- Docker a container system making use of LXC containers
- Docker is an open-source project that automates the deployment of applications inside software containers, by providing an additional layer of abstraction and automation of operating-system-level virtualization on Linux, Mac OS and Windows.
Build, Ship, and Run Any App, Anywhere
http://www.docker.com
- The Registry is a stateless, highly scalable server-side application that stores and lets you distribute Docker images. The Registry is
open -source, under the permissive Apache license.
You should use the Registry if you want to: - both ENTRYPOINT and CMD give you a way to identify
which executable should be run is started
In fact, if you want your image to be - An ENTRYPOINT helps you to configure a container that you can run as an executable.
-
It is generally recommended
It’s ok to have multiple processes but to get the most benefit out of Docker, avoid one container being responsible for multiple aspects of your overall application. You can connect multiple containers using user-defined networks and shared volumes. - By default, Docker containers are “unprivileged” and cannot, for example, run a Docker daemon inside a Docker container. This is because by default a container
is not allowed to is given
https://docs.docker.com/engine/reference/run/#runtime-privilege-and- - Docker is a platform that sits between apps and infrastructure. By building apps on Docker, developers and IT operations get freedom and flexibility. That’s because Docker runs everywhere that enterprises deploy apps: on-
prem is containerized prem - The architecture of a Docker container includes a physical machine with a host operating system. On top of the host operating system, a Docker engine
is deployed applications can be deployed as well as - By default, when you launch a container, you will also use a shell command
- Docker Hub is a registry service on the cloud that allows you to download Docker images that
are built - we can use the CentOS image available in Docker Hub to run CentOS on our Ubuntu machine https://www.tutorialspoint.com/docker/docker_images.htm
- In our example, we
are going to
https://www.tutorialspoint.com/docker/building_web_server_docker_file.htm - Docker also gives you the capability to create your own Docker images, and it can
be done
A Docker File is a simple text file with instructions on how to build your images. - You might
have the
You may not want to host the repositories on Docker Hub. For this, there is a repository container itself from Docker. - In Docker, the containers themselves can have applications running on ports. When you run a container, if you want to access the application in the container via a port number, you need to map the port number of the container to the port number of the Docker host. https://www.tutorialspoint.com/docker/docker_managing_ports.htm
sudo docker run -p 8080:8080 -p 50000:50000jenkins
The left-hand side of the port number mapping is the Docker host port to map to and the right-hand side is the Docker container port number.- You might have a Web Server and a Database Server. When we talk about linking Docker Containers, what we are talking about here is
- By linking containers, you provide a secure channel via which Docker containers can communicate with each other. This is a generic and portable way of linking the containers together rather than via the networking port that we saw earlier in the series
- One of the
many in be accessed -- any number of docker containers without the need to expose container's internal ports to the outside world.
https://linuxconfig.org/basic-example-on-how-to-link-docker-containers - NGINX is a popular lightweight web application that
is used
#This is a - In Docker, you have a separate volume that can
be shared These are known Some of the - Docker takes care of the networking aspects so that the containers can communicate with other containers and also with the Docker Host. If you do an
- The Docker server creates and configures the host system’s docker0 interface as an Ethernet bridge inside the Linux kernel that could
be used - the basics of creating your own custom Docker spins. you can roll your own from your favorite Linux distribution
- Create a simple parent image using scratch
- 2. Creating Base Image using Scratch In the Docker registry, there is a special repository known as Scratch, which
- Create a base image
- An image developer can define image defaults related to:
- Detached (-d)
- Foreground
- If you would like to keep your container running in detached mode, you need to run something in the foreground.
Kitematic Kitematic Kitematic VirtualBox - Docker Flow is a project aimed towards creating an easy to use continuous deployment flow. It depends on Docker Engine, Docker Compose, Consul, and
Registrator is proven are recommended
https://technologyconversations.com/2016/04/18/docker-flow/ Portainer to easily manage
https://hub.docker.com/r/portainer/portainer/- Docker in Docker
( Dind
Docker in Docker - “Play with Docker
”
The application - Although running Docker inside Docker (
DinD DooD is generally not recommended
http://blog.teracy.com/2017/09/11/how-to-use-docker-in-docker-dind-and-docker-outside-of-docker-dood-for-local-ci-testing/
tightly control where your images are being stored
fully own your images distribution pipeline
integrate image storage and distribution tightly into your in-house development workflow
https://docs.docker.com/registry/
Combining ENTRYPOINT and CMD allows you to specify the default executable for your image while also providing default arguments to that executable which may
https://www.ctl.io/developers/blog/post/dockerfile-entrypoint-vs-cmd/
- The ENTRYPOINT specifies a command that will always
- ENTRYPOINT: command to run when container starts.
