- DAST
Web Application Vulnerability Scanners
Tools Listing
AVDS
Burp Suite
Grabber
Grendel-Scan
Vega
Wapiti
WebCookies
Wikto
w3af
Zed Attack Proxy - OWASP ZAP
https://www.owasp.org/index.php/Category:Vulnerability_Scanning_Tools
- Dynamic Application Security Testing (DAST)
http://www.gartner.com/it-glossary/dynamic-application-security-testing-dast/
- Today’s organizations deploy a myriad of web applications, ranging from external-facing corporate websites to internal-facing portals
. WhiteHat
https://www.whitehatsec.com/products/dynamic-application-security-testing/
- Application security can help organizations protect all kinds of applications (such as legacy, desktop, web, mobile, micro services) used by internal and external stakeholders including customers, business partners and employees
Why Application Security?
As validated by multiple studies, the majority of successful breaches target exploitable vulnerabilities residing in the application layer, indicating the need for enterprise IT departments to be extra vigilant about application security.Now, the software supply chain is much more complicated considering the outsourced development, the number of legacy applications, coupled with in-house development that takes advantage of 3rd party, open source and commercial, off-the-shelf software components.
Organizations need application security solutions that cover all of their applications, from those used internally to popular external apps used on customers’ mobile phones.
These solutions must cover the entire development stage and offer testing after an application is put into use to monitor for potential problems.
What is SAST?
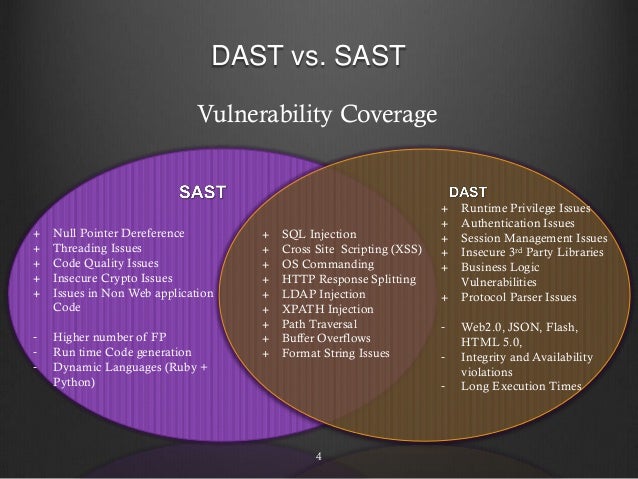
Static Application Security Testing (SAST) scans the application source files, accurately identifies the root cause and helps remediate the underlying security flaws.
Developer Benefits of Static Application Security Testing:
Fully integrated with the Integrated Developer Environment (IDE)
What is DAST?
Dynamic Application Security Testing (DAST) simulates controlled attacks on a running web application or service to identify exploitable vulnerabilities in a running environment.
Benefits of Dynamic Application Security Testing:
Provides a comprehensive view of application security by focusing on what’s exploitable and covering all components (server, custom code, open source, services)
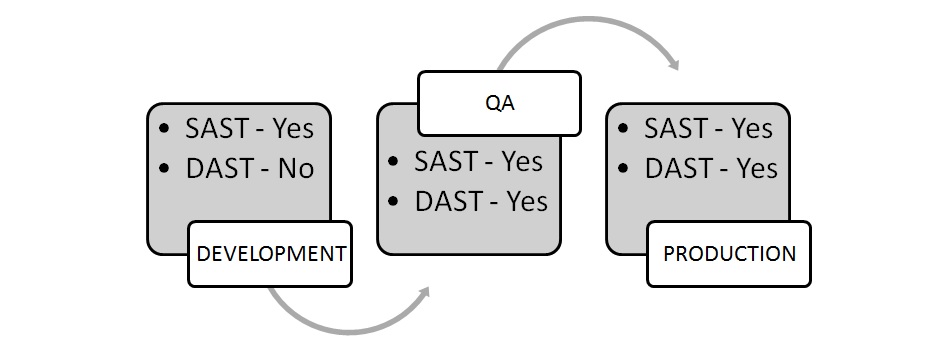
Can be integrated into Dev, QA and Production to offer a continuous holistic view
Tests functional app, so unlike SAST, is not language constrained and runtime and environment-related issues can be discovered
https://www.microfocus.com/en-us/what-is/application-security
- What is Dynamic Application Security Testing (DAST)?
Dynamic Application Security Testing (DAST) is the process of analyzing a web application through the front-end to find vulnerabilities through simulated attacks.This type of approach evaluates the application from the “outside in” by attacking an application like a malicious user would.
