- Your private path to access network resources and services securely
- Linux Notes (without RPM)
If you are using Debian, Gentoo, or a non-RPM-based Linux distribution, use your distro-specific packaging mechanism such as apt-get on Debian or emerge on Gentoo.
It is also possible to install OpenVPN on Linux using the universal
tar
Then cd to the top-level directory and type:
./configure
make
make install
OpenVPN is a full-featured SSL VPN which implements OSI layer 2 or 3 secure network extension using the industry standard SSL/TLS protocol, supports flexible client authentication methods based on certificates, smart cards, and/or username/password credentials, and allows
https://openvpn.net/index.php/open-source/documentation/howto.html#install
- What is openNAC
http://www.opennac.org/opennac/en.html
FreeNAC .
PacketFence
http://packetfence.org/
Captive-portal for registration and remediation
Centralized wired and wireless management
802.1X support
Layer-2 isolation of problematic devices
Integration with the Snort IDS and the Nessus vulnerability scanner
https://www.techrepublic.com/article/how-to-install-packetfence-on-centos-7/
database server (MariaDB)
web server (Apache)
DHCP server (PacketFence)
RADIUS server (FreeRADIUS )
firewall (iptables )
3.2. Minimum Hardware Requirements
The following provides a list of the minimum server hardware recommendations:
Intel or AMD CPU 3 GHz, 2 CPU cores
12 GB of RAM (16 GB recommended)
100 GB of disk space (RAID-1 recommended)
1 network card (2 recommended)
3.3. Operating System Requirements
PacketFence supports the following operating systems on the x86_64 architecture:
Red Hat Enterprise Linux 7. x Server
Community ENTerprise Operating System (CentOS) 7. x
Debian 9.0 (Stretch)
https://packetfence.org/doc/PacketFence_Installation_Guide.html
Malware detection and alerting: Along with internal features,PacketFence can work with remote sensors like from Snort.
Vulnerability scans with Nessus: Can use the external Nessus programto periodically run vulnerability scans.
Isolation of problematic devices: One of the several isolation techniquesPacketFence support is VLAN isolation (with VoIP support), where problematic clients would be moved to a designated VLAN. Switches from many vendors are supported .
DHCP fingerprinting: Usedto automatically allow