use
all traffic between your computer and
then
all webpages
with
- How VPN Works
Using VPNs, an organization can help secure private network traffic over an unsecured network, such as the Internet. VPN helps provide a secure mechanism for encrypting and encapsulating private network traffic and moving it through an intermediate network.
https://technet.microsoft.com/en-us/library/cc779919(v=ws.10).aspx
- A virtual private network (VPN) extends a private network across a public
network, and enables users to send and receive data across shared or public networks as iftheir computing devices were directly connected to the private network. VPNs may allow employeesto securely access a corporate intranet while located outside the office. They are usedto securely connect geographically separated offices of an organization, creating one cohesive network. Individual Internet users may secure their transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and locationin order to stay anonymous on the internet. However, some Internet sites block access to known VPN technology to prevent the circumvention of their geo-restrictions
- The
IPsec VPN service provides secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session.
- Using Virtual Private Networks
Introduction
This publication provides guidance on how
For
User accounts
User accounts for VPN connections should be separate from standard user accounts. This will limit the activities
Further, the permissions applied to VPN user accounts should
This will minimise the severity of a successful compromise. VPN user accounts with minimum permissions, that can only perform basic operations on a network, will also impede the ability of an adversary to gain a foothold on a network.
For example, if a user only needs access to email services,
Multi-factor authentication
Multi-factor authentication should
Device authentication
Device authentication
VPN termination points
Split tunnelling
Devices accessing a network via a VPN connection should disable split tunnelling.
Split tunnelling allows a device to
Organisations should ensure that web browsing from a device connected to
Whitelisting connection sources
If a site-to-site VPN implementation supports whitelisting,
This will prevent unauthorised connection attempts even when legitimate credentials have
If a site-to-site VPN implementation does not support MAC or IP address whitelisting, VPN connection log entries should
https://www.cyber.gov.au/publications/using-vpns
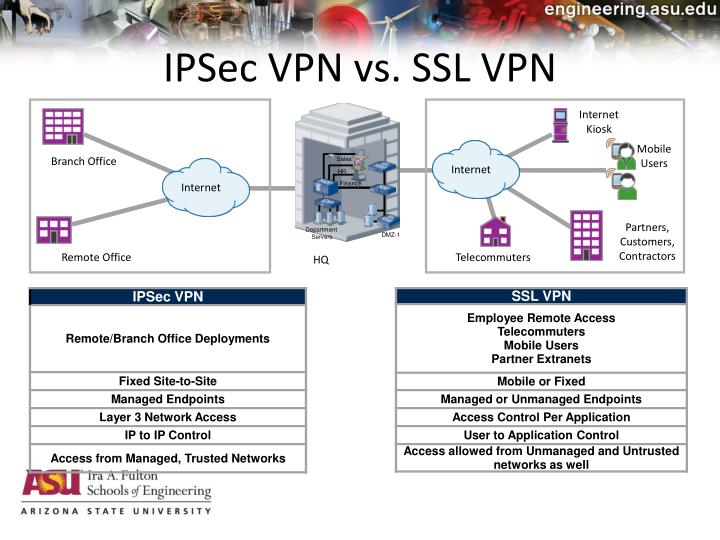
- VPN encryption explained:
IPSec vs SSL
This article, however, will examine how major commercial VPN providers
VPN protocols that use
This article compares and contrasts
The differences between varying types of encryption include:
Encryption strength, or the method and degree to which your data
How the encryption keys
What interfaces, protocols, and ports they use
What OSI layers they run on
Ease of deployment
Performance (read: speed)
Security
SSL VPNs don’t have this problem because they use public key cryptography to negotiate a handshake and securely exchange encryption keys
Firewall traversal
NAT firewalls often exist on wifi routers and other network hardware. To protect against threats, they throw out any internet traffic that
To get around this, many
OpenVPN uses port 1194 by default for UDP traffic, but
Speed and reliability
Both are reasonably fast, but IKEv2/
Ease of use
SSL works by default in most web browsers, but a third-party application is usually necessary to use OpenVPN.
the
The reason is that
It is more difficult to restrict access to specific resources.
