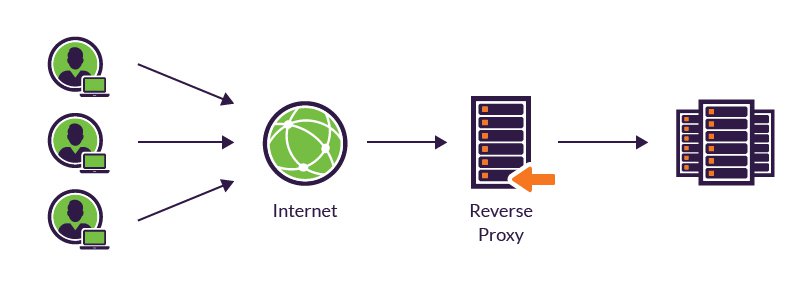
- reverse proxy
a reverse proxy is a
While a forward proxy acts as an intermediary for its (usually nearby) associated client
for its (usually nearby) associated server
Uses of reverse proxies
Reverse proxies can hide the existence and characteristics of an origin server or servers.
Application firewall features can protect against common web-based attacks. Without a reverse proxy, removing malware or
A reverse proxy can distribute the load from incoming requests to several servers, with each server serving its own application area.
A reverse proxy can reduce load on its origin servers by caching static content,
A reverse proxy can optimize content by compressing it
Reverse proxies can operate whenever multiple web-servers must be accessible via a single public IP address. The web servers listen on different ports in the same machine, with the same local IP address or, possibly, on different machines and different local IP addresses altogether. The reverse proxy analyzes each incoming request and delivers it to the right server within the local area network.
http://en.wikipedia.org/wiki/Reverse_proxy
Proxy vs. Reverse Proxy (Explained by Example)
- gateway proxy
HTTP gateway proxy is a server-side Java (Java EE) -based non-transparent intercepting web proxy. The main function of the proxy is to act as a controlled proxy between the client and a web service (gateway) based on the hypertext transfer protocol (HTTP). The non-transparency hides the real gateway that
http://www.slotteconsulting.com/en/solutions-and-utilities/HTTP_gateway_proxy/
- Squid is a caching proxy for the Web supporting HTTP, HTTPS, FTP, and more. It reduces bandwidth and improves response times by caching and reusing
frequently-requested web pages
- Varnish Cache is a web application accelerator also known as a caching HTTP reverse proxy. You install it in front of any server that speaks HTTP and configures it to cache the contents. Varnish Cache is really,
really fast.
- NGINX
accelerates content and application delivery, improves security, facilitates availability and scalability for the busiest websites on the Internet
-
HAProxy is a free,very fast and reliable solution offering high availability, load balancing, andproxying for TCP and HTTP-based applications. Itis particularly suited for web sites crawling undervery high loads while needing persistence or Layer7 processing
http://haproxy.1wt.eu/
HAProxy is a free,very fast and reliable solution offering high availability, load balancing, andproxying for TCP and HTTP-based applications
How Keep-Alive works:
Keep-alive provides the following Advantages:
Reducing latency in subsequent requests.
Faster data retrieval as the TCP connection stays open after
Minimising the chance of
Errors being reported without the need of closing the TCP connection.
No need for additional handshakes after
https://www.fastcomet.com/tutorials/gtmetrix/enable-keep-alive
- Create the
Keepalived Configuration File
on your primary server, create the main
we will open a block called
We will start off by telling
Since we are configuring our primary server, we will set the state configuration to "MASTER".
https://www.digitalocean.com/community/tutorials/how-to-set-up-highly-available-web-servers-with-keepalived-and-floating-ips-on-ubuntu-14-04
usefull if you use virtual ips.
2 virtual IPs one is on the first load balancer and the other is on the second
The common solution is to listen on 0.0.0.0
it not always practical
The solution is a
put this in /etc/
https://sebest.github.io/post/linux-how-to-bind-ip-that-doesn-t-exist-yet/
Keepalived is used for IP failover between two servers. Its facilities for load balancing and high-availability to Linux-based infrastructures. It worked on VRRP (Virtual Router Redundancy Protocol) protocol.
2.
3. By default single
https://tecadmin.net/setup-ip-failover-on-ubuntu-with-keepalived/
- The active (master) router informs the backup routers of its active status using the Virtual Router Redundancy Protocol (VRRP)
the active router is using Network Address Translation or NAT to direct traffic from the Internet to a variable number of real servers on the second
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/load_balancer_administration/ch-keepalived-overview-vsa
- In order for the
Keepalived service to forward network packets properly to the real servers, each router node must have IP forwarding turned on in the kernel
The changes take effect when you reboot the system.
To check if
/
To check if
/
If both the above commands return a 1, then the respective settings
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/load_balancer_administration/s1-initial-setup-forwarding-vsa
vrrp_script
Defines a virtual server group, which allows a real server to be a member of several virtual server groups.
Defines a virtual server for load balancing,
https://docs.oracle.com/cd/E37670_01/E41138/html/section_wv3_hjn_pr.html
- Configuring Simple Virtual IP Address
Failover UsingKeepalived
The default advertisement interval is one second. If the backup nodes
If several backup servers have the same priority, the backup server with the highest IP address value becomes the master server.
Only one server should be active as the master
https://docs.oracle.com/cd/E37670_01/E41138/html/section_uxg_lzh_nr.html
- High availability refers to a system or component that is continuously operational for a desirably long length of time
The
https://vexxhost.com/resources/tutorials/highly-available-web-servers-keepalived-floating-ips-ubuntu-16-04/
Keepalived is a routing software written in C. The main goal of this project is to provide simple and robust facilities forloadbalancing and high-availability to Linux system and Linux based infrastructures.Loadbalancing framework relies on well-known and widely used Linux Virtual Server (IPVS) kernel module providing Layer4loadbalancing .Keepalived implements a set of checkers to dynamically and adaptively maintain and manageloadbalanced server pool according their health.On the other hand high -availabilityis achieved by VRRP protocol. VRRP is a fundamental brick for router failover. In addition,Keepalived implements a set of hooks to the VRRP finite state machine providing low-level and high-speed protocol interactions.Keepalived frameworks canbe used independently or all together to provide resilient infrastructures.
- Configuring
Keepalived for Session Persistence and Firewall Marks
If you enable the load balancer in
Firewall marks are another method for controlling session access so that
https://docs.oracle.com/cd/E37670_01/E41138/html/section_g5j_4lf_qr.html
No comments:
Post a Comment