physical and logical)
Single points of failure
If we instead declare that network location has no value, VPN is suddenly rendered obsolete, along with several other modern network constructs.
this mandate necessitates pushing enforcement as far toward the network edge as possible, but at the same time relieves the core from such responsibility
By leveraging distributed policy enforcement and applying zero trust principles, we can produce a design
Introducing the Zero Trust Control Plane
Once the control plane has decided that the request will be allowed , it dynamically configures the data plane to accept traffic from that client (and that client only)
In addition, it can coordinate the details of an encrypted tunnel between the requestor and the resource. This can include temporary one-time -use credentials, keys, and ephemeral port numbers
Evolution of the Perimeter Model
Managing the Global IP Address Space
The journey that led to the perimeter model began with address assignment.
Birth of Private IP Address Space
It had another interesting effect, which lingers with us today: networks using private addresses were more secure, because they were fundamentally incapable of joining other networks, particularly the internet.
Private Networks Connect to Public Networks
With established private networks, it was often the case that this mail server would be the only server with an internet connection. It would have one network interface facing the internet, and one facing the internal network.
the perimeter model was born. The internal network became the “secure” network, and the tightly controlled pocket that the external hosts laid in became the DMZ, or the demilitarized zone.
Birth of NAT
The IP Network Address Translator, defines a standard for a network device that is capable of performing IP address translation at organizational boundaries. By maintaining a table that maps public IPs and ports to private ones, it enabled devices on private networks to access arbitrary internet resources. This lightweight mapping is application-agnostic, which meant that network operators no longer needed to support internet connectivity for particular applications; they needed only to support internet connectivity in general .
These NAT devices had an interesting property: because the IP mapping was many-to-one, it was not possible for incoming connections from the internet to access internal private IPs without specifically configuring the NAT to handle this special case. In this way, the devices exhibited the same properties as a stateful firewall. Actual firewalls began integrating NAT features almost instantaneously, and the two became a single function, largely indistinguishable.
The Contemporary Perimeter Model
With a firewall/NAT device between the internal network and the internet, the security zones are clearly forming. There is the internal “secure” zone, the DMZ (demilitarized zone), and the untrusted zone (aka the internet).
We went from offline/private networks with just one or two hosts with internet access to highly interconnected networks with security devices around the perimeter.
Evolution of the Threat Landscape
Even before the public internet, communicating with a remote computer system was highly desirable. This was commonly done over the public telephone system. Users and computer systems could dial in and, by encoding data into audible tones, gain connectivity to the remote machine
It wasn’t long after that people realized it would be a good idea to protect those internet -facing hosts. Hardware firewalls were the best way to do it (most operating systems had no concept of a host-based firewall at the time).
This is where things took an interesting turn. NAT was introduced to grant internet access to clients on internal networks
Hosts on the “trusted” internal networks could then communicate directly with untrusted internet hosts, and the untrusted host was suddenly in a position to abuse the client attempting to speak with it
The ability to launch attacks from hosts within an internal network is a very powerful one . These hosts almost certainly have permission to talk to other hosts in the same security zone (lateral movement) and might even have access to talk to hosts in zones more secure than their own.
The critical flaw enabling attack progression is subtle, yet clear: security policies are defined by network zones, enforced only at zone boundaries, using nothing more than the source and destination details.
Perimeter Shortcomings
The problem comes when architecting security zones into the network itself. Imagine the following scenario: you run a small ecommerce company. You have some employees, some internal systems (payroll, inventory, etc.), and some servers to power your website
employees need access to internal systems, web servers need access to database servers, database servers don’t need internet access but employees do, and so on
Traditional network security would codify these groups as zones and then define which zone can access what
since they are defined on a zone-by-zone basis, it makes sense to enforce them wherever one zone can route traffic into another.
your HR representative might need access to the HR software’s database in order to perform audits. In these cases, an acceptable approach is to configure a firewall exception permitting traffic from that individual’s IP address to the particular server( s) in question.
Bypassing perimeter security is trivial with malware that phones home, and firewalls between zones consider nothing more than source and destination when making enforcement decisions.
It is a network that is completely untrusted. Lucky for us, we interact with such a network very frequently: the internet.
The zero trust model dictates that all hosts be treated as if they’re internet-facing.
Automation enables us to extend this level of security to all of the systems in our infrastructure.
Automation as an Enabler
Zero trust networks do not require new protocols or libraries
Automation systems are what allow a zero trust network to be built and operated .
Interactions between the control plane and the data plane are the most critical points requiring automation
If policy enforcement cannot be dynamically updated , zero trust will be unattainable; therefore it is critical that this process be automatic and rapid.
There are many ways that this automation can be realized . Purpose-built systems are most ideal, though more mundane systems like traditional configuration management can fit here as well . Widespread adoption of configuration management represents an important stepping stone for a zero trust network, as these systems often maintain device inventories and are capable of automating network enforcement configuration in the data plane
Perimeter Versus Zero Trust
Over time, we have come to learn that this assumption is false, and it is not only necessary to protect your hosts from the outside, but it is also necessary to protect them from each other
Thus, protecting resources by using IP addresses or physical location as an identifier is not enough.
All hosts, even those which share “trust zones,” must provide proper identification.
There are three key components in a zero trust network: user/application authentication, device authentication, and trust
The first component has some duality in it due to the fact that not all actions are taken by users. So in the case of automated action (inside the datacenter , for instance), we look at qualities of the application in the same way that we would normally look at qualities of the user.
Authenticating and authorizing the device is just as important as doing so for the user/application. This is a feature rarely seen in services and resources protected by perimeter networks
It is often deployed using VPN or NAC technology, especially in more mature networks, but finding it between endpoints (as opposed to network intermediaries) is uncommon.
NAC as a Perimeter Technology
NAC, or Network Access Control, represents a set of technologies designed to strongly authenticate devices in order to gain access to a sensitive network.
