- Bard
draw network topology for this output: $ get router info routing-table all
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
V - BGP VPNv4
* - candidate default
Routing table for VRF=0
S* 0.0.0.0/0 [10/0] via 172.30.72.254, port36, [1/0]
C 10.10.1.0/24 is directly connected, FortiSASE
C 10.10.1.1/32 is directly connected, FortiSASE
C 10.88.2.0/24 is directly connected, DCFW
C 10.88.11.0/24 is directly connected, P22
C 10.88.12.0/24 is directly connected, ISFW-HA
C 10.88.23.0/24 is directly connected, FSA-DMZ
C 10.88.41.0/24 is directly connected, FSA-DMZ2
C 10.88.51.0/24 is directly connected, FWLC
C 10.88.52.0/24 is directly connected, WLC-Teachers
C 10.88.53.0/24 is directly connected, WLC-Students
C 10.88.54.0/24 is directly connected, WLC-Staff
S 10.88.101.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.102.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.103.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.110.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.120.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.130.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.210.0/24 [10/0] via 10.88.2.21, DCFW, [1/0]
S 10.89.0.0/16 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
C 10.89.20.0/24 is directly connected, port16
C 10.100.1.0/24 is directly connected, FITNUC
C 10.254.252.0/23 is directly connected, snf.FortiLink
C 10.254.254.0/24 is directly connected, qtn.FortiLink
C 10.255.11.0/24 is directly connected, nac_segment
C 169.254.1.0/24 is directly connected, FortiLink
C 169.254.11.0/24 is directly connected, onboarding
C 172.30.72.0/24 is directly connected, port36
C 192.168.20.0/24 is directly connected, port4
Here is a network topology for the output of the get router info routing-table all command:
+--------------+
| FortiSASE |
+--------------+
|
|
+-----------+
| 10.88.12.99 |
+-----------+
|
|
+--------------+
| DCFW |
+--------------+
|
|
+--------------+
| ISFW-HA |
+--------------+
|
|
+--------------+
| FSA-DMZ |
+--------------+
|
|
+--------------+
| FSA-DMZ2 |
+--------------+
|
|
+--------------+
| FWLC |
+--------------+
|
|
+--------------+
| WLC-Teachers |
+--------------+
|
|
+--------------+
| WLC-Students |
+--------------+
|
|
+--------------+
| WLC-Staff |
+--------------+
|
|
+--------------------+
| FortiLink |
+--------------------+
|
|
+--------------------+
| FITNUC |
+--------------------+
|
|
+--------------------+
| onboarding |
+--------------------+
|
|
+--------------------+
| nac_segment |
+--------------------+
Legend:
Solid lines: Directly connected subnets
Dashed lines: Remote subnets
Notes:
The get router info routing-table all command displays the routing table for all VRFs. The output in the question shows the routing table for VRF=0.
The S code in the routing table indicates a static route.
The C code in the routing table indicates a directly connected subnet.
The 10.88.12.99 IP address is the IP address of the ISFW-HA device.
The 172.30.72.254 IP address is the IP address of the Internet gateway.
Summary:
The network topology shows a FortiGate firewall (FortiSASE) connected to a DCFW, ISFW-HA, and several other devices. The FortiSASE device is also connected to the Internet. The ISFW-HA device acts as a default gateway for the other devices on the network.
- ChatGPT
draw network topology for this output: $ get router info routing-table all
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
V - BGP VPNv4
* - candidate default
Routing table for VRF=0
S* 0.0.0.0/0 [10/0] via 172.30.72.254, port36, [1/0]
C 10.10.1.0/24 is directly connected, FortiSASE
C 10.10.1.1/32 is directly connected, FortiSASE
C 10.88.2.0/24 is directly connected, DCFW
C 10.88.11.0/24 is directly connected, P22
C 10.88.12.0/24 is directly connected, ISFW-HA
C 10.88.23.0/24 is directly connected, FSA-DMZ
C 10.88.41.0/24 is directly connected, FSA-DMZ2
C 10.88.51.0/24 is directly connected, FWLC
C 10.88.52.0/24 is directly connected, WLC-Teachers
C 10.88.53.0/24 is directly connected, WLC-Students
C 10.88.54.0/24 is directly connected, WLC-Staff
S 10.88.101.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.102.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.103.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.110.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.120.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.130.0/24 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
S 10.88.210.0/24 [10/0] via 10.88.2.21, DCFW, [1/0]
S 10.89.0.0/16 [10/0] via 10.88.12.99, ISFW-HA, [1/0]
C 10.89.20.0/24 is directly connected, port16
C 10.100.1.0/24 is directly connected, FITNUC
C 10.254.252.0/23 is directly connected, snf.FortiLink
C 10.254.254.0/24 is directly connected, qtn.FortiLink
C 10.255.11.0/24 is directly connected, nac_segment
C 169.254.1.0/24 is directly connected, FortiLink
C 169.254.11.0/24 is directly connected, onboarding
C 172.30.72.0/24 is directly connected, port36
C 192.168.20.0/24 is directly connected, port4
I can describe the network topology based on the provided routing table output. However, since I can't draw diagrams in this text-based format, I'll describe the relationships between the networks and devices in a textual format.
Here's a textual representation of the network topology:
[FortiSASE]
/ | \
[10.10.1.0/24] [10.10.1.1/32] [ISFW-HA]
|
[DCF] [P22] [FSA-DMZ] ... [Other Networks]
| | | \
[10.88.2.0/24] ... [10.88.23.0/24]
[FWLC]
|
[10.88.51.0/24] [10.88.52.0/24] [10.88.53.0/24] [10.88.54.0/24]
[ISFW-HA]
/ | \
[10.88.101.0/24] ... [Other Networks]
[FITNUC]
[10.100.1.0/24]
[snf.FortiLink] [qtn.FortiLink] [nac_segment] [Other Networks]
[10.254.252.0/23] [10.254.254.0/24] [10.255.11.0/24]
[FortiLink] [onboarding] [Other Networks]
[169.254.1.0/24] [169.254.11.0/24]
[port36]
[172.30.72.0/24]
[port4]
[192.168.20.0/24]
- Simply put, ping sends an "are you there?" message to a remote host. If the host is, in fact, there, ping returns a "yup, I'm here" message. It does this using a protocol known as ICMP, or Internet Control Message Protocol. ICMP was designed to be an error reporting protocol and has a wide variety of uses that we won't go into here.
Ping uses two ICMP message types: type 8 (Echo Request) and type 0 (Echo Reply). When you issue a ping command, the source sends an ICMP Echo Request to the destination. If the destination is available and is allowed to respond, then it replies with an ICMP Echo Reply. Once the message returns to the source, the ping command displays a success message as well as the Round Trip Time (RTT). The RTT can be an indicator of the latency between the source and the destination
Traceroute
Traceroute is a finicky beast. This tool is meant to identify the path between a source and a destination point.
Think of traceroute as a string of ping commands. At each step along the path, traceroute identifies the hop's IP as well as the latency to that hop.
Traceroute uses UDP or ICMP, depending on the OS.
On a typical *nix system it uses UDP and sends traffic to port 33434 by default.
On a Windows system, traceroute uses ICMP.
Traceroute displays the ICMP message's source address as the name of the hop and moves on to the next hop. When the source address finally matches the destination address, traceroute knows that it has reached the destination.
As with ping, the RTT values shown are not necessarily representative of the real RTT to a service such as HTTP or SSH. Traceroute, like ping, is considered to be lower priority compared to other traffic, so RTT values aren't guaranteed.
There is a second caveat with traceroute that you should be aware of: Traceroute shows you the path from the source to the destination, but this does not mean that the reverse is true. In fact, there is no current way to identify the path from the destination to the source without running a second traceroute from the destination
https://www.redhat.com/sysadmin/ping-traceroute-netstat
- The Ping Command
The ping command is a very common method for troubleshooting the accessibility of devices. It uses a series of Internet Control Message Protocol (ICMP) Echo messages to determine:
Whether a remote host is active or inactive.
The round-trip delay in communicating with the host.
Packet loss.
The ping command first sends an echo request packet to an address, then waits for a reply. The ping is successful only if:
the echo request gets to the destination, and
the destination is able to get an echo reply back to the source within a predetermined time called a timeout. The default value of this timeout is two seconds on Cisco routers.
Using the ping and traceroute commands, we obtain the round-trip time (RTT). This is the time required to send an echo packet, and get an answer back. This can be useful to have a rough idea of the delay on the link. However, these figures are not precise enough to be used for performance evaluation.
The Traceroute Command
The traceroute command is used to discover the routes that packets actually take when traveling to their destination. The device (for example, a router or a PC) sends out a sequence of User Datagram Protocol (UDP) datagrams to an invalid port address at the remote host.
Three datagrams are sent, each with a Time-To-Live (TTL) field value set to one. The TTL value of 1 causes the datagram to "timeout" as soon as it hits the first router in the path; this router then responds with an ICMP Time Exceeded Message (TEM) indicating that the datagram has expired.
