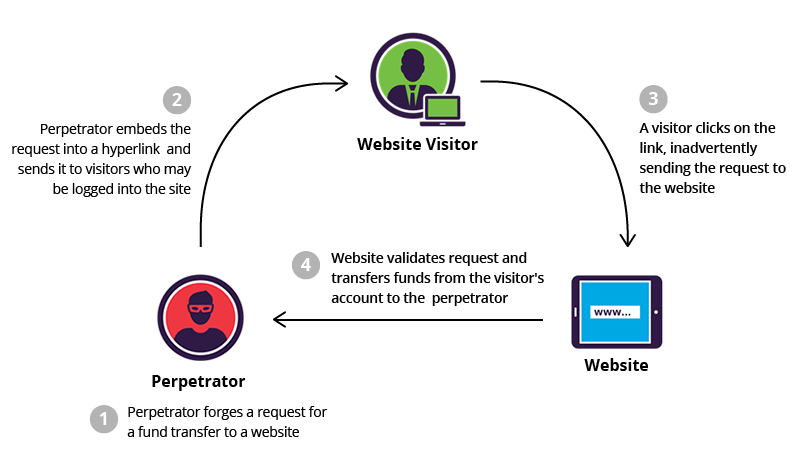
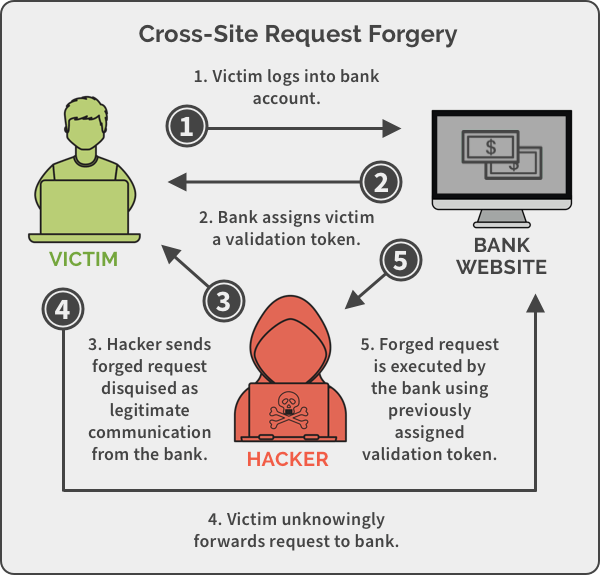
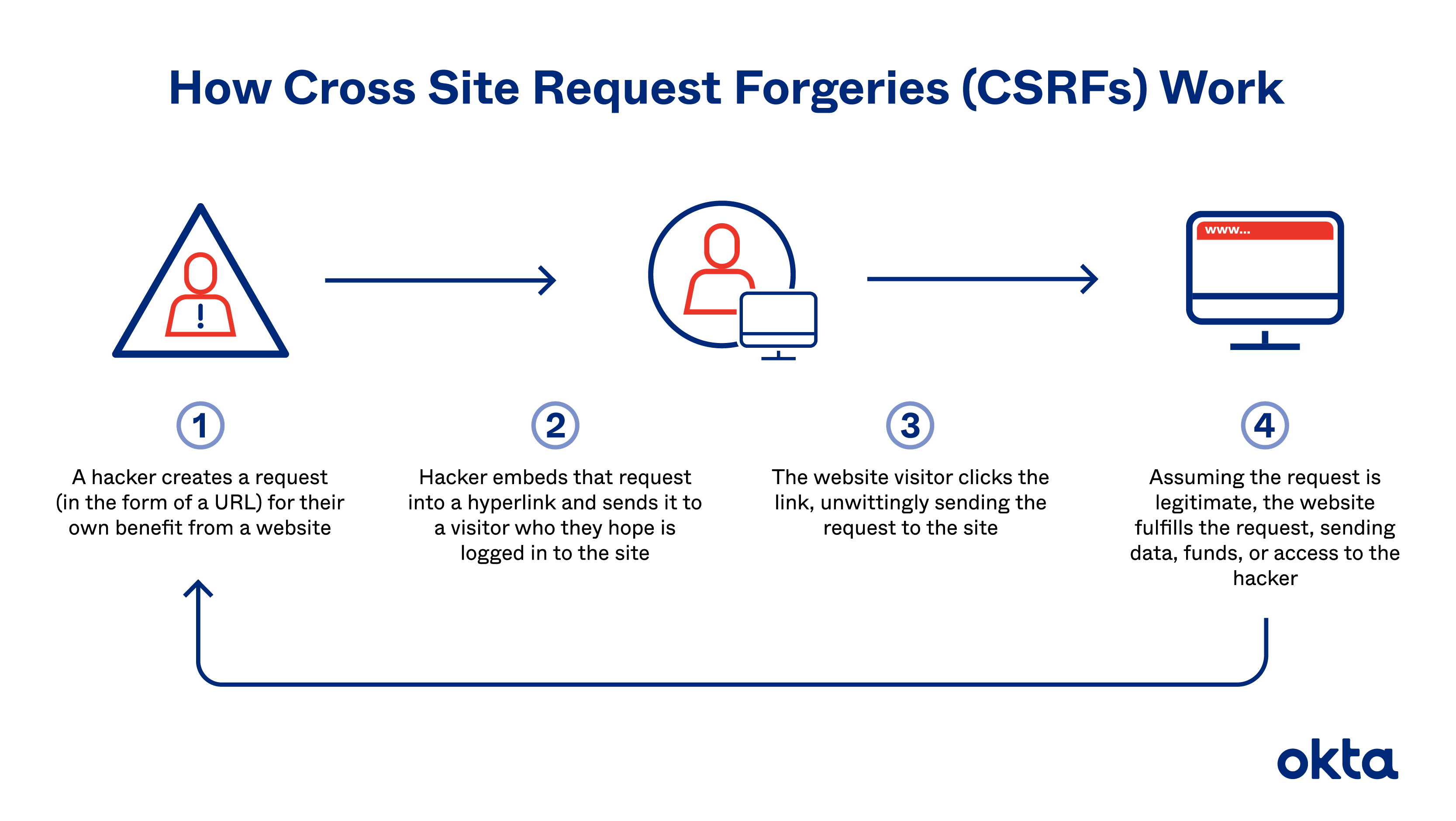
- Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're
currently like
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
- Q: How can you defend yourself against CSRF attacks?
To defend yourself against CSRF attacks, you can opt for two available methods.
https://mindmajix.com/cyber-security-interview-questions
- If a logged-in user clicks that link, what would stop the picture from being submitted? You guessed it: Nothing. Hacker wins.
WordPress uses nonces (numbers used once) to validate the request
The basic process looks like this:
That
On the back end,
https://css-tricks.com/wordpress-front-end-security-csrf-and-nonces/
- DOM Based XSS
Definition
DOM Based XSS (or as it
https://www.owasp.org/index.php/DOM_Based_XSS
- DOM Based XSS
simply be found It can only be observed
- What do you mean by Cross Site Scripting?
Cross Site Scripting
Q: What can you defend yourself from Cross Site Scripting attack?
Like any other injection attack, Cross Site Scripting attack can also
There are software or applications available for doing this, like the XSS Me for Firefox and
https://mindmajix.com/cyber-security-interview-questions
- XSS-Me is the Exploit-Me
tool currently . rnrnThe that are
https://addons.mozilla.org/en-US/firefox/addon/xss-me/
HACKING TUTORIAL - XSS Me
- What is Cross-Site Request Forgery?
when an attacker gets a victim’s browser to make requests, ideally with their credentials included, without their knowing. A solid example of this is when an IMG tag points to a URL associated with an action, e.g.
What is the difference between stored and reflected XSS?
Stored is on a static page or pulled from a database and displayed to the user directly. Reflected comes from the user in the form of a request (usually constructed by an attacker
What are the common defenses against XSS?