- The main purpose of a CMD is to provide defaults for an executing container.
- The CMD specifies arguments that will
- CMD: command to run when container starts or arguments to ENTRYPOINT if specified.
- CMD sets default command and/or parameters, which can
- Both CMD and ENTRYPOINT instructions define what command gets executed when running a container. There are few rules that describe their co-operation.
- Dockerfile should specify at least one of CMD or ENTRYPOINT commands
- https://stackoverflow.com/questions/21553353/what-is-the-difference-between-cmd-and-entrypoint-in-a-dockerfile
If you need to run
Put all of your commands in a wrapper script, complete with testing and debugging information. Run the wrapper script as your CMD.
Use a process manager like
https://docs.docker.com/config/containers/multi-service_container/
In hypervisor-based application virtualization, a virtualization platform (for example Hyper-V or
http://www.networkcomputing.com/data-centers/docker-containers-9-fundamental-facts/1537300193
We used this command to create a new container and then used the Ctrl+P+Q command to exit out of the container. It ensures that the container still exists even after we exit from the container
We can verify that the container still exists with the Docker ps command.
There is an easier way to attach to containers and exit them cleanly without the need of destroying them.
https://www.tutorialspoint.com/docker/docker_containers_and_shells.htm
https://www.tutorialspoint.com/docker/docker_hub.htm
Step 1 − Create a file called Docker File and edit it using vim. Please note that the name of the file has to be "Dockerfile" with "D" as capital.
Step 2 − Build your Docker File using the following instructions.
#This is a sample Image
FROM ubuntu
MAINTAINER demousr@gmail.com
RUN apt-get update
RUN apt-get install
CMD [
https://www.tutorialspoint.com/docker/docker_file.htm
Registry is the container managed by Docker
https://www.tutorialspoint.com/docker/docker_private_registries.htm
The output of the
https://www.tutorialspoint.com/docker/docker_managing_ports.htm
We can launch one Docker container that will
We will launch the second Docker container (Web Server) with a link flag to the container launched in Step 1. This way, it will
This is a generic and portable way of linking the containers together rather than via the networking port that we saw earlier in the series
Check out Docker Compose, which provides a mechanism to do the linking but by specifying the containers and their links in a single file
https://rominirani.com/docker-tutorial-series-part-8-linking-containers-69a4e5bf50fb
https://rominirani.com/docker-tutorial-series-part-8-linking-containers-69a4e5bf50fb
FROM ubuntu
MAINTAINER pumpkin@gmail.com
RUN apt-get update
RUN apt-get install
CMD [
They can
Any changes to the volume itself can
They exist even after the container
Now suppose you wanted to map the volume in the container to a local volume
https://www.tutorialspoint.com/docker/docker_storage.htm
This is a bridge between the Docker Host and the Linux Host
One can create a network in Docker before launching containers
You can now attach the new network when launching the container.
https://www.tutorialspoint.com/docker/docker_networking.htm
The docker0 bridge is
https://developer.ibm.com/recipes/tutorials/networking-your-docker-containers-using-docker0-bridge/
because running Linux inside a container
simple setup that installs and starts a barebones Apache server into the official Ubuntu image
https://www.
You can use Docker’s reserved,
https://docs.docker.com/develop/develop-images/baseimages/#create-a-full-image-using-tar
https://linoxide.com/linux-how-to/2-ways-create-docker-base-image/
A parent image is an image that
A base image either has no FROM
Create a full image using tar
There are more example scripts for creating parent images in the Docker GitHub Repo:
CentOS / Scientific Linux CERN (SLC) on Debian/Ubuntu or on CentOS/RHEL/SLC/etc.