Another three UDP messages are now sent, each with the TTL value set to 2, which causes the second router to return ICMP TEMs. This process continues until the packets actually reach the other destination. Since these datagrams are trying to access an invalid port at the destination host, ICMP Port Unreachable Messages are returned, indicating an unreachable port; this event signals the Traceroute program that it is finished.
The purpose behind this is to record the source of each ICMP Time Exceeded Message to provide a trace of the path the packet took to reach the destination
https://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-software-releases-121-mainline/12778-ping-traceroute.html
- The key point people usually miss is that each packet that’s sent out doesn’t go to a different place. Many people think
that
Then it sends a packet to the second hop, gets a time, and keeps going until it gets done.
That’s incorrect.
It
How does
For example, TTL = 1 should produce the message from the first router, TTL = 2 generates a message from the second router in the path, and so on..
- In the following example of the
tracert
The command:
C:\>
The output from the command:
Tracing route to 11.1.0.1 over a maximum of 30 hops
---------------------------------------------------
1 2 ms 3 ms 2 ms 157.54.48.1
2 75 ms 83 ms 88 ms 11.1.0.67
3 73 ms 79 ms 93 ms 11.1.0.1
Trace complete.
https://support.microsoft.com/en-us/kb/314868
Traceroute traceroute is broken
What is
How does
What’s an alternative to
So if the ICMP port is closed somewhere along its way to your destination server, what is your alternative? Well, instead of using ping, try a
https://community.spiceworks.com/networking/articles/2531-traceroute-request-timed-out-why-traceroute-is-broken
- How would
traceroute
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
- Q: Describe the working of
Traceroute
Small Time To Live (TTL) values are transmitted traceroute given the sender is sent Traceroute are used traceroute
https://mindmajix.com/cyber-security-interview-questions
- how does
traceroute
ICMP (Internet Control Message Protocol) is a companion to the IP protocol. It compensates the IP protocol in error reporting since IP protocol doesn’t have an error reporting method in place. ICMP only reports errors and expects higher layers of the OSI architecture model to handle and correct the errors.
ICMP has two types of messages
Destination Unreachable
Time exceeded
Source Quench
Parameter Problem
Redirection
- Network Troubleshooting using PING, TRACERT, IPCONFIG, NSLOOKUP COMMANDS
Understanding the Output
The first line represents your home router (assuming you’re behind a router), the next lines represent your ISP, and each line further down represents a router that’s further
The format of each line is as follows
Hop RTT1 RTT2 RTT3 Domain Name [IP Address]
Hop: Whenever a packet is passed this is referred
RTT1, RTT2, RTT3: This is the round-trip time that it takes for a packet to get to a hop and back to your computer (in milliseconds). This is often referred latency, Traceroute – indicate
Domain Name [IP Address]: The domain name, if available, can often help you see the location of a router. If this isn’t available, only the IP address of the router is displayed
https://www.howtogeek.com/134132/how-to-use-traceroute-to-identify-network-problems/
The source sends an ICMP echo-request message to the destination.
The ping program setsan sequence incremented with each echo-request message. It also sets a TTL (Time-to-live) period.
Ping also inserts the sending time in the data section of the message.
If the host is alive and responding, it sends an ICMP echo-reply message back to the source.
Ping notes the time ofthe arrival of
It then increments the sequence identifier (as said above) and sends a new echo-request message. This goes on for the number of ping requests set by the user or the programis terminated
https://2buntu.com/articles/1204/ping-how-does-it-work/
address are
of desitination Tracert
eg. , ,
eg. HUB,Router
session seperately transport network
This is called In general it many application simply ( be able to
Private IP addresses are assigned These addresses are used routable at the same time
Netstat
Multicast message
In the event that actually
A VLAN is required new user is connected is spread It is used purpos
b. It converts the binary data received from Data Link Layer into signals and transmits them over the local media which can be electrical signals, light etc
b. It is responsible for the physical transformation data. It ensures the message delivery to the right device on the basis of
e. It performs error checking. If any data segment is lost
In Windows:
Go to Control Panel > Network and Internet > Network and Sharing Center > (on the left bar) Change Adapter Settings
Right-Click the adapter you want to configure and choose Properties
Double-Click InternetProtocel Version4 (TCP/IPv4 )
You can set your DNS servers’ address on the bottom half.
In Linux:
Edit the file: /etc/resolv . conf
You add “nameserver xxx. xxx. xxx. xxx”, where the x’s are the IP addresses for your DNS server
In public-key cryptography you have a public and a private key, and you often perform both encryption and signing functions.Which key is used for which function?
Encoding is designed to protect the integrity of data as it crosses networks and systems, i.e. to keep its original message upon arriving, and it isn’t primarily a security function
You’rebasically trying to infiltrate your defenses from the outside.
Hunting is more of an inside-out approach. The assumption is that the bad guys are already in your environment, despite your best efforts to keep them out. Looking at what’s going on inside your environment, specifically odd behavior, will lead to discovering malicious activity.
Can I use what’s detected inhunt to improve my organization’s security?
Security teams can take the threat information gathered during a hunt, determine why they weren’t able to detect these threats and then figure out how they can detect the suspicions in future attacks
If I conduct a hunt anddon’t find anything in my environment, did I waste time and money?
a key goal of hunting is to find existing threats in your environment. For example, let’s say that a financial service company conducts a hunt discovers thatit’s environment is clean. However, many employees are using FTP and around 100GB of data are leaving the company each day. Further investigation shows that the FTP use is legit, but the CISO is concerned . FTP was banned to eliminate the possibility that attackers could use ftp.exe for data exfiltration. Without a hunt, the CISO would've continued to operate under a false assumption that could jeopardize the company’s security.
Whatdo threat hunters do exactly? Are they like Boba Fett or Indiana Jones?
a white hat version
malware attack vectors, and threat actors. They know what Tools, Techniques and Procedures (TTPs) to look for in an environment.
Hunters care about gathering information on the attack, like what information the attackers are after, their overall goals andwhat systems were infiltrated . They’re not incident responders. Remediation isn’t their job ( although they can work with incident response teams. It’s not uncommon for hunters to have government backgrounds. They’ve worked for the military or a three-letter federal agency.
https://www.cybereason.com/blog/blog-threat-hunting-101-you-asked-we-answered
IP is required to connect all networks; TCP is a mechanism that allows us to transfer data safely; and HTTP, which utilizes TCP to transfer its data, is a specific protocol used by Web servers and clients.
which can be accessed from a Linux or Mac system by using the Samba program. Depending on the version, this can allow for share access, printing, and even Active Directory membership.
What are the three ways to authenticate a person?
Something they know (password), something they have (token), and something they are (biometrics). Two-factor authentication oftentimes uses a password and token setup, although in some cases this can be a PIN and thumbprint.
How do you protect your home Wireless Access Point?
using WPA2, not broadcasting the SSID, and using MAC address filtering are the most popular among them.
What is an easy way to configure a network to allow only a single computer to login on a particular jack?
Sticky ports are one of the network admin’s best friends and worst headaches. They allow you to set up your network so that each port on a switch only permits one (or a numberthat you specify) computer to connect on that port by locking it to a particular MAC address.
You areremoted in to a headless system in a remote area. You have no physical access to the hardware and you need to perform an OS installation. What do you do?
What you would want to dois setup a network-based installer capable of network-booting via PXE
What’s the difference between a White Box test and a Black Box test?
Information given by the person commissioning the test.A White Box test is one where the pen testing team is given as much information as possible regarding the environment, while a Black Box test is… well… a Black Box. They don’t know what’s inside.
Whyis deleted data not truly gone when you delete it?
When you press delete on a file, it doesn’tactually go anywhere. A bit on the file is flipped telling the operating system that that file is no longer needed and it can be overwritten as is required . Until that happens, the file can still be restored no matter if it’s in a Recycling Bin or not. There are ways around this, such as using File Shredders and disk wipers
How would you permanently remove the threat of data falling into the wrong hands?
If data is on physical media such as a diskette, cd or even paper, there are shredders, pulverizers and destroyers that can turn plastic and paper into confetti
For harddisks a two-fold method for ensuring a disk’s destruction by first using a specially made disc wiping program, taking apart the hard drive, removing the platters, scratching them up beyond recognition and then degaussing them with a high-powered magnet.
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
An HIDS runs as a background utility in the same as an anti-virus program for instance,
a Network Intrusion Detection System sniffs packets as they go across the network looking for things that aren’tquite ordinary.
Both systems have two basic variants: signature based and anomaly based
http://resources.infosecinstitute.com/top-50-information-security-interview-questions
Let's start with HIDS (Host-based Intrusion Detection System). Wikipedia defines it as "A host-based intrusion detection system (HIDS) is an intrusion detection system that monitors and analyzes the internals of a computing systemas well as (in some cases ) the network packets on its network interfaces (just like a network-based intrusion detection system (NIDS) would do)."