Pros of DAST
Independent of the application
Immediately finds vulnerabilities that could be exploited
Does not require access to the source code
Cons of DAST
Does not find the exact location of a vulnerability in the code
Security knowledge is needed to interpret reports
Test can be time-consuming
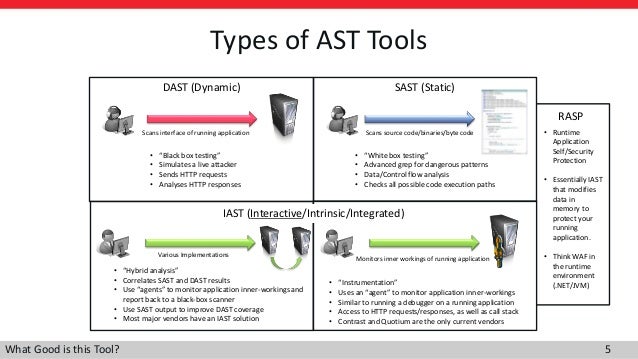
There are many ways to test application security, including:
Static Application Security Testing (SAST)
Dynamic Application Security Testing (DAST)
Mobile Application Security Testing (MAST)
Interactive Application Security Testing (IAST)
Why is DAST Important?
Human error will inevitably play a part at some point in the Software Development Life Cycle (SDLC), and the sooner a vulnerability is caught during the SDLC, the cheaper it is to fix.
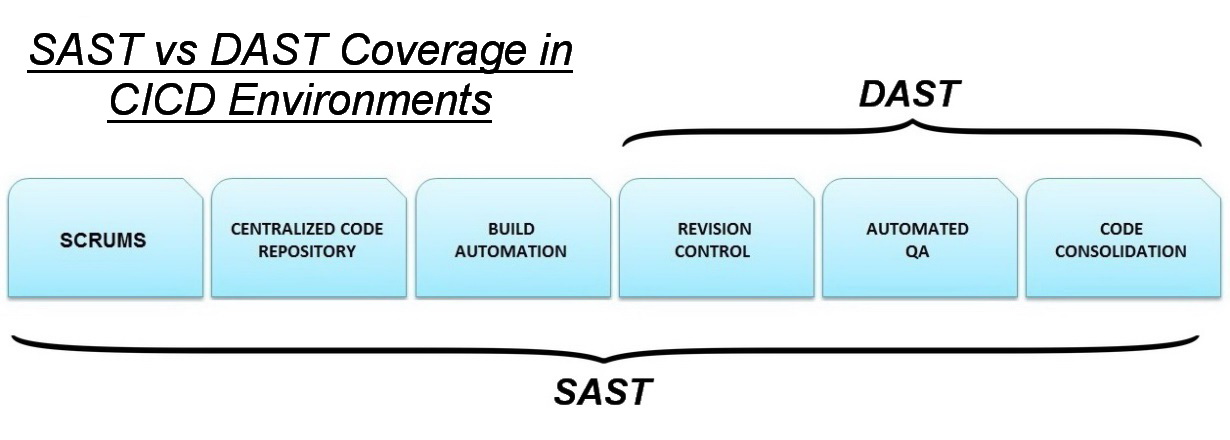
When DAST is included as part of the Continuous Integration/Continuous Development (CI/CD) pipeline, this is referred to as “Secure DevOps,” or “DevSecOps.”
How does DAST work?
A DAST scanner searches for vulnerabilities in a running application and then sends automated alerts if it finds flaws that allow for attacks like SQL injections, Cross-Site Scripting (XSS), and more. Since DAST tools are equipped to function in a dynamic environment, they can detect runtime flaws which SAST tools can’t identify.
What is the difference between SAST and DAST?
SAST, on the other hand, analyzes static environments, meaning the source code of an application. It looks at the application from the “inside out,” searching for vulnerabilities in the code.
To maximize the strength of your security posture, it’s a best practice to use both SAST and DAST. Having this unified taxonomy across testing methods enables you to have a complete view of vulnerabilities.
https://www.microfocus.com/en-us/what-is/dast
- ZAPGETTINGSTARTEDGUIDE-2.7
Software security testing is
we
At its core, ZAP is
It stands between the tester’s browser and the web application so
When you
location. If you do not persist the session, those
saving the
Expand Your
Any pages protected by a login page are not discoverable during a passive scan because, unless you’ve
handle the required authentication Any pages that are not
of passive scanning.
Quick Scan uses the traditional ZAP spider, which discovers links by examining the HTML in responses from the web application. This spider is fast, but it is not
always
Spiders are a great way to explore your basic site, but
Spiders, for example, will only enter basic default data into forms in your web application but a user can enter more relevant information which can, in
turn, expose more of the web application to ZAP.
