- A bastion host is a special-purpose computer on a network specifically designed and configured to withstand attacks,
(attack surface)
The computer generally hosts a single application or process, for example, a proxy server or load balancer, and all other services are removed or limited to reduce the threat to the computer
It is hardened in this manner primarily due to its location and purpose, which is either on the outside of a firewall or inside of a demilitarized zone (DMZ) and usually involves access from untrusted networks or computers.
There are two common network configurations that include bastion hosts and their placement. The first requires two firewalls, with bastion hosts sitting between the first "outside world" firewall, and an inside firewall, in a DMZ.
Often, smaller networks do not have multiple firewalls, so if only one firewall exists in a network, bastion hosts are commonly placed outside the firewall
These are several examples of bastion host systems/services:
DNS (Domain Name System) server
Email server
FTP (File Transfer Protocol) server
Honeypot
Proxy server
VPN (Virtual Private Network) server
Web server
https://en.wikipedia.org/wiki/Bastion_host
The ideal “Modern Bastion Host” has the following traits:
Uses SSH certificates
Centrally managed
Cloud platform agnostic
Logs to a Cloud Data Warehouse
Runtime security & alerting
https://eng.sigmacomputing.com/modern-bastion-hosts-abed8c7c7c63
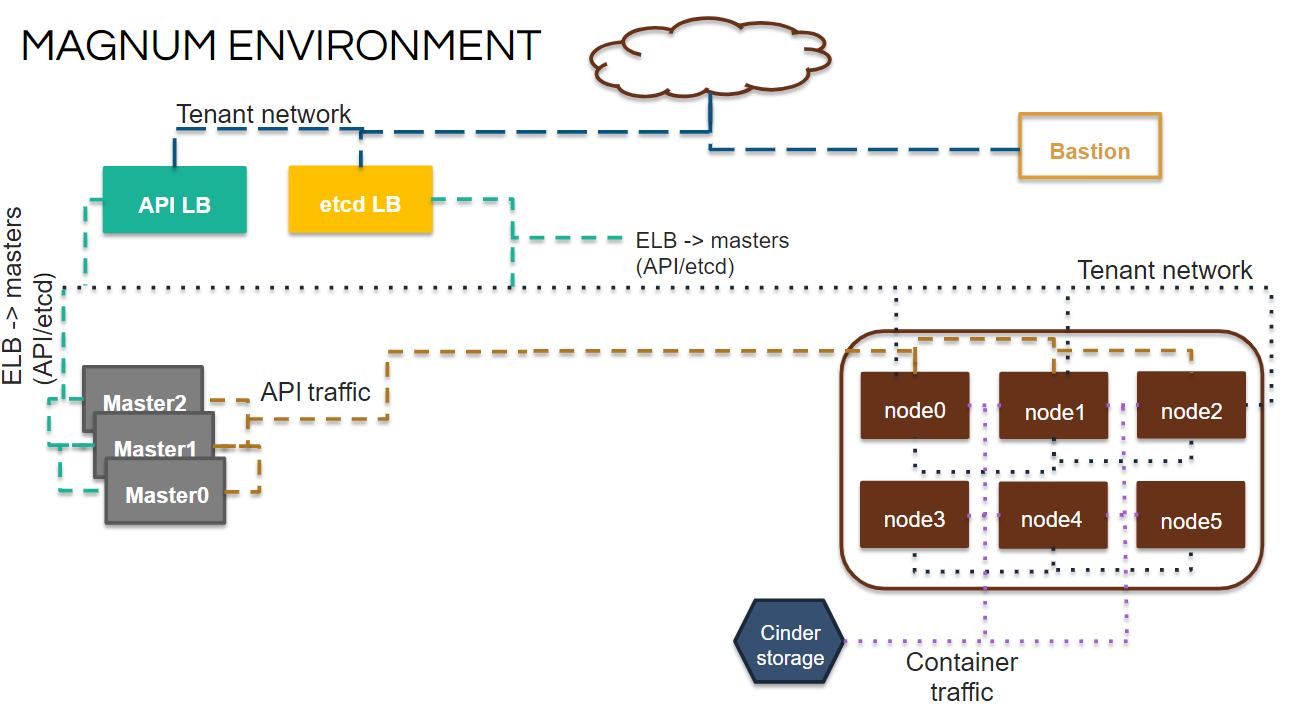
- Bastion hosts are hosts that can be used as a jump point to an inaccessible network. This is useful in the context of an OpenStack project as you don't necessarily want to reserve a floating IP for each of all instances. This way you can isolate certain resources so that there is only a single point of access to them and also preserve floating IP addresses so that you don't exceed quota.
https://github.com/CSCfi/openstack-bastion
Bastion
Access with SSH through a single point-of-contact: Bastion
.By default, all nodes have a public IP and are accessible to SSH from the outside world. With a Bastion you can limit the vulnerabilities of penetration to your cluster.