NIDS (Network Intrusion Detection System) Wikipedia defines it as "An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations."
https://www.alienvault.com/forums/discussion/11275/hids-vs-nids-shortcut-to-intrusion-detection-with-alienvault-usm-tip-of-the-month-august-2017
SYN, SYN/ACK, ACK. SYN is the outgoing connection request from client toserver . ACK is the acknowledgement of the server back to the client, saying that yes I hear you, let’s open a connection. SYN/ACK is the final connection, and allows the two to speak. The problem is that this can be used as a very basic type of Denial of Service Attack. The client opens up the SYN connection, the server responds with the SYN/ACK, but then the client sends another SYN. The server treats this as a new connection request and keeps the previous connection open
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
This is usually done on a firewall that has a public-facing IP on the Internet to protect internal users
You want to allow users to connect remotely, what would youuse to allow them to connect to the internal network from the Internet?
Email is not a secure transmission, so some companieschoose to encrypt communication. You can use PGP, which is software that lets you encrypt email messages with a public-private key combination.
You want to allow users to connect remotely, what would youuse to allow them to connect to the internal network from the Internet?
VPN. A Virtual Private Network allows users to “tunnel” from the Internet to the private network. You would still have a firewall and security in place, but the VPN protects user information and hides data sent from the user’s home computer to the private network.
What protocol broadcasts messages across all devices?
IGMP is Internet Group Management Protocol. It’s a communication protocol that lets adjacent routers and communication devices send packets across the networkas a whole instead of direct to another host. It’s used mostly for streaming such as videos and gaming
http://resources.infosecinstitute.com/cissp-interview-questions
pentest ?
“Pentest ” is short for “penetration test”, and involves having a trusted security expert attack a system for the purpose of discovering, and repairing, security vulnerabilities before malicious attackers can exploit them
What is social engineering?
“Social engineering” refers to the use of humans as an attack vector to compromise a system. It involves fooling or otherwise manipulating human personnel into revealing information or performing actions on theattacker’s behalf. Common social engineering techniques include phishing, clickjacking , and baiting
https://www.toptal.com/security/interview-questions
generally have three kinds of techniques to go about. The first technique is to implement a policy for account lockout. In this method, an account will be locked out unless and until the administrator himself opens it. The second being progressive delays. In this method, after a few attempts of login, your account will stay locked for the next few number of days. Lastly , use a challenge-response test. This prevents any kind of automatic submissions on the login page.
Q: What is the need for DNS monitoring?
The Domain Name System allots your website under a certain domain that is easily recognizable and also keeps the information about other domain names. It works like a directory for everything on the internet. Thus, DNS monitoring is very important since you can easily visit a website withoutactually having to memorise their IP address.
SSL and HTTPS: Which is more secure?
SSL (Secure Sockets Layer) is a protocol which enables safe conversations between two or more parties over the internet. HTTPS (Hypertext Transfer Protocol Secure) is HTTP combined with SSL which provides you with a safer browsing experience with encryption. So, this is a very tricky question but SSL wins in terms of security.
Q: In encryption and compression of data during transmission, which of them would you do first? Justify with proper reasons.
If I had the option to encrypt and compress data, I would first compress the data. This is because of encrypting a data weobtain a stream of bits which are random. Now, these random bits become impossible to be compressed , in other words, they are incompressible. The reason to why these random bits become incompressible is because of the lack of any patterned structure. Compressing data always requires any specific pattern to be compressed which is lacked in random bits.
https://mindmajix.com/cyber-security-interview-questions
Confidentiality: Keeping the information secret.
Integrity: Keeping the information unaltered.
Availability: Information is available to theauthorised parties at all times.
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
What is the CIA triangle?
Confidentiality, Integrity, Availability.
Confidentiality- keeping data secure. Integrity- keeping data intact. Availability- keeping data accessible.
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
Vulnerability Assessment is an approach used to find flaws in an application/network whereas Penetration testing is the practice of finding exploitable vulnerabilities like a real attacker will do. VA islike travelling on the surface whereas PT is digging it for gold
What is compliance?
Abiding by a set of standards set by a government/Independent party/organisation. E.g. An industry which stores, processes or transmits Payment related information needs tobe complied with PCI DSS (Payment card Industry Data Security Standard). Other compliance examples can be an organisation complying with its own policies.
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
like travelling on the surface whereas PT is digging it for gold
What is compliance?
Abiding by a set of standards set by a government/Independent party/organisation. E.g. An industry which stores, processes or transmits Payment related information needs tobe complied with PCI DSS (Payment card Industry Data Security Standard). Other compliance examples can be an organisation complying with its own policies.
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
not hard data encryption. It is designed to be able to prove that the person you are talking to on the other end is who they say they are. SSL and its big brother TLS are both used almost everyone online, but the problem is because of this it is a huge target and is mainly attacked via its implementation (The Heartbleed bug for example) and its known methodology . As a result, SSL can be stripped in certain circumstances, so additional protections for data-in-transit and data-at-rest are very good ideas.
11) How would you judge if a remote server is running IIS or Apache?
Error messagesoftentimes giveaway what the server is running, and many times if the website administrator has not set up custom error pages for every site, it can give it away as simply as just entering a known bad address. Other times, just using telnet can be enough to see how it responds.
13) How can you safeguard a company or an institute from SQL injection?
An organization can rely on following methods to guard themselves against SQL injection
Sanitize user input: User input should be never trusted it mustbe sanitized before it is used
Stored procedures: These can encapsulate the SQL statements and treat all input as parameters
Regular expressions: Detecting and dumping harmful code before executing SQL statements
Database connection user access rights: Only necessary and limited access right shouldbe given to accounts used to connect to the database
Error messages: Error message should not be specific telling where exactly the error occurred it shouldbe more generalized .
https://nsdmacademy.com/top-cyber-security-interview-question-and-answers/
a few signs ofmalware as seen through DNS traffic
1. Young domains
When employees’ systems look up domains that are less than a week — or a day — old, companies shouldstart investigating . Young domains are a solid sign that a machine has been infected with malware . Companies can either monitor and investigate the traffic or just block the requests. Maybe the solution is that you do not want to allow traffic to go to a site that is less than 24 hours old.
2. Esoteric domains
the uniqueness of a domain can be a tip that some unsavory activity is going on. If you just have one or two domains that only a few devices are querying, that is a good thing tostart looking at. As with young domains, esoteric domains can escape IP blacklists that might otherwise signal the company that the domain is hosting a malicious Web site.
3. Lookup failures
if a computer hasa large number of failed domain lookups, that could also be a sign that something is wrong. If a device tries 1,000 different domains and only one or two are valid, then focus on that device.
http://www.hacktress.com/why-is-dns-monitoring-important/
It’s also a plaintext protocol, which can benefit an incident responder who cannot otherwise examine the contents of an encrypted connection.
assive DNS monitoring is a method by which a traffic monitoring station examines the contents of DNS queries and responses, then logs that information in a standardized format to text files or other long-term storage mechanisms.
Why Is Passive DNS Monitoring Important in DFIR?
The hostname/IP address associations can help characterizeNetFlow observations, which have no layer 7 context. Additionally, the server’s IP address can be useful in identifying clients that make direct requests to servers outside the environment.
Such behavior mightindicate a misconfigured resource, a platform with a hard-coded DNS server IP address, or a rogue actor that is ignoring internal DNS server directives assigned by DHCP or a domain hierarchy.
the clearest use of such DNS log evidence would be to support findings that incorporate threat intelligence. The use cases here arenumerous , but examples include flagging heavy query activity for newly-registered -domains or identifying a newly-observed domain from a list of the top 5,000 typically queried within your environment. Further, maintaining such logs for an appropriately long period of time can quickly aid an investigator to find the earliest evidence of compromise after a domain or domain-generation algorithm is identified as malicious or suspect.
Four Approaches to Creating DNS Log Evidence
1: Use the DNS Server for DNS Logging
2: Deploy Passive DNS Monitoring Software
Another option is to deploy passive DNS monitoring software,which can be installed on the DNS server or onto a separate system that observes the DNS traffic through a network tap. Options for this observation model include the venerable BRO IDS, the tiny-footprint PassiveDNS project
3: Outsource DNS Service
4: Collect Network Activity on Endpoints
A final option is to collect network activity on each endpoint, then aggregate to a central location for analysis
The endpoint sensor logs network connection metadata, including the destination IP address and requested hostname. This differs from native DNS loggingin that it does not reveal blocked or failed requests, nor other context specific to the DNS protocol. However, it does provide valuable context related to the process that initiated the connection
https://redcanary.com/blog/passive-dns-monitoring-your-ir-team-needs-it/
ping uses TCP or UDP. An answer of either is a fail, as those are layer 4 protocols.
Ping is ICMP, which islayer 3. Ports are not used until layer 4 which handles UDP and TCP
What’s the difference between Diffie-Hellman and RSA?
Diffie-Hellman is a key-exchange protocol, and RSA is an encryption/signing protocol. If they get that far, make sure they can elaborate on the actual difference, which is that one requires you to have key material beforehand (RSA), while the other does not (DH).
What kind of attack is a standard Diffie-Hellman exchange vulnerable to?
Man-in-the-middle, asneither side is authenticated .