These technologies, which include protocols like 802.1X and the Trusted Network Connect (TNC) family, focus on admittance to a network rather than admittance to a service and as such are independent to the zero trust model. An approach more consistent with the zero trust model would involve similar checks as close to the service being accessed as possible
While NAC can still be employed in a zero trust network, it does not fulfill the zero trust device authentication requirement due to its distance from the remote endpoint.
Finally, a “trust score” is computed , and the application, device, and score are bonded to form an agent.
If the request is authorized , the control plane signals the data plane to accept the incoming request
This action can configure encryption details as well . Encryption can be applied at the device level, application level, or both. At least one is required for confidentiality.
With these authentication /authorization components, and the aide of the control plane in coordinating encrypted channels, we can assert that every single flow on the network is authenticated and expected. Hosts and network devices drop traffic that has not had all of these components applied to it, ensuring sensitive data can never leak out. Additionally, by logging each of the control plane events and actions, network traffic can be easily audited on a flow-by-flow or request-by -request basis.
Identity can be proven cryptographically, meaning it no longer matters what IP address any given connection is originating from
With automation removing the technical barriers, VPN is essentially obsoleted
“Private” networks no longer mean anything special: the hosts there are just as hardened as the ones on the internet.
Thinking critically about NAT and private address space, perhaps zero trust makes it more obvious that the security arguments for it are null and void.
Applied in the Cloud
you can’t trust the network in a public cloud.
The ability to authenticate and secure communication without relying on IP addresses or the security of the network connecting them means that compute resources can be nearly commoditized .
Since zero trust advocates that every packet be encrypted , even within the same datacenter , operators need not worry about which packets traverse the internet and which don’t.
The zero trust model carefully manages trust in the system. These types of networks lean on automation to realistically manage the security control systems that allow us to create a more dynamic and hardened system. We introduced some key concepts like the authentication of users, devices, and applications, and the authorization of the combination of those components
https://www.oreilly.com/library/view/zero-trust-networks/9781491962183/ch01.html
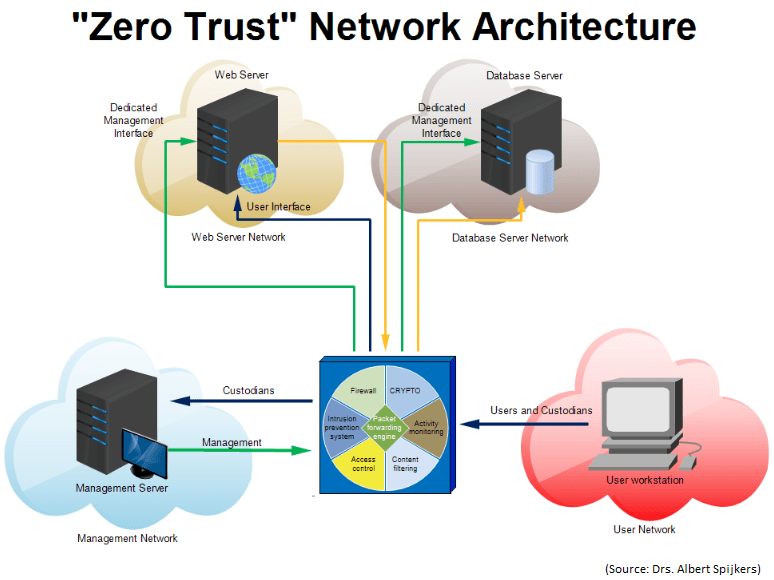
- Zero Trust Security Model
– A Framework for a Different Approach
I will refer to it as the Trusted Network model. This model is based on the theory that the external network is not secure, while the internal network within the corporate boundaries is considered secure.
What is Zero Trust Model?
A Zero Trust architecture changes access controls from the corporate network perimeter to individual devices and users, called endpoints
A Zero Trust model definitely has its appeal because it focuses on protecting the network endpoints, rather than network security boundaries on the perimeter
However, this model may not be practical for every organization. It may require replacing legacy applications, updating custom programs, or updating the network infrastructure, all of which come at a cost. In addition to the cost and complexity issues, monitoring endpoints closely also raises some serious privacy issues.
Forrester claims that “There is no chance of violating Civil Liberties – Zero Trust focuses on keeping internal data safe and would not result in any foreseeable encroachment on Civil Liberties.” It’s hard to believe that monitoring and logging all network traffic going in and out of the endpoints doesn’t encroach on Civil Liberties.
Forrester developed the Zero Trust model in 2010 and envisioned the model to be a vendor-neutral design so it is not tied to a specific technology or vendor.
Google decided to incorporate Forrester’s Zero Trust model into its “BeyondCorp” initiative whose mission is “To have every Google employee work successfully from untrusted networks without use of a VPN.” BeyondCorp is now available as a GCP service called Identity-Aware Proxy (IAP).
By shifting access controls from the network perimeter to individual devices and users, BeyondCorp allows employees to work more securely from any location without the need for a traditional VPN.”
What Will Not Change with Zero Trust Model
When businesses implement a Zero Trust model, the need for cybersecurity awareness training won’t go away.
Because the focus would be on endpoints, employees would have to become even more aware of cybersecurity threats because they won’t be inside a secure bubble that’s safe from the external attacks.
The wireless devices are more prone to cyberattacks and the smartphones and Internet of Things (IoTs ) are a good excuse for organizations to implement a Zero Trust model.
https://www.zubairalexander.com/blog/zero-trust-security-model/
- What is Zero Trust Security?
most enterprise security models have tended to employ a “verify, then trust” model, which means if someone has the correct user credentials, they are admitted to whichever site, app, or device they are requesting.
Why a Zero Trust Security Model is Needed
New business initiatives and processes have created new attack surfaces, and a corporate security perimeter no longer makes sense.
Applications, users, and devices are moving outside, dissolving what was once the trusted enterprise perimeter. Protection is now needed where applications and data, and users and devices, are.
