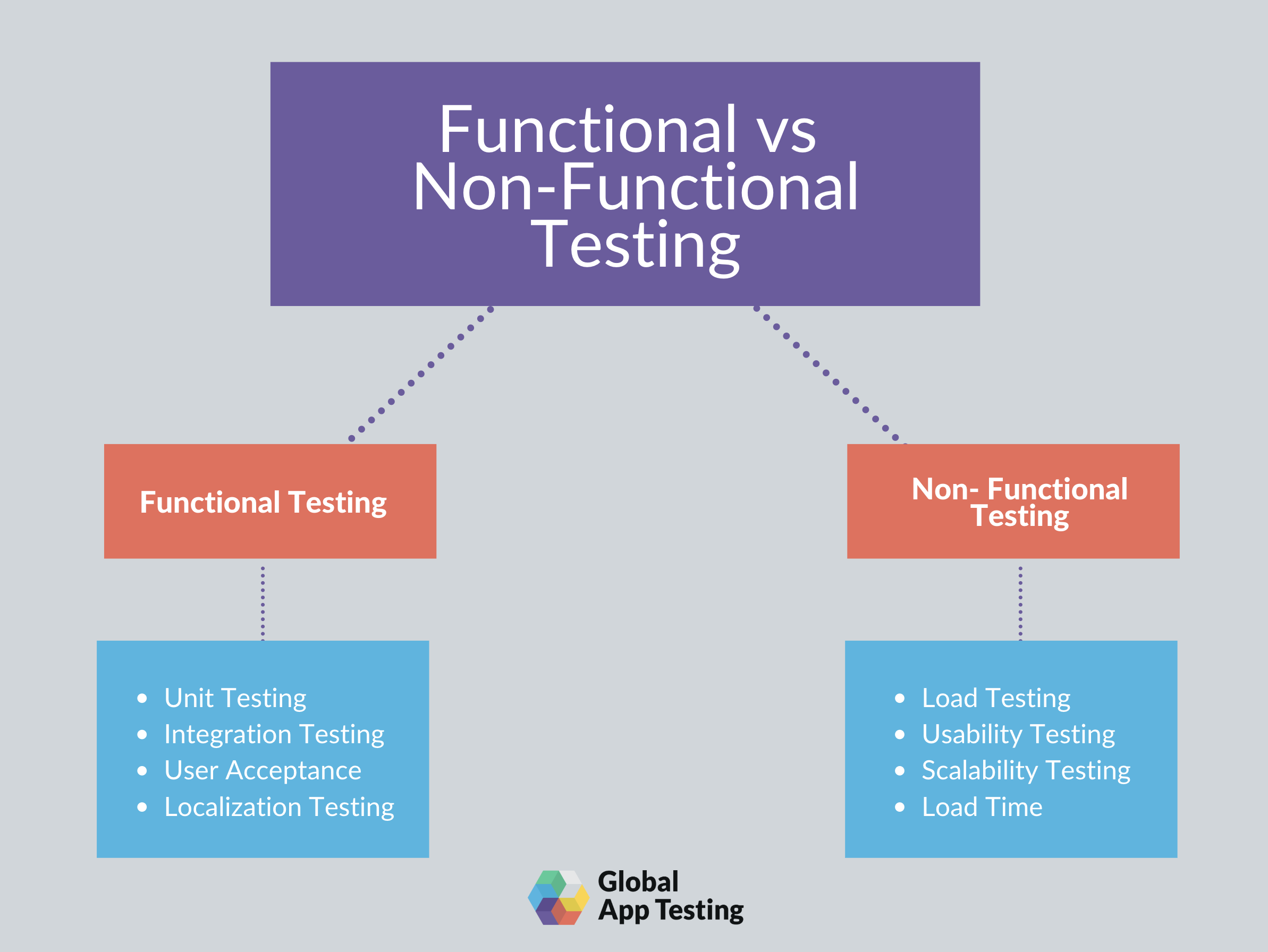
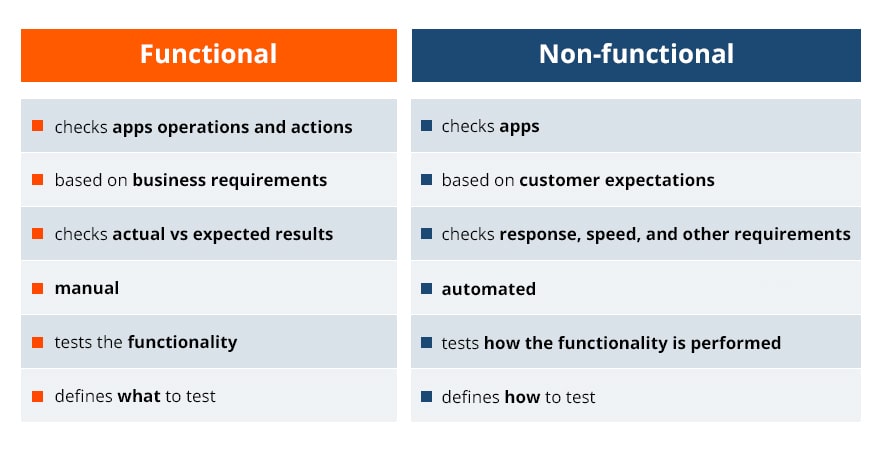
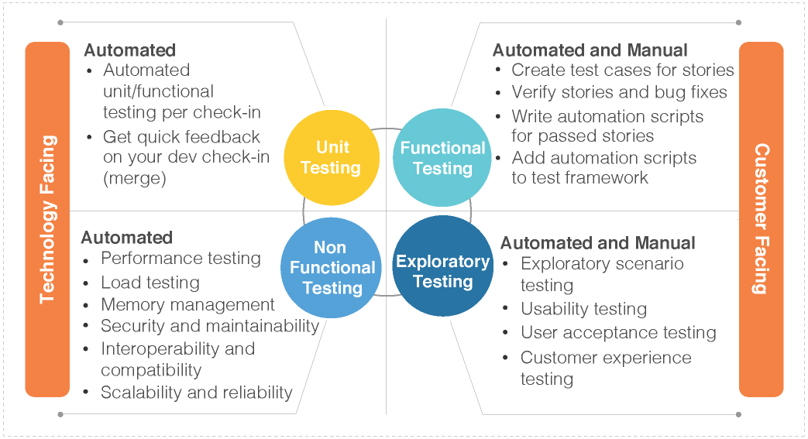
- The main difference between functional and nonfunctional testing
Functional requirements: describe the behavior/execution of the software system
Non-functional requirements: describe the performance or usability of the software system
Here are some of the common functional testing techniques:
Installation testing – for desktop or mobile application, testing proper installation
Boundary value analysis – testing of the boundaries of numerical inputs
Equivalence partitioning – grouping tests together to reduce overlap of similar functional tests
Error guessing – assessing where functional issues are most likely to be found and testing these more extensively than other areas
Unit testing – testing performed at the smallest level of the software—not how the system is functioning as a whole, but whether each unit is executing properly
API testing – checks that internal and external APIs are functioning properly, including data transfer and authorization
Regression testing – tests that are performed to verify that new software changes did not have adverse effects on existing functionality (most common automation technique)
These are the chief nonfunctional testing techniques:
Load testing – tests performed on simulated environment to test the behavior of the system during expected conditions (various number of users)
Stress testing – testing performance when low on resources, such as server issues or lack of hard drive space on a device
Scalability testing – checking a system’s ability to scale with increased usage and to what extent performance is affected
Volume testing – testing performance with a high volume of data, not necessarily high number of users, but could be one user performing a high-volume task, such as a multiple-file upload
Security testing – tests performed to uncover how vulnerable the system is to attacks, and how well data is protected
Disaster recovery testing – checks on how quickly a system can recover following a crash or major issue
Compliance testing – tests of the software system against any set of standards (whether due to industry regulations or a company’s set of standards)
Usability testing – testing whether the GUI is consistent and if the application as a whole is intuitive and easy to use
https://testlio.com/blog/whats-difference-functional-nonfunctional-testing/#:~:text=Functional%20requirements%20are%20the%20WHAT,customer%20expectations%20are%20being%20met.
