Firewall
A firewall can either be software-based or hardware-based and is used to help keep a network secure. Its primary objective is to control the incoming and outgoing network traffic by analyzing the data packets and determining whether it should be allowed through or not, based on a predetermined rule set
http://en.wikipedia.org/wiki/Firewall_(computing)
Firewall Stateful versus Stateless
state
snapshot, freeze frame in memory
context-sensitive
9.3 Understanding Stateful vs Stateless Inspection
statefull firewalls, OSI layer 3,4,5
keeps track of the state of the connection
UDP connectionless
state references TCP state
most common deployed firewalls
state table; source,destination,port,sequencing,flag
state table processed by ACL
limitations; udp,icmp etc protocols do not contain state information
- STATELESS Firewalls
STATEFUL Firewall
Stateful firewalls can watch traffic streams from end to end. They are aware of communication paths and can implement various IP Security (IPsec) functions such as tunnels and encryption. In technical terms, this means that stateful firewalls can tell what stage a TCP connection is in (open, open sent, synchronized, synchronization acknowledge or established). It can tell if the MTU has changed and whether packets have fragmented. etc.
https://www.cybrary.it/0p3n/stateful-vs-stateless-firewalls/
- A stateful firewall is capable of tracking connection states, it is better equipped to allow or deny traffic based on such knowledge. A TCP connection for example goes through the handshake (SYN-SYN+ACK-SYN), to EASTABLISHED state, and finally is CLOSED. A stateful firewall can detect these states. If a packet belongs to an already running flow it can be allowed, while a new connection form the untrusted host can be dropped.
When to use Stateless firewall?
A stateless firewall can be a faster and less resource intensive alternative in the following cases
Server side firewall: If you are running a purely server application with well-known ports on a machine. In this case firewall can be explicitly programmed to allow connection to and from the server port. As the server ports are well known to the firewall and the server expects new connection anyway, stateless firewalls can handle this use case.
Client side firewall: A client program which strictly connect to a small set of trusted hosts (internal) can be protected using stateless firewalls with specific rules
https://chandanduttachowdhury.wordpress.com/2018/03/25/stateful-vs-stateless-firewalls-which-one-to-use-when/
- When an IP session, for instance on the TCP protocol, is initiated, and the connection is authorised - let's assume, an HTTP connection from an internal network towards an external web site on port 80 - the firewall will keep track of who has started the connection and to which destination, will inspect and understand the information exchanged inside the communication, and will open other ports accordingly to allow the connection to be instantiated and maintained - for instance, the firewall has to accept the acknowledge packet from the server, and to do that, it has to allow the reply happening on a certain port from the server back to the client, maybe perform the NAT/P (Network and Port Address Translation) down to the client (if it was placed for instance in a private range addressing). This network opening happens "on the fly" in the firewall, as normally the same packet would not be allowed from external to internal, if the session was not initiated from the internal
As opposed to stateful firewalls, stateless have no such capabilities. They only basically keep a list of ports that are allowed or not, and are not able to adjust them dynamically depending on the protocol involved. This means for instance that in the case of a client on an internal network connecting to an FTP server on an outside network, you would need to allow the outgoing FTP port from client to server, and then a range of high ports (for "high" ports it is meant any port > 1024) connecting between the client and the server; the stateless firewall cannot open the high port on the fly, and therefore you need to keep all the ports that can be possibly negotiated open all the time, which of course exposes your surface to many more risks
Stateless firewalls are basically ACL (Access Control List) based, that is, they are the software that often provides ACLs on routers.
