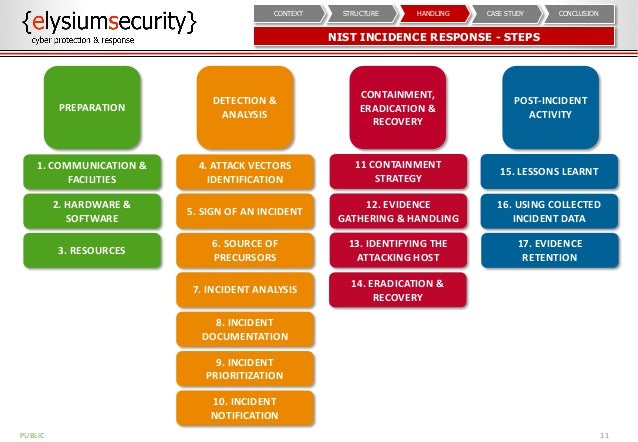
Preparation—review and codify an organizational security policy, perform a risk assessment, identify sensitive assets, define which are critical security incidents the team should focus on, and build a Computer Security Incident Response Team (CSIRT).
Identification—monitor IT systems and detect deviations from normal operations, and see if they represent actual security incidents. When an incident is discovered, collect additional evidence, establish its type and severity, and document everything.
Containment—perform short-term containment, for example by isolating the network segment that is under attack. Then focus on long-term containment, which involves temporary fixes to allow systems to be used in production, while rebuilding clean systems.
Eradication—remove malware from all affected systems, identify the root cause of the attack, and take action to prevent similar attacks in the future.
Recovery—bring affected production systems back online carefully, to prevent additional attacks. Test, verify and monitor affected systems to ensure they are back to normal activity.
Lessons learned—no later than two weeks from the end of the incident, perform a retrospective of the incident. Prepare complete documentation of the incident, investigate the incident further, understand what was done to contain it and whether anything in the incident response process could be improved.
https://www.cynet.com/incident-response/incident-response-sans-the-6-steps-in-depth/
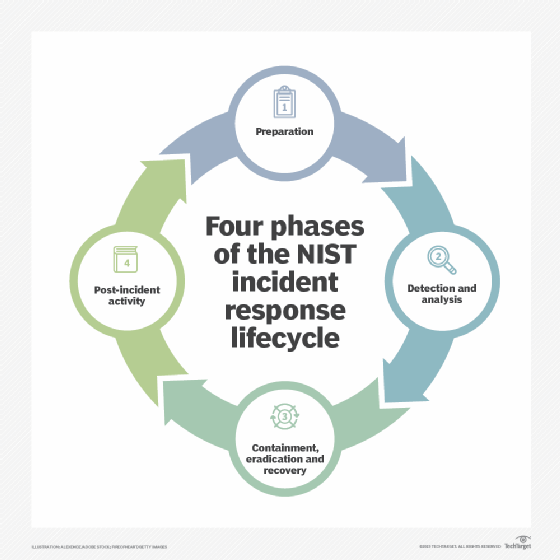
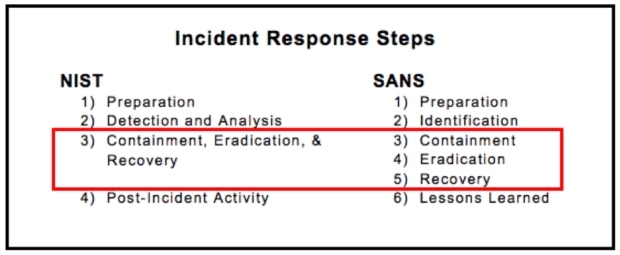
The Difference Between NIST and SANS Incident Response Steps
NIST and SANS have all the same components and the same flow but different verbiage and clustering
Step 1) Preparation = Step 1) Preparation
This step is similar for both NIST and SANS.
In this step you compile a list of all your assets, including but not limited to: servers, networks, applications, and critical endpoints (like C-level laptops).
After you’ve compiled your asset list, rank them by level of importance.
Then monitor their traffic patterns so you can create baselines to be used for comparisons later.
Create a communication plan, with guidance on who to contact, how, and when based on each incident type
Determine which security events, and at what thresholds, these events should be investigated.
Then create an incident response plan for each type of incident
It can be improved through security event simulations, where you identify holes in your process, but it will also be improved after actual events
The point is, get a process in place.
Step 2) Detection and Analysis = Step 2) Identification
this step is similar for both NIST and SANS, but with different verbiage.
At this point in the process, a security incident has been identified.
This is where you go into research mode.
Gather everything you can on the the incident.
Determine the entry point and the breadth of the breach.
This process is made substantially easier and faster if you’ve got all your security tools filtering into a single location.
Step 3) Containment, Eradication, & Recovery = Steps 3-5) Containment. Eradication. Recovery.
NIST and SANS kind-of part ways in their similarities before agreeing again on the final step
NIST views the process of containment, eradication, and recovery as a singular step with multiple components.
SANS views them as their own independent steps.
Containment aims to stop the bleeding. Here is where you patch the threat’s entry point.
Eradication aims to remove the threat.If the threat gained entry from one system and proliferated into other systems, you’ll have more work
Recovery aims to get the system operational if it went down or simply back to business as usual if it didn’t
Step 4) Post-Incident Activity = Step 6) Lessons Learned
NIST and SANS are in agreement again in their last step, if not in verbiage, in spirit.
This step provides the opportunity to learn from your experience so you can better respond to future security events.
Take a look at the incident with a humble but critical eye to identify areas for improvement.
Then go add those improvements to your documentation.
Some scenarios can’t even be fathomed until they’ve occurred.
The threat landscape is also ever-evolving so your incident response process will naturally need the occasional update.
Which Incident Response Steps Framework is Better?
Does it make more sense to you to break containment, eradication, and recovery into their own steps or keep them grouped in a single step?
both NIST and SANS have incident handling checklists available to get you started. Just remember to customize them to your specific needs and company’s environment
https://cybersecurity.att.com/blogs/security-essentials/incident-response-steps-comparison-guide
- SANS Incident Response Plan
Preparation—review and codify an organizational security policy, perform a risk assessment, identify sensitive assets, define which are critical security incidents the team should focus on, and build a Computer Security Incident Response Team (CSIRT).
Identification—monitor IT systems and detect deviations from normal operations, and see if they represent actual security incidents. When an incident is discovered, collect additional evidence, establish its type and severity, and document everything.
Containment—perform short-term containment, for example by isolating the network segment that is under attack. Then focus on long-term containment, which involves temporary fixes to allow systems to be used in production, while rebuilding clean systems.
Eradication—remove malware from all affected systems, identify the root cause of the attack, and take action to prevent similar attacks in the future.
Recovery—bring affected production systems back online carefully, to prevent additional attacks. Test, verify and monitor affected systems to ensure they are back to normal activity.
Lessons learned—no later than two weeks from the end of the incident, perform a retrospective of the incident. Prepare complete documentation of the incident, investigate the incident further, understand what was done to contain it and whether anything in the incident response process could be improved.
https://www.cynet.com/incident-response/incident-response-sans-the-6-steps-in-depth/


No comments:
Post a Comment