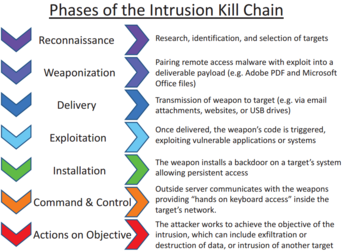
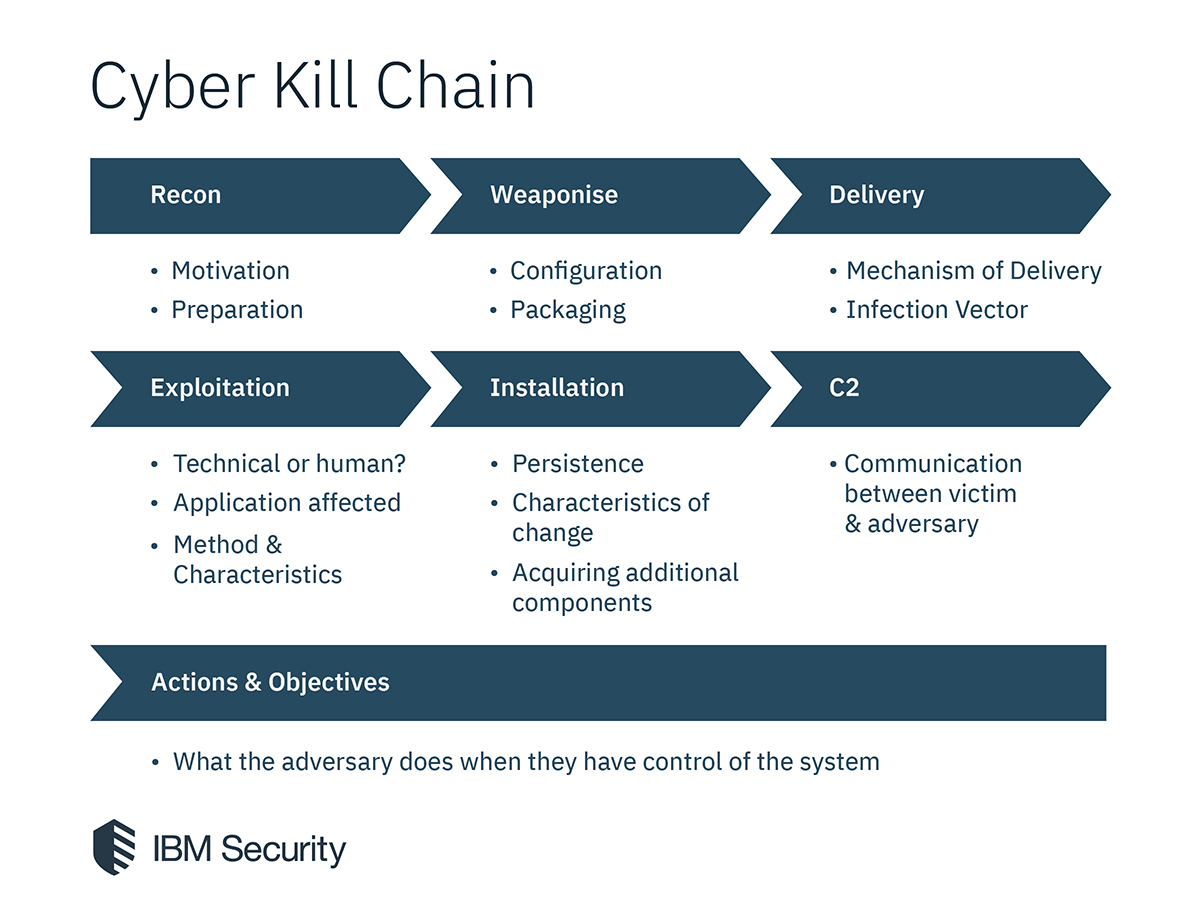
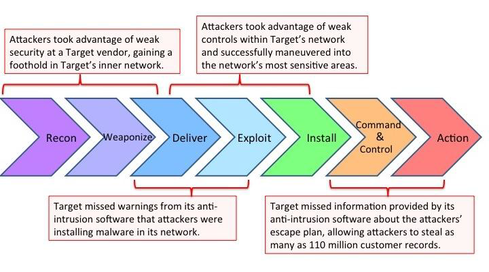
of a cyber attack and identifies various phases during a system intrusion.
