- Not every network uses
all of the model’s layers. ISO’s intent in creating the OSI model
design. This model is useful for conceptualizing network components to
how they fit together to help the computers within the network communicate.
ard protocols associated with each layer. Instead,
Physical layer.
Data link layer. Here again, Nmap has to use this layer or nothing gets sent to the destination. But there are some cases where Nmap
On Windows,
There are some NSE scripts that probe layer-2 protocols:
If the target is on the same data link,
Network layer.
Transport layer. This is where the "port
Application layer. This is where version detection (-
When on the same local network,
layer 3 (network layer)
the transport layer (layer 4)
https://stackoverflow.com/questions/47210759/which-layer-in-the-osi-model-does-a-network-scan-work-on
Trace route works on network layer of OSI Model
Its uses ICMP packets and relies on a function called TTL
The Windows command is
https://www.quora.com/What-trace-route-works-on-which-layer
OSI Model Explained | Real World Example
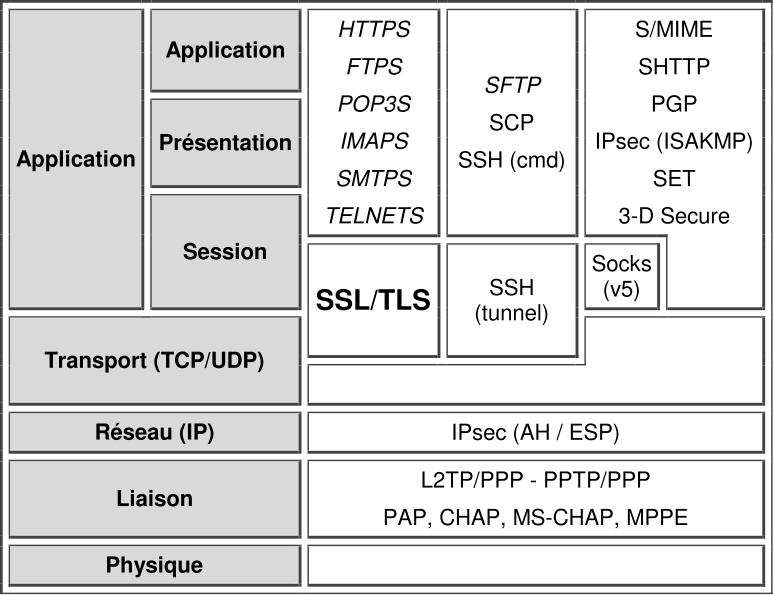
- Connection-Oriented and Connectionless Protocols in TCP/IP
Looking again at TCP/IP, it has two main protocols that operate at the transport layer of the OSI Reference Model. One is the Transmission Control Protocol (TCP), which is connection -oriented; the other, the User Datagram Protocol (UDP), is connectionless. TCP is used for applications that require the establishment of connections (as well as TCP’s other service features), such as FTP
Even though a TCP connection can be used to send data back and forth between devices, all that data is indeed still being sent as packets; there is no real circuit between the devices. This means that TCP must deal with all the potential pitfalls of packet-switched communication, such as the potential for data loss or receipt of data pieces in the incorrect order. Certainly, the existence of connection-oriented protocols like TCP doesn't obviate the need for circuit switching technologies
The principle of layering also means that there are other ways that connection-oriented and connectionless protocols can be combined at different levels of an internetwork .
Just as a connection-oriented protocol can be implemented over an inherently connectionless protocol, the reverse is also true
http://www.tcpipguide.com/free/t_ConnectionOrientedandConnectionlessProtocols-3.htm
- a basic understanding of the layered nature of modern networking
architecture,The Open System Interconnection (OSI) Reference Model
Even though packets may be used at lower layers for the mechanics of sending data, a higher-layer protocol can create logical connections through the use of messages sent in those packets.
Circuit-switched networking technologies are inherently connection-oriented, but not all connection-oriented technologies use circuit switching. Logical connection-oriented protocols can in fact be implemented on top of packet switching networks to provide higher-layer services to applications that require connections.
http://www.tcpipguide.com/free/t_ConnectionOrientedandConnectionlessProtocols-2.htm
Data Encapsulation OSI TCPIP
OSI Encapsulation
Understanding the OSI Reference Model: Cisco Router Training 101
- What is OSI model?