This is especially true with things like
registration forms where a valid email address
correctly formatted string, which may cause more of the application to
Obscurity is not
Passive scanning is good at
Active scanning, however,
- The OWASP Top Ten Proactive Controls 2016 is a list of security techniques that should
be included
Encode Data
Validate All Inputs
Implement Identity and Authentication Controls
Implement
Protect Data
Implement Logging and Intrusion Detection
Leverage Security Frameworks and Libraries
Error and Exception Handling
https://www.owasp.org/index.php/OWASP_Proactive_Controls
- OWASP OWTF
Aligned with OWASP Testing Guide + PTES + NIST
https://www.owasp.org/index.php/OWASP_OWTF
- Vega is a free and open source web security scanner and web security testing platform to test the security of web applications. Vega can help you find and validate SQL Injection, Cross-Site Scripting (XSS), inadvertently disclosed sensitive information, and other vulnerabilities
Arachni is a feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administratorsevaluate the security of modern web applications
- w3af is a Web Application Attack and Audit Framework. The project’s goal is to create a framework to help you secure your web applications by finding and exploiting all web application vulnerabilities
. W3afis known asmost powerful and flexible tool for finding web application’s vulnerability. It’seasy to use feature made it popular among the security professionals like ethical hackers. W3af contains many web assessment and exploitation pluginsas well .
http://w3af.org/
- Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers
. Niktois sponsored byNetsparker , a false positive free web application security scanner.
https://cirt.net/Nikto2
- Burp Suite is an integrated platform for performing security testing of web applications
-
Spider - This can be used for automatically crawling an application, to discover its content and functionality. Scanner - This is usedto automatically scan HTTP requests to find security vulnerabilities.
Intruder - This allows you to perform customized automated attacks, to carry out all kinds of testing tasks.
Repeater - This is used
Sequencer -
Decoder - This lets you transform bits of application data using common encoding and decoding schemes.
Comparer -
https://portswigger.net/burp/help/suite_gettingstarted
- Firefox - Go to the Firefox menu, click on Options, click on Advanced, go to the Network tab, and click on the Settings button in the Connection section. Select the "Manual proxy configuration" radio button. Enter your Burp Proxy
listener address in the "HTTP proxy" field (by default, 127.0.0.1). Enter your Burp Proxylistener port in the "Port" field (by default, 8080). Make sure the "Use this proxy server for all protocols" boxis checked . Delete anything that appears in the "No proxy for" field. Then click "OK" to closeall of the options dialogs.
https://portswigger.net/burp/help/suite_gettingstarted#browser
The intercept feature will intercept ALL traffic sent from the browser, additional extensions such as FoxyProxy can be used to specify which URLs and IPs are blacklisted /whitelisted and therefore bypass the Burp intercept.
http://www.primalsecurity.net/0x2-exploit-tutorial-web-hacking-with-burp-suite/
- Two ways to go about this are static application security testing (SAST) and dynamic application security testing (DAST). These application security testing methodologies
are used . The two methodologies approach applicationsvery differently. They are most effective at different phases of the software development life cycle (SDLC) and find differenttypes of vulnerabilities. For example, SAST detects critical vulnerabilities such as cross-site scripting (XSS), SQL injection, and buffer overflow earlier in the SDLC. DAST, on the other hand, uses an outside-in penetration testing approach to identify security vulnerabilities while web applications are running.
- SAST vs DAST
- SAST, DAST, IAST, and RASP: Pros, cons and how to choose
Some organizations need to focus on their developers, adding static application security testing (SAST) to the development cycle to catch potential flaws early
Other organizations may want to prove their need by using dynamic application security testing (DAST) or penetration testing to show how vulnerable their applications are.
there's interactive application security testing (IAST), which uses agents and additional software libraries to collect data from running applications that can then reveal vulnerabilities.
Companies that want to “virtually patch” their applications can lock down their portfolios using some form of application firewall or a newer technology, such as runtime application self-protection (RASP), a form of IAST.
IAST, including RASP: Protect code against exploits and known bugs
a new approach—known as interactive application security testing (IAST), or “glass-box” testing—promises to catch attacks that the other approaches miss
IAST runs as an agent, allowing you to collect and analyze event data from running applications.
https://learn.techbeacon.com/units/sast-dast-iast-rasp-pros-cons-how-choose
- Fiddler
http://www.telerik.com/fiddler
paros
http://sectools.org/tool/paros/
- Odysseus
http://www.darknet.org.uk/2007/02/odysseus-win32-proxy-telemachus-http-transaction-analysis/
- Charles is an HTTP proxy / HTTP monitor / Reverse Proxy that enables a developer to view
all of the HTTP and SSL / HTTPS traffic between their machine and the Internet.
https://www.charlesproxy.com/
- Application Security Automation
https://github.com/OWASP/glue
- OWASP Glue Tool Project
https://www.owasp.org/index.php/OWASP_Glue_Tool_Project
- What is BeEF?