Open-Source Intelligence (OSINT) is the act of collecting information from publicly available sources.
Armed with this information, attackers can launch very convincing spear phishing attacks during the delivery phase.
somewhere. Similarly, if the attack involves phishing emails, then the attacker will need to craft the email bodies.
This phase may use information gathered during the reconnaissance phase to develop attacks specific to a target.
Automation allows for quickly provisioning infrastructure. This significantly reduces the time between the reconnaissance phase, and the actual strike.
in a matter of minutes using common automation tools such as Puppet, Chef, or Ansible.
This delivery can take the form of a phishing email, a watering hole attack, a supply chain attack, or even a dropped USB drive.
, or even Pinterest and Instagram to deliver their payloads.
Users are much more likely to trust a link directing them to a known site with a valid certificate.
During the exploit phase the attacker will exploit any vulnerabilities found during the reconnaissance phase.
install their malicious payload. The installation phase usually
for financial or other gain, the malicious payload must send this information back to the attackers.
The callback phase is how attackers control their new asset. This connection can
extract information, add the compromised host to a botnet, or attack other systems on the network.
By using popular public services, malicious traffic is more likely to bypass firewalls, and has the added benefit of blending in with regular traffic.
public services also provides resilience for the attackers infrastructure. Continuing with the Twitter example, all malicious traffic gets routed through Twitter’s servers. This makes investigations much more difficult as the traffic cannot
This may involve extracting valuable information, defacing websites, launching a denial-of-service attack, or moving laterally throughout the organizations network.
https://www.lockheedmartin.com/us/what-we-do/aerospace-defense/cyber/cyber-kill-chain.html
http://lockheedmartin.com/content/dam/lockheed/data/corporate/documents/Seven_Ways_to_Apply_the_Cyber_Kill_Chain_with_a_Threat_Intelligence_Platform.PDF
Cyberspace example: Reconfiguring a network in response to network intrusion threat. The tactic is the network protection re-configuration
Malicious activity/Counter Base Infrastructure Threats/CAC High Agility, etc..
- Threat Hunting with MITRE’s ATT&CK Framework: Part 1
The framework consists of 11 tactics, from initial access, execution, all the way through command and control and data exfiltration
Each phase of this attack lifecycle consists of a multitude of techniques that have been observed in the wild being used by various threat actor groups when compromising an organization’s network.
When was the ATT&CK Framework Created?
This framework can be extremely useful for gauging an environment’s level of visibility against targeted attacks with the tools that have been deployed across your endpoints and perimeter.
That being said, I don’t personally think you need to check off all 282 - at the time of this writing - checkboxes to be uber secure from the bad guys.
My approach to this framework has always been to focus more on the higher fidelity indicators while tagging the lower fidelity ones for threat hunting purposes.
Let’s start off with the Execution phase. Once an adversary has easily tricked Bob in Accounting - who by the way clicks on everything that arrives to his inbox - there will be a series of activities that will execute on Bob’s machine unknowingly in the background. One of those items may be the execution of an ATT&CK technique, PowerShell, which is a built-in Windows tool that is commonly leveraged by malware to install itself.
Running the functions DownloadFile, DownloadString, Base64ToString, Invoke-Shellcode, EncodedCommand, etc. are all naughty commands that should signal our IR Spidey Senses that an intruder has come a-knocking. Therefore, creating a simple signature that looks like something below will yield a high-fidelity threat alert for your Level 1 crew to immediately investigate.
Process = Powershell.exe & Command_Line contains “DownloadFile, DownloadString, Base64ToString, Invoke-Shellcode, EncodedCommand”
https://digitalguardian.com/blog/threat-hunting-mitres-attck-framework-part-1
- Threat Hunting with MITRE’s ATT&CK Framework Part 2 – Advanced Use Cases
I’d like to walk through three hunting use cases: Command & Control, Lateral Movement, and Data Exfiltration.
Let’s start off with selecting a couple of techniques from the ATT&CK Framework to hunt for Command and Control activity; aka malicious network traffic. Our top hitting alarm, ATP – Outbound TCP Connections, will show all outbound connections made by process.