How does HTTP handle state?
It doesn’t, of course . Not natively. Good answers are things like “cookies”, but the best answer is that cookies are a hack to make up for the fact that HTTP doesn’t do it itself.
What are the primary design defects of HTTP?
Commands are text-based, which slows down parsing considerably.
It’s point-to-point. You can’t receive amulticast stream via HTTP, which is why you have to tolerate awful video, horrible lag and massive delays whilst watching.
URLs breakIPv6 standards
It’s designed on the assumption that machines are static
https://www.quora.com/What-are-the-primary-design-defects-of-HTTP
In HTTP,client initiates an HTTP session by opening a TCP connection to the HTTP server with which it wishes to communicate. It then sends request messages to the server, each of which specifies a particular type of action that the user of the HTTP client would like the server to take. The server responds to the client's request and sends the data which he wants. But HTTP uses only one TCP connection i.e. from client to server , there is no TCP connection from server to client . The server sends data to client there is no guarantee that the client is going to get it. If client don't get the data in the TTL ( time to live) , it again make a request for the data.
HTTP Is asession based protocol. If it will use UDP then it has to maintain or handle session. E.g in case of any packet loss HTTP need to re transmit the missing packet. TCP already providing the session services. IN TCP, before sending any HTTP request , a TCP connection is setup . So sending node gets no connection setup if no listener on destination.
HTTP uses TCP instead of UDP because it guarantees delivery via a three-way handshake and re-transmission of lost packets.UDP is mainly used for voice and video streaming to prevent out of order packet assembly that can cause jitter and doesn’t require the use of a three-way handshake beyond the SIP, Skinny protocols used to setup the call. TCP will re-transmit lost packets and ensure all data is received as a result, ensuring that you will get all images, links and other elements of the web-page . If you do that with a voice call, there would be call quality issues when the packets arrive out of order or are dropped and there is delay waiting for that packet to re-transmit.
https://www.quora.com/Does-HTTP-use-TCP-or-UDP-Why
It is NOT expected to run over UDP, which is an unreliable datagram protocol (in fact, while that's not its official name, that's a good way to remember what it is).
The OSI model allows higher layer protocols to run over any underlying protocol providing the correct services. HTTPS is HTTP using SSL/TLS security. SSL/TLS typically runs on top of TCP, but there is nothing to stop you from running it on UDP, SCTP or any other transport layer protocol
https://serverfault.com/questions/98951/does-https-use-tcp-or-udp
Which of the following is referred to as a C3 cipher? Caesar cipher
Which of the following algorithms uses a key length that is the same as the length of the message tobe encrypted ?
One-time pad
Which of the following algorithms has an unbreakable encryption scheme?
One-time pad
Which of the following is a symmetric key cipher that operates on one character ora bit of a message at a time?
Stream cipher
Which goal of cryptography ensures thata message is not altered while in transit?
Integrity
Which of the following has theobjective to find some weakness or insecurity in a cryptographic scheme?
Cryptanalysis
Which of the following ensures that the subject of an activity or event cannot deny that the event occurred?
Nonrepudiation
Which of the following is the size of the block for Triple DES?
8 bytes
What is the correct length of the key used in the DES-EEE3 mode?
168 bits
What is the correct length of the Skipjack key?
80 bits
What is the size of each key used in the key-bundle of the 3DES algorithm (excluding parity bits)?
56 bits
Which of the following is the least secure mode of the Data Encryption Standard?
Electronic Codebook mode
Which of the following is a set of rules used by computers to communicate with each other across a network?
Protocol
Which of the following algorithmsis not supported by the Digital Signature Standard?
AES
If Nancy wishesto digitally sign a message to Matthew, which key should she use to create the signature?
Private Key
If Matthew receives a digitally signed message from Nancy, which key should heuse to verify the signature?
Nancy’s Public key
If Matthew wishesto digitally sign a message to Nancy, which key should he use to digitally sign the message?
Private Key
If Nancy receives a digitally signed message from Matthew, which key should sheuse to verify the signature?
Mathew’s public key
If Renee receives a digitally signed message from Mike, what key does sheuse to verify that the message truly came from Mike?
Mike’s public key
Which of the following uses both a public and private key to encrypt and decrypt data?
Asymmetric Cryptography
Which of the following algorithms doubles the length of any messagethat it encrypts?
El Gamal
Howis annualized loss expectancy (ALE) calculated?
SLE*ARO( single loss expectancy * annualized rate of occurrence
What is the length of a message digest produced by the MD5 algorithm?
B. 128 bits
You are the security administrator of a large law firm.You have been asked to select a security model that supports your organization’s desire to ensure data confidentiality and integrity. You must select one or more models that will protect data from internal and external attacks. What security model( s) will you choose? (Choose all that apply.)
Bell-LaPadula,Clark -Wilson
In what phase of the Capability Maturity Model for Software (SW-CMM) are quantitative measuresutilized to gain a detailed understanding of the software development process?
Managed
A VPN can be established over which of the following?
Wireless LAN connection
Remote access dial-up connection
WAN link
What is the Biba access control model primarily based upon?
Lattice
Which one of the following database backup techniques requires the greatest expenditure of funds?
Remote mirroring maintains a live database server at the remote site and comes at the highest cost
Which one of the following security modes does not require that a user have a valid security clearance for all information processed by the system?
In multilevel security mode, some users do not have a valid security clearance for all information processed by the system
You are the security administrator for an international shipping company.You have been asked to evaluate the security of a new shipment tracking system for your London office. It is important to evaluate the security features and assurance of the system separately to compare it to other systems that management is considering. What evaluation criteria should you use (assume the year is 1998)?
ITSEC was developed in Europe for evaluating systems. Although TCSEC (also called the Orange Book) would satisfy the evaluation criteria, only ITSEC evaluates functionality and assurance separately.
What is the last phase of the TCP/IP three-way handshake sequence?
The SYN packet is first sent from theinitiating host to the destination host. The destination host then responds with a SYN /ACK packet. The initiating host sends an ACK packet and the connection is then established .
Which of the following is a requirement of change management?
Oneof the requirements of change management is that all changes must be capable of being rolled back
Which of the following is a procedure designed to test and perhaps bypass a system's security controls?
Penetration testing is the attempt to bypass security controls to test overall system security.
At whichlayer of the OSI model does a router operate?
Network hardware devices, including routers, function at layer 3, the Network layer
Which of the following is considered a denial of service attack?
Not all instances of DoSare the result of a malicious attack. Errors in coding OSs, services, and applications have resulted in DoS conditions. Some examples of this include a process failing to release control of the CPU or a service consuming system resources out of proportion to the service requests it is handling. Social engineering and sniffing are typically not considered DoS attacks.
Audit trails, logs, CCTV, intrusion detection systems, antivirus software, penetration testing, password crackers, performance monitoring, and cyclic redundancy checks (CRCs) are examples of what?
Examples of detective controls are audit trails, logs, CCTV, intrusion detection systems, antivirus software, penetration testing, password crackers, performance monitoring, and CRCs.
Which one of the following vulnerabilities would best be countered by adequate parameter checking?
Parameter checking is used to prevent the possibility of buffer overflow attacks
What technology allows a computer to harness the power ofmore than one CPU?
Multiprocessing computers usemore than one processor, in either a symmetric multiprocessing (SMP) or massively parallel processing (MPP) scheme.
What type of backup stores all filesmodified since the time of the most recent full or incremental backup?
Differential backups store all files that havebeen modified since the time of the most recent full or incremental backup.
What type of detected incident allows the most time for an investigation?
Scanning incidents aregenerally reconnaissance attacks. The real damage to a system comes in the subsequent attacks, so you may have some time to react if you detect the scanning attack early.
Auditing is a required factor to sustain and enforce what?
Auditing is a required factor to sustain and enforce accountability
Which type of firewall automatically adjusts its filtering rules based on the content of the traffic of existing sessions?
Dynamic packet-filtering firewalls enable real-time modification of the filtering rules based on traffic content
Which of the following is the principle that objectsretain their veracity and are only intentionally modified by authorized subjects?
Integrity
E-mail is the most common delivery vehicle for which of the following?
Malicious code
Worms
Viruses
What type of physical security controls are access controls, intrusion detection, alarms, CCTV, monitoring, HVAC, power supplies, and fire detection and suppression?
Technical
What is the first step of the Business Impact Assessment process?
Identification of priorities is the first step of the Business Impact Assessment process.
The "something you are" authentication factoris also known as what?
Type 3 authentication factor is something you are, such as fingerprints, voice print, retina pattern, iris pattern, face shape, palm topology, hand geometry, and so on.
What is the primary goal of risk management?
The primary goal of risk management is to reduce risk to an acceptable level
https://www.yeahhub.com/cissp/#answer
types of access control seeks to discover evidence of unwanted,unauthorized , or illicit behavior or activity?Detective
Define and detail the aspects of password selection that distinguish good password choices from ultimately poor password choices.
Difficult to guess or unpredictable
Meet minimum length requirements
Meet specific complexity requirements
What type of malware uses social engineering to trick a victim into installing it?
