- IPsec
Internet Protocol Security (IPsec) is a protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session
Some other Internet security systems in widespread use, such as Secure Sockets Layer (SSL), Transport Layer Security (TLS) and Secure Shell (SSH), operate in the upper layers of the TCP/IP model. In the past, the use of TLS/SSL had to
http://en.wikipedia.org/wiki/IPsec
- 85) What
do mean by tunnel mode?
This is a mode of data exchange wherein two communicating computers do not use IPSec themselves. Instead, the gateway that is connecting their LANs to the transit network creates a virtual tunnel that uses the IPSec protocol to secure all communication that passes through it.
IPsec consist of several protocols
ISAKMP
IKE
ESP - protocol 50
AH - protocol 51
IPsec Modes
Transport Mode
Tunnel Mode
Encryption Algols
DES
3DES
AES
RSA
Hashing Algols
MD5
SHA-1
IKE Phases
Data integrity - HMAC
Data Confidentiality - Encryption
Data Origin Authentication - SA peer
anti-replay - sequence numbers
HMAC
Diffie-Hellman
http://networkqna.com/ipsec/
- Q1 – In which IPSEC Phase is the keys used for data encryption derived.
Q2 – In IPSEC, If ESP provides both encryption and authentication, why is AH required.
Q3 – Explain two methods by which two IPSEC routers can authenticate with each other.
Q4 – Which UDP ports should be open on a firewall to allow traffic from a L2TP/IPSEC based VPN clients to a PPTP VPN server on the inside
Q5 -Which IP protocol does AH and ESP headers use in IPSEC
Q6 – Which type of VPN would you use if data has to be encrypted at the network layer
Q7 – What is the use of configuring ACL in IPSEC configuration on a Cisco router
Q8 – If a packet sniffer is used on the VPN tunnel can the inner IP header be viewed
Q9 – Are the pre-shared keys used between the routers used for data encryption between systems at the different sites.
Q10
http://tcpipguru.com/ipsec-interview-questions/
- IPSEC - The Internet Protocol Security is a set of protocols that provides security features to IP; like authentication, encryption and confidentiality.
L2TP -Layer Two Tunneling Protocol is a tunneling protocol (VPN) used to transport in L2 traffic over an IP Network ( Internet)
L2TP as follows from the name, is a layer 2 tunneling protocol. So, it can tunnel Layer 2 frames over IPSEC.
https://learningnetwork.cisco.com/s/question/0D53i00000Kt2n1/ipsec-vs-l2tp-over-ipsec
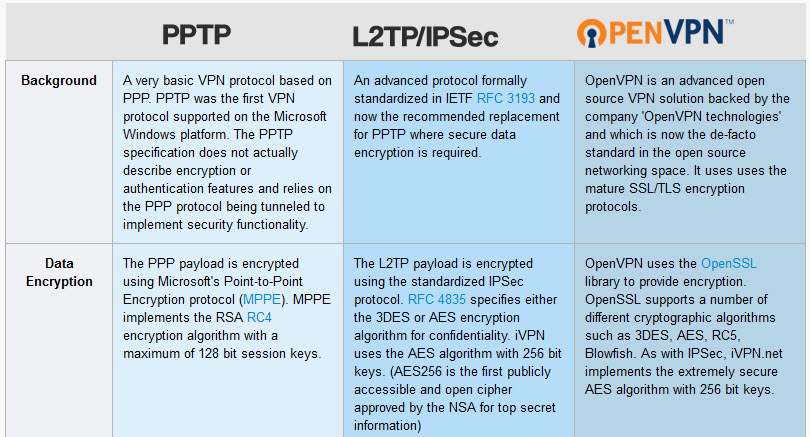
PPTP or Point-to-Point Tunneling Protocol is an outdated method for implementing VPNs. It is developed by Microsoft and the easiest protocol to configure. PPTP VPN has low overhead and that makes it faster than other VPN protocols.
L2TP or Layer 2 Tunneling Protocol (L2TP) is the result of a partnership between Cisco and Microsoft.
It was created to provide a more secure VPN protocol than PPTP. L2TP is a tunneling protocol like PPTP that allows users to access the common network remotely.
https://www.purevpn.com/blog/difference-between-pptp-and-l2tp-protocols/
IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN.
https://en.wikipedia.org/wiki/IEEE_802.1X
No comments:
Post a Comment