Hunting for Lateral Movement
One of the most effective methods I’ve used for years is baselining PsExec activity. PsExec is a remote administration tool and has been observed across many threat actor groups as being one of the tools of choice for conducting lateral movement. Why? Because it’s a legitimate, Microsoft signed tool which allows them to blend in.
For this analysis, we’re going to look at a few key fields. The process path, process name, and command line being executed.
Defense Evasion techniques such as Masquerading.
Process Path: The path by which a program runs can be quite relevant when it comes to threat hunting. Executing tools out of their standard locations isn’t cool so the bad guys create their own little hidden folders on the endpoint to be slick and remain clandestine. Aggregating on the process path may yield a few suspicious directories that require some additional investigation. Below, we see psexec.exe running from a c:\temp\32bit, c:\programdata, and a c:\misc.
Process Name: The process name may, or may not indicate suspicious behavior but threat actors love to rename their toolsets and are super lazy on the command line. They love single character and two character binary names since it’s less to type. In the picture below we see a p.exe. Yikes… in this case, someone is covertly running the psexec tool or Masquerading.
Command Line: Looking at the commands that are being executed by PsExec can be insightful as well.
When confirming whether or not Lateral Movement is malicious, it’s good to conduct a ‘look around’ for everything that is executing around that time. Once a threat is on a box, they’ll engage in several additional techniques outlined within MITRE’s framework.
Hunting for Data Exfiltration
This hunting technique will come down to the types of tools and visibility you have in your own environment as it relates to outbound data egress,
Above you’ll see a chart of the processes that are sending data outbound aggregated by total size.
The file extensions associated with this activity includes ‘rar’ which I always feel is pretty threat-actor-esque and lines up with one of our MITRE ATT&CK stages for Data Compressed.
Not all compressed data leaving the network is bad but tagging this activity with rules will help speed up the hunt process to zero in on possible exfiltration.
Looking at the forensic details for this event, we see the source file is named 123.rar and it’s going directly to an IP address (forgive the redaction) over FTP.
Data exfiltration hunting isn’t always going to be this effortless, but developing signatures to detect various types of events such as the one above will make your hunt a bit easier, especially when you’re able to pair this information with source process name/directory/command line etc.
I remember back in the day when only being able to hunt through web proxy logs.
A couple other tips to look for when it comes to data exfiltration include:
Destination Domains being dynamic DNS Sites
Source file extensions equal .rar, .7z, .zip, .tar, .cab, etc. (be careful here because this is easy to obfuscate with an extension name change)
Protocols such as FTP, SFTP, SCP, SSH
Tor traffic/domains
This concludes our second installment of Threat Hunting with MITRE’S ATT&CK framework.
https://digitalguardian.com/blog/threat-hunting-mitres-attck-framework-part-2-%E2%80%93-advanced-use-cases
- Threat Hunting with MITRE’s ATT&CK Framework Part 3 – High Fidelity
describes how to best leverage MITRE's Attack Framework for threat hunting.
These particular techniques I’d consider to be higher fidelity and should ultimately be constructed into alarms for immediate response.
Looking at the obfuscated command that generated the alarm… clearly not legitimate. So how do we proactively detect, and even better yet prevent this in the future? Creating signatures for this particular technique is highly advised and will yield almost zero false positive
https://digitalguardian.com/blog/threat-hunting-mitre-attck-framework-part-3-high-fidelity
- MITRE ATT&CK™ APT3 Assessment
MITRE’s ATT&CK for Enterprise, produced by the Cyber Security division of MITRE, is an adversarial behavior model for possible attacker actions. The ATT&CK matrix used is a visualization tool in the form of a large table, intended to help provide a framework to talk about attacks in a unified way. This is coupled to detailed descriptions of different tactics and techniques and how they differ from attacker to attacker.
When you participate in the assessment, MITRE is the red team simulating the techniques, used by APT3 in this case, and we as McAfee are the blue team using our products to detect their actions and report them. When the red team attacks us with a variant of a technique, as a blue team, we need to prove we detected it.