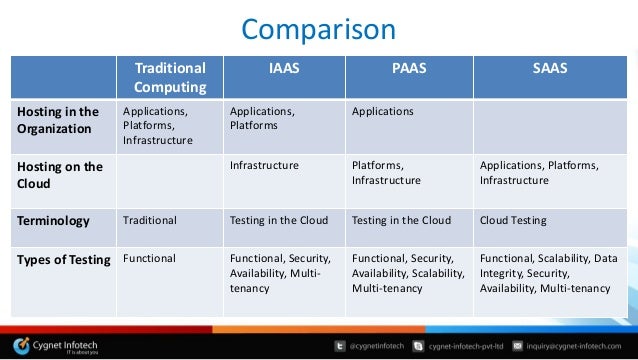
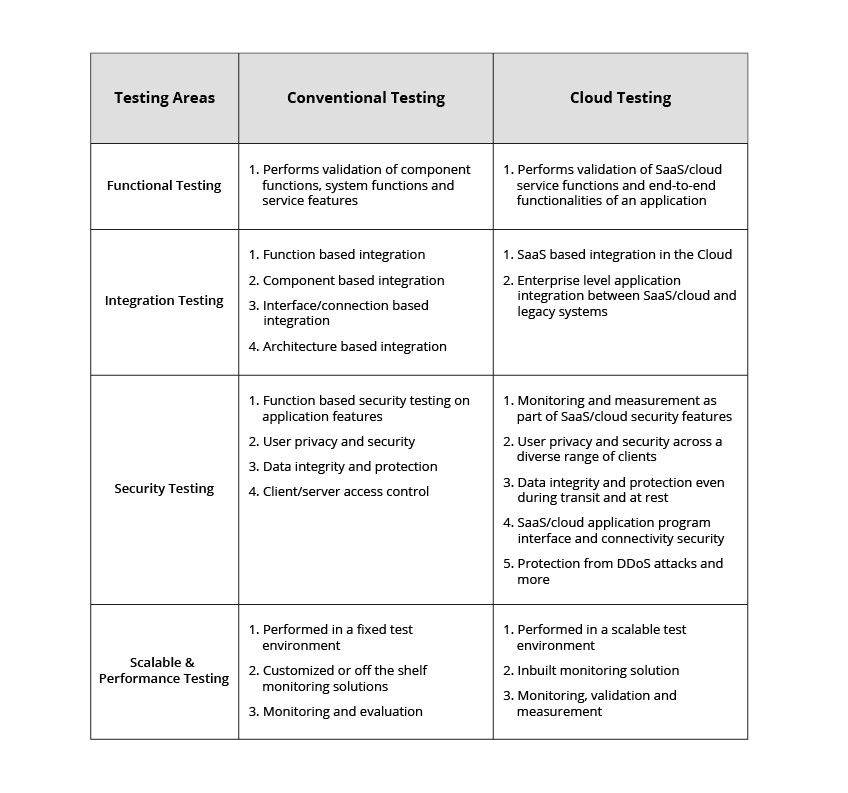
- Differences between Functional and Non-functional Testing
Functional Testing:
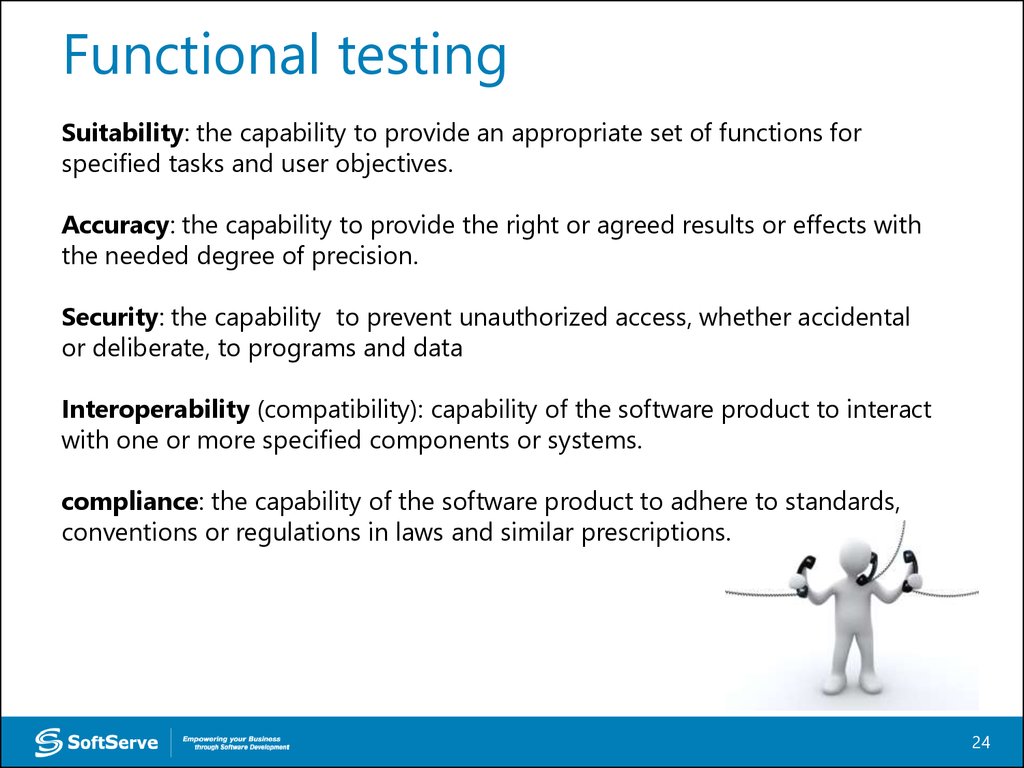
Functional testing is a type of software testing in which the system is tested against the functional requirements and specifications. Functional testing ensures that the requirements or specifications are properly satisfied by the application. This type of testing is particularly concerned with the result of processing. It focuses on simulation of actual system usage but does not develop any system structure assumptions.
Non-functional Testing:
Non-functional testing is a type of software testing that is performed to verify the non-functional requirements of the application. It verifies whether the behavior of the system is as per the requirement or not. It tests all the aspects which are not tested in functional testing.
https://www.geeksforgeeks.org/differences-between-functional-and-non-functional-testing/


- The implementation under test is that which implements the base standard(s) being tested.
https://link.springer.com/referenceworkentry/10.1007%2F978-0-387-73003-5_700
Implementation under test, a term used in technological vulnerability analysis, particularly protocol evaluation
https://en.wikipedia.org/wiki/IUT
Implementation Under Test (IUT) That part of a real system which is to be tested, which should be an implementation of applications, services or protocols.
https://portal.etsi.org/CTI/CTISupport/Glossary.htm
- The main difference is that regression testing is designed to test for bugs you don't expect to be there, whereas retesting is designed to test for bugs you do expect to be there.
The point of regression testing is to ensure that new updates or features added to software don’t break any previously released updates or features.
To perform regression testing you typically have a regression suite – a series of test cases set up to test these older features.