Common IT Challenges
Network Trust and Malware
IT needs to ensure that users and devices can safely connect to the Internet, regardless of where they are connecting from
How to Start Your Zero Trust Security Journey
Move to a least-privilege application access model
If you opt for a simple VPN setup, you probably do what many companies do — you allow logged-in users to have IP-level access to your entire network
why should a contractor using your billing system have access to the credit card processing terminals? Access should be to just those applications needed in order to perform a role.
Get an access solution that:
Keeps users off the corporate network
Provides single sign-on for all corporate applications (on-premises, SaaS, IaaS )
Enables you to add multi-factor authentication
Includes application acceleration and application security built in
Get a threat protection solution that
Protects users on and off network
Provides visibility of all
Internet-bound traffic
Prohibits DNS-based data exfiltration
https://www.akamai.com/us/en/solutions/security/zero-trust-security-model.jsp
- General Inefficiencies of VPN
What you might not want to concede is that VPNs pose a very real threat to enterprise security. By their very nature, they punch a hole in the network firewall and typically provide unfettered network access. They also lack intelligence; VPNs can’t accurately confirm the identities of those who are trying to access your network or provide a continuously adaptive go/no go based on multi-factor authentication (MFA)
Eliminating your VPN is not only a viable option, but it is becoming imperative due to four modern real
workforce mobility, varied digital ecosystems, cloud migration, and the threat landscape
A cloud-based service enables IT to implement a zero trust security framework by closing all inbound firewall ports and keeping users off the network, while simultaneously providing users the instant, vital application access they require to do their jobs — and all of this can be executed with considerable ease by IT through a single portal in minutes instead of day
How Does a Cloud Framework for Application Access Work?
View an application access cloud architecture as your universal portal.
That means you’ll have
data path protection,
identity and access management (IAM),
application security and acceleration,
and single sign-on (SSO) —
— in one service across all applications
This, in turn, provides secure service to all users, remote or otherwise, with no direct path into your network
Instead, it delivers a mutually authenticated Transport Layer Security (TLS) connection from within your data center or cloud, thus bringing the permitted applications directly to the use
Maybe best of all, the applications are now presented in any browser on the user’s device of choice
The 4 Benefits of VPN Elimination
Determining the explicit applications that a user needs, and limiting access accordingly
It’s increasingly vital for businesses to not only identify users’ devices, but to also verify the identity of the specific individual requesting access
cloud-based access delivers four key improvements across the organizatio
1. SIMPLER, MORE SPECIFIC REMOTE ACCES
Challenge: Unnecessary Full-Network Acces
Organizations should strive to reduce their attack surface by identifying only the applications needed per user.
Yet once you eliminate a VPN, you are also eliminating redundancies and gratuitous permissions — along with needless, time-consuming security monitoring
Solution: Identify the End User, Device, and Context
trust should be continually assessed based on identity, device, and contextual signals in terms of location, time of day, authentication state, group membership of user, and more
it becomes imperative to not only authenticate and authorize the individual who is requesting access, but also the device and the context in which they are requesting
2. REDUCTION IN MANAGEMENT AND IT SECURITY BURDEN
Challenge: Permissions for Non-Employee
If best practice is to limit access for your employees, it’s certainly necessary to qualify and restrict access to the other members of your ecosystem as well , such as contractors and client
And as access controls are based on identity versus IP address, the next logical step would be to empower IT to simply and quickly set policies that bind a user to a given application, without making hardware upgrades and laborious, blanket changes to the networ
Solution: Set Secure Authorization Parameter
Establish one centralized control point for both authentication and monitoring to curtail access and reduce the risk of a potential malicious actor acquiring network credentials
3. STREAMLINED SECURITY POLICIE
Challenge: Digital Transformation Increases Risk Exposure
Fragmented security policies are inevitable with VPNs or VPCs, and they will eventually increase your company’s exposure due to ongoing routing environment complexities and manual deploymen
Solution: Adopt a Zero Trust Strategy
And when you need to set or adjust a policy, you can quickly and simply configure a new user without additional installation
Complete auditing and reporting of user activity will be at your fingertips on the back end as wel
4. ERADICATION OF END-USER FRUSTRATIONS WITH SEAMLESS ACCES
Challenge: Eliminate Unwieldy Processes
Solution: Adapt in the Cloud
data path protection,
IAM,
application security and acceleration,
SSO,
MFA,
and more are easily and immediately integrated, managed, monitored, and updated through this cloud architecture
Faster, simpler, and more secure solutions are available to lock down all inbound firewall ports while providing end users with remote access to only the specific applications they need.
https://www.akamai.com/us/en/multimedia/documents/white-paper/the-4-benefits-of-vpn-elimination.pdf
- Zero Trust Security Architectures - Akamai's Approach
This post will explain Akamai's approach, which is based on an Identity Aware Proxy (IAP) architecture in the cloud.
Much like Google's Beyond Corp model, Akamai has adopted an IAP architecture for our own corporate security.
Akamai's platform provides a security framework that only delivers apps and data to authenticated and authorized users, allows inline inspection and logging of traffic, prevents malware and DNS-based breaches, protects end users from phishing attacks, can identify and block bot traffic, connects to modern SaaS applications as well as legacy data center apps, seamlessly integrates with a Web Application Firewall (WAF) for advanced threat protection, and provides clientless application access while ensuring those applications are fast and reliable.
EAA allows enterprises to provide access to private applications over the internet, whether hosted in the cloud or in a data center and enforce the "need to know" principles of least privilege and zero trust.
Only authenticated users and devices have access to the internal applications they are authorized to access, and no inbound firewall ports need to be opened or maintained
EAA integrates data path protection, single sign-on, identity access, application security, and management visibility and control into a single cloud-based service backed by the Akamai Intelligent Platform.
It ultimately secures private enterprise applications and creates an air gap between those applications and the Internet, thus minimizing the attack surface and making the enterprise infrastructure and data invisible to the public.