OSI stands for = Open Systems Interconnection (OSI) model
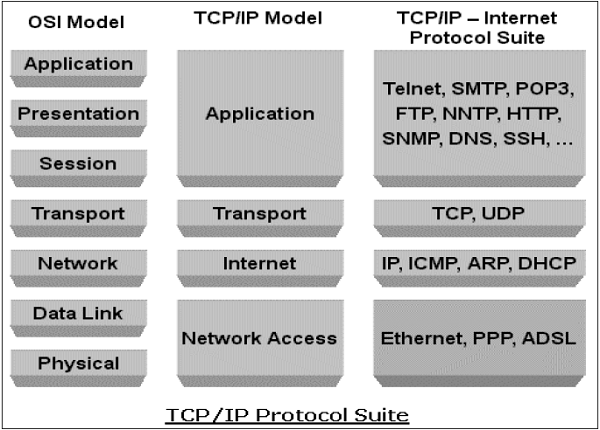
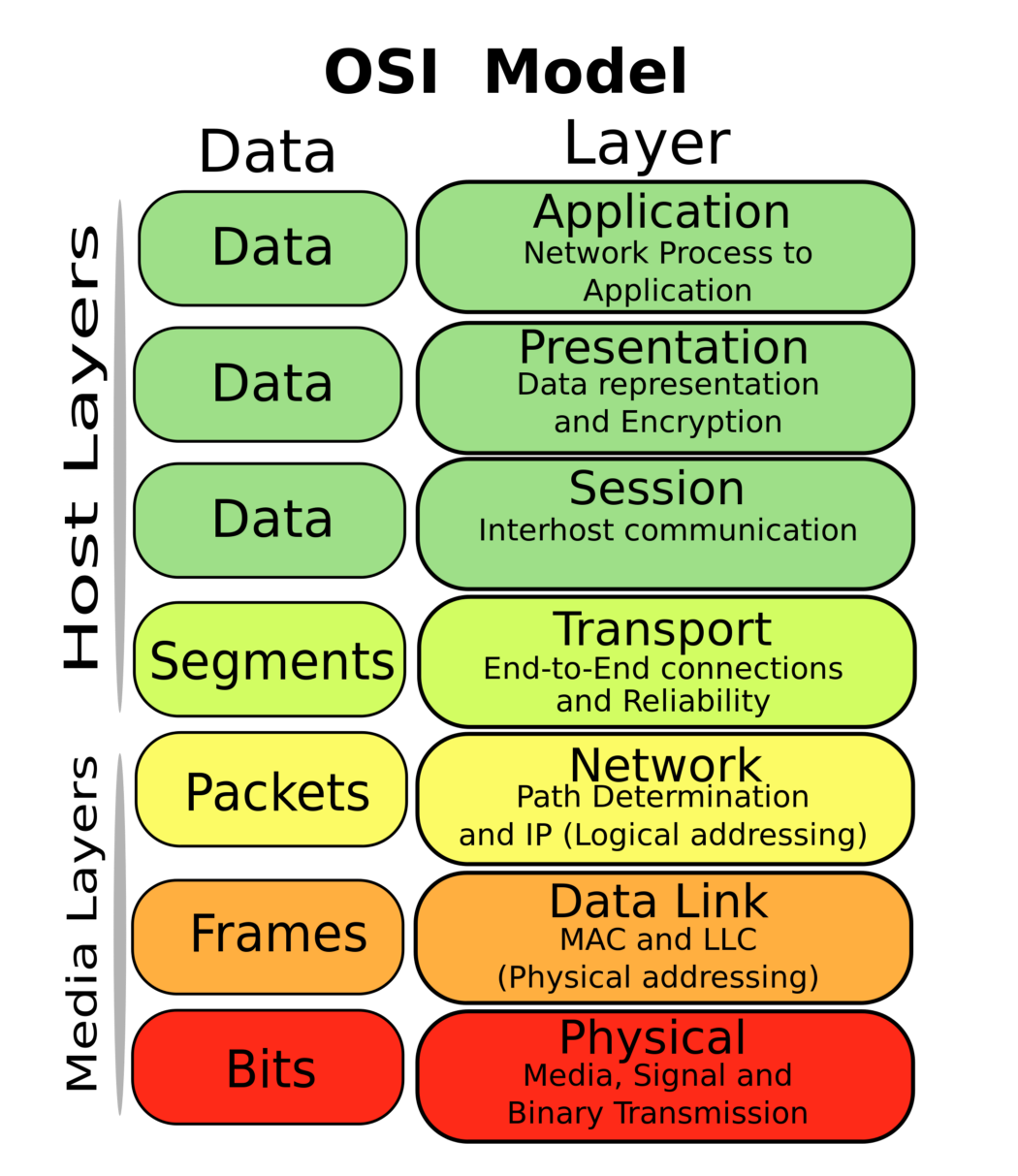
OSI model is a reference model containing 7 layers such as physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer.
It is a prescription of characterizing and standardizing the functions of a communications system in terms of abstraction layers. Similar communication functions are grouped into logical layers. A layer serves the layer above it and is served by the layer below it
What is TCP/IP model?
TCP/IP model is an implementation of OSI reference model. It has five layers. They are: Network layer, Internet layer, Transport layer and Application layer.
What are the differences between OSI and TCP/IP model?
Important differences are:
OSI is a reference model and TCP/IP is an implementation of OSI model.