While MITRE’s evaluation focused on MVISION EDR’s detection capabilities, there are several aspects that defenders need to consider in order to properly triage, scope, contain and close an incident. During the APT3 attack we generated 200+ alerts and telemetry datapoints which were the core of MITRE’s evaluation. Yet we don’t expect analysts to review them individually. In MVISION EDR those 200+ data points got clustered into 14 threats which added context to paint a more complete picture of what happened in order to speed triage.
Although it was not exercised by MITRE, the next step for the analyst would have been to use MVISION EDR’s real time search to further scope the affected devices and take containment actions (e.g. quarantine, kill processes, etc).
https://securingtomorrow.mcafee.com/business/endpoint-security/mitre-attck-apt3-assessment/
- Apply MITRE’s ‘ATT&CK’ Model to Check Your Defenses
Once you have your list and risk classification ready, you must next study the tactics, techniques, and procedures used by these adversaries. For mapping their techniques and associated campaigns, we use the MITRE Adversarial Tactics, Techniques, and Common Knowledge model (ATT&CK). The matrix covers hundreds of techniques, and can be applied for different purposes. In this case, we will focus on the risk versus mapping the defensive architecture.
With MITRE’s Navigator tool you can select an actor or malware family. After making the selection, the boxes in the matrix show which techniques the actor or malware has used.
From these techniques we can learn how our environments protect against these techniques and where we have gaps. The goal is not to create coverage or signatures for each technique; the matrix helps organizations understand how attackers behave.
Having more visibility into their methods leads us to the right responses, and helps us contain and eradicate attacks in a coordinated way. By comparing the multiple actors from your initial risk assessment, you can build the matrix from the perspective of high/medium/low risk and map it against your defenses.
it is still good to ask yourself “What if we were a target?” Would your environment create enough visibility to detect and deal with these techniques?
When we looked at the first quarter, we noticed that the three techniques were the most popular in the category of Privilege Escalation:
Exploitation of vulnerability
Process injection
Valid accounts
To determine your coverage and detection capacity, you should ask if the exploits used completely new vulnerabilities (no patches available) or if they had existed for a while. Would your environment have the right patches installed or are you missing them and have to take action?
There are many ways to apply it for red teaming, threat hunting, and other tasks.