Debian / Ubuntu
Note: Because Docker for Mac and Docker for Windows use a Linux VM, you need a Linux binary, rather than a Mac or Windows binary. You can use a Docker container to build it:
https://docs.docker.com/develop/develop-images/baseimages/
detached or foreground running
container identification
network settings
runtime constraints on CPU and memory
Detached vs foreground
When starting a Docker container, you must first decide if you want to run the container in the background in a “detached” mode or in the default foreground mode:
To start a container in detached mode, you use -
https://docs.docker.com/engine/reference/run/#general-form
To start a container in detached mode, you use -
Do not pass a service x start command to a detached container. For example, this command attempts to start the
$
This
To
To reattach to a detached container, use
https://docs.docker.com/engine/reference/run/#detached
In foreground mode (the default
https://docs.docker.com/engine/reference/run/#foreground
An easy way to do this is to tail the /dev/null device as the CMD or ENTRYPOINT command of your Docker image.
CMD tail -
Docker containers, when running in detached mode (the most common -d option),
http://bigdatums.net/2017/11/07/how-to-keep-docker-containers-running/
https://docs.docker.com/kitematic/userguide/#overview
Following are the two primary scenarios where Dind can
Folks developing and testing Docker need Docker as a Container for faster turnaround time.
Ability to create multiple Docker hosts with less overhead. “Play with Docker” falls in this scenario.
For Continuous integration
The primary purpose of Docker-in-Docker was to help with the development of Docker itself
Now this container will have access to the Docker socket, and therefore will
https://jpetazzo.github.io/2015/09/03/do-not-use-docker-in-docker-for-ci/
“Play with Docker” can also
https://sreeninet.
- Images: The filesystem and metadata needed to run containers.
- The goal is to offer a distro and vendor-neutral environment for the development of Linux container technologies.
- Containers do not launch a separate OS for each application, but share the host kernel while maintaining the isolation of resources and processes where required
" - Basically, a container encapsulates applications and defines their interface to the surrounding system, which should make it simpler to drop applications into VMs running Docker in different clouds.
Simply put IaaS be used in conjunction added benefits—for Docker containers can be created
Docker containers are - Docker containers wrap a piece of software in a complete filesystem that contains everything needed to run: code, runtime, system tools, system libraries – anything that can
be installed
COMPARING CONTAINERS AND VIRTUAL MACHINES
The metadata includes defaults for the command to run, environment variables, labels, and health check command.
Containers:
An instance of an isolated application.
A container needs the image to define its initial state and uses the read-only filesystem from the image along with a container specific read-write filesystem.
A running container is a wrapper around a running process, giving that process
References:
To the docker engine, an image is just an image id. This is a unique immutable hash. A change to an image results in creating a new image id. However, you can have one or more references pointing to an image id, not unlike symbolic links
https://stackoverflow.com/questions/21498832/in-docker-whats-the-difference-between-a-container-and-an-image
Our main focus possible as the one you'd get from a VM but without the overhead that comes with running a separate kernel and simulating all the hardware.
This is achieved namespaces
https://linuxcontainers.org/
https://linuxcontainers.org/
In a virtual machine, you'll find a full operating system install with the associated overhead of virtualized device drivers, memory management, etc., while containers use and share the OS and device drivers of the host. Containers are therefore smaller than VMs, start up much faster, and have better performance, however, this comes at the expense of less isolation and greater compatibility requirements due to host’s
The right way to think about Docker is thus to view each container as an encapsulation of one program with all its dependencies. The container canbe dropped
The right way to think about Docker is thus to view each container as an encapsulation of one program with all its dependencies. The container can
Though
Docker replaced LXC with its own
https://www.upguard.com/articles/docker-vs.-vmware-how-do-they-stack-up
VIRTUAL MACHINES
Virtual machines include the application, the
CONTAINERS
Containers include the application and all of its dependencies
https://www.docker.com/what-docker
- Docker vs. VMs? Combining Both for Cloud Portability Nirvana Docker and container technology
- Docker is an open source application deployment container that evolved from the
LinuX .
http://www.bogotobogo.com/DevOps/Docker/Docker_Container_vs_Virtual_Machine.php
http://www.rightscale.com/blog/cloud-management-best-practices/docker-vs-vms-combining-both-cloud-portability-nirvana
- Linux Containers: System-wide changes are visible in each container. For example, if you upgrade an application on the host machine, this change will apply to all sandboxes that run instances of this application.
- KVM virtualization KVM virtualization lets you boot full operating systems of different
https://stackoverflow.com/questions/20578039/difference-between-kvm-and-lxc
LXC - Linux Containers
Containers are a lightweight alternative to full machine virtualization offering lower overhead
LXC is an operating-system-level virtualization environment for running multiple isolated Linux systems on a single Linux control host.