SSL VPNs
OpenVPN, which uses the OpenSSL library for encryption and
It can support either the UDP or TCP protocol.
https://www.comparitech.com/blog/vpn-privacy/ipsec-vs-ssl-vpn/
Explanation of VPN Technologies:
Site-to-Site VPN:
- Creates a secure tunnel between two network locations, allowing them to communicate privately over the public internet.
- Used for connecting geographically dispersed offices, data centers, or cloud environments.
- Provides secure access to resources and applications located on the remote network.
- Commonly implemented with technologies like IPsec, DMVPN, or FlexVPN.
DMVPN (Dynamic Multipoint VPN):
- An extension of IPsec designed for efficient Site-to-Site VPN connections over shared infrastructure, such as MPLS or the public internet.
- Provides dynamic tunnel establishment and communication between multiple sites without requiring dedicated hardware at each location.
- Efficiently utilizes network resources and simplifies VPN deployment and management.
IPsec (IP Security):
- A suite of protocols and standards for securing IP communication.
- Encrypts data in transit and provides authentication and integrity checks.
- Commonly used for implementing Site-to-Site and remote access VPNs.
- Offers strong security capabilities but can be complex to configure and manage.
FlexVPN (Flexible VPN):
- A Cisco proprietary technology that simplifies VPN deployment and management.
- Combines the features of IPsec, DMVPN, and other VPN technologies into a single platform.
- Provides a centralized management interface and configuration options for various VPN scenarios.
- Offers automatic tunnel establishment and policy enforcement for easier deployment and management.
IKE (Internet Key Exchange):
- A protocol responsible for key negotiation and establishment of secure IPsec tunnels.
- Utilizes strong cryptographic algorithms to ensure secure communication.
- Different versions of IKE exist, with IKEv2 being the latest and most secure option.
RAVPN (Remote Access VPN):
- Provides secure remote access to corporate networks for individual users or devices.
- Allows users to connect to the network from anywhere with an internet connection.
- Often implemented using technologies like IPsec or SSL VPN.
GETVPN (Generic Encapsulation Transport VPN):
- A Cisco proprietary technology for remote access VPN connections.
- Utilizes GRE (Generic Routing Encapsulation) to encapsulate IPsec packets.
- Provides secure tunnel establishment and data encryption for remote users.
In summary:
- Site-to-Site VPN creates secure links between networks.
- DMVPN is a dynamic and efficient Site-to-Site VPN solution.
- IPsec is a suite of protocols for secure IP communication.
- FlexVPN simplifies VPN deployment and management.
- IKE negotiates keys and establishes secure IPsec tunnels.
- RAVPN provides secure remote access for individual users.
- GETVPN is a Cisco technology for secure remote access.
Choosing the appropriate technology depends on the specific requirements of your network and security needs.
Sure, these are different VPN (Virtual Private Network) technologies used to establish secure connections over the internet or untrusted networks. Here's an overview of each:
1. Site-to-Site VPN (Site2Site):
- Description: Site-to-Site VPN connects multiple sites or networks securely over the internet, allowing communication between different locations of an organization.
- Use Case: Ideal for connecting branch offices, data centers, or multiple locations within an organization to create a seamless network.
2. Dynamic Multipoint VPN (DMVPN):
- Description: DMVPN is a scalable VPN solution that simplifies the hub-and-spoke network topology, allowing direct spoke-to-spoke communication without requiring traffic to pass through the hub.
- Use Case: Suited for networks with multiple branch locations needing direct communication while maintaining security and scalability.
3. IPsec (Internet Protocol Security):
- Description: IPsec is a protocol suite used to secure communication at the IP layer by encrypting and authenticating IP packets.
- Use Case: Widely used in VPNs to establish secure connections, ensuring confidentiality, integrity, and authenticity of transmitted data.
4. FlexVPN / IKE (Internet Key Exchange):
- Description: FlexVPN is a highly modular and scalable VPN framework developed by Cisco, providing flexibility in configuration and deployment options. IKE is a key management protocol used within FlexVPN to establish security associations.
- Use Case: Offers versatility and adaptability in deploying VPN solutions across various network architectures.
5. Remote Access VPN (RAVPN):
- Description: Remote Access VPN allows individual users or remote devices to securely connect to a corporate network from external locations, typically over the internet.
- Use Case: Enables remote employees or users to access resources on a private network securely while working from different locations.
6. Group Encrypted Transport VPN (GETVPN):
- Description: GETVPN is a type of VPN architecture that provides encryption and authentication for IP multicast traffic within a private network.
