- Introduction To Perfect Forward Secrecy
If
This holds true of every SSL/TLS session using that private key. Even though each secure session will have used a separate and
Implementation of PFS
SSL and TLS are
‘server gating
This is how, for instance, ‘server gating’ operates where a server can mandate that
Therefore, to implement PFS it is necessary to make suitable cipher suites available on the server receiving the connections and for the client
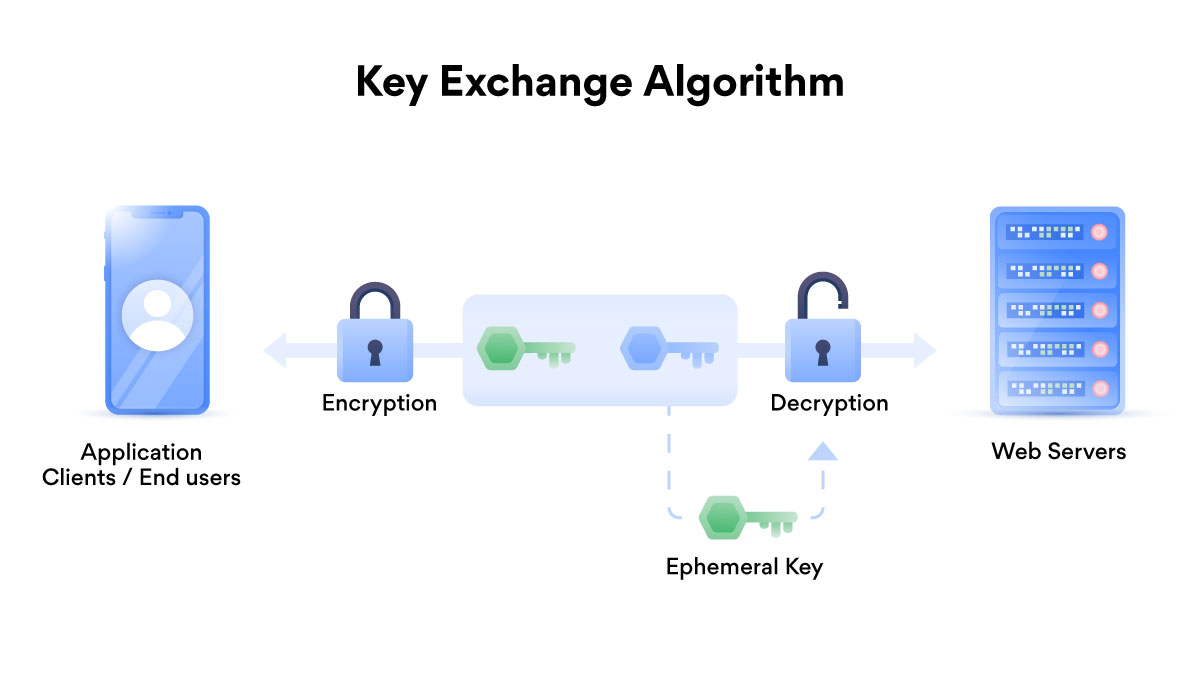
PFS-compliant key exchange mechanisms that are available include:
ECDHE_RSA - Ephemeral Elliptic Curve Diffie-Hellman with RSA signatures
DHE_RSA - Ephemeral Diffie-Hellman with RSA signatures
https://www.ciso-central.org/transport-layer-security/perfect-forward-secrecy
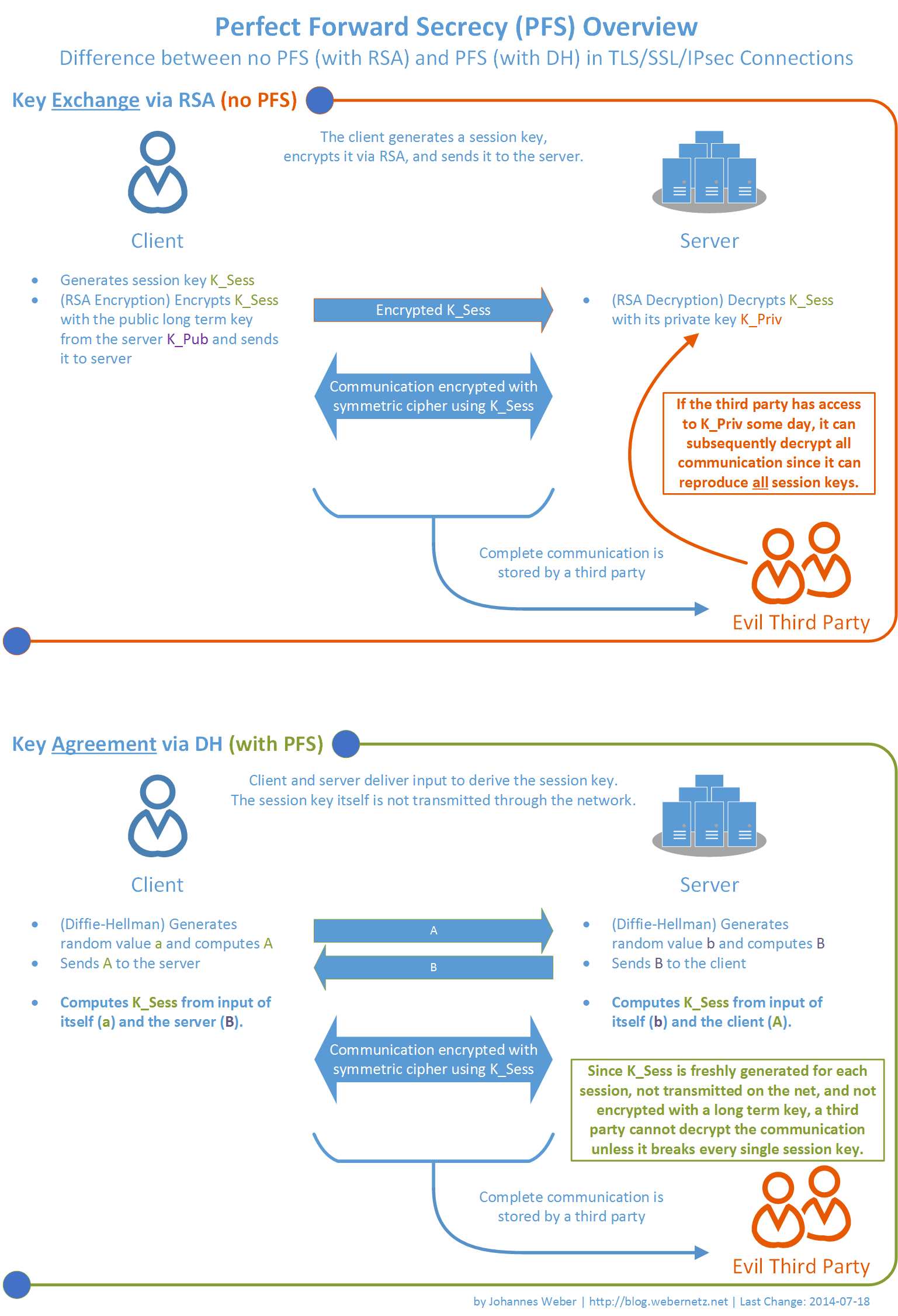
- When you use the RSA key exchange mechanism, it creates a link between the server’s key pair and the session key created for each
unique secure is ever able to
In contrast, when you enable Perfect Forward Secrecy (PFS), there is no link between your server’s private key and each session key. If an attacker ever gets access to your server’s private key, the attacker cannot use the private key to decrypt any of your archived sessions, which is why it
Deploying Perfect Forward Secrecy
Instead of using the RSA method for exchanging session keys,
Configuring Apache for Forward Secrecy
Configuring Nginx for Forward Secrecy
https://www.digicert.com/ssl-support/ssl-enabling-perfect-forward-secrecy.htm
- Deploying Perfect Forward Secrecy
Instead of using the RSA method for exchanging session keys,
Configuring Apache for Forward Secrecy
Before you configure your Apache server for Forward Secrecy, your web server and SSL/TLS library should support Elliptic Curve cryptography (ECC).
Minimum Required Versions
OpenSSL 1.0.1c+
Apache 2.4x
Configuring Nginx for Forward Secrecy
Before you configure your Nginx server for Forward Secrecy, your web server and SSL/TLS library should support Elliptic Curve cryptography (ECC).
