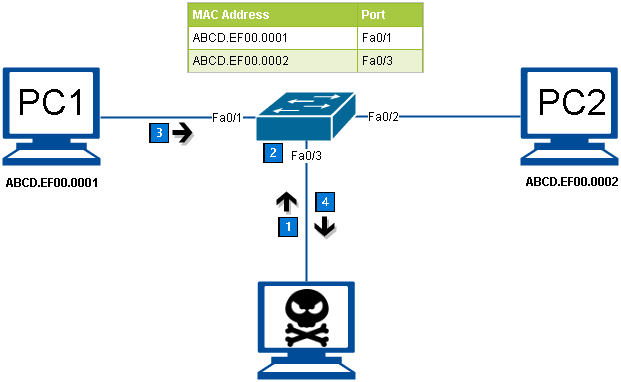
- Computer A sends traffic to computer B. The switch receives the frames and looks up the destination MAC address in its MAC address table. If the switch does not have the destination MAC in the MAC address table, the switch then copies the frame and sends it out every switch port like a broadcast. This means that not only PC B receives the frame, PC C also receives the frame from host A to host B, but because the destination MAC address of that frame is host B, host C drops that frame.
PC B receives the frame and sends a reply to PC A. The switch then learns that the MAC address for PC B is located on port 2 and writes that information into the MAC address table. From now on any frame sent by host A (or any other host) to host B is forwarded to port 2 of the switch and not broadcast out every port.
https://howdoesinternetwork.com/2011/mac-address-flooding
- After launching a successful MAC flooding attack, a malicious user can use a packet analyzer to capture sensitive data being transmitted between other computers, which would not be accessible were the switch operating normally. The attacker may also follow up with an ARP spoofing attack which will allow them to retain access to privileged data after switches recover from the initial MAC flooding attack.
https://en.wikipedia.org/wiki/MAC_flooding
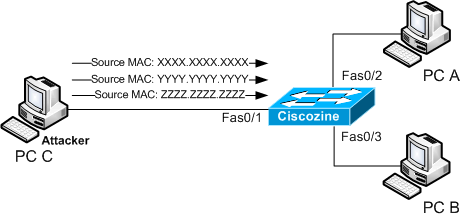
the attacker floods the switch with a huge number of requests, each with a fake MAC address. When the MAC table reaches the allocated storage limit, it begins removing old addresses with the new ones.
After removing all the legitimate MAC addresses, the switch starts broadcasting all the packets to every switch port and takes on the role of network hub. Now, when two valid users attempt to communicate, their data is forwarded to all available ports, resulting in a MAC table flooding attack.
As a result, the attacker will be able to capture all the ingoing and outgoing traffic passing through the user’s system and can sniff the confidential data it contains.
https://linuxhint.com/mac-flooding-attack/
- Static MAC address entries are manually configured and delivered to each LPU. Static MAC address entries never age.
The static MAC address entries saved in the system are not lost after a system restart, LPU hot swap, or LPU reset.
Dynamic MAC address entries are obtained by learning source MAC addresses of packets on an interface, and can be aged.
Dynamic MAC address entries are lost after a system restart, LPU hot swap, or LPU reset.
https://support.huawei.com/view/contentview!getFileStream.action?mid=SUPE_DOC&viewNid=EDOC1000177795&nid=EDOC1000177795&partNo=j005&type=htm
- Setting the Aging Time for Dynamic Entries
Learned MAC addresses are entered in the table as dynamic entries, which means that they are subject to aging.
For any dynamic entry, if no packet arrives on the switch with the MAC address as the source or destination address within the timer period, the address is removed from the table. The default aging time is 1800 seconds
https://www.dell.com/support/manuals/tr-tr/dell-emc-os-9/s3048-on-9.14.2.6-config-pub/setting-the-aging-time-for-dynamic-entries?guid=guid-345e5a06-bd27-4504-b6ce-efc9ec430f31&lang=en-us
- A valid MAC address must satisfy the following conditions:
It must contain 12 hexadecimal digits.
One way to represent them is to form six pairs of the characters separated with a hyphen (-) or colon(:). For example, 01-23-45-67-89-AB is a valid MAC address.
Another way to represent them is to form three groups of four hexadecimal digits separated by dots(.). For example, 0123.4567.89AB is a valid MAC address.
https://www.geeksforgeeks.org/how-to-validate-mac-address-using-regular-expression/

No comments:
Post a Comment