Input Validation/Output Sanitization, with
What is spear phishing
Spear phishing is a social engineering attack in which a perpetrator, disguised as a trusted individual, tricks a target into clicking a link in a spoofed email, text message or instant message. As a result, the target unwittingly reveals sensitive information, installs malicious programs (malware) on their network or executes the first stage of an
While similar to phishing and whaling attacks, spear phishing
Spear phishing vs. phishing and whaling attacks
Phishing emails are impersonal, sent in bulk and often contain spelling errors or other mistakes that reveal their malicious intent.
Spear phishing emails
Whaling uses deceptive email messages targeting high-level decision makers within an organization, such as CEOs, CFOs, and other executives.
The difference between whaling and spear phishing is that whaling
Spear phishing mitigation
several risk prevention measures can help, including two-factor authentication (2FA), password management policies and educational campaigns.
Two factor authentication
2FA helps secure login to sensitive applications by requiring users to have two things: something they know, such as a password and
Password management policies
A prudent password management policy should take steps to prevent employees from using corporate access passwords on fake external websites.
Educational campaigns
At the organizational level, enterprises can raise awareness and actively train employees
https://www.imperva.com/learn/application-security/spear-phishing/
- 5 Practical Scenarios for XSS Attacks
how to create XSS attack
Hijack a user’s session
Perform unauthorized activities
Perform phishing attacks
Capture key strokes
Steal sensitive information
If the application does not escape special characters in the input/output and reflects user input as-is back to the browser, an adversary may
XSS Attack 1: Hijacking the user session
XSS Attack 2: Perform unauthorized activities
XSS Attack 3: Phishing to steal user credentials
XSS Attack 4: Capture the key strokes by injecting a keylogger
XSS Attack 5: Stealing sensitive information
https://pentest-tools.com/blog/xss-attacks-practical-scenarios/
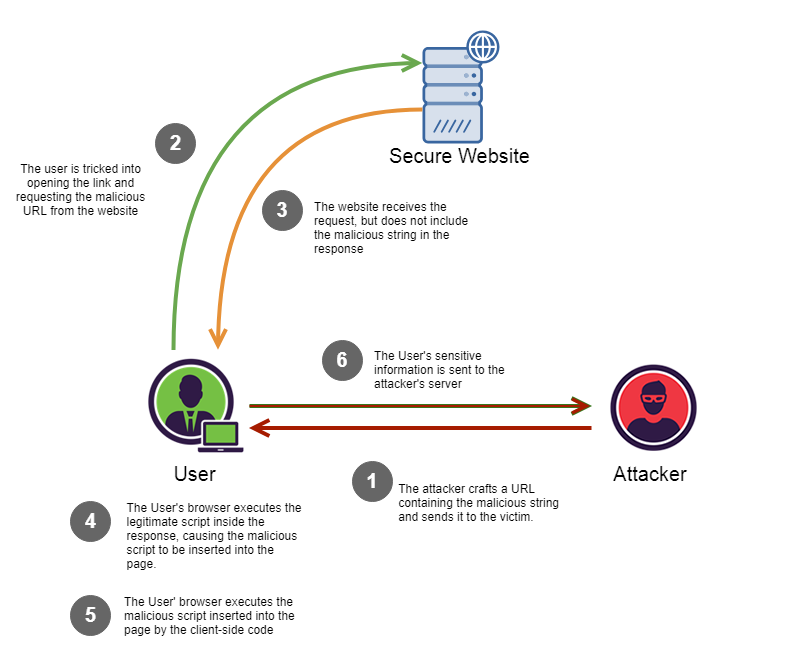
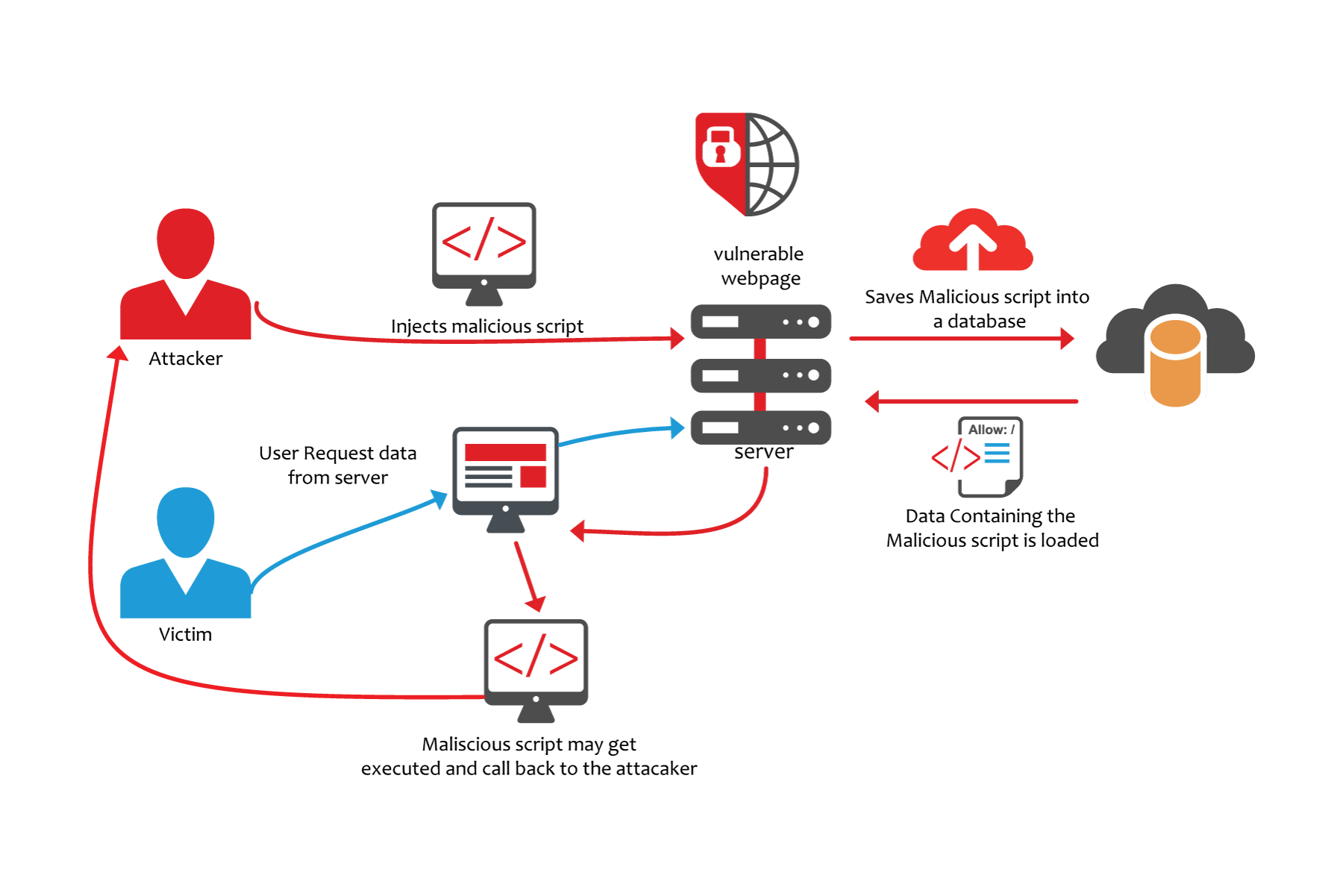
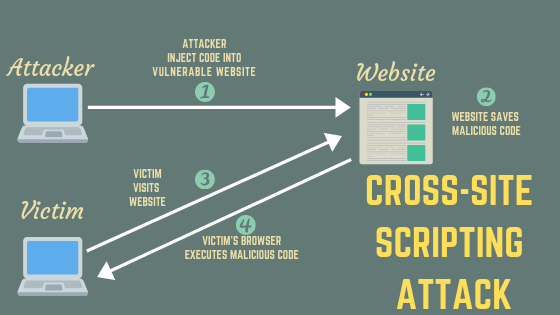
- What is Cross-Site Scripting?