Minimum Required Versions
OpenSSL 1.0.1c+
Nginx 1.0.6+ and 1.1.0+
https://www.digicert.com/ssl-support/ssl-enabling-perfect-forward-secrecy.htm#apache_forward_secrecy
- DROWN is a cross-protocol attack that exploits vulnerabilities in the SSLv2 implementation against transport layer security (TLS), the attacks doesn’t work against the SSLv2 connections.
DROWN exploits a bug in SSLv2 protocol implementation to attack the security of connections made under a different protocol, in this case, TLS.
Users need to update their OpenSSL to the newer versions 1.0.2g or 1.0.1s.
https://securityaffairs.co/wordpress/44945/hacking/drown-attack.html
- Hacker Lexicon: What Is Perfect Forward Secrecy?
To solve that problem of future security mistakes threatening past secrets, cryptographers have come up with a security feature called
For perfect forward secrecy to offer its intended protection in messaging apps, the user needs
Every modern browser
https://www.wired.com/2016/11/what-is-perfect-forward-secrecy/
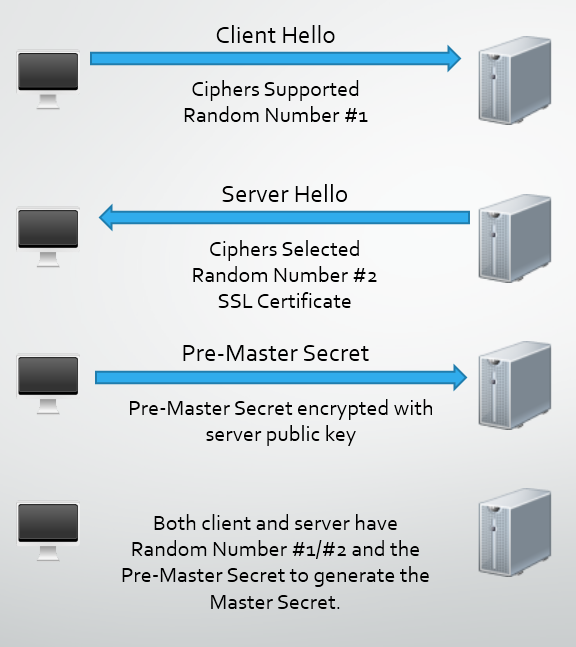
- What does this have to do with
Heartbleed
The Heartbleed bug allows an attacker to extract data from the memory of a vulnerable server. This includes things like usernames, passwords, email addresses, session data and worst of all, the server's private key. Once the private key has been compromised that it now has the private key for. This problem can be dealt Secondly all of the that is what is never actually sent right now,
How does Perfect Forward Secrecy help?