Unlike software defined tunnels that utilize point to point VPNs, EAA is clientless for web-based applications. All that is required is an HTML5 compliant web browser, the Akamai Intelligent Platform and a reverse proxy component (the Akamai Enterprise Connector - AEC) in the data center or IaaS (virtual private cloud). The Enterprise Connector requires no local management and has no inbound open tunnels or ports to the enterprise. It is a pre-configured, hardened virtual machine supporting most hypervisors and containers. It mutually authenticates with the Akamai Platform over TLS. For identity management, EAA integrates with any identity store such as Active Directory or a SAML IdP.
The user authenticates, using Multi-Factor Authentication (MFA) if required, through the browser over TLS with the Akamai Platform and the enterprise's identity store. Once securely authenticated, Akamai simply stitches together the user's TLS session with the Enterprise Connector's over the Akamai Platform to provide access only to the authorized applications on the enterprise network, and nothing else. Single Sign-On may also be utilized to provide seamless app access.
Akamai has built its cloud-based zero trust model around an IAP because of the security controls and reductions in attack surface, simplicity of deployment, the value of service insertion from an application-layer approach, ease of operations and maintenance, and identity-based security.
https://blogs.akamai.com/2018/10/zero-trust-security-architectures---akamais-approach.html
What is BeyondCorp? What is IAP (BeyondCorp in a Bottle)
- A brief history of
BeyondCorp and Zero Trust
A brief history of BeyondCorp and Zero Trust
A particular network connection must not determine which services a user can access.
All access to services must be authenticated , authorized and encrypted.
Core Zero Trust recommendations include:
Ensure all resources are accessed securely regardless of location
Adopt a least-privileged strategy and strictly enforce access control
Continuously monitor the ecosystem
although BeyondCorp sought to replace the VPN while ZeroTrust pushed for stronger segmentation with Next-Gen Firewalls, both concepts essentially say the same thing:
Do not rely on location and perimeter for security
Enforce granular access controls based on context
Continuously monitor and adapt your security policies
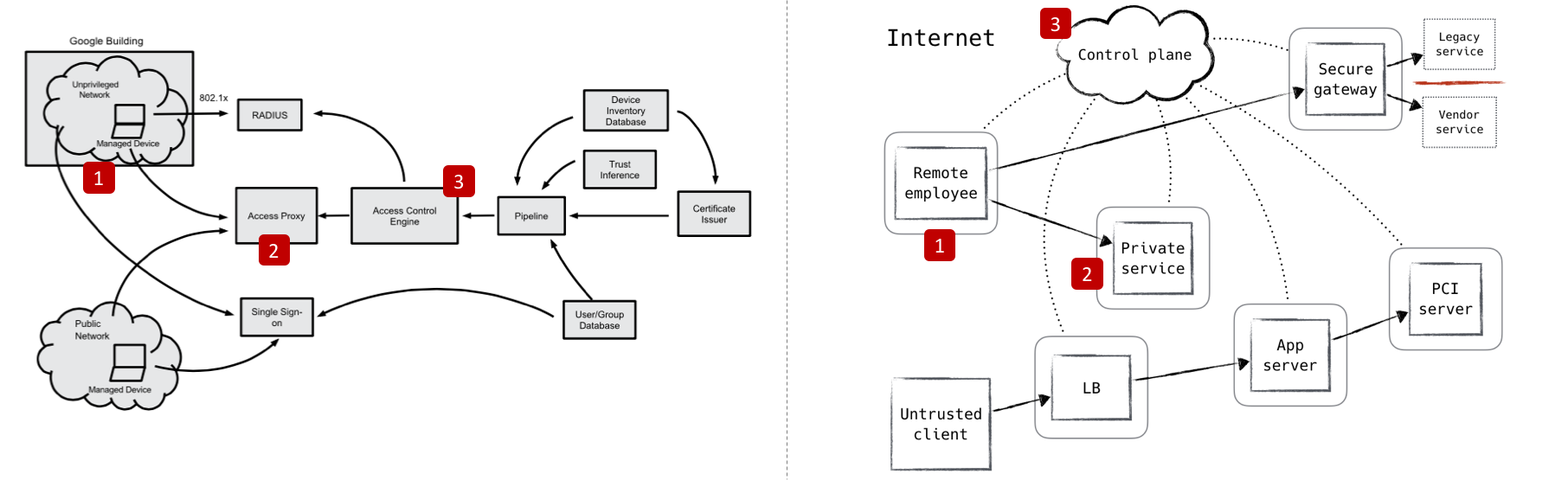
First, too many Zero Trust initiatives make the fundamental mistake of focusing solely on the network layer.
As the end-to-end principle tells us, controls should lie close to the users and applications we are securing , and not in the network infrastructure.
Second, many BeyondCorp and Zero Trust solutions do not leverage the capabilities that modern clouds such as AWS and Azure provide; they instead force organizations to purchase and manage entirely new sets of duplicate functionality.
A common pattern involves setting up a Man-In-The-Middle Cloud DMZ to mediate access instead of using the native capabilities in AWS Load Balancer and Route53. Another pattern involves deploying Next Gen Firewalls and Host-based Microsegmentation instead of using AWS VPCs and Security Groups.
we propose four new guidelines for security teams charged with deploying ZeroTrust and BeyondCorp initiatives:
Make no changes to the network. Your security initiative should not require changes to network management in order to roll out Zero Trust.
Incrementally roll out new security measures without changing apps. A Zero Trust solution should have the capability to be rolled out one brownfield service at a time, without mandating organization-wide or application changes.
Architect solutions that go beyond the perimeter. Zero Trust architectures should have the ability to manage controls down to individual users and devices, and the services and hosts they access.
Leverage existing enterprise tools. The ideal Zero Trust and BeyondCorp architecture should leverage existing enterprise investments via integrations. This applies not just to leveraging public cloud platforms but also to using existing identity providers, enterprise device managers and workload orchestrators.
https://www.banyanops.com/blog/beyondcorp-zero-trust/
- How Zero-trust Network Security Can Enable Recovery From Cyberattacks
Corporate risk managers and security professionals understand that risk is not a problem that can be solved , but rather a process that must be managed .