Stateless filtering is still used in certain cases, especially in WAN networking
For instance, let's assume you need to allow a third party to connect to your corporate network via VPN, and you are using router as a site-to-site VPN terminator; this router does not support stateful filtering, and you cannot afford for any reason to install a proper stateful firewall, but you still want to somehow limit the access this external company has to your network - I am aware it is not really a secure filtering, but ACLs can be better than nothing.
let's assume you have Cisco routers which do not support stateful filters, but you still want to apply some security - for instance on WAN or links. Routers and other equipment are used as WAN network hops or BGP routers to direct Internet traffic; generally, you cannot afford installing a firewall in front of every Internet-exposed router, and therefore you would limit filtering to simple ACLs (for instance allowing ICMP packets on the public interface and management only to the internal interface)
https://www.quora.com/What-is-the-difference-between-stateful-and-stateless-firewalls-Are-there-different-applications-for-each
- A Next-Generation Firewall (NGFW) is an integrated network platform that is a part of the third generation of firewall technology, combining a traditional firewall with other network device filtering functionalities, such as an application firewall using in-line deep packet inspection (DPI), an intrusion prevention system (IPS).
Other techniques might also be employed , such as TLS/SSL encrypted traffic inspection, website filtering, QoS/bandwidth management, antivirus inspection and third-party identity management integration
- Next-Generation IPS
https://f5.com/solutions/enterprise/reference-architectures/next-generation-ips
- Cisco Firepower Next-Generation IPS (NGIPS) threat appliances combine superior visibility, embedded security intelligence, automated analysis, and industry-leading threat effectiveness
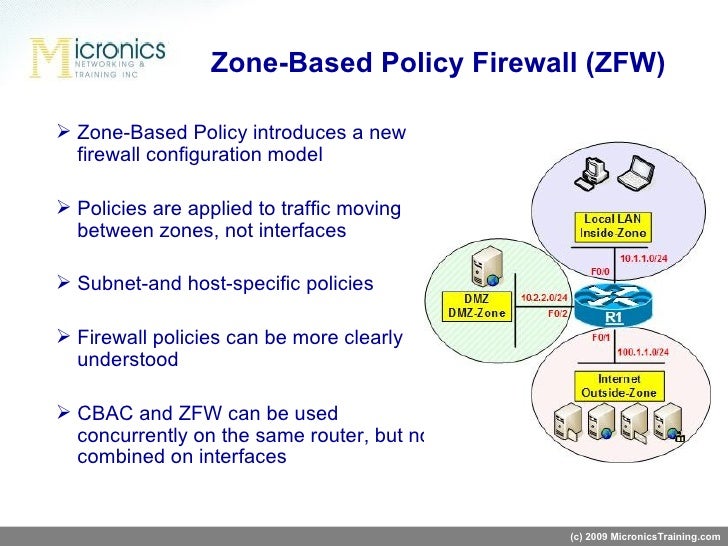
Two important terms used in Cisco IOS Zone Based Firewall terminology are Zones and Zone Pairs
zones can be created in IOS and then the router interfaces can be assigned to specific zones. Network traffic between zone interfaces is controlled by zone policy.
http://www.omnisecu.com/ccna-security/what-are-zones-and-zone-pairs.php
the basic config and options of Cisco IOS zone based firewall using the Topology below Grab the initial configs and GNS3
https://www.m00nie.com/2011/03/simple-zone-based-ios-firewall-gns3-lab/
Configuring the Zone-Based Firewall
A Zone-Based Firewall assigns each interface to a specific zone. The firewall zones will be used to define what traffic is allowed to flow between the interfaces. The traffic that originates in the EdgeRouter itself will also be assigned to a zone: the local zone.
https://help.ubnt.com/hc/en-us/articles/204952154-EdgeRouter-Zone-Based-Firewall
Zone Based Firewall Configuration Example
Zone Based Firewall is the most advanced method of a stateful firewall that is available on Cisco IOS routers. The idea behind ZBF is that we don’t assign access-lists to interfaces but we will create different zones. Interfaces will be assigned to the different zones and security policies will be assigned to traffic between zones.
https://networklessons.com/cisco/ccie-routing-switching/zone-based-firewall-configuration-example
- Next-Generation Intrusion
https://www.trendmicro.com/en_us/business/products/network/integrated-atp/next-gen-intrusion-prevention-system.html
- Forefront Unified Access Gateway (UAG)
https://technet.microsoft.com/en-us/library/ff358694.aspx
- Unified threat management (UTM) or unified security management (USM), is a solution in the network security industry, and since 2004 it has gained currency as a primary network gateway defense solution for organizations.