A Trojan horse isa form of malware that uses social engineering tactics to trick a victim into installing it—the trick is to make the victim believe that the only thing they have downloaded or obtained is the host file, when it fact it has a malicious hidden payload.
What kind of recovery facility enables an organization to resume operations as quickly as possible, if not immediately, upon failure of the primary facility?
Hot sites provide backup facilities maintained in constant working order and fully capable of taking over business operations.
Warm sitesconsist of preconfigured hardware and software to run the business, neither of which possesses the vital business information.
Cold sites aresimply facilities designed with power and environmental support systems but no configured hardware, software, or services. Disaster recovery services can facilitate and implement any of these sites on behalf of a company.
Which of the following represent natural events that can pose a threat or risk to an organization?
Natural events that can threaten organizations include earthquakes, floods, hurricanes, tornados, wildfires, and other acts of nature as well
The collection of components in the TCB that work together to implement reference monitor functions is called the . ..?
The collection of components in the TCB that work together to implement reference monitor functions is called the security kernel
Why are military and intelligence attacks among the most serious computer crimes?
The purpose of a military and intelligence attack is to acquire classified information. The detrimental effect of using such information could be nearly unlimited in the hands of an enemy. Attacks of this typeare launched by very sophisticated attackers. It is often very difficult to ascertain what documents were successfully obtained . So when a breach of this type occurs, you sometimes cannot know the full extent of the damage
Which of the following is not a defense against collusion?
Group user accounts allow for multiple people to log in under a single user account. This allows collusion because it prevents individual accountability.
Which of the following are a defense against collusion?
Separation of duties
Restricted job responsibilities
Job rotation
Which of the following is not a composition theory related to security models?
Iterative is not one of the composition theories related to security models. Cascading, feedback, and hookup are the three composition theories
Which of the following statements is true?
The more complex a system, the less assurance it provides. More complexity means more areas for vulnerabilities to exist and more areas that mustbe secured against threats. More vulnerabilities and more threats mean that the subsequent security provided by the system is less trustworthy.
System architecture, system integrity, covert channel analysis, trusted facility management, and trusted recovery are elements of what security criteria?
Assurance isthe degree of confidence you can place in the satisfaction of security needs of a computer, network, solution, and so on. Operational assurance focuses on the basic features and architecture of a system that lend themselves to supporting security
Which one of the following is a layer of the ring protection scheme thatis not normally implemented in practice?
Layers 1 and 2 contain device drivers butare not normally implemented in practice.
Layer 0 always contains the security kernel.
Layer 3 contains user applications.
Whyis separation of duties important for security purposes ?
It prevents any single security subject (person ) from being able to make major securitychanges without involving other subjects
Which of the following is the least acceptable form ofbiometric device?
Retina scan
Which of the following forms of authentication provides the strongest security?
Passphrase and a smart card
Kerberos provides the security services of . . protection for authentication traffic.
confidentiality and integrity
What is the most important aspect of a biometric device?
Accuracy
A network environment that uses discretionary access controls is vulnerable to which?
Impersonation
What is the point of a secondary verification system?
To verify the correctness of a system
What can be used as an authentication factor that is a behavioral or physiological characteristic unique to a subject?
Biometric factor
Which of the following contains the primary goals and objectives of security?
The primary goals and objectives of security are confidentiality, integrity, and availability, commonly referred to as the CIA Triad.
Vulnerabilities and risks are evaluated based on their threats against which of the following?
Vulnerabilities and risks are evaluated based on their threats against one or more of the CIA Triad principles.
Which of the following is a principle of the CIA Triad that meansauthorized subjects are granted timely and uninterrupted access to objects?
Availability means thatauthorized subjects are granted timely and uninterrupted access to objects
Which of the following are considered a violation of confidentiality?
Violations of confidentiality include capturing network traffic, stealing password files, social engineering, port scanning, shoulder surfing, eavesdropping, and sniffing.
https://www.brainscape.com/flashcards/assessment-test-4218413/packs/6347928
- So what happens when we ping a machine?
The source sends an ICMP echo-request message to the destination.
The ping program sets
Ping also inserts the sending time in the data section of the message.
If the host is alive and responding, it sends an ICMP echo-reply message back to the source.
Ping notes the time of
It then increments the sequence identifier (as said above) and sends a new echo-request message. This goes on for the number of ping requests set by the user or the program
https://2buntu.com/articles/1204/ping-how-does-it-work/
Network Troubleshooting using PING, TRACERT, IPCONFIG, NSLOOKUP COMMANDS
- List of TCP and UDP port numbers
There are different types of Well Known
https://howdoesinternetwork.com/2012/tcp-udp-port-numbers-list
- 1. Explain
range
Answer :
CLASS A = 1 to 126
CLASS B = 128 to 191
CLASS C = 192 to 223
CLASS D = 224 to 239 (Multicasting)
CLASS E = 240 to 255 (Research)
66) What are the maximum networks and hosts in a class A, B and C network?
For Class A, there are 126 possible
For Class B, there are 16,384 possible
For Class C, there are 2,097,152 possible
2. What are Pvt. IP address ?
Private IPv4
RFC1918 name IP address range Mask bits
24-bit block 10.0.0.0 –
20-bit block 172.16.0.0 –
16-bit block 192.168.0.0 –
3. What is function ?
Answer :
4. What is Default Gateway :
Answer :
52) What is the use of a default gateway?
Default gateways provide means for the local networks to connect to the external network. The default gateway for connecting to the external network is usually the address of the external router port.
39) What are gateways?
Gateways provide connectivity between two or more network segments. It is usually a computer that runs the gateway software and provides translation services. This translation is a key in allowing different systems to communicate on the network.
5. What is Subnet Mask ?
Answer : a given
Class A = 255.0.0.0
Class B = 255.255.0.0
Class C = 255.255.255.0
6. What is Loopback address ?
Answer : loopback
suite or local machine
7. What protocol is used ( ?
Answer : (
59) What is ICMP?
ICMP is Internet Control Message Protocol. It provides messaging and communication for protocols within the TCP/IP stack. This is also the protocol that manages error messages that are used
8. What is used Tracert ?
Answer : Tracert desitnation show
11. Difference between Switch and Hub
Full-duplex Half-duplex
5. When to use cross cable and straight cable
Similar device = cross cable
Unsimilar device = straight cable
71) What is the difference between a straight-through and crossover
A crossover cable is used to connect two similar devices together, such as a PC to PC or Hub to hub
A straight-through cable is used to connect computers to a switch, hub or router.
7. difference between domain and workgroup
Domain Workgroup
a. centralized network model decentralized network
b. Domain is controlled centrailzed
c. Centralised login Local login
d. centrailsed databased
e. Easy and centrailsed
f. good for large small
9. Explain in short about
Application layer = user interface and application
Presentation layer = Data conversion and transformation
Data link layer = Physical addressing like MAC address.
Physical layer = Physical transmission of data using 0's and 1's.
What is DNS ?
Answer :
2. Types of Zone in DNS ?
Answer :
Reverse lookup - it is used to resolve IP to FQDN
4. what is NSlookup ?
Answer :
5 What is DHCP ?
Answer: DHCP is used to automatically provide
8. What is WINS ?
Answer : NetBIOS
5) Port numbers for various application and services
There are total 65536 ports available. Below are the list of some well-known ports.
LDAP : : , : , : , : , : , : , :
RPC : , : , : , :
4) What is SNMP ?
Answer : )
used to monitor and manage network devices like Switches, Routers, Servers, etc. SNMP
uses port UDP port number 161 and 162.
5. Name the two routing protocols?
Ans:-RIP & OSPF (intra domain
6. What is the advantage of OSPF protocol?
Ans:-OSPF( It handle timely
36) What is the main purpose of OSPF?
OSPF, or Open Shortest Path First, is a link-state routing protocol that uses routing tables to determine the best possible
9. Difference between intra domain and inter domain
Ans:-Routing within an autonomous system is referred intra domain is called inter domain
27. What is utility of sequence number in Reliable Transmission?
Ans:- The protocol specifies that frames numbering has to be done A field is added in order
http://intquestionsandans.blogspot.com/p/tcpip.html
- 7) What is
point to point
It refers to a direct connection between two computers on a network. A point to point
14) Briefly describe NAT.
NAT is Network Address Translation. This is a protocol that provides a way for multiple computers on a common network to share single
Can I Set Up A Gateway To The Internet That Translates Ip Addresses, So That I
17) What is RIP?
RIP, short for Routing Information Protocol is used
23) What are proxy servers and how do they protect computer networks?
Proxy servers primarily prevent external users who identifying the IP addresses of an internal network.
Proxy servers can make a network virtually invisible to external users.
26) What does 10Base-T mean?
The 10 refers to the data transfer rate, in this case is 10Mbps. The word Base refers to base band broad
27) What is a private IP address?
42) Give some examples of private network addresses.
10.0.0.0 with a subnet mask of 255.0.0.0
172.16.0.0 with subnet
192.168.0.0 with subnet mask of 255.255.0.0
31) What is the purpose of cables being shielded and having twisted pairs?