Cyber DRaaS in a Zero-trust Network
Zero trust places a high-performance NGF cluster at the center of the network to act as a data traffic distribution hub, segmenting the network into isolated work groups.
Zero trust also assumes that all data traffic on the network is untrusted. Therefore, all traffic must be scanned for malware and then authorized by the NGF according to a predetermined rule set before being allowed to traverse the network within a work group
https://www.isaca.org/Journal/archives/2014/Volume-6/Pages/How-Zero-trust-Network-Security-Can-Enable-Recovery-From-Cyberattacks.aspx?utm_referrer=
- Zero Trust
https://www.vmtech.com.au/cyber-security/new-zero-trust/
- What Is Zero Trust?
Its intent is to design network security from the inside-out rather than the old outside-in notion.
The inside-out Zero Trust approach involves determining a microcore and perimeter (MCAP). The MCAP is an interior definition of data, services, applications, or assets to be protected by a comprehensive set of controls.
Employees, contractors, and partners are insiders, and they must be enabled to operate with appropriate controls for performing their roles within your organization’s infrastructure.
To build a Zero Trust network, you can apply a data-centric approach. The security controls should be as close to the data as possible
To architect a zero trust data-centric MCAP, follow these steps:
Know where your organization’s data is.
Classify your data.
Securely dispose of data you no longer require.
Understand what roles should have access to the data classifications.
Apply the principle of least privilege to enforce access controls to verify and never trust.
Use multifactor authentication for administrative access and data access.
Use encryption for data at rest and data in flight.
Monitor and log all access.
Alert suspicious access or behaviors.
Where Is Your Data?
identify where your organization’s data exists and who has access to it
If you do not understand where your data is and who has access to it, UBA can provide a baseline to build classification and policy from empirical observations.
Classifying Your Data
Classification of the data, in the terminology of the Zero Trust model, involves identification of toxic data. Toxic data is sensitive data that is not intended to be exposed outside an organization.
Delete the Data You No Longer Require
Unnecessary data is a liability to retain . It should be deleted .
Controlling Access to Your Data
Mapping access to the sensitive data and applying the principle of least privilege means giving people in your organization access only to the data required to perform their jobs and nothing more. This involves the use of role-based access control (RBAC), which applies not only to data access but also administrative access
MFA for administrative access is a requirement for U.S. public sector organizations or those that must follow the PCI-DSS.
enabled by Security Assertion Markup Language (SAML) 2.0. SSH command-line access uses chained two-factor authentication using a public key and password
Data-at-Rest Encryption
a capability called secure purge to cryptographically remove toxic data
Data-in-Flight Encryption
protects user data access and control plane access.
FIPS mode for control plane access, which enables FIPS-approved algorithms and disables algorithms that are not FIPS approved .
Monitoring and Logging Data Access and Suspicious Behavior
After RBAC policies are in place, active monitoring, auditing, and alerting must be deployed
toward machine learning (ML) and artificial intelligence (AI) for greater event fidelity and fewer, if any, false positives. All events should be logged to a syslog server or to a security information and event management (SIEM) system, which can also employ ML and AI.
https://blog.netapp.com/achieve-a-data-centric-approach-to-zero-trust-with-netapp-ontap/
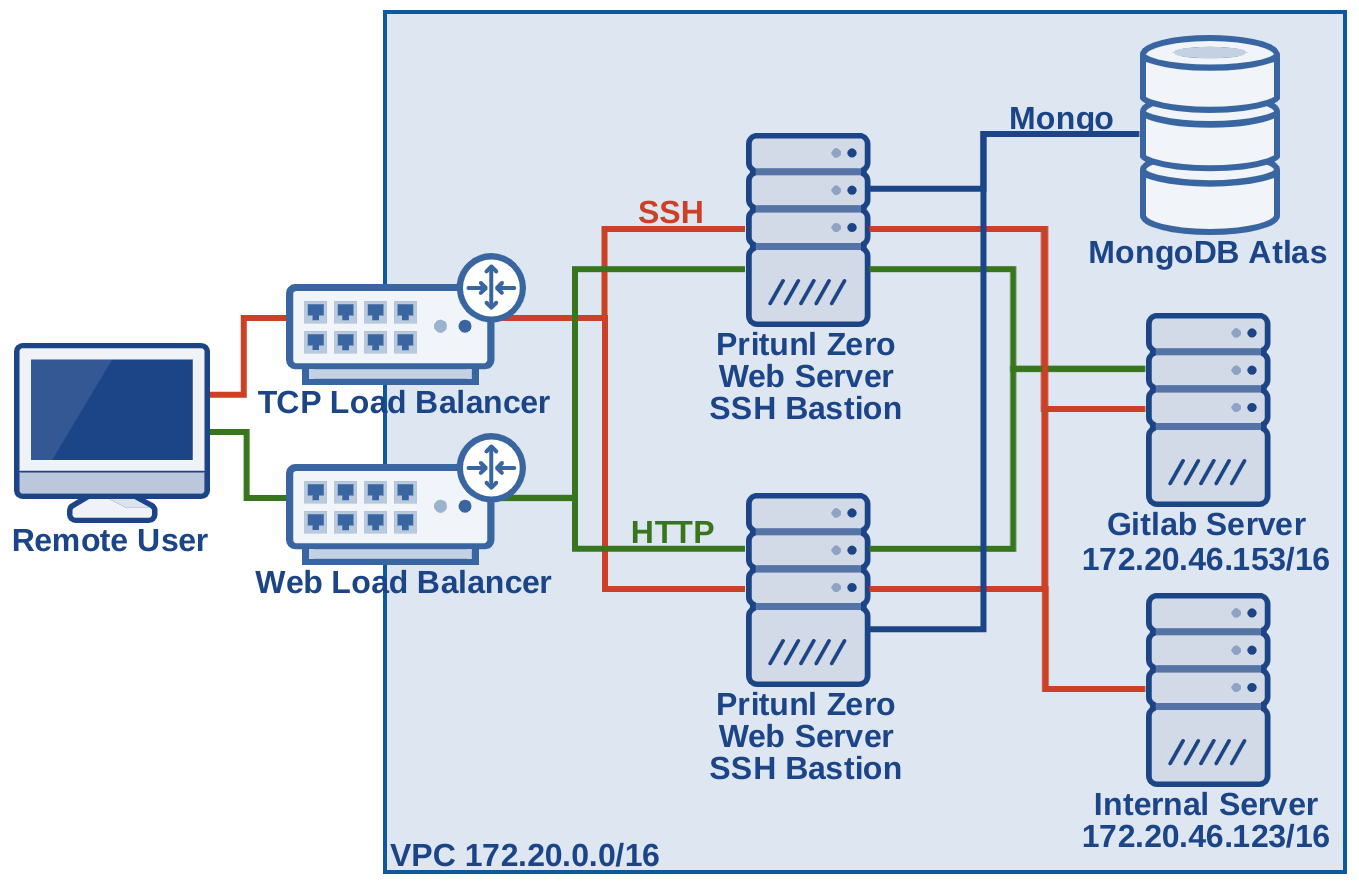
Pritunl Zero
Free and open source BeyondCorp server providing zero trust security for privileged access to ssh and web applications
https://zero.pritunl.com/
- 5 Steps to a Zero Trust Network - From Theory to Practice
Concepts of zero trust
All resources are accessed in a secure manner regardless of location.