LXC works as
It share the kernel hypervisors and you can't customize it or load new modules.
Areas of application for the different technologies
KVM
Rendering, VPN, Routing, Gaming
Systems that require an own running kernel
Windows or BSD O.S.
LXC
Websites, Web Hosting, DB Intensive or
local Application Development
- Why KVM?
XEN allows
A Note About
A Note About QEMU
QEMU is a processor emulator that relies on dynamic binary translation to achieve a reasonable speed while being easy to
A Note About
Para-virtualized drivers enhance the performance of fully virtualized guests. With the para-virtualized drivers
https://www.cyberciti.biz/faq/centos-rhel-linux-kvm-virtulization-tutorial
- QEMU What is QEMU? QEMU is a generic and open source machine emulator and
- QEMU - Wikipedia QEMU is a free and open-source hosted hypervisor that performs hardware virtualization QEMU is a hosted virtual machine monitor: it emulates
https://www.qemu.org/
https://en.wikipedia.org/wiki/QEMU
- Linux Containers Compared to KVM Virtualization The main difference between the KVM virtualization and Linux Containers is that virtual machines require a separate kernel instance to run on, while
LinuX
https://wiki.archlinux.org/index.php/Linux_Containers
KVM virtualization
Virtual machines are
Guest virtual machine
- Linux containers (LXC), is an open source, lightweight operating system-level virtualization software that helps us to run a multiple isolated Linux systems (containers) on a single Linux host. LXC provides a Linux environment as close as to a standard Linux installation but
without the need for the VMware ,VirtualBox , and KVM, but it is good enough to provide an isolated environment that has its own CPU, memory, block I/O, network.
https://www.itzgeek.com/how-tos/linux/ubuntu-how-tos/setup-linux-container-with-lxc-on-ubuntu-16-04-14-04.html
- LXC To understand
- What is LXC? LXC is
- LXD is a container hypervisor providing a ReST API to manage LXC containers. https://tutorials.ubuntu.com/tutorial/tutorial-setting-up-lxd-1604#0
- LXD, pronounced Lex-Dee, is an expansion of LXC, the Linux container
tecnology behind Docker. Specifically, according toStéphane Graber, an Ubuntu project engineer, LXD is a" daemon exporting an authenticated representational state transfer application programming interface (REST API) both locally over a unix socket and over the network usinghttps . There are then two clients for this daemon, one is an OpenStack plugin, the other a standalonecommand line tool. main features are to include: linuxcontainers . org is the umbrella project behind LXC, LXD and LXCFS.
The goal is to offer a distro and vendor neutral environment for the development of Linux container technologies.- The relationship between LXD and LXC LXD works
- With the Docker vs LXC discussion, we have to take into account IT operations including dev and test environments. While BSD jails have focused on IT Operations, Docker has focused on the development and test organizations. A simple way to package and deliver applications and all their dependencies, one that enables seamless application portability and mobility.
LXC—short for “Linux containers”, is a solution for virtualizing software at the operating system level within the Linux kernel
LXC lets you run single applications in virtual environments, although you can also virtualize an entire operating system inside an LXC container if you’d like.
LXC’s main advantages include making it easy to control a virtual environment using
If you’re thinking
LXD
It’
The more technical way to define LXD is to describe it as a REST API that connects to
LXD, which
LXD offers advanced features not available from LXC, including live container migration and the ability to snapshot a running container.
LXC+LXD vs. Docker/CoreOS
LXD
https://www.sumologic.com/blog/code/lxc-lxd-explaining-linux-containers/
What is LXD?
LXD isn't a rewrite of LXC, in fact it's building on top of LXC to provide a new, better user experience. Under the hood, LXD uses LXC through
https://stackshare.io/stackups/lxc-vs-lxd
Secure by default (unprivileged containers
Image based workflow (no more locally built
Support for online
Live migration support
Shell command control
You can run Docker inside LXD technology.
We see LXD as being complementary with Docker, not a replacement.
"With Xen or KVM you create a space in memory where you emulate a PC and then you install the kernel and the operating system.
There's only one kernel, the host kernel. instead of running another kernel in memory space, you just run say a CentOS file system.