The main purpose of this is to prevent crosstalk. Crosstalks are electromagnetic interferences or noise that can affect data being transmitted across cables.
33) What are MAC addresses?
MAC, or Media Access Control, uniquely identifies a device on the network. It is also known physical A MAC address is made
35) How can you identify the IP class of a given
By looking at the first octet of any given
45) Describe at one disadvantage of a peer to peer
When you are accessing the resources that are shared of the workstations
61) What is peer to peer
Peer to peer are networks that does not reply on a server. All PCs on this network act as individual workstations.
47) What is DHCP?
DHCP is short for Dynamic Host Configuration Protocol. Its main task is to automatically assign th
90) How does dynamic host configuration protocol aid in network administration?
Instead of having to visit each client computer to configure a static IP address, the network administrator can apply dynamic host configuration protocol to create a pool of IP addresses known as scopes that can be dynamically assigned
48) What is the main job of the ARP?
The main task of ARP or Address Resolution Protocol is to map a known IP address to a MAC layer address.
55) What is netstat
57) What happens when you use cables longer than the prescribed length?
Cables that are too long would result in be affected
69) You need to connect two computers for file sharing. Is it possible to do this without using a hub or router?
Yes, you can connect two computers together using only one cable. A crossover type cable can be use
74) When you move the NIC cards from one PC to another PC, does the MAC address gets transferred as well?
Yes, that's because MAC addresses are hard-wired into the NIC circuitry, not the PC. This also means that a PC can have a different MAC address when the NIC card was replace by another one
80) What is SMTP?
SMTP is short for Simple Mail Transfer Protocol. This protocol deals with all Internal mail, necessary
81) What is multicast
87) What is one advantage of mesh topology?
96) What is one basic requirement for establishing VLANs?
https://www.guru99.com/networking-interview-questions.html
- What Are The Networking Protocol Options For The Windows Clients If
For Some Reason You ip
NWLink (Novell), NetBEUI, AppleTalk (Apple).
What Is Tcp/ip
TCP/IP model is an implementation of OSI reference model. It has five layers.
Network layer,
Internet layer,
Transport layer
Application layer.
What Is A Link ip
A link refers to the connectivity between two devices. It includes the type of be able to
https://www.skillhirejobs.com/career-guide/tcp-ip-interview-questions-and-answers
- What is TCP Three-Way Handshake?
A TCP Three-way Handshake is a method to establish a connection between the client/localhostand
What is CRC? On which layer CRC works?
CRC is Cyclic Redundancy Check. It is used to detect errors in a network. It works at Data Link Layer.
What is Port Number and Define the Range of Port Numbers?
A port number is a unique identification 16-bit unsigned number that is put
The range of Port Numbers:
a. Well Known
b. Registered Ports: 1024 to 49151
c. Private or Open Ports: 49152 to 65535
What is the difference between Half-Duplex and Full-Duplex?
Half-Duplex: In half-duplex data can travel in both directions but not at the same time. Either device can send the data or can receive the data at a single point of time.
Full-Duplex: In Full-Duplex scenario, Data can travel in both direction at the same time. Data can travel in both directions simultaneously.
Explain the Physical Layer of the OSI model?
a. It is the 1st layer of the OSI model.
c. All the hardware such as NIC, Ethernet, ADSL, Bluetooth are the protocols of Physical Layer.
Explain the difference between Flow Control and Error Control?
Flow Control: Flow Control is the function of adjusting the flow of data from one device to another device in between adjacent OSI layers. It is used It is particularly used is capable of transmitting
Error Control: Error Control is the process of
Explain the functions of Data Link, Network and Transport Layer?
Data Link Layer
a. It is the second layer of the OSI model.
c. It helps in generating error notification and flow control.
d. It provides services to the upper layer i.e. Network Layer by transforming packets into frames.
e. Data link layer adds the customized header into the messaging which contains hardware source and destination MAC address.
Network Layer
a. It is the third layer of the OSI model.
b. It manages the network devices on the basis of
c. It is responsible for packet forwarding, routing and addressing.
d. It transmits data segments between networks in the form of packets.
e. It also determines the best path for the packet delivery between the Source IP Address and Destination IP address.
Transport Layer
a. Transport Layer is the fourth layer of the OSI model
b. It receives data from the Session Layer and segments it.
c. Each segment is made up of
d. Transport layer has two well-known protocols—
f. It provides the feature of Data Integrity by maintaining flow control.
Is there any other alternative model to the OSI model? If yes, explain it.
We have TCP/IP as an alternate model which also explains the standards of communication between computers/application over the network. It is a much more simple model as compared to the OSI layer model and also contains fewer details of protocols than the OSI model
What is OSI Layer Model?
OSI is the Open Systems Interconnection is a reference model which defines the standards of communication between the computer systems/applications over the network.
https://tblogqus.com/osi-model-interview-questions-and-answers-ccna/
- How do you change your DNS settings in Linux/Windows?
In Windows:
Go to Control Panel > Network and Internet > Network and Sharing Center > (on the left bar) Change Adapter Settings
Right-Click the adapter you want to configure and choose Properties
Double-Click Internet
You can set your DNS servers’ address on the bottom half.
In Linux:
Edit the file: /etc/
You add “
In public-key cryptography you have a public and a private key, and you often perform both encryption and signing functions.
- 6. What is the difference between a threat, a vulnerability, and a risk?
a threat is from someone targeting a vulnerability (or weakness) in the organization that was not mitigated or taken care of since it was not properly identified as a risk.
8. Why is DNS monitoring important?
DNS monitoring is prudent because DNS queries are a data-exfiltration vector from networks that allow any host to communicate to the Internet on Port 53.
9. What port does ping work over?
Watch out for this. Ping is a layer-3 protocol like IP; ports are an element of the layer-4 protocols TCP and UDP.
10. What is the difference between encoding, encrypting, and hashing?
Encoding: Encoding converts the data in a desired format required for exchange between different systems. This doesn’t convert it into a secret data, but usable data. It can be further decoded through the same tools when necessary.
It is easily reversible
Hashing: This serves for maintaining the integrity of a message or data. This way if any day it is hampered or changed, you will get to know.
hashing the operation is one -way (non-reversible), and the output is of a fixed length that is usually much smaller than the input.
Encryption: Encryption ensures that the data is secure and one needs a digital verification code or image in order to open or access it.
Encryption is designed purely for confidentiality and is reversible only if you have the appropriate key/keys.
Encryption is reversible whereas hashing is irreversible. Hashing can be cracked using rainbow tables and collision attacks but is not reversible.
Encryption ensures confidentiality whereas hashing ensures Integrity.
Encryption is the process of turning text into code. A cipher is that actual code.
19. What is the difference between symmetric and asymmetric encryption?
Asymmetric encryption is commonly used to secure an initial key-sharing conversation, but then the actual conversation is secured using symmetric crypto.
Communication using symmetric crypto is usually faster due to the slightly simpler math involved in the encryption/decryption process and because the session setup doesn’t involve PKI certificate checking
18. What does RDP stand for?
Remote desktop protocol, and its port number is 3389.
15. How would you strengthen user authentication?
two-factor authentication or non-repudiation
14. If you had to both compress and encrypt data during a transmission, which would you do first?
Compress and then encrypt, since encrypting first might make it hard to show compression having much of an effect.
- What are the main differences between threat hunting and penetration testing?
You’re
Hunting is more of an inside-out approach. The assumption is that the bad guys are already in your environment, despite your best efforts to keep them out. Looking at what’s going on inside your environment, specifically odd behavior, will lead to discovering malicious activity.
Can I use what’s detected in
Security teams can take the threat information gathered during a hunt, determine why they weren’t able to detect these threats and then figure out how they can detect the suspicions in future attacks
If I conduct a hunt and
a key goal of hunting is to find existing threats in your environment. For example, let’s say that a financial service company conducts a hunt discovers that
What
a white hat version
malware attack vectors, and threat actors. They know what Tools, Techniques and Procedures (TTPs) to look for in an environment.
Hunters care about gathering information on the attack, like what information the attackers are after, their overall goals and
https://www.cybereason.com/blog/blog-threat-hunting-101-you-asked-we-answered
- Q.4 The HTTP protocol uses TCP or UDP?
How are TCP/IP and HTTP related?
The term "TCP/IP" stands for Transmission Control Protocol / Internet Protocol and refers to a number of protocols. The "IP" part of the term, which stands for Internet Protocol, is used by TCP and UDP , to transport them from one network to another. Think of IP as a sort of high-way that allows other protocols to get on and find their way to other computers. TCP and UDP are the "trucks" on the highway, and the "load" they are carrying are protocols such as HTTP, File Transfer Protocol (FTP) and more.
As you can understand, TCP and UDP are transport protocols used by protocols such as FTP, HTTP, and SMTP. While both TCP and UDP are used to transport other protocols, they have one significant difference; TCP offers guaranteed data transportation, whereas UDP doesn't. What this means is that TCP has a special mechanism that ensures data is safely transferred without errors from one point to another, whereas UDP doesn't provide any such insurance.
https://searchnetworking.techtarget.com/answer/How-are-TCP-IP-and-HTTP-related
- How would you login to Active Directory from a Linux or Mac box?