Cross-site scripting (XSS) is a code injection security attack which delivers malicious, client-side scripts to a user’s web browser for execution. Targets
Types of Cross-Site Scripting Attacks
Reflected XSS
A reflected XSS attack involves a vulnerable website accepting data (i.e. malicious script) sent by the target’s own web browser to attack the target with. Because the malicious script
Persistent XSS
As the name implies,
DOM-Based XSS
Another type of XSS attack is DOM-based, where the vulnerability exists in the client-side scripts that the site/app always provides to visitors. This attack differs from reflected and persistent XSS attacks in that the site/app doesn’t directly serve up the malicious script to the target’s browser
https://www.rapid7.com/fundamentals/cross-site-scripting/
- Preventing XSS: 3 Ways to Keep Cross-Site Scripting Out of Your Apps
1. Escaping
The first method you can and should use to prevent XSS vulnerabilities from appearing in your applications is by escaping user input. Escaping data means taking the data an application has received and ensuring
If your page doesn’t allow users to add their own code to the page,
2. Validating Input
Validating input is
3. Sanitizing
Sanitizing user input is especially helpful on sites that allow HTML markup, to ensure data received can do no harm to users
https://www.checkmarx.com/2017/10/09/3-ways-prevent-xss/
- This article provides a simple positive model for preventing XSS using output escaping/encoding properly.
XSS Prevention Rules
RULE #0 - Never Insert Untrusted Data Except in Allowed Locations
RULE #1 - HTML Escape Before Inserting Untrusted Data into HTML Element Content
RULE #2 - Attribute Escape Before Inserting Untrusted Data into HTML Common Attributes
RULE #3 - JavaScript Escape Before Inserting Untrusted Data into JavaScript Data Values
RULE #3.1 - HTML escape JSON values in an HTML context and read the data with JSON
RULE #4 - CSS Escape And Strictly Validate Before Inserting Untrusted Data into HTML Style Property Values
RULE #5 - URL Escape Before Inserting Untrusted Data into HTML URL Parameter Values
RULE #6 - Sanitize HTML Markup with a Library Designed for the Job
RULE #7 - Avoid JavaScript URL's
RULE #8 - Prevent DOM-based XSS
Bonus Rule #1: Use
Bonus Rule #2: Implement Content Security Policy
Bonus Rule #3: Use an Auto-Escaping Template System
Bonus Rule #4: Use the X-XSS-Protection Response Header
Bonus Rule #5: Properly use modern JS frameworks like Angular (2+) or
https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
- What
does trigger an incident investigation?
Keepnet Labs’ Incident Responder is one helpful tool that does this by installing a user-friendly plugin that lets end-users instantly report a suspicious email to the Keepnet Incident Response Platform ( IRP). The alert can be sent with only one click. This way, the incident response time is reduced from minutes to seconds.
A user reports a suspicious email with a single click using phishing reporter add-in installed in Outlook and sends it automatically to the analysis. If the results are malicious, an incident response operation is started on the inboxes of the other users.
https://www.keepnetlabs.com/protecting-employees-inboxes-phishing-threats-incident-response/
- Security Incident Phishing workflow template
The Security Incident - Phishing - Template allows you to perform a series of tasks designed to handle spear phishing emails on your network.
https://docs.servicenow.com/bundle/newyork-security-management/page/product/security-incident-response-orchestration/task/si-phishing-template.html




Nice post.
ReplyDeleteTelugu movies download
Indian movies download
movies download
Movies watch online
Online movies watch
Hindi movies download
Should there be another persuasive post you can share next time, I’ll be surely waiting for it.
ReplyDeletewatch online free movies
micro strategy certification training
ReplyDeletemsbi course training