So while LXD will take up more resources than a pure container, it won't take up as much memory room as a VM approach.
In addition, an LXD container will have access to the resources and speed of the hardware without a VM's need to emulate hardware.
http://www.zdnet.com/article/ubuntu-lxd-not-a-docker-replacement-a-docker-enhancement/
Our
LXC is the well known set of tools, templates, library and language bindings. It's
LXD is the new LXC experience. It offers a
LXCFS
https://linuxcontainers.org/
https://blog.scottlowe.org/2015/05/06/quick-intro-lxd/
Docker benefits:
Reduces a container to a single process which
Encapsulates application configuration and delivery complexity
Provides a highly efficient
Docker limitations:
-Treats containers differently from a standard host, such as sharing the host’s IP address and providing access to the container via a selectable port. This approach can cause management issues when using traditional applications and management tools that require access to Linux utilities such as
-Uses layers and disables storage persistence, which results in reduced disk subsystem performance
-Is not ideal for stateful applications
-Is essentially a lightweight VM with its own hostname, IP address, file systems, and full OS init
-Performs nearly
-Can efficiently run one or more multi-process applications.
-An LXC-based container can run almost any Linux-based application without sacrificing performance or operational ease of use. This makes LXC an ideal platform for containerizing performance-sensitive, data-intensive enterprise applications.
LXC Benefits:
Provides a “normal” OS environment that supports all the features and capabilities
Supports layers and enables Copy-On-Write cloning and
Uses simple, intuitive, and standard IP addresses to access the containers and allows full access to the host file.
Supports static IP addressing,
Provides full root access.
Allows you to create your own network interfaces.
LXC Limitations:
Inconsistent feature support across different Linux distributions. LXC is primarily being maintained & developed by Canonical on Ubuntu platform.
Docker is a great platform for building
- Docker vs LXD Docker specializes in deploying apps
LXD specializes in deploying (Linux) Virtual Machines
Containers are a lightweight virtualization mechanism that does not require you to set up a virtual machine on an emulation of physical hardware.
a Self-Contained OS
You create many virtual machines, that have
Docker used
The filesystem is an abstraction to Docker, while
https://unix.stackexchange.com/questions/254956/what-is-the-difference-between-docker-lxd-and-lxc
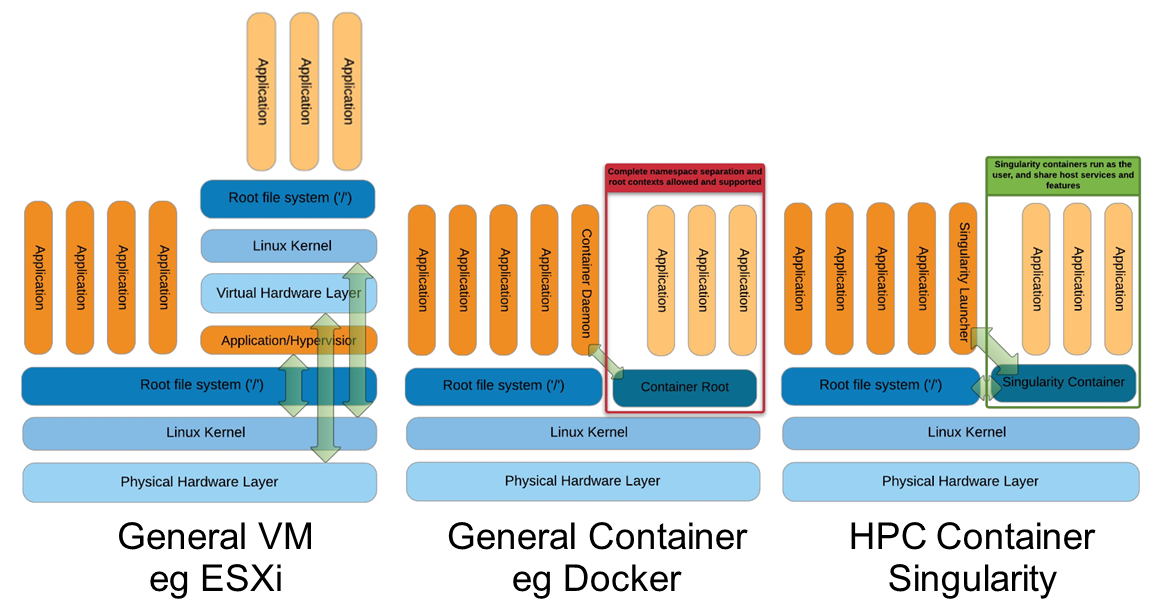
- Singularity enables users to have full control of their environment.