OSI has 7 layers whereas TCP/IP has only 4 layers The upper 3 layers of the OSI model is combined on the TCP/IP model.
OSI has: physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer
TCP/IP has : Network layer, Internet layer, transport layer and application layer.
Explain in detail the process of sending a piece of information from a host on subnet A to a host on subnet B.
What I'm looking for:
Some knowledge of the OSI model
The concept of layers, layer units, and encapsulation.
The concept of MTU/fragmentation (not required, but nice if they know it)
The address resolution process at layer 3 (DNS)
The determination of local vs. non-local addresses (subnet masks/what are subnets/when to use a default gateway)
The address resolution process at layer 2 (ARP)
At least a vague understanding of layer 1 and associated issues
Protocols according to layers
Data Link Layer
ARP/RARP Address Resolution Protocol/Reverse Address
Network Layer
DHCP Dynamic Host Configuration Protocol
ICMP/ICMPv6 Internet Control Message Protocol
IP Internet Protocol version 4
IPv6 Internet Protocol version 6
Transport Layer
TCP Transmission Control Protocol
UDP User Datagram Protocol
Session Layer
DNS Domain Name Service
LDAP Lightweight Directory Access Protocol
Application Layer
FTP File Transfer Protocol
HTTP Hypertext Transfer Protocol
IMAP4 Internet Message Access Protocol rev 4
NTP Network Time Protocol
POP3 Post Office Protocol version 3
SMTP Simple Mail Transfer Protocol
SNMP Simple Network Management Protocol
SOCKS Socket Secure (Server)
TELNET TCP/IP Terminal Emulation Protocol
References:
http://rancidtaste.hubpages.com/hub/OSI-Reference-Model-and-TCP-IP-Model-Interview-Questions-and-Answers
http://www.protocols.com/pbook/tcpip1.htm
- please-physical layer-Bits-
Hubs , Repeater live - do-Data link layer-Frames-
Switches,Bridges live-MAC,Physical addressing - not -Network layer-Packets-Routers
live,IP Addressing,logical addressing - throw-Transport layer-Segments-TCP
, UDP - sausage-Session Layer-data
- pizza-presentation layer-data
- away-application layer-data
- OSI Model Explained CCNA - Part 1
- please-physical layer-Bits-
Hubs , Repeater - do-Data link layer-Frames-
atm,frame relay ,switches , - not -Network layer-Packets or
Datagrams -IP, IPV4, IPV6, IPSEC, IPX, routers - throw-Transport layer-Segments-TCP
, UDP - sausage-Session Layer-data-sessions between local and remote hosts
- pizza-presentation layer-data-
ascii,jpeg , mpeg etc deals with dataformating - away-application layer-data-
ftp , http , telnet , dns , dhcp etc deals with protocols
- Problems with TCP/IP
2.1 Built for the Wide Area
TCP/IP was originally designed , and is usually implemented , for wide-area networks. While TCP/IP is usable on a local-area network, it is not optimized for this domain. For example, TCP uses an in-packet checksum for end-to-end reliability, despite the presence of per-packet CRC's in most modern network hardware. But computing this checksum is expensive, creating a bottleneck in packet processing. IP uses header fields such as `Time-To-Live' which are only relevant in a wide-area environment. IP also supports internetwork routing and in-flight packet fragmentation and reassembly, features which are not useful in a local-area environment. The TCP/IP model assumes communication between autonomous machines that cooperate only minimally. However, machines on a local-area network frequently share a common administrative service, a common file system, and a common user base. It should be possible to extend this commonality and cooperation into the network communication software.
2.2 Multiple Layers
Standard implementations of the Sockets interface and the TCP/IP protocol suite separate the protocol and interface stack into multiple layers. The Sockets interface is usually the topmost layer, sitting above the protocol. The protocol layer may contain sub-layers: for example, the TCP protocol code sits above the IP protocol code. Below the protocol layer is the interface layer, which communicates with the network hardware. The interface layer usually has two portions, the network programming interface, which prepares outgoing data packets, and the network device driver, which transfers data to and from the network interface card (NIC).
This multi-layer organization enables protocol stacks to be built from many combinations of protocols, programming interfaces, and network devices, but this flexibility comes at the price of performance. Layer transitions can be costly in time and programming effort. Each layer may use a different abstraction for data storage and transfer, requiring data transformation at every layer boundary. Layering also restricts information transfer. Hidden implementation details of each layer can cause large, unforeseen impacts on performance. Also, the number of programming interfaces and protocols is small: there are two programming interfaces (Berkeley Sockets and the System V Transport Layer Interface) and only a few data transfer protocols (TCP/IP and UDP/IP) in widespread usage. This paucity of distinct layer combinations means that the generality of the multi-layer organization is wasted . Reducing the number of layers traversed in the communications stack should reduce or eliminate these layering costs for the common case of data transfer.