Access control is on a “need-to-know” basis and is strictly enforced .
Verify and never trust.
Inspect and log all traffic.
The 5 Steps to a Zero Trust Network
1. Identify your toxic data sources
2. Map the transaction flows regarding toxic data
3. Architect a Zero Trust network based upon the toxic data sources and the way it's used transactionally
4. Write your rules on your segmentation gateway based on the expected behavior of the data and the users or applications that interact with the data
5. Monitor the network; inspect and log the traffic; and update rules based up on the visibility and intelligence that you get from your security analytics system.
https://www.slideshare.net/AlgoSec/5-steps-to-a-zero-trust-network-from-theory-to-practice
- Re-Building the Secure Network
FW
WLAN GW
IPS
WAF
NAC
Email
WCF
DAM
DLP
DB ENC
VPN
CRYPTO
AM
CF
FW
IPS
AC
Packet Forwarding Engine
Zero Trust Drives Future Network Design
MCAP – Micro Core and Perimeter
MCAP resources have similar functionality and share global policy attributes
MCAPs are centrally managed to create a unified switching fabric
Management = Backplane
https://slideplayer.com/slide/4775506/
- In 2010, Forrester branded the concept of a Zero Trust network. In 2014, Google implemented it as the
BeyondCorp security approach. In 2017, Gartner framed it as continuous adaptive risk and trust assessment (CARTA).
The BeyondCorp implementation of Zero Trust architecture
Step 1: Securely identify the device
Build a meta-inventory database of “managed device” identities using device certificates, which are issued upon a qualification process with periodic reviews.
Step 2: Securely identify the user
Generate short-lived authorization tokens using a centralized, single sign-on portal with multifactor authentication that validates identity against a user and group database.
Step 3: Remove trust from the network
RADIUS servers dynamically assign “managed devices” to an unprivileged network or “unmanaged devices” to a guest network via 802.1x authentication, which checks for the device certificates from Step 1.
Step 4: Externalize apps and workflow
An Internet-facing reverse access proxy enforces encryption between the client and application for all web-based apps via CNAME (public DNS) records.
Step 5: Implement inventory-based access control
Per application access request, enforce service-level authorization by first interrogating multiple data sources to dynamically infer the level of device or user trustworthiness.
https://www.cisco.com/c/en/us/products/security/zero-trust-network.html
- Learning about SDP via Google
BeyondCorp
Google’s software-defined perimeter (SDP) architecture can act as a model that enterprise organizations can emulate and enhance over time .
If you are not familiar with BeyondCorp , it is Google’s spin on what’s become known as a software-defined perimeter (SDP). SDP, also called a “black cloud,” originated at the Defense Information Systems Agency (DISA) and is now being driven by the Cloud Security Alliance (CSA).
If you are not familiar with BeyondCorp , it is Google’s spin on what’s become known as a software-defined perimeter (SDP). SDP, also called a “black cloud,” originated at the Defense Information Systems Agency (DISA) and is now being driven by the Cloud Security Alliance (CSA).
SDP is closely aligned with previous work done with network access control (NAC).
https://www.csoonline.com/article/3053561/learning-about-sdp-via-google-beyondcorp.html
- Fundamentals of the
BeyondCorp ‘Zero-Trust’ Security Framework
Core Concepts
This known fact is breaking down the walls of the traditional perimeter-based security methods, where trust is determined purely by being on the inside or outside.
Instead, all applications and services are deployed to the public Internet, where access is granted based on a device, its state, and the associated user.
Zero Trust by Default
Instead of granting privileged access based on location and network rules, the BeyondCorp framework authenticates and authorizes every request in real-time based on a set of dynamic conditions, accounting for the constant changes in user status and device state.
Once access is granted , a short-lived credential is issued only for that specific request.
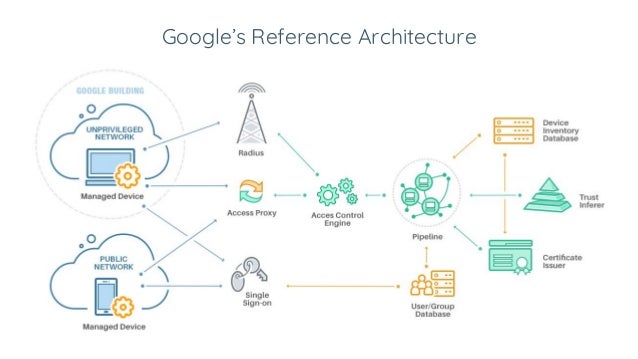
Google maintains an always updating inventory of employee devices that they monitor with a system known as the Trust Inferer .