Singularity containers can be used that you don’t have to ask your cluster admin to install anything for you-you can put it in a Singularity container and run. Did you already invest in Docker? The Singularity software can import your Docker images without having Docker installed or being a superuser. Need to share your code? Put it in a Singularity container and your collaborator won’t have to go through the pain of installing missing dependencies. Do you need to run a different operating system entirely? You can “swap out” the operating system on your host for a different one within a Singularity container
http://singularity.lbl.gov/
- The Scientific Filesystem (SCIF) provides internal modularity of containers, and it makes it easy for the creator to give the container implied metadata about software. For example, installing a set of libraries, defining environment variables, or adding labels that belong to app
foo makes a strong assertion that those dependencies belong tofoo . When I runfoo , I can be confident that the container is running in this context, meaning withfoo 's custom environment, and withfoo ’s libraries and executables on the path. This is drastically different from serving many executables in a single container because there is no way to know whichare associated
https://singularity.lbl.gov/docs-scif-apps
- Shifter enables container images for HPC. In a nutshell, Shifter allows an HPC system to efficiently and safely allow end-users to run a docker image. Shifter
consists of ) a utility that typically runs on the compute node that creates therun time environment for the application 2) an image gateway service that pulls images from a registry and repacks it in a format suitable for the HPC system (typicallysquashfs ) 3) and example scripts/plugins to integrate Shifter with various batch scheduler systems.
https://github.com/NERSC/shifter
Docker vs Singularity vs Shifter in an HPC environment
build is the “Swiss army knife” of container creation. You can use it to download and assemble existing containers from external resources like Singularity Hub and Docker Hub.
compressed read-only
writable ext3 file system suitable for interactive development (--writable option)
writable (
But default the container will
If you want your container in a different format use the
https://singularity.lbl.gov/docs-build-container
- Although
scif is notexclusively for containers, in that a container can provide an encapsulated, reproducible environment, the scientific filesystem works optimally when contained. Containers traditionally have one entry point, one environment context, and one set of labels to describe it. A container created with a Scientific Filesystem can expose multiple entry points, each that includes its own environment, metadata, installation steps, tests, files, and a primary executable script. SCIF thus brings internal modularity and programmatic accessibility to encapsulated, reproducible environments
- A Research Scientist
want
https://sci-f.github.io/examples
- Containers are encapsulations of system environments
Docker is the most well known and
Designed primarily for network micro-service virtualization
Facilitates creating, maintaining and distributing container images
Containers are kinda reproducible
Easy to install, well documented, standardized
If you ever need to scale beyond your local resources, it may be a
Docker, and other enterprise-focused containers,
even compatible with traditional HPC
Singularity: Design Goals
Architected to support “Mobility of Compute”, agility, BYOE, and portability
Single file based container images
Facilitates distribution, archiving, and sharing
Very efficient for parallel file systems
No system, architectural or workflow changes necessary to integrate on HPC
Limits user’s privileges (inside user == outside user)
No root owned container daemon
Simple integration with resource managers,
systems, and supports multiple architectures (x86_64, PPC, ARM, etc..)
Container technologies
applications with the same performance characteristics as native applications.
There is a minor theoretical performance penalty as the kernel must now navigate
isolation.
design goals.
This gives Singularity a much lighter footprint, greater performance potential and easier
integration than container platforms that
http://www.hpcadvisorycouncil.com/events/2017/stanford-workshop/pdf/GMKurtzer_Singularity_Keynote_Tuesday_02072017.pdf#43
- What is Singularity?*
"Singularity enables users to have full control of their environment.
- With Singularity, developers who like to
be able to in order to modify the container.
OpenVZ OpenVZ creates multiple secure, isolated Linux containers (otherwise known as VEs or VPSs) on a single physical server enabling better server utilization and ensuring that applications do not conflict. Each container performs and executes exactly like a stand-alone server; a container canbe rebooted independently and have root access, users, IP addresses, memory, processes, files, applications, system libraries and configuration files.