To enable PFS, the client and the server have to be capable of using be stored is derived is used to derive the session key. Even if the private key of the server is compromised because the associated public key was never used to protect anything. What's even better is that with Perfect Forward Secrecy, the server generates a new set of Diffie-Hellman parameters for each session and both parties create a new shared secret that is unique and unknown to an attacker. Even if the attacker managed to compromise particular No previous or future sessions would be compromised
https://scotthelme.co.uk/perfect-forward-secrecy/
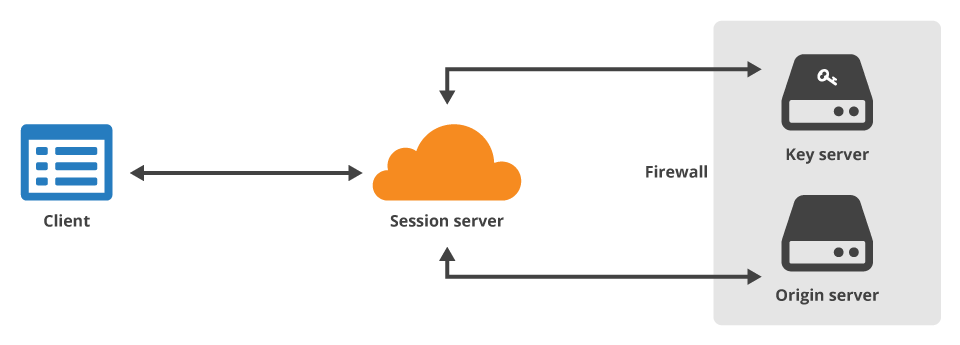
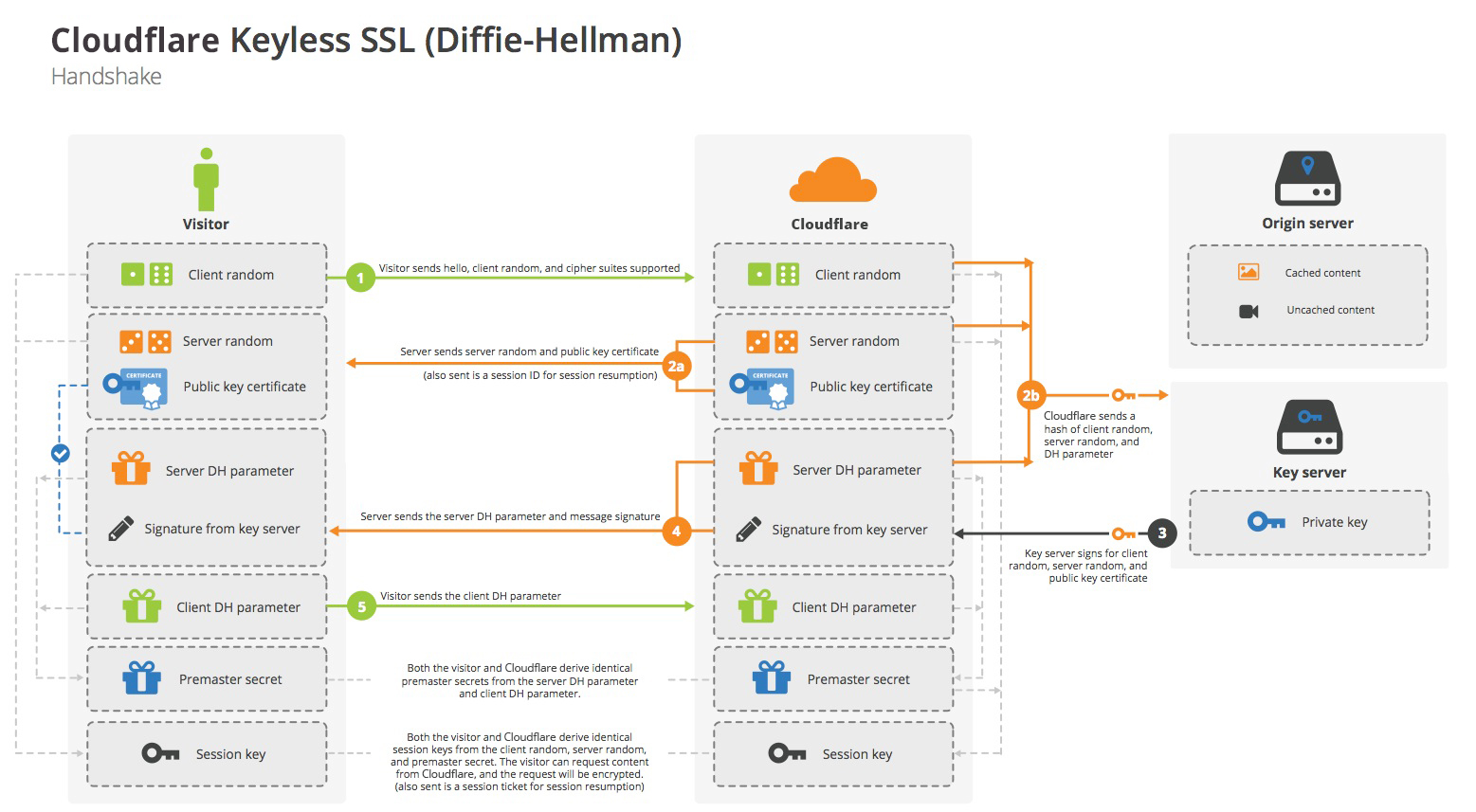
- What is keyless SSL?
Keyless SSL is a service for companies that use a cloud vendor for SSL encryption.
Usually this would mean that the cloud vendor has to know the company's private key, but keyless SSL is a way to circumvent that.
For regulatory reasons many organizations cannot share their private keys
SSL, more accurately known as TLS, is a protocol for authenticating and encrypting communications over a network.
SSL/TLS requires the use of what's called a public key and a private key, and in the case of a company using the protocol to secure traffic to and from their website (see HTTPS), the private key typically remains in the company's possession.
But when a company moves to the cloud and a vendor provides TLS encryption, the vendor has the private key instead.