https://fakecineaste.blogspot.com/2019/05/kubernetes-hardening.html

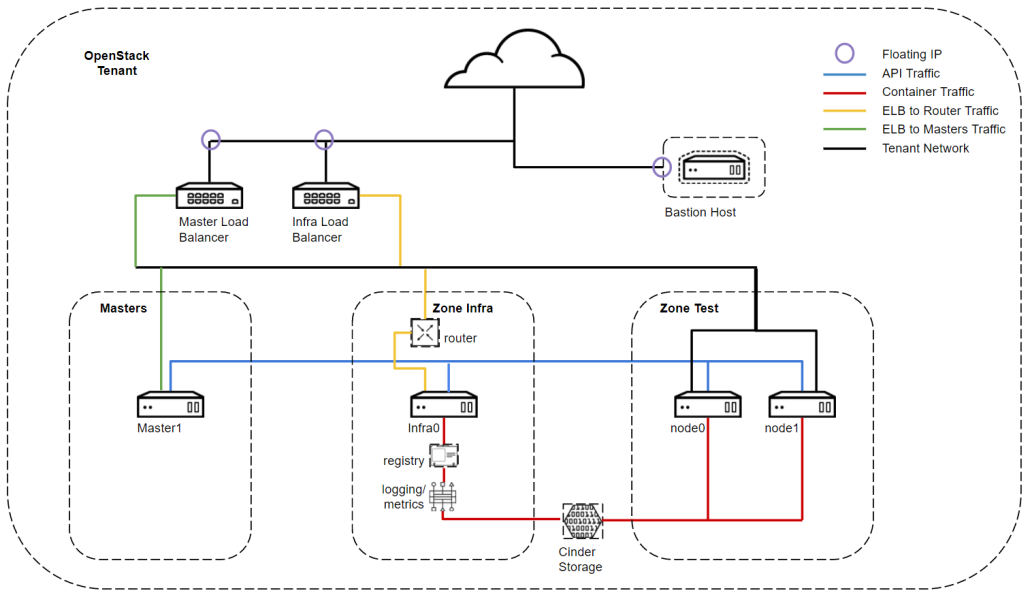
A bastion host is a jump-host that the orchestration engine uses to access all computes in a private network to deploy a service catalog. An admin network is a private network connecting to all compute nodes. The orchestration engine uses the admin network for provisioning. The following tutorial shows how you can define a bastion host and an admin network in the topology.
During the deployment, the orchestration engine creates the security group Secgroup_BastionHost on the bastion host, which allows TCP incoming traffic on port 22 from the remote IP of the orchestration engine. As a result, it can connect to the bastion host over the public network (step 1)
The orchestration engine uses the bastion host as a jump host to SSH to the private Compute_2 in the admin network and deploy the service catalog HelloWorld (step 2). To access Compute_2 over the bastion host, the orchestrator creates the security group Secgroup_Admin on Compute_2, which allows incoming traffic from the remote Secgroup_BastionHost on port 22. It also enables TCP forwarding on the bastion host.
https://docs.designer.otc-service.com/examples/bastion_host/bastion_host/

- How to Record SSH Sessions Established Through a Bastion Host
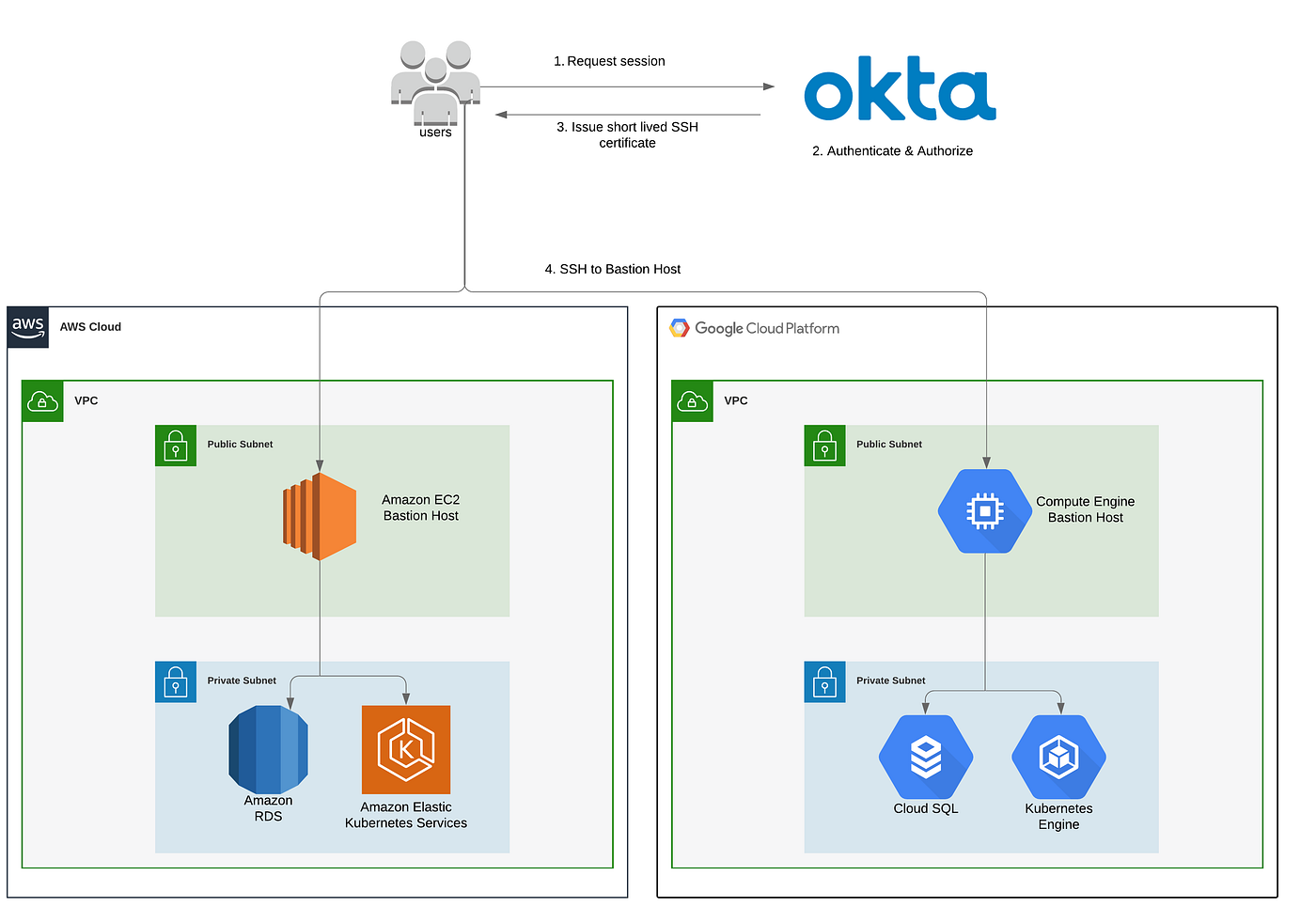
A bastion host is a server whose purpose is to provide access to a private network from an external network, such as the Internet. Because of its exposure to potential attack, a bastion host must minimize the chances of penetration. For example, you can use a bastion host to mitigate the risk of allowing SSH connections from an external network to the Linux instances launched in a private subnet of your Amazon Virtual Private Cloud (VPC)
The bastion host runs on an Amazon EC2 instance that is typically in a public subnet of your Amazon VPC.
Linux instances are in a subnet that is not publicly accessible, and they are set up with a security group that allows SSH access from the security group attached to the underlying EC2 instance running the bastion host
Bastion host users connect to the bastion host to connect to the Linux instances
For example, you could have the bastion host in a separate Amazon VPC and a VPC peering connection between the two Amazon VPCs.
solution for recording SSH sessions resides on the bastion host only
You configure the solution by running commands at launch as the root user on an Amazon Linux instance.
It is a best practice to harden your bastion host because it is a critical point of network security. Hardening might include disabling unnecessary applications or services, tuning the network stack, and the like.