[ 1] In theory, UTM is the evolution of the traditional firewall into an all-inclusive security product able to perform multiple security functions within onesingle system: networkfirewalling , network intrusion prevention and gateway antivirus (AV), gateway anti-spam, VPN, content filtering, load balancing, data loss prevention, and on-appliance reporting.
https://en.wikipedia.org/wiki/Unified_threat_management
- First, BIG-IP AFM offers high-speed, application-aware firewall rules that allow security personnel to manage their layer 4 network. Second, BIG-IP AFM
is aware of 38 types of DDoS attacks and automatically alerts and mitigates them (organizations can further define their own DDoS scenarios). Finally, BIG-IP AFM offers, for the first time, granular visibility and logging at the application level, allowing organizationsto slowly begin to deprecate their zone abstractions and provide instrumentation directly to the individual application teams
- What is a UTM Firewall?
In the early days of network security, a firewall merely filtered traffic based on ports & IP addresses. Over time, firewalls continued to evolve by keeping track of the state of network connections passing through the appliance, which we call "stateful."
organizations deployed multiple appliances, each with differing roles to defend against different classes of attacks
A stateful packet inspection firewall allowed inbound & outbound traffic on the network
An additional web proxy filtered content & URLs while scanning with antivirus services
A separate Intrusion Prevention System (IPS) was often deployed to detect & block malicious traffic
An appliance was needed for spam filtering to filter junk emails & phishing attempts
VPN servers connected remote offices or allowed remote users to access company resources
UTM firewalls could now collocate multiple security services into one appliance, providing robust network protection against a plurality of attack types
Benefits that UTM provided
UTM firewalls protected inbound & outbound traffic from a multitude of threats & attack types
Antivirus, anti-malware, & anti-spyware services could run concurrently to prevent attacks at the gateway
Integrated Intrusion Prevention blocked the exploit of vulnerabilities
Email filtering blocked unwanted emails like spam & email-borne threats
Web sites & web content could be filtered & monitored from the same central command dashboard
Control & visibility over traffic flows improved with Quality of Service enhancements & bandwidth management
Working remotely became more convenient with the ability to connect easily to remote locations with a site-to-site VPN
Simplification of complex networks allowed for dynamic routing, policy-based routing, & multiple Internet connections on a single secure network
On to the Next Generation
The most current iteration of firewall appliances are referred to as Next Generation Firewalls, or NGFWs.
This current generation saw major improvements in the coordination & communication between the multiple services that UTM firewalls consolidated. Artificial intelligence, machine learning, & automation began to feature in these cutting-edge services, allowing for improvements in threat intelligence & response times that a human administrator alone could not reach.manufacturers heavily emphasized "Single-Pane-Of-Glass" (SPOG) management platforms in which all relevant dashboards & interfaces could be viewed & interacted with through a single portal or page, removing the need to bounce around multiple tabs while managing a network
Benefits that NGFWs provide
Real-time, automated communication between services allows for devices to be isolated & quarantined after an incident until IT can respond
Cloud-based sandboxing technology allows for the quarantine & detonation of potentially harmful files
Everything from NAT policies, content filtering, user groups, access control lists, Wi-Fi, & more can be managed through a single screen
Emphasis is placed on maintaining network performance even with multiple complex security services operating in tandem
Integrated Intrusion Prevention with deep packet scanning
Ability to identity & control hosted & cloud-based applications
https://www.firewalls.com/what_is_utm_firewall
- How does a firewall work?
It can permit or block any port number, web application, and network-layer protocols based on configuration.
Common ports:
80 HTTP
443 HTTPS
20 & 21 FTP
23 Telnet
22 SSH
25 SMTP
- What are the types of firewalls?
The National Institute of Standards and Technology (NIST), an organization from the US, divides firewalls into three basic types: Packet filters, Stateful inspection, and Proxy.