https://securingtomorrow.mcafee.com/other-blogs/mcafee-labs/apply-mitres-attck-model-to-check-your-defenses/
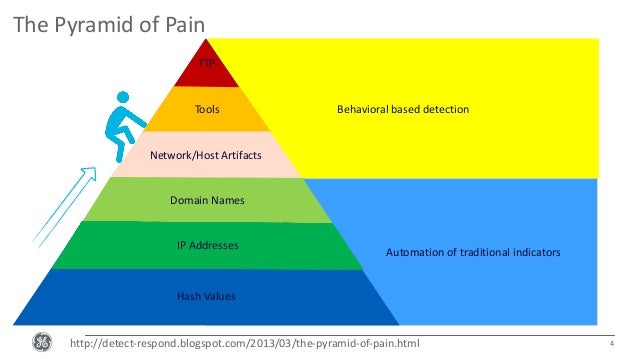
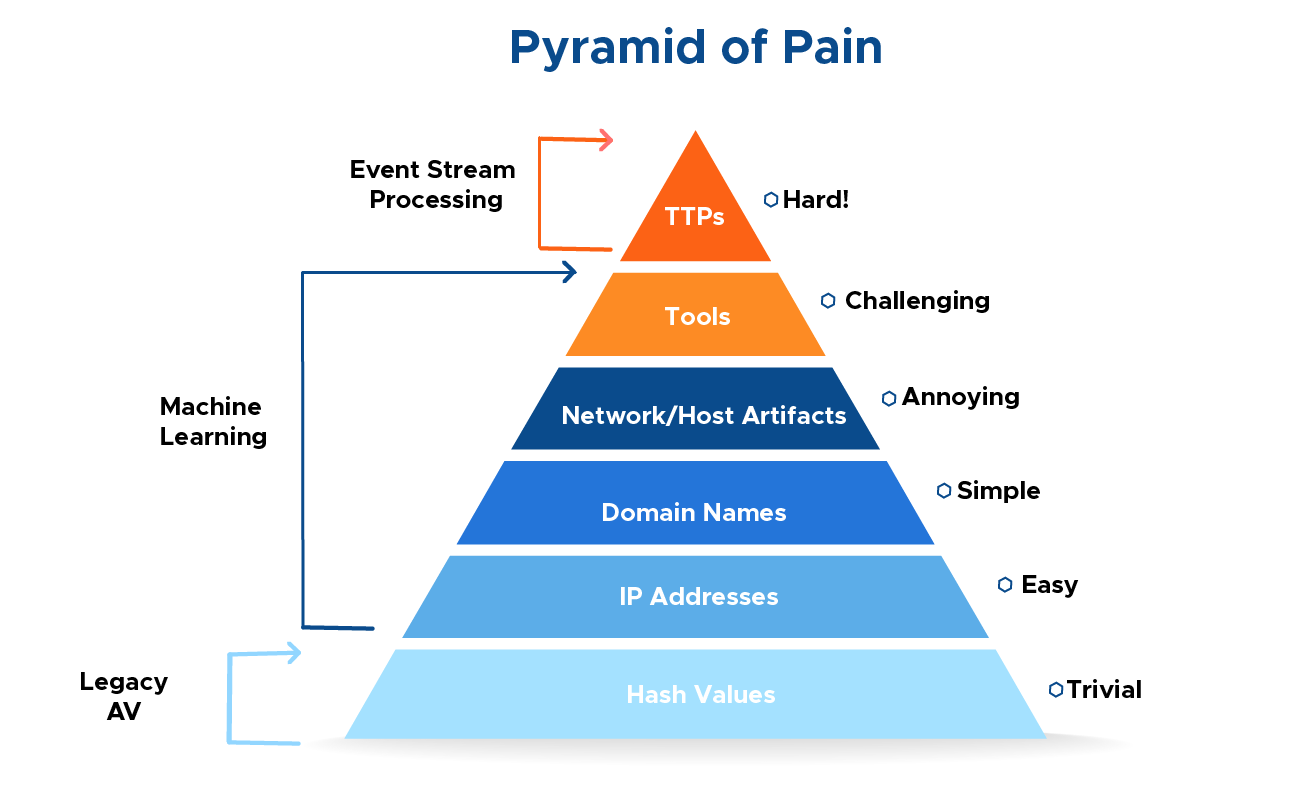
To illustrate this concept, I have created what I like to call the Pyramid of Pain. This simple diagram shows the relationship between the types of indicators you might use to detect an adversary's activities and how much pain it will cause them when you are able to deny those indicators to them
Types of Indicators
Hash Values: SHA1, MD5 or other similar hashes that correspond to specific suspicious or malicious files. Often used to provide unique references to specific samples of malware or to files involved in an intrusion.
IP Addresses:
Domain Names:
Network Artifacts: Observables caused by adversary activities on your network. Technically speaking, every byte that flows over your network as a result of the adversary's interaction could be an artifact, but in practice this really means those pieces of the activity that might tend to distinguish malicious activity from that of legitimate users. Typical examples might be URI patterns, C2 information embedded in network protocols, distinctive HTTP User-Agent or SMTP Mailer values, etc.
Host Artifacts: Observables caused by adversary activities on one or more of your hosts. Again, we focus on things that would tend to distinguish malicious activities from legitimate ones. They could be registry keys or values known to be created by specific pieces of malware, files or directories dropped in certain places or using certain names, names or descriptions or malicious services or almost anything else that's distinctive.
Tools: Software used by the adversary to accomplish their mission. Mostly this will be things they bring with them, rather than software or commands that may already be installed on the computer. This would include utilities designed to create malicious documents for spearphishing, backdoors used to establish C2 or password crackers or other host-based utilities they may want to use post-compromise.
Tactics, Techniques and Procedures (TTPs): How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between. "Spearphishing" is a common TTP for establishing a presence in the network. "Spearphishing with a trojaned PDF file" or "... with a link to a malicious .SCR file disguised as a ZIP" would be more specific versions. "Dumping cached authentication credentials and reusing them in Pass-the-Hash attacks" would be a TTP. Notice we're not talking about specific tools here, as there are any number of ways of weaponizing a PDF or implementing Pass-the-Hash.
The Pyramid Explained
Both the width and the color are very important in understanding the value of these types of indicators.