https://aws.amazon.com/blogs/security/how-to-record-ssh-sessions-established-through-a-bastion-host/
- SSH traffic to servers that are not directly accessible via SSH is instead directed through a bastion host, which proxies the connection between the SSH client and the remote servers.
First, you’ll want to ensure you have public key authentication properly configured, both on the bastion host as well as the remote instances.
You can use the same key for both the bastion host and the remote instances, or different keys; you’ll just need to ensure that the keys are loaded by ssh-agent appropriately so they can be used as needed.
Next, you’ll want to ensure that name resolution is working—both from the client to the bastion as well as from the bastion to the remote instances
The bastion host is going to use the hostname specified on the ssh command line, so if it can’t resolve the name the connection will fail.
Finally, you’ll want to configure the ProxyCommand setting for the remote instances in your SSH configuration file. For example, let’s say that you had a remote instance named “private1” and you wanted to run SSH connections through a bastion host called “bastion”.
With this configuration in place, when you type ssh user@private1 SSH will establish a connection to the bastion host and then through the bastion host connect to “private1”, using the specified keys. The user won’t see any of this; he or she will just see a shell for “private1” appear.
(try running who on the remote node), you’ll see the connections are coming from the bastion host, not the original SSH client.
https://blog.scottlowe.org/2015/11/21/using-ssh-bastion-host/
- Typical uses for local port forwarding include:
Tunneling sessions and file transfers through jump servers
Connecting to a service on an internal network from the outside
Connecting to a remote file share over the Internet
https://www.ssh.com/academy/ssh/tunneling/example
- SSH forwarding is useful for
transporting network data of services that use an unencrypted protocol, such as VNC or FTP ,
accessing geo-restricted content, or
bypassing intermediate firewalls.
Basically, you can forward any TCP port and tunnel the traffic over a secure SSH connection.
There are three types of SSH port forwarding:
Local Port Forwarding. - Forwards a connection from the client host to the SSH server host and then to the destination host port.
Remote Port Forwarding. - Forwards a port from the server host to the client host and then to the destination host port.
Dynamic Port Forwarding. - Creates a SOCKS proxy server that allows communication across a range of ports.
https://linuxize.com/post/how-to-setup-ssh-tunneling/



No comments:
Post a Comment