This system captures device and host properties, such as whether the disk is encrypted or the latest patches installed.
Based on this information, Google assigns the device to a Trust Tier, which is a representation of its permitted access levels.
Every resource then has an associated minimum tier that must be met to be accessed , based on the sensitivity of the data.
Centralized Access Proxy
Google places a reverse proxy in front of every resource
Each request flows through this central point, where it is fully authenticated and authorized .
For authentication, Google operates its own Identity Provider service as the system of record, which supports a wide range of options such as OpenID Connect and OAuth to handle all of the types of methods a backend service may use
Once identity is confirmed , authorization is verified through Access Control Lists that are queryable via remote procedure calls.
Google developed its own domain-specific language for the Access Control Lists that is easily understandable
The Access Proxy handles coarse-grained policies across the organization, while the Trust Inferer enforces fine-grained policies more specific to an individual resource.
Key Advantages
shifting access controls from the perimeter to individual users and devices
Real-Time Trust Evaluation
Intelligent Decision Making
The authentication and authorization processes are tightly integrated with the workflows employees are already used to, providing advanced security measures without negatively affecting productivity.
Enforced Security Controls
Another byproduct of moving all sensitive resources to the untrusted public Internet is forming better habits for communicating over secure channels, encrypting data, monitoring all endpoints, implementing multi-factor authentication, keeping a device inventory, and managing credentials.
Device Management
With BeyondCorp , device data is just as important as user data for evaluation.
Adopting BeyondCorp
If we boil down BeyondCorp to its essence, it’s a modern take on the established Authentication, Authorization, and Accounting (AAA) framework that factors in the distributed teams and connected devices that make up a modern enterprise organization.
https://dzone.com/articles/fundamentals-of-the-beyondcorp-zero-trust-security
Use identity and context to sign in to apps and VMs
Cloud Identity-Aware Proxy (Cloud IAP) controls access to your cloud applications and VMs running on Google Cloud Platform (GCP). Cloud IAP works by verifying user identity and context of the request to determine ifa user should be allowed to access an application or a VM
https://cloud.google.com/iap/
BeyondCorp is about making intelligent access decisions based on the user and the state of the connecting device. This is only really useful if the corresponding credentials are dynamic, issued at a point-in-time that is understood , revocable, and auditable.
With a centralized Identity Provider such as Active Directory, Google Identity Platform, or Okta handling authentication, the next step is to tie in the authorization process with the resource being requested. ScaleFT Dynamic Access Management integrates with your IdP to issue short-lived client-certificates for every authorization event, removing the use of static credentials that can easily be lost or stolen.
Pushing all internal applications to the public Internet quickly forces better security practices such as end-to-end encryption and perfect forward secrecy, but can open your systems up to network attacks. Placing a reverse proxy in front of the services manages the traffic by balancing the load and identifying any potential threats.
what makesBeyondCorp unique is how both the user and connecting device together make up a profile where trust decisions can be made in real-time.
AdoptingBeyondCorp doesn’t necessarily mean you have to operate infrastructure the same way Google does, or anywhere near the same level of scale. For most organizations, it’s a better option to leverage a service such as CloudFlare for DDoS protection. For an on-prem solution, F5 offers a robust appliance for similar use.
BeyondCorp is just as much about minimizing the risk of insider threats as it is about thwarting cyber attacks.
Organizations adopting DevOps best practices should closely examine the security implications of automation. For example, a CI/CD pipeline may includea number of tools coordinating with each other through an event-driven pipeline. These tools are performing administrative functions, which means the need the privilege to do so
https://www.scaleft.com/blog/googles-infrastructure-security-design-revealed/
The isolation provided to the VMs is based on hardware virtualization using the open source KVM stack. We have further hardened our particular implementation of KVM by moving some of the control and hardware emulation stack into an unprivileged process outside the kernel. We have also extensively tested the core of KVM using techniques like fuzzing, static analysis, and manual code review.
https://cloud.google.com/security/infrastructure/design/
Use identity and context to sign in to apps and VMs
Cloud Identity-Aware Proxy (Cloud IAP) controls access to your cloud applications and VMs running on Google Cloud Platform (GCP). Cloud IAP works by verifying user identity and context of the request to determine if
https://cloud.google.com/iap/
- You must first implement
authentication , authorization, and accounting (AAA) that covers your employees, systems, and applications.
With a centralized Identity Provider such as Active Directory, Google Identity Platform, or Okta handling authentication, the next step is to tie in the authorization process with the resource being requested
Pushing all internal applications to the public Internet quickly forces better security practices such as end-to-end encryption and perfect forward secrecy, but can open your systems up to network attacks. Placing a reverse proxy in front of the services manages the traffic by balancing the load and identifying any potential threats.
what makes
Adopting
Organizations adopting DevOps best practices should closely examine the security implications of automation. For example, a CI/CD pipeline may include
https://www.scaleft.com/blog/googles-infrastructure-security-design-revealed/
- Google Infrastructure Security Design Overview
The isolation provided to the VMs is based on hardware virtualization using the open source KVM stack. We have further hardened our particular implementation of KVM by moving some of the control and hardware emulation stack into an unprivileged process outside the kernel. We have also extensively tested the core of KVM using techniques like fuzzing, static analysis, and manual code review.