Packet filters permit or block packets based on port number, protocols source, and destination address.
Stateful inspection works on the principle of the state of active connections between client and server. It uses state information to allow or block network traffic.
Proxy firewall combines stateful inspection technology to enable deep packet inspection. Here, the firewall act as a proxy; a client makes a connection with the firewall, and then the firewall makes a separate connection to the server on behalf of the client.
- What is source-routed traffic and why is it a threat?
It allows a sender of a packet to partially or completely specify the route the packet takes through the network.
Generally, the router decides the route from destination to source.
If source-routed traffic allows through the firewall, an attacker can generate traffic claiming to be from a system "inside'' the firewall. In general, such traffic wouldn’t route to the firewall properly, but with the source routing option, all the routers between the attacker's machine and the target will return traffic along the source route's reverse path
Most commercial routers incorporate the ability to block source routing specifically, and many versions of Unix that might be used to build firewall bastion hosts have the ability to disable or to ignore source routed traffic.
Source Routed Packets
Drop Source Routed IP Packets - (Enabled by default.) Clear this checkbox if you are testing traffic between two specific hosts and you are using source routing.
IP Source Routing is a standard option in IP that allows the sender of a packet to specify some or all of the routers that should be used to get the packet to its destination.
This IP option is typically blocked from use as it can be used by an eavesdropper to receive packets by inserting an option to send packets from A to B via router C. The routing table should control the path that a packet takes, so that it is not overridden by the sender or a downstream router.
How Does Source Routing Work?
In the Internet Protocol (IPv4), there are built-in header options for a sender of a packet to force the path instead of taking the normal best possible routing implemented by every routing protocol. Specifically, the rarely used Strict Source Route (SSR) and Loose Source Route (LSR) header options are what enables source routing mechanism. In the IPv6, the header that allows for source routing is called Type o Routing (RHo).
In the IPv4, a partial or complete list of nodes on the network can be determined by using the LSR and SSR fields respectively. In this case, node address list can not be greater than 40 bytes long, that is the size maximum size of IPv4 option part of header. This allows for defining 9 routing nodes at most for IPv4 networks.
In IPv6 on the other hand, source routing is implemented in an extension header which is not limited in size. Assuming packet fragmentation is not allowed, IPv6 extension header size will be limited only by the maximum size of a packet defined by TCP MTU (Maximum Transmission Unit). In this case 90 routing nodes can be defined inside a packet where the MTU is 1500 bytes.
source routing is not considered secure and as suggested by IETF, it needs to be disabled by default on networking devices and on operating system
Attack 1: Information Gathering
Even if source routing is not allowed on a network, an attacker can send an IP packet and use the ICMP (Internet Control Message Protocol) response to get information (E.g., operating system) about the target computer or network device. For this reason, the default configuration should be to drop IP source route packets in order to prevent leaking information about the network devices and their configuration.
Attack 2: Network Topology Discovery
Source routing can be used by attackers to probe the network by forcing packets into specific parts of the network.
Attack 3: IP Spoofing
LSR can allow an attacker to spoof an address and successfully receive response packets by forcing return traffic for spoofed packets to pass through the attacker’s device. For this reason, packets marked as LSR are usually blocked on the Internet.
Attack 4: Bypass Security Measures
Attack 5: Network Congestion (DoS)
in IPv6, source routing is implemented in an extension header which is not limited in size. Depending on the the IPv6 configuration, this can allow an attacker to define 90 nodes or more to force packets to pass through on the network. This could lead an attacker with limited upload link to congest the network significantly, resulting in DoS (Denial of Service).
https://cybersophia.net/articles/what-is/what-is-source-routing/
http://dev.fyicenter.com/Interview-Questions/Computer-Security-2/What_is_source_routed_traffic_and_why_is_it_a_th.html
http://help.sonicwall.com/help/sw/eng/9510/26/2/3/content/Firewall_Advanced.070.3.htm


No comments:
Post a Comment