- Use Case: Suited for enterprises needing to encrypt and secure multicast traffic across their network infrastructure.
Each VPN technology has its strengths and applications depending on the specific requirements of an organization, such as scalability, security, ease of deployment, or support for different network architectures. Choosing the right VPN solution involves considering factors like network topology, security needs, scalability, and the types of traffic to be secured.
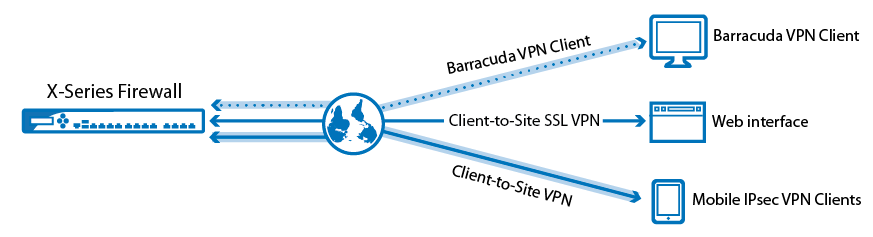
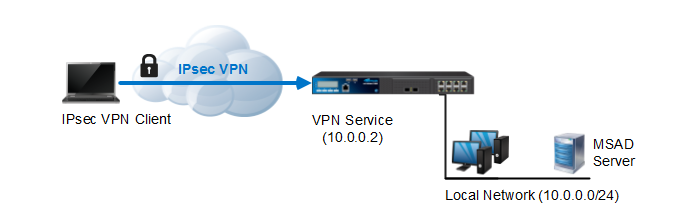

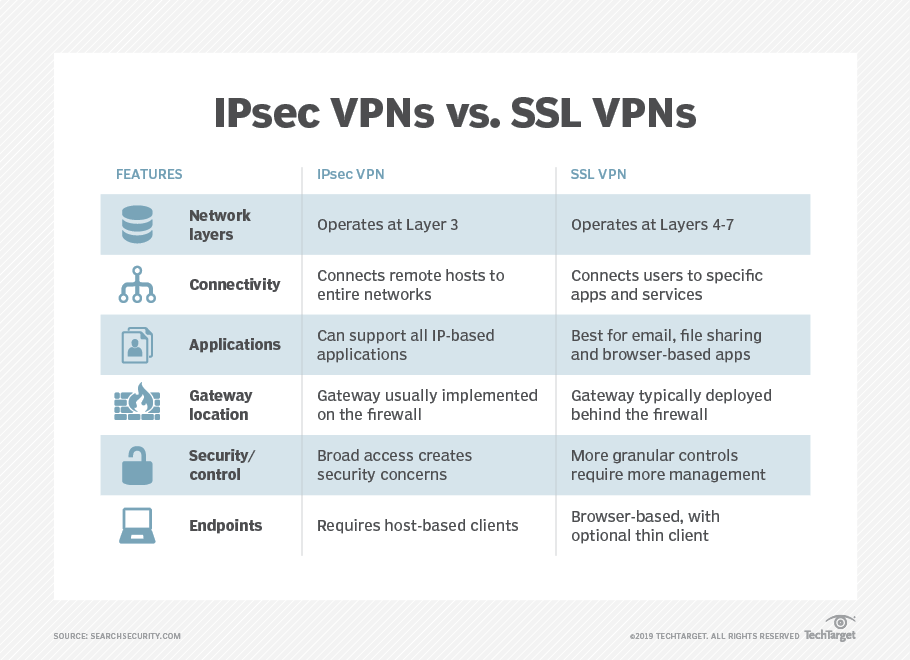



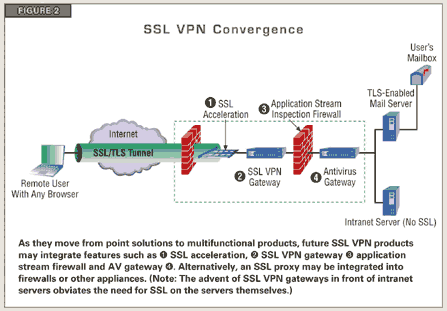


I got here much interesting stuff. The post is great! Thanks for sharing it! VPN service for Windows
ReplyDelete