- unlike VMs, containers have a dual lens you can view them through: are they infrastructure (aka “lightweight VMs”) or are they application management and configuration systems?
The reality is that they
Unfortunately, while you can run an unmodified kernel on Intel-VTx, system calls that touch networking and disk still wind up hitting emulated hardware. Intel-VTx primarily solved the issues of segregating, isolating, and allowing high-performance access to direct CPU calls and memory access (via Extended Page Table [EPT]). Intel-VT does not solve access to network and disk, although SR-IOV, VT-d, and related attempted to address this issue, but never quite got there
Within the hypervisor and
Containers and Security
It’s a popular refrain to talk about containers as being “less secure” than hypervisors,
But many will point to the magic voodoo that a hypervisor can do to provide isolation, such as Extended Page Table (EPT). Yet, EPT, and many other capabilities in the hypervisor are no longer provided by the hypervisor itself, but by the Intel-
You can expect Intel to continue to enrich the Intel-
Combined with removing most of the operating system wrapped arbitrarily around the application in a hypervisor VM, containers may actually already be more secure than the hypervisor model
This then leads us to understand that hypervisors sole value
if you don’t care about multiple guest operating systems, if you integrate the DUNE libraries from Stanford into the container
Highly
Probably as secure as any hypervisor if configured properly
Significantly simpler than a hypervisor with less overhead and operating system bloat
as we become container-centric, we’re inherently becoming application-centric
The apps and modern cloud-native app developer just cares about the infrastructure contract: I call an API, I get the infrastructure resource, it either performs to
More and more, customers
http://cloudscaling.com/blog/cloud-computing/will-containers-replace-hypervisors-almost-
- Dune provides ordinary user programs with safe and efficient access to privileged CPU features that are traditionally only available to kernels. It does so by leveraging modern virtualization hardware, enabling direct execution of privileged instructions in an unprivileged context. We have implemented Dune for Linux, using Intel's VT-x virtualization architecture to expose access to exceptions, virtual memory, privilege modes, and segmentation. By making these hardware mechanisms available at user-level, Dune creates opportunities to deploy novel systems without specialized kernel modifications.
- Windows Server Containers
Container endpoints can
https://docs.microsoft.com/en-us/windows-server/networking/sdn/technologies/containers/container-networking-overview
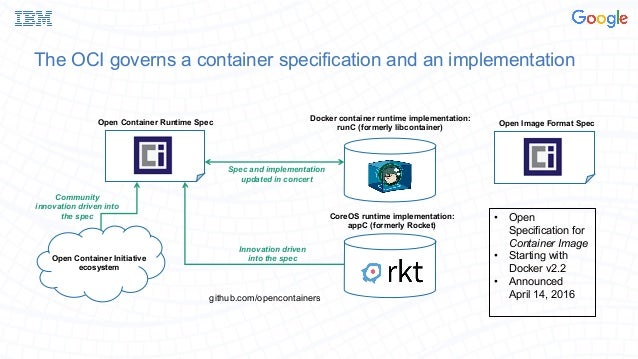
- Established in June 2015 by Docker and other leaders in the container industry, the OCI
currently contains two specifications: the Runtime Specification (runtime-spec) and the Image Specification (image-spec). The Runtime Specification outlines how to run a “filesystem bundle” thatis unpacked on disk. At a high-level, an OCI implementation would download an OCI Image then unpack that image into an OCI Runtime filesystem bundle.At this point, the OCI Runtime Bundle would be run by an OCI Runtime.
https://www.opencontainers.org/
- Kata Containers is an open source project and community working to build a standard implementation of lightweight Virtual Machines (VMs) that feel and perform like containers, but provide the workload isolation and security advantages of VMs.
The Kata Containers project has six components: Agent, Runtime, Proxy, Shim, Kernel and packaging of QEMU 2.11.
https://katacontainers.io/
- Firecracker runs in user space and uses the Linux Kernel-based Virtual Machine (KVM) to create
microVMs
The fast startup time and low memory overhead of each microVM enable you to pack thousands of microVMs onto the same machine.
Firecracker is an alternative to QEMU, an established VMM with a general purpose and broad feature set that allows it to host a variety of guest operating systems.
What is the difference between Firecracker and Kata Containers and QEMU?