https://cloud.google.com/security/infrastructure/design/
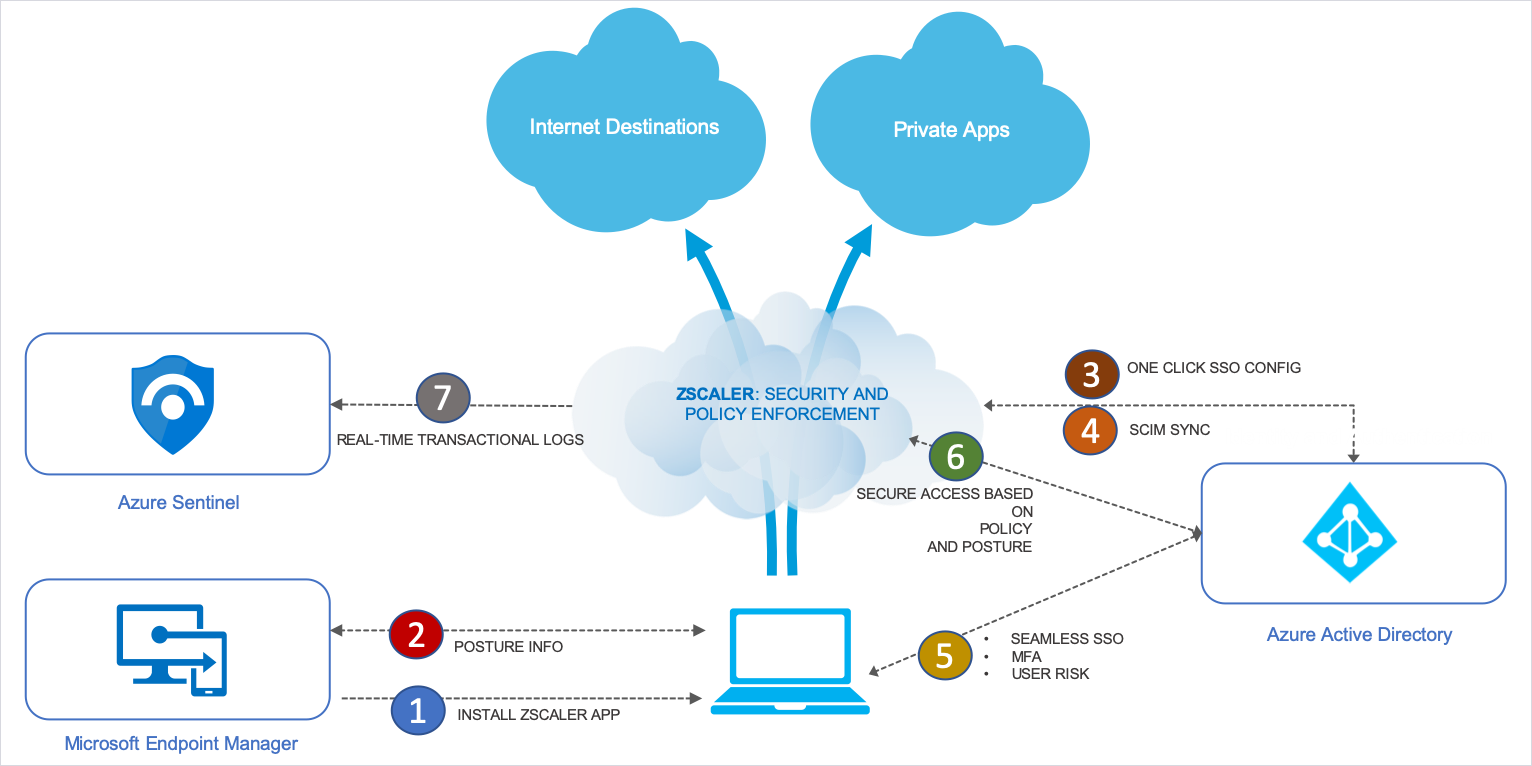
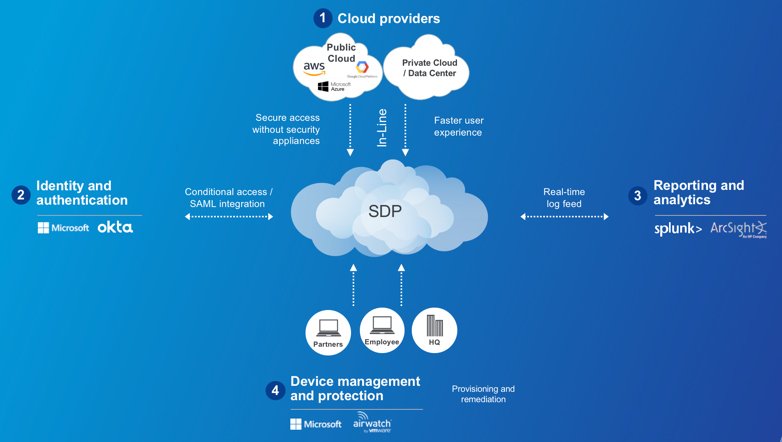
The zero trust ecosystem
At the heart of this ecosystem is a software-defined perimeter (SDP) solution.cloud-based technologies that securely connect users to internal apps
via the internet instead of network firewalls and appliances.zero trust security ecosystem players:
Identity providers (such as Azure AD, Okta, Ping, Centrify):
These password and authentication providers integrate with SDPs and are
used to centralize identities, simplify management, and provide
authorized access to apps by creating and passing SAML attributes.
Mobile device management (such as Intune, AirWatch, MobileIron, Good Technology):
These solutions can be used to silently deploy SDP software onto
endpoints so that all connectivity from iOS, Android, Windows, and Mac
devices is based on zero trust
SIEM providers (such as Splunk, LogRhythm, EventTracker):
A key technology within the enterprise SOC, SIEM is used to provide
visibility into user activity and consume audit logs coming from the SDP
to identify suspicious activity.
IaaS platforms: Platforms such as Azure, AWS, and
Google Cloud Platform (to which many internal apps are now migrating) do
have some high-level security features of their own, such as the AWS
Security Groups. But, teams can combine these with a purpose-built SDP
solution to provide secure access to cloud apps across hybrid and
multi-cloud environments
https://www.zscaler.com/blogs/corporate/zero-trust-security-5-reasons-its-not-about-firewalls-and-passwordshttps://www.zscaler.com/blogs/corporate/zero-trust-security-5-reasons-its-not-about-firewalls-and-passwords