What are the three ways to authenticate a person?
Something they know (password), something they have (token), and something they are (biometrics). Two-factor authentication often
How do you protect your home Wireless Access Point?
using WPA2, not broadcasting the SSID, and using MAC address filtering are the most popular among them.
What is an easy way to configure a network to allow only a single computer to login on a particular jack?
Sticky ports are one of the network admin’s best friends and worst headaches. They allow you to set up your network so that each port on a switch only permits one (or a number
You are
What you would want to do
What’s the difference between a White Box test and a Black Box test?
Information given by the person commissioning the test.
Why
When you press delete on a file, it doesn’t
How would you permanently remove the threat of data falling into the wrong hands?
If data is on physical media such as a diskette, cd or even paper, there are shredders, pulverizers and destroyers that can turn plastic and paper into confetti
For hard
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
- What is the difference between an HIDS and
a NIDS ?
An HIDS runs as a background utility in the same as an anti-virus program for instance,
a Network Intrusion Detection System sniffs packets as they go across the network looking for things that aren’t
Both systems have two basic variants: signature based and anomaly based
http://resources.infosecinstitute.com/top-50-information-security-interview-questions
Let's start with HIDS (Host-based Intrusion Detection System). Wikipedia defines it as "A host-based intrusion detection system (HIDS) is an intrusion detection system that monitors and analyzes the internals of a computing system
NIDS (Network Intrusion Detection System) Wikipedia defines it as "An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations."
https://www.alienvault.com/forums/discussion/11275/hids-vs-nids-shortcut-to-intrusion-detection-with-alienvault-usm-tip-of-the-month-august-2017
- What is the Three-way handshake? How can it
be used to create a DOS attack?
SYN, SYN/ACK, ACK. SYN is the outgoing connection request from client to
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
- When you want to filter packets that traverse the network, what should you do?
You want to allow users to connect remotely, what would you
Email is not a secure transmission, so some companies
You want to allow users to connect remotely, what would you
VPN. A Virtual Private Network allows users to “tunnel” from the Internet to the private network. You would still have a firewall and security in place, but the VPN protects user information and hides data sent from the user’s home computer to the private network.
What protocol broadcasts messages across all devices?
IGMP is Internet Group Management Protocol. It’s a communication protocol that lets adjacent routers and communication devices send packets across the network
http://resources.infosecinstitute.com/cissp-interview-questions
- 9 Essential System Security Interview Questions
“
What is social engineering?
“Social engineering” refers to the use of humans as an attack vector to compromise a system. It involves fooling or otherwise manipulating human personnel into revealing information or performing actions on the
https://www.toptal.com/security/interview-questions
- Q: What are the techniques used in preventing a brute force login attack?
Q: What is the need for DNS monitoring?
The Domain Name System allots your website under a certain domain that is easily recognizable and also keeps the information about other domain names. It works like a directory for everything on the internet. Thus, DNS monitoring is very important since you can easily visit a website without
SSL and HTTPS: Which is more secure?
SSL (Secure Sockets Layer) is a protocol which enables safe conversations between two or more parties over the internet. HTTPS (Hypertext Transfer Protocol Secure) is HTTP combined with SSL which provides you with a safer browsing experience with encryption. So, this is a very tricky question but SSL wins in terms of security.
Q: In encryption and compression of data during transmission, which of them would you do first? Justify with proper reasons.
If I had the option to encrypt and compress data, I would first compress the data. This is because of encrypting a data we
https://mindmajix.com/cyber-security-interview-questions
- CIA triangle?
Confidentiality: Keeping the information secret.
Integrity: Keeping the information unaltered.
Availability: Information is available to the
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
What is the CIA triangle?
Confidentiality, Integrity, Availability.
Confidentiality- keeping data secure. Integrity- keeping data intact. Availability- keeping data accessible.
http://resources.infosecinstitute.com/top-50-information-security-interview-questions/
- What is the difference between VA and PT?
Vulnerability Assessment is an approach used to find flaws in an application/network whereas Penetration testing is the practice of finding exploitable vulnerabilities like a real attacker will do. VA is
What is compliance?
Abiding by a set of standards set by a government/Independent party/organisation. E.g. An industry which stores, processes or transmits Payment related information needs to
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
- What is the difference between VA and PT?
What is compliance?
Abiding by a set of standards set by a government/Independent party/organisation. E.g. An industry which stores, processes or transmits Payment related information needs to
https://www.greycampus.com/blog/information-security/top-cyber-security-interview-questions
- 6) What is SSL and why is it not enough
when it comes to encryption?
11) How would you judge if a remote server is running IIS or Apache?
Error messages
13) How can you safeguard a company or an institute from SQL injection?
An organization can rely on following methods to guard themselves against SQL injection
Sanitize user input: User input should be never trusted it must
Stored procedures: These can encapsulate the SQL statements and treat all input as parameters
Regular expressions: Detecting and dumping harmful code before executing SQL statements
Database connection user access rights: Only necessary and limited access right should
Error messages: Error message should not be specific telling where exactly the error occurred it should
https://nsdmacademy.com/top-cyber-security-interview-question-and-answers/
- what is
dns monitoring?
- why is
dns monitoring-important?
a few signs of
1. Young domains
When employees’ systems look up domains that are less than a week — or a day — old, companies should
2. Esoteric domains
the uniqueness of a domain can be a tip that some unsavory activity is going on. If you just have one or two domains that only a few devices are querying, that is a good thing to
3. Lookup failures
if a computer has
http://www.hacktress.com/why-is-dns-monitoring-important/
- Why Is Passive DNS Monitoring Important in DFIR?
It’s also a plaintext protocol, which can benefit an incident responder who cannot otherwise examine the contents of an encrypted connection.
Why Is Passive DNS Monitoring Important in DFIR?
The hostname/IP address associations can help characterize
Such behavior might
the clearest use of such DNS log evidence would be to support findings that incorporate threat intelligence. The use cases here are
Four Approaches to Creating DNS Log Evidence
1: Use the DNS Server for DNS Logging
2: Deploy Passive DNS Monitoring Software
Another option is to deploy passive DNS monitoring software,
3: Outsource DNS Service
4: Collect Network Activity on Endpoints
A final option is to collect network activity on each endpoint, then aggregate to a central location for analysis
The endpoint sensor logs network connection metadata, including the destination IP address and requested hostname. This differs from native DNS logging
https://redcanary.com/blog/passive-dns-monitoring-your-ir-team-needs-it/
- What port
does ping work over?
Ping is ICMP, which is
What’s the difference between Diffie-Hellman and RSA?
Diffie-Hellman is a key-exchange protocol, and RSA is an encryption/signing protocol. If they get that far, make sure they can elaborate on the actual difference, which is that one requires you to have key material beforehand (RSA), while the other does not (DH).
What kind of attack is a standard Diffie-Hellman exchange vulnerable to?
Man-in-the-middle, as
How does HTTP handle state?
It doesn’t
What are the primary design defects of HTTP?
Commands are text-based, which slows down parsing considerably.
It’s point-to-point. You can’t receive a
URLs break
It’s designed on the assumption that machines are static
https://www.quora.com/What-are-the-primary-design-defects-of-HTTP
- Does HTTP use TCP or UDP? Why?
In HTTP,
HTTP Is a
HTTP uses TCP instead of UDP because it guarantees delivery via a three-way handshake and re-transmission of lost packets.
https://www.quora.com/Does-HTTP-use-TCP-or-UDP-Why
- Does
https use tcp orudp ?
The OSI model allows higher layer protocols to run over any underlying protocol providing the correct services. HTTPS is HTTP using SSL/TLS security. SSL/TLS typically runs on top of TCP, but there is nothing to stop you from running it on UDP, SCTP or any other transport layer protocol
https://serverfault.com/questions/98951/does-https-use-tcp-or-udp
- CISSP
Which of the following algorithms uses a key length that is the same as the length of the message to
Which of the following algorithms has an unbreakable encryption scheme?
Which of the following is a symmetric key cipher that operates on one character or
Stream cipher
Which goal of cryptography ensures that
Integrity
Which of the following has the
Cryptanalysis
Which of the following ensures that the subject of an activity or event cannot deny that the event occurred?
Nonrepudiation
Which of the following is the size of the block for Triple DES?
8 bytes
What is the correct length of the key used in the DES-EEE3 mode?
168 bits
What is the correct length of the Skipjack key?
80 bits
What is the size of each key used in the key-bundle of the 3DES algorithm (excluding parity bits)?
56 bits
Which of the following is the least secure mode of the Data Encryption Standard?
Electronic Codebook mode
Which of the following is a set of rules used by computers to communicate with each other across a network?