Hash Values
Most hash algorithms compute a message digest of the entire input and output a fixed length hash that is unique to the given input. In other words, if the contents of two files varies even by a single bit, the resultant hash values of the two files are entirely different. SHA1 and MD5 are the two most common examples of this type of hash.
You may also encounter so-called fuzzy hashes, which attempt to solve this problem by computing hash values that take into account similarities in the input. In other words, two files with only minor or moderate differences would have fuzzy hash values that are substantially similar, allowing an investigator to note a possible relationship between them.
http://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html



- This library of tests will walk you through each of the phases of MITRE’s ATT&CK framework allowing you to truly gauge your visibility and readiness for the inevitable
https://github.com/redcanaryco/atomic-red-team
- Categorizing and Enriching Security Events in an ELK with the Help of Sysmon and ATT&CK
https://cyberwardog.blogspot.com/
- The Playbook viewer is a system for parsing STIX2 content that contains an Adversary Playbook
https://pan-unit42.github.io/playbook_viewer/?pb=sofacy
- MITRE evaluates cybersecurity products using an open methodology based on our ATT&CK™ framework.
Instead, we show how each vendor approaches threat detection in the context of the ATT&CK matrix.
https://attackevals.mitre.org/
- Adversary Emulation Approach
While we aspire to test across the entirety of ATT&CK, the number of actions required to test all techniques and the many possible variations in implementation (i.e. procedures) makes testing across the entirety of ATT&CK impractical. Additionally, certain techniques are complex and are not implementable in a lab environment. Since we need a way to select a subset of techniques to define test criteria, as well as chain activity together, we choose to focus on techniques used by a known threat group, which we refer to as adversary emulation, for our evaluations.
To generate our emulation plans, we identify public threat intelligence reporting, map techniques in the reporting to ATT&CK, chain together the techniques, and then determine a way to replicate the behaviors.
When emulating an adversary, several factors differentiate the emulation from being a direct copy of the adversary’s actions or a full replay of an actual intrusion. First, the red team tasked with emulating the adversary generally does not use the actual adversary tools; instead, they attempt to emulate the techniques as closely as possible using publicly-available tools. To get “as close as possible,” the emulators analyze threat intel reports and malware reverse engineering reports to understand what the adversary (or specific pieces of the adversary’s malware) did at the lowest level. The emulators then map those observed functions to the closest analogous function of the publicly available tool, which may cause slight differences in functionality or implementation method.
Another limitation of adversary emulation is that emulators rely on publicly-available threat reporting. Not all adversary activity is covered in public reporting, so emulations will only cover a portion of all adversary activity. For example, a new Windows patch may prevent a specific User Account Control (UAC) bypass technique. When faced with such a situation, the emulators may use another or newer UAC bypass technique that is available. We recognize that when emulating an adversary, we will only be able to mimic their historical behavior.
To perform the evaluation using adversary emulation, we chain techniques together in a logical flow.We recognize that adversaries often do not execute atomic actions, so this is another limitation to the emulation of real adversary behavior.
Another significant difference between our evaluations and the “real world” is that we do not have any “user noise” in our lab environment.Therefore, we encourage users of our results to perform additional testing in their own environments, which will have the noise necessary to determine if detections are valuable in your environment.
https://attackevals.mitre.org/methodology/
CALDERA is an automated adversary emulation system, built on the MITRE ATT&CK™ framework.
CALDERA works by attaching abilities to an adversary and running the adversary in an operation. Full documentation for this system can be found in the wiki.
https://github.com/mitre/caldera
The evaluation is broken into four phases:
Setup: Vendors install their product(s)/tool(s) in a Microsoft Azure cyber range we provide.
Execution: During a joint evaluation session, our red team executes an adversary emulation.
Processing and Feedback: We process the results, assign detection categories, and summarize detections into short notesPublication: We review all vendor feedback, but we are not obligated to incorporate it. When reviewing the vendor’s feedback, we consider how we apply detection categories across the entirety of the vendor’s evaluation as well as the other vendors’ results to ensure that we are making consistent and fair decisions. We release the evaluation methodology and the evaluation results onto the ATT&CK Evaluations website.
https://attackevals.mitre.org/methodology/evaluation-process.html