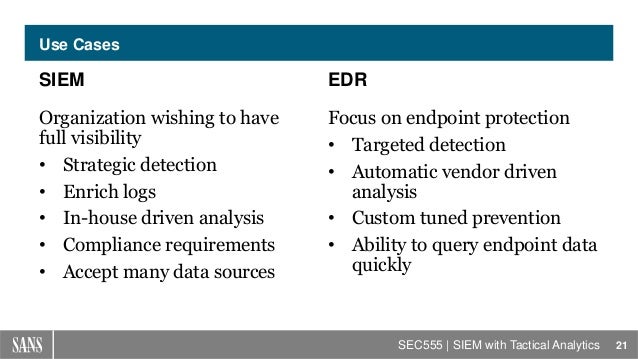
- The situation, task, action, result (STAR) format is a technique used by interviewers to gather all the relevant information about a specific capability that the job requires
Situation: The interviewer wants you to present a recent challenge and situation in which you found yourself.
Task: What were you required to achieve? The interviewer will
be looking to see what you were trying to achieve from the situation
Action: What did you do? The interviewer will
be looking for information on what you did, why you did it and what the alternatives were.
Results: What was the outcome of your actions? What did you achieve through your actions and did you meet your objectives? What did you learn from this experience and have you used this learning since?
https://en.wikipedia.org/wiki/Situation,_task,_action,_result
- STAR stands for Situation, Task, Action, Result. Using this strategy is particularly helpful in response to competency-focused questions, which typically start out with phrases such as, "Describe a time when..." and "Share an example of a situation where...."
The STAR interview response technique is a way of answering behavioral interview questions.
Behavioral interview questions are questions about how you have behaved in the past.
Specifically, they are about how you have handled certain work situations.
For example, employers might
be looking for proof of problem-solving skills, analytical ability, creativity, perseverance through failure, writing skills, presentation skills, teamwork orientation, persuasive skills, quantitative skills, or accuracy.
Examples of behavioral interview questions include
the following:
Tell me about an occasion when you had to complete a task under a tight deadline.
Have you ever gone above and beyond the call of duty?
What do you do when a team member refuses to complete his or her quota of the work?
However, job seekers can also use the STAR interview method to prepare for behavioral interview questions.
STAR is an acronym for four key concepts. Each concept is a step the job candidate can
utilize to answer a behavioral interview question.
Situation: Describe the context within which you performed a job or faced a challenge at work. For example, perhaps you were working on a group project, or you had a conflict with a coworker.
This situation can be drawn from a work experience, a volunteer position, or any other relevant event.
Task: Next, describe your responsibility in that situation.
Perhaps you had to help your group complete a project within a tight deadline, resolve a conflict with a coworker, or hit a sales target.
Action: You then describe how you completed the task or endeavored to meet the challenge. Focus on what you did, rather than what your team, boss, or coworker did. (Tip: Instead of saying, "We did
xyx," say "I did
xyz.")
Result: Finally, explain the outcomes or results generated by the action taken. It may be helpful to emphasize what you accomplished, or what you learned.
How to Prepare for an Interview Using STAR
Since you won’t know in advance what interviewing
techniques your interviewer will
be using, you’ll
benefit from preparing several scenarios from the jobs you’ve held.
First, make a list of the skills and/or experiences that
are required for the job.
It may help you
to look at the job listing and similar job listings for indications of the required or preferred skills/qualities and match your qualifications to those listed in the posting.
Then, consider specific examples of occasions when you displayed those skills.
For each example, name the situation, task, action, and result.
Examples of Interview Questions and Answers Using STAR
Example Question 1: Tell me about a time you had to complete a task within a tight deadline. Describe the
situation, and explain how you handled it.
Example Question 2: What do you do when a team member refuses to complete his or her quota of the work?
Example Question 3: Tell me about a time you showed initiative on the job.
https://www.thebalancecareers.com/what-is-the-star-interview-response-technique-2061629
- What is a Behavioral Job Interview?
Behavioral based interviewing is interviewing based on discovering how the interviewee acted in specific employment-related situations
The logic is that how you behaved in the past will predict how you will behave
in the future, i.e., past performance predicts future performance.
Traditional Interviews
In a traditional interview,
you will be asked a series of questions which typically have straightforward answers like "What are your strengths and weaknesses?" or "What major challenges and problems did you face? How did you handle them?" or "Describe a typical work week."
In a behavioral interview, an employer has decided
what skills are needed in the person they hire and will ask questions to find out if the candidate has those skills.
Instead of asking how you would behave, they will ask how you
did behave.
The interviewer will want to know how you handled a situation, instead of what you might do
in the future.
Questions Asked
Behavioral interview questions will be more pointed, more probing and more specific than traditional interview questions:
Finally, review the job description, if you have it, or the job posting or ad. You may
be able to get a sense of what skills and behavioral characteristics the employer are seeking from reading the job description and position requirements.
It's important to keep in mind that there are no right or wrong answers. The interviewer is
simply trying to understand how you behaved in a
given situation. How you respond will determine if there is a fit between your skills and the position the company is seeking to fill.
https://www.thebalancecareers.com/behavioral-job-interviews-2058575
- The interviewer will want examples of what happened in a particularly challenging circumstance, what you did, and how you achieved a positive outcome.
The Best Behavioral Interviewing Techniques and Strategies
Review what a behavioral interview is and what companies are looking for during a behavioral interview.
Use the STAR interview technique to prepare examples to share during an interview.
Review sample behavioral interview questions.
Research the Job and Company
Techniques
(S) A specific situation
(T) The tasks that needed to
be done
(A) The action you took
(R) The results, i.e., what happened
It is the STAR interview response technique, and it's an excellent way to prepare.