Kata Containers is an OCI-compliant container runtime that executes containers within QEMU based virtual machines. Firecracker is a cloud-native alternative to QEMU that is purpose-built for running containers safely and efficiently, and nothing more. Firecracker provides a minimal required device model to the guest operating system while excluding non-essential functionality (there are only 4 emulated devices: virtio -net, virtio -block, serial console, and a 1-button keyboard controller used only to stop the microVM ).
https://firecracker-microvm.github.io/
- CoreOS is an open-source lightweight operating system based on the Linux kernel and designed for providing infrastructure to clustered deployments, while focusing on automation, ease of application deployment, security, reliability and scalability. As an operating system, CoreOS provides only the minimal functionality required for deploying applications inside software containers, together with built-in mechanisms for service discovery and configuration sharing
https://en.wikipedia.org/wiki/CoreOS
- With Container Linux and
Kubernetes , CoreOS provides the key components to secure, simplify and automatically update your container infrastructure.
rkt is an application container engine developed for modern production cloud-native environments. It features a pod-native approach, a pluggable execution environment, and a well-defined surface area that makes it ideal for integration with other systems.
https://coreos.com/rkt/
- Turbo and Docker
Docker is a new containerization technology built on top of the LXC kernel container system, a component of the Linux OS.
Platform
Turbo
Docker
the Turbo VM plays the same role for Turbo containers as LXC does for Docker
Turbo supports both desktop and server Windows applications, and works on all desktop and server editions of Windows from Windows Vista forward
Turbo does not require modifications to the base operating system kernel.
Turbo does not execute a parallel copy of the base operating system.
Turbo containers support many Windows-specific constructs, such as Windows Services, COM/DCOM components, named kernel object isolation,
Turbo also provides a desktop client with many features (GUI tool to launch applications, file extension associations, Start Menu integration) that allow containerized applications to interact with the user in the same way as traditionally installed desktop applications. Turbo also provides a small browser plugin that allows users to launch and stream containerized applications directly from any web browser.
Layering
For example, to build a container for a Java application that uses a MongoDB database, a Turbo user could combine a Java runtime layer with a MongoDB database layer, then stack the application code and content in an application layer on top of its dependency layers. Layers make it
Layers can
Docker does not distinguish between content that
Multi-base image support
Continuation
Turbo's unique continue command allows execution to
Isolation Modes
Unlike Docker,
For example, it is possible to specify that one directory
Networking
Docker relies on root access to the host device at two levels.
First, the LXC/
Second, the Docker daemon itself runs with root privileges.
Turbo containerization inherits this ability from the user mode Turbo app virtualization engine, which operates on top of (rather than within) the OS kernel.
This approach has two critical advantages:
Like Docker, Turbo provides command-line interfaces (turbo) and a scripting language (
Configuration
Streaming
Turbo, like Docker, supports the use of local containers and the ability to push and pull containers from a central repository
https://turbo.net/docs/about/turbo-and-docker#platform
- What is Turbo?
Turbo allows you to package applications and their dependencies into a lightweight, isolated virtual environment called a "container."
With Turbo, testers can:
Run development code in a pre-packaged, isolated environment with software-configurable networking
Rapidly rollback changes and execute tests across
Test in multiple client, server, and browser environments concurrently on a single physical device
With Turbo, system administrators can:
Remove errors
Allow users to test out new or beta versions of applications without interfering with existing versions
Simplify deployment of desktop applications by eliminating dependencies (
Improve security by locking down desktop and server environments while preserving application access
Do Turbo containers work by running a full OS virtual machine?
No. Turbo containers use a special, lightweight application-level VM called Turbo VM. Turbo VM runs in user mode on top of a single instance of the base operating system.
When I run a container with multiple base images, does it link multiple containers or make a single new container?
Running with multiple base images creates a single container with
Does Turbo support virtual networking?
Yes. Controlling both inbound and outbound traffic
Does Turbo support linking multiple containers?
Yes. See the
Is there a difference between server and desktop application containers?
No, there is no special distinction. And desktop containers can contain services/servers and vice versa.
https://turbo.net/docs/about/what-is-turbo#why-use-turbo





http://www.hardware.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
ReplyDeletehttp://www.computer-science.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.computers.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.child-health.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.weight-loss.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.healthcare-industry.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.autos.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.online-teaching.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.shopping.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/
http://www.clothing.sbm.pw/News/docker-and-kubernetes-training-%7C-docker-training-in-hyderabad/