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser
https://beefproject.com/
- OWASP Application Security Verification Standard Project
The OWASP Application Security Verification Standard (ASVS) Project provides a basis for testing web application technical security controls and also provides developers with a list of requirements for secure development.
https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project
- Free for Open Source Application Security Tools
the following lists of automated vulnerability detection tools
Static Application Security Testing (SAST) Tools
Dynamic Application Security Testing (DAST) Tools - (Primarily for web apps)
Interactive Application Security Testing (IAST) Tools - (Primarily for web apps and web APIs)
Keeping Open Source libraries up-to-date (to avoid Using Components with Known Vulnerabilities (OWASP Top 10-2017 A9))
Static Code Quality Tools
- https://www.owasp.org/index.php/Free_for_Open_Source_Application_Security_Tools
- Software Assurance Maturity Model
The Software Assurance Maturity Model (SAMM) is an open framework to help organizations
https://www.opensamm.org/
Overview of Burp Suite
DAST (Dynamic Application Security Testing) / Penetration Testing Tool
Integrated platform for performing security testing of web apps
Developed to provide comprehensive solution for web app security checks.Functionality includes proxy server, scanner, intruder, spidering, a repeater, a decoder,comparer, an extender, and sequence
Desired an automated approach to running Burp Suitesecurity scanning
Manual security scanning is time consuming (bottleneck) due to applicationdiscovery/ crawling process
Used Automated UI tests for application discovery
Used protractor (selenium) UI automated tests to act as the event based trigger forapplication discovery while using Burp Proxy to intercept all Requests/Response
Used Jenkins (Cl/CD) to run the automated UI test
Burp Suite Professional (v.1.7.34) with 'Burp-REST-API
Automated the spidering, proxy, intercepts request/response from UI tests, thenkicks off security scan, then generates Burp security scan report
Development Frivironment
Angular/NodeJS Web application
Protractor/Jasmine — Automated UI tool
Jenkins Cl/CD pipeline
Burp Suite Faternal API
Using multiple approach to testing applications
Manual Penetration Testing
DAST (Web App Scanning Tools)
Burp
Accunetix
Netsparker
SAST (DevSecOps Tools)
Checkmarx
Fortify
SonarQube
https://www.osti.gov/servlets/purl/1639985




Pretty article! I found some useful information in your blog, it was awesome to read, thanks for sharing this great content to my vision, keep sharing. Need to learn
ReplyDeleteSecurity Testing Services
Test Automation Services
Software Testing Services
Compatibility Testing Services
Regression Testing Services
ReplyDeleteGreat post. It was a good read and lots to know about fastest growing sectors. Having the Information Security Services in your enterprise or organization to identify and classify the security issues in IT systems. IARM is a single platform which can handle all your Cyber Security services and Conducting information security audits as well as vulnerability assessments that helps your businesses to analyze the status of the organization's security.
Top Cyber Security Company In India
Penetration Testing Company In Chennai
Soc Services In India
Cyber Attack Recovery Services In India
Vapt Service Provider India
Thank you for sharing such a great blog post with us this blog is really informative and useful, keep it up..
ReplyDeleteSoftware Testing Services
Software Testing Company
Functional Testing Services
QA Automation Testing Services
eCommerce Testing Services
Performance Testing Services
Security Testing Services
API Testing Services
Regression Testing Services
Mobile App Testing Services
Thank you for some other informative blog. Where else may I get that type of info written in such a perfect approach? I have a mission that I am simply now working on, and I have been on the glance out for such information.
ReplyDeleteVery nice post. I just stumbled upon your weblog and wished to say that I've really enjoyed surfing around your blog posts. After all I will be subscribing to your rss feed and I hope you write again soon!
ReplyDeleteFor growing teams, Clove HRMS acts as a robust Employee Management System with streamlined workflows. The Leave Management System minimizes scheduling conflicts and ensures accurate leave balances, promoting fair planning. The end-to-end solution aligns payroll, performance, and attendance, delivering a transparent experience for employees and administrators while reducing administrative overhead.
ReplyDeleteAs a trusted name in software testing services in india, DevstringX Technologies provides end-to-end QA solutions tailored to modern development cycles. From test planning to execution and reporting, their experts optimize test coverage, leverage automation, and ensure drop-in scalability for projects of any size. They excel in risk-based testing and continuous quality improvement.
ReplyDeleteDevstringx Technologies is the Best custom software development company in Noida, India, and the United States offering software development, Product Development, App Development, Angular Development, React Development, etc. We started our journey in 2014. Our headquarter is located in Noida, & another branch is in DE, USA. We hire Qualified candidates who help businesses grow and clients' happiness and also focus to deliver top-quality services. We are a well-established 100+ employees organization. To know more about Devstringx Technologies from a clearer angle kindly visit our site.
ReplyDeleteWe have specialization in:-
- Product Development
- Product Testing
- Software Testing
- App Development
- Angular Development
- React Development
Kindly visits our website & contact our experts to get a free quotation.
mobile app development companies in Noida