Regression test cases are often automated because these tests build up as the software changes or grows
retesting is designed to test specific defects that you’ve already detected (typically during your regression testing).
In other words, regression testing is about searching for defects, whereas retesting is about fixing specific defects that you’ve already found.
https://www.leapwork.com/blog/difference-between-retesting-and-regression-testing
Regression testing is performed for passed test cases while Retesting is done only for failed test cases
Regression testing checks for unexpected side-effects while Re-testing makes sure that the original fault has been corrected.
Regression Testing doesn’t include defect verification whereas Re-testing includes defect verification.
Regression testing is known as generic testing whereas Re-testing is planned testing.
Regression Testing is possible with the use of automation whereas Re-testing is not possible with automation.
https://www.guru99.com/re-testing-vs-regression-testing.html
- Examples of Functional testing are
Black Box testing
https://www.guru99.com/functional-testing.html
Black-box testing. Contrary to white-box testing, black-box testing involves testing against a system where the internal code, paths and infrastructure are not visible. Thus, testers use this method to validate expected outputs against specific inputs.
https://www.applause.com/blog/functional-testing-types-examples
- It helps detect defects in the software.
Testing is done by executing the program.
Dynamic testing involves both functional and non-functional testing.
https://www.professionalqa.com/dynamic-testing
- Ensures the functionality, reliability, and performance between the integrated module.
To be precise the success of Integration Testing lies in the perfection of the test plan.
https://www.professionalqa.com/integration-testing