Protocol
Which of the following algorithms
AES
If Nancy wishes
Private Key
If Matthew receives a digitally signed message from Nancy, which key should he
Nancy’s Public key
If Matthew wishes
Private Key
If Nancy receives a digitally signed message from Matthew, which key should she
Mathew’s public key
If Renee receives a digitally signed message from Mike, what key does she
Mike’s public key
Which of the following uses both a public and private key to encrypt and decrypt data?
Asymmetric Cryptography
Which of the following algorithms doubles the length of any message
El Gamal
How
SLE*ARO
What is the length of a message digest produced by the MD5 algorithm?
B. 128 bits
You are the security administrator of a large law firm.
Bell-
In what phase of the Capability Maturity Model for Software (SW-CMM) are quantitative measures
Managed
Wireless LAN connection
Remote access dial-up connection
WAN link
What is the Biba access control model primarily based upon?
Lattice
Which one of the following database backup techniques requires the greatest expenditure of funds?
Remote mirroring maintains a live database server at the remote site and comes at the highest cost
Which one of the following security modes does not require that a user have a valid security clearance for all information processed by the system?
In multilevel security mode, some users do not have a valid security clearance for all information processed by the system
You are the security administrator for an international shipping company.
What is the last phase of the TCP/IP three-way handshake sequence?
The SYN packet is first sent from the
Which of the following is a requirement of change management?
One
Which of the following is a procedure designed to test and perhaps bypass a system's security controls?
Penetration testing is the attempt to bypass security controls to test overall system security.
At which
Network hardware devices, including routers, function at layer 3, the Network layer
Not all instances of DoS
Audit trails, logs, CCTV, intrusion detection systems, antivirus software, penetration testing, password crackers, performance monitoring, and cyclic redundancy checks (CRCs) are examples of what?
Examples of detective controls are audit trails, logs, CCTV, intrusion detection systems, antivirus software, penetration testing, password crackers, performance monitoring, and CRCs.
What technology allows a computer to harness the power of
Multiprocessing computers use
What type of backup stores all files
Differential backups store all files that have
What type of detected incident allows the most time for an investigation?
Scanning incidents are
Auditing is a required factor to sustain and enforce what?
Auditing is a required factor to sustain and enforce accountability
Which type of firewall automatically adjusts its filtering rules based on the content of the traffic of existing sessions?
Dynamic packet-filtering firewalls enable real-time modification of the filtering rules based on traffic content
Which of the following is the principle that objects
Integrity
E-mail is the most common delivery vehicle for which of the following?
Malicious code
Worms
Viruses
What type of physical security controls are access controls, intrusion detection, alarms, CCTV, monitoring, HVAC, power supplies, and fire detection and suppression?
Technical
What is the first step of the Business Impact Assessment process?
Identification of priorities is the first step of the Business Impact Assessment process.
The "something you are" authentication factor
Type 3 authentication factor is something you are, such as fingerprints, voice print, retina pattern, iris pattern, face shape, palm topology, hand geometry, and so on.
What is the primary goal of risk management?
The primary goal of risk management is to reduce risk to an acceptable level
https://www.yeahhub.com/cissp/#answer
- Assessment Test Flashcards
Define and detail the aspects of password selection that distinguish good password choices from ultimately poor password choices.
Difficult to guess or unpredictable
Meet minimum length requirements
Meet specific complexity requirements
What type of malware uses social engineering to trick a victim into installing it?
A Trojan horse is
What kind of recovery facility enables an organization to resume operations as quickly as possible, if not immediately, upon failure of the primary facility?
Hot sites provide backup facilities maintained in constant working order and fully capable of taking over business operations.
Warm sites
Cold sites are
Which of the following represent natural events that can pose a threat or risk to an organization?
Natural events that can threaten organizations include earthquakes, floods, hurricanes, tornados, wildfires, and other acts of nature as well
Why are military and intelligence attacks among the most serious computer crimes?
The purpose of a military and intelligence attack is to acquire classified information. The detrimental effect of using such information could be nearly unlimited in the hands of an enemy. Attacks of this type
Which of the following is not a defense against collusion?
Group user accounts allow for multiple people to log in under a single user account. This allows collusion because it prevents individual accountability.
Which of the following are a defense against collusion?
Separation of duties
Restricted job responsibilities
Job rotation
Which of the following is not a composition theory related to security models?
Iterative is not one of the composition theories related to security models. Cascading, feedback, and hookup are the three composition theories
Which of the following statements is true?
The more complex a system, the less assurance it provides. More complexity means more areas for vulnerabilities to exist and more areas that must
System architecture, system integrity, covert channel analysis, trusted facility management, and trusted recovery are elements of what security criteria?
Assurance is
Which one of the following is a layer of the ring protection scheme that
Layers 1 and 2 contain device drivers but
Layer 0 always contains the security kernel.
Layer 3 contains user applications.
Why
It prevents any single security subject (
Which of the following is the least acceptable form of
Retina scan
Which of the following forms of authentication provides the strongest security?
Kerberos provides the security services of
confidentiality and integrity
What is the most important aspect of a biometric device?
Accuracy
A network environment that uses discretionary access controls is vulnerable to which?
Impersonation
What is the point of a secondary verification system?
To verify the correctness of a system
Biometric factor
Which of the following contains the primary goals and objectives of security?
The primary goals and objectives of security are confidentiality, integrity, and availability, commonly referred to as the CIA Triad.
Which of the following is a principle of the CIA Triad that means
Availability means that
Violations of confidentiality include capturing network traffic, stealing password files, social engineering, port scanning, shoulder surfing, eavesdropping, and sniffing.
https://www.brainscape.com/flashcards/assessment-test-4218413/packs/6347928
- Static routing is always preferred over dynamic routing protocols, because of the manual, trusted configuration and route stability.
https://webcache.googleusercontent.com/search?q=cache:qRIJRkp7P-kJ:https://apprize.best/security/cisco/5.html+&cd=1&hl=en&ct=clnk&gl=tr&client=firefox-b-d
- Dynamic routing is always preferred over static routing in a
mid-sized and large networking environment. The two classes
of dynamic routing protocols are distance-vector protocols
such as Routing Information Protocol (RIP) and Interior
Gateway Routing Protocol (IGRP), and link-state protocols such
as the Open Shortest Path First (OSPF) protocol and
Intermediate System to Intermediate System (IS-IS).
https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.129.3721&rep=rep1&type=pdf
- Specify the static route on the device to resolve and determine the packet’s next-hop interface using the Longest Match Routing Rule (most specific entry), sometimes referred to as the longest prefix match or maximum prefix length match. The Longest Match Routing Rule is an algorithm used by IP routers to select an entry from a routing table. The router uses the longest (prefix) match to determine the egress (outbound) interface and the address of the next device to which to send a packet. Typically, the static route prefers the directly connected subnet route for resolving the next hop rather than performing a longest prefix match with any other available routes.
https://www.juniper.net/documentation/us/en/software/junos/static-routing/topics/ref/statement/longest-match-next-hop-edit-static-routing-options.html
- What is static routing?
Network administrators use static routing, or nonadaptive routing, to define a route when there is a single route or a preferred route for traffic to reach a destination. Static routing uses small routing tables with only one entry for each destination. It also requires less computation time than dynamic routing because each route is preconfigured.
What is dynamic routing?
Dynamic routing, sometimes called adaptive routing, is more complex than static routing because it creates more possible routes to send packets across a network. Dynamic routes are typically used in larger, fluid networks where static routes would be cumbersome to maintain and frequently reconfigure. Because dynamic routing is more complicated, it consumes more bandwidth than static routing.
https://www.techtarget.com/searchnetworking/answer/Static-and-dynamic-routing
- Why is it that an ICMP packet does not have source and destination port number?
The ICMP packet does not have source and destination port numbers because it was designed to
communicate network-layer information between hosts and routers, not between application
layer processes. Each ICMP packet has a "Type" and a "Code". The Type/Code combination
identifies the specific message being received. Since the network software itself interprets all
ICMP messages, no port numbers are needed to direct the ICMP message to an application layer
process.
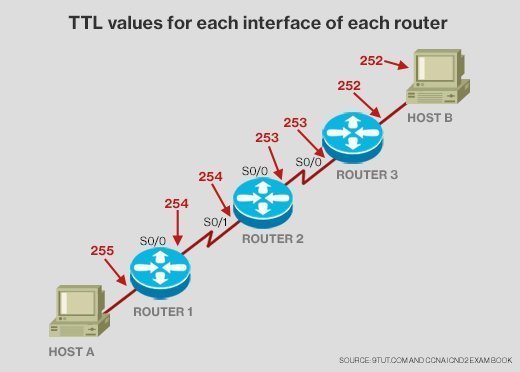










Hi There,
ReplyDeleteSuch vivid info on the How exactly does traceroute/tracert work at the protocol level? ! Flabbergasted! Thank you for making the read a smooth sail!
I am new to Linux, and I am hoping to have just a
leisurely conversation about switching from windows. I will find answers to specific questions hopefully with a search here, but I may still ask anyway.
Excellent tutorials - very easy to understand with all the details. I hope you will continue to provide more such tutorials.
Thank you,
Radhey