2.3 Complicated Memory Management
Current TCP/IP implementations use a complicated memory management mechanism. This system exists for a number of reasons. First, a multi-layered protocol stack means packet headers are added (or removed) as the packet moves downward (or upward) through the stack. This should be done easily and efficiently, without excessive copying. Second, buffer memory inside the operating system kernel is a scarce resource; it must be managed in a space-efficient fashion.
https://www.usenix.org/legacy/publications/library/proceedings/ana97/full_papers/rodrigues/rodrigues_html/node2.html
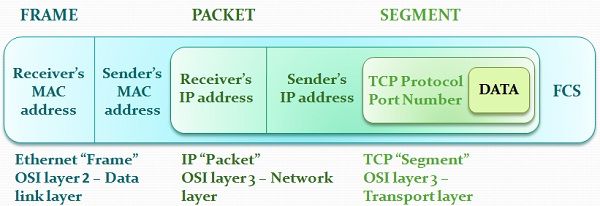
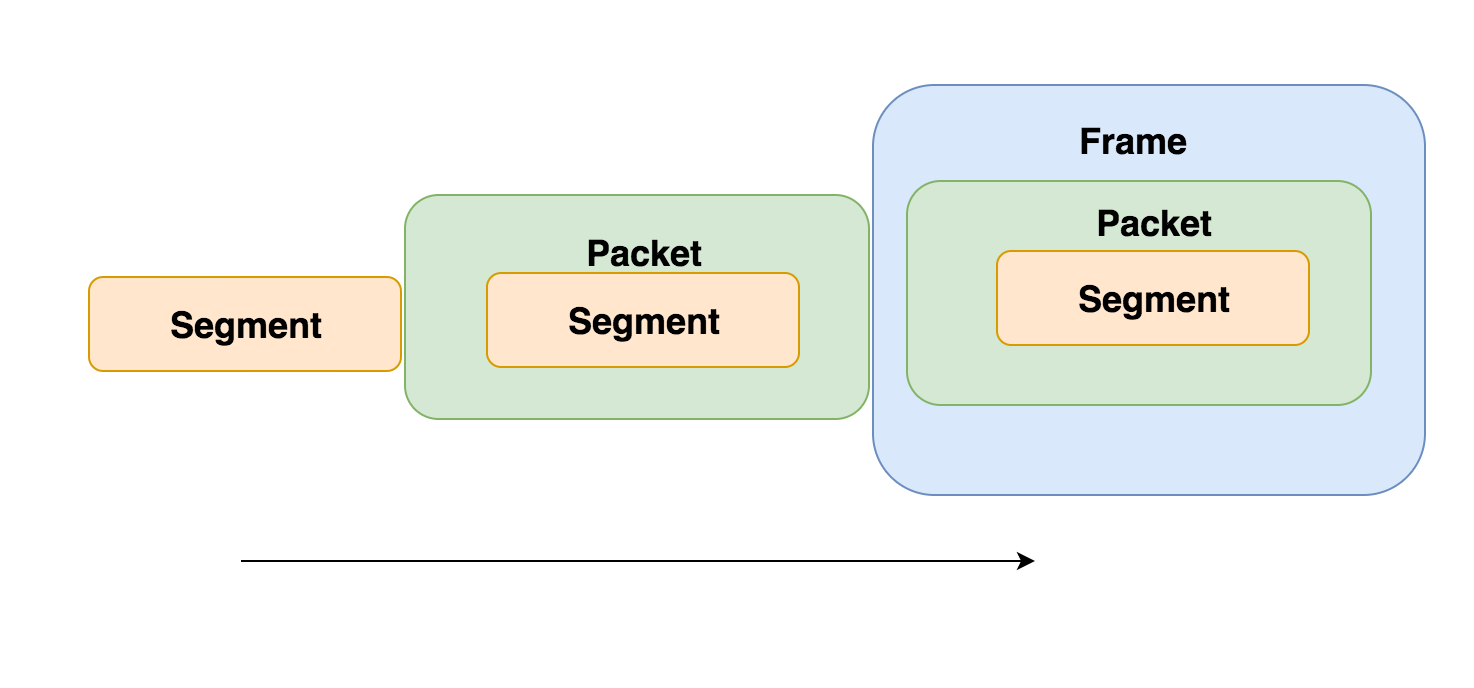
- The term PDU is used to refer to the packets in different layers of the OSI model. Thus PDU gives an abstract idea of the data packets. The PDU has a different meaning in different layers still we can use it as a common term. To give a clear picture:-
The PDU of Transport Layer is called as a Segment.
The PDU of Network Layer is called as a Packet.
The PDU of the Data-Link Layer is called Frames.
https://www.geeksforgeeks.org/difference-between-segments-packets-and-frames/






No comments:
Post a Comment