Do keep in mind that there are no right or wrong answers to behavioral interview questions. The interviewer's goal is to understand how you behaved in a
given situation. How you respond will determine if there is a match between your skills and the position the company is seeking to fill.
https://www.thebalancecareers.com/behavioral-interview-techniques-and-strategies-2059621
- Behavioral Based Job Interview Questions
In a behavioral job interview, the company asks questions about your past work experiences
in order to find out if you have the skills needed for the job. Behavioral interview questions focus on how you handled various work situations in the past. Your response will reveal your skills, abilities, and personality.
(S) Situation. Describe the situation in which the event took place.
(T) Task. Describe the task
you were asked to complete. If there was a particular problem or issue you were trying to solve, describe that here.
(A) Action. Explain what action you took to complete the task or solve the problem.
(R) Results. Explain the result of your actions. For example, if your actions resulted in completing a task, resolving a conflict, improving your company’s sales record, etc., explain this. Try to focus on how your actions resulted in a success for the company.
Follow the STAR Technique. Be sure to answer
any questions using the STAR technique described above. By completing each of the four steps, you will provide a thorough answer without rambling or getting off topic.
Be Positive. Often, behavioral interview questions require you to focus on a problem or a failure at work. Describe the problem or issue you faced, but don’t focus too much on the negative. Quickly shift to describing how you solved the problem and the positive results.
Give an example of a goal you didn't meet and how you handled it.
Have you been
in a situation where you didn't have enough work to do?
Have you ever made a mistake? How did you handle it?
Have you ever dealt with company policy you weren't in agreement with? How?
When you worked on multiple projects how did you prioritize?
https://www.thebalancecareers.com/behavioral-job-interview-questions-2059620
- Competency-Based Interview Questions
Competency-based interview questions require interviewees to give specific examples of times in which they
demonstrated particular skills or attitudes.
Often, these types of questions begin with the phrases "Describe a time when..." or "Give me an example of a situation where..."
Generally, these questions require interviewees to describe a problem or situation, the actions they took to handle it, and the end results.
They allow the employer
to quickly evaluate a candidate's
mindset, and gauge how a candidate handles certain situations.
an interviewer for an upper management job may ask questions about leadership, independence, and creativity.
How to Prepare for Competency-Based Interview Questions
make a list of skills and attitudes
that you think are important for the job for which you are interviewing.
Check the job listing for examples of required abilities.
Next, list situations in which you have
demonstrated each of these competencies.
For each situation, write
down the situation or problem, the actions you took to handle the problem, and the ultimate results
STAR stands for situation, task, action, result. Using this technique will help you give a brief, coherent, and structured response to interview questions.
Once you have prepared a list of situations, review it. By thinking of examples before the interview, you will
be able to answer questions quickly and concisely.
Be Concise
It is easy to wander when answering a competency-based interview question, particularly if you do not have a specific situation or problem in mind.
Do Not Place Blame
If you are describing a particular problem or difficult situation (for example, a time when you had to work with a difficult boss), it may feel natural to attack or place blame on another person. However, these questions are about you, not about anyone else. Focus on what you did to manage the situation; do not dwell on other peoples’ issues or failures.
Examples of Competency-Based Interview Questions
Adaptability
Tell us about the biggest change you have had to deal with in your previous employment. How did you handle it?
Decisiveness
Tell us about a decision you made that you knew would be unpopular with certain people. How did you handle the decision-making process? How did you handle other peoples’ negative reactions?
Integrity
Tell us about a time when someone asked you to do something you objected to. How did you handle the situation?
Resilience
How do you deal with stress?
Describe a time in which you received negative feedback from an employer, colleague, or client. How did you manage this feedback? What was the outcome?
https://www.thebalancecareers.com/competency-based-interview-questions-2061195
- This method is slightly more involved than the STAR method and some people may prefer using it, particularly if they have a lot of management experience from which to draw examples.
The SOARA method:
1) Identify a Situation that enables you to illustrate how you behaved in that recent event, giving particular emphasis
to describing the required competency the question
is aimed at assessing.
2) State the
Objective you wanted to attain by the conclusion of this situation or event.
3) Describe what Action you took to achieve your
objective. Your actions and behaviors must reflect those of someone who is performing the role. This is most easily shown in your reasoning for doing what you did and how you assessed alternatives.
4) Make sure you clearly state the Results of your decisions and actions
as well as how you attained your
objective.
5) Conclude your answer with a summary of what you learnt from this situation and how this has influenced you since.
This is referred to as the Aftermath
To make it easier to identify the best events and challenges Helena has quickly created a 'situation mind map' from her work experiences and personal achievements. This visual representation of her resume will
be copied and completed for each competency required in the role. In this example it is for 'strategic thinking.'
This mind map shows the five projects that enable her to illustrate strategic thinking. The table below shows how she uses SOARA to prepare an answer to the selected question.
If you
are going to succeed in a competency-based
interview then your answers must:
• Be specific in their description and detail
• Be concise and highlight your achievements clearly
• Show
your actions were structured
• Convey the maximum achievement in the minimum time
• Give a strong and positive impression at the end of your answer
• Show what you learnt from the situation.
Key Points
The SOARA method is slightly more involved than the STAR method.
SOARA stands for: Situation,
Objective, Action, Results, and Aftermath.
The process is
similar to that of the STAR method explained earlier
in that it is time consuming and takes a lot of work.
Both methods provide you with the best examples of competency-specific behaviors
that you can use in all of your interviews.
http://www.free-management-ebooks.com/faqcr/competency-04.htm






:max_bytes(150000):strip_icc()/behavioral-job-interview-questions-2061629_round2-5b4f594846e0fb005b443466.png)