By moving the part of the handshake involving the private key off of the vendor's server, the private key can remain securely in the company's possession. Instead of using the private key directly to generate session keys, the cloud vendor gets the session keys from the company over a secure channel and uses those keys to maintain encryption. Thus, a private key is still used, but it is not shared with anyone outside the company.
For instance, suppose that Acme Co. implements SSL. Acme Co. will securely store their private key on a server that they own and control. If Acme Co. moves to the cloud and uses a cloud service provider for web hosting, that vendor will then have the private key. However, if Acme Co. moves to the cloud with a vendor that implements keyless SSL instead, the private key can stay on the server that Acme Co. owns and controls, as in the non-cloud SSL implementation.
How does keyless SSL work?
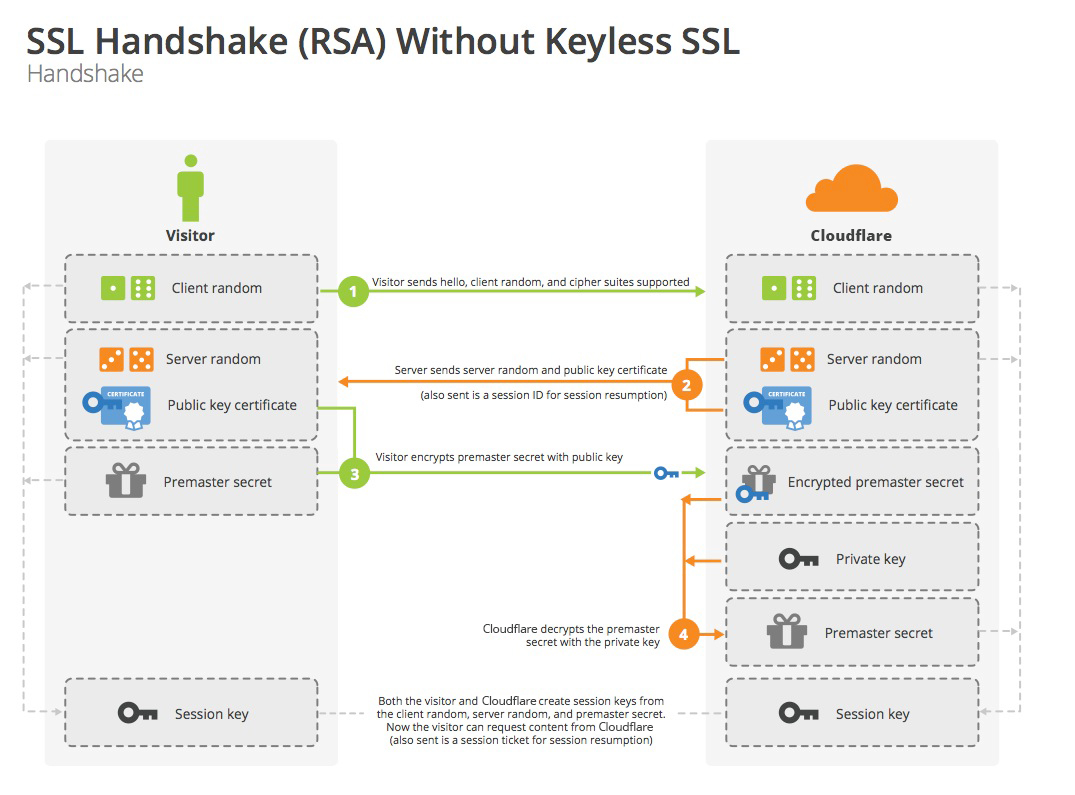
Keyless SSL is based on the fact that there is only one time when the private key is used during the TLS handshake, which occurs at the beginning of a TLS communication session. Keyless SSL works by splitting the steps of the TLS handshake up. A cloud vendor offering keyless SSL moves the private key part of the process to another server, usually a server that the customer keeps on premises.
When the private key becomes necessary during the handshake for decrypting or encrypting data, the vendor's server forwards the necessary data to the customer's private key server. The private key encrypts or decrypts the data on the customer's server and sends the data back to the vendor's server, and the TLS handshake continues like usual.
Keyless SSL is only "keyless" from the cloud vendor's point of view: they never see their customer's private key, but the customer still has and uses it. Meanwhile, the public key is still used on the client side like normal.
https://www.cloudflare.com/learning/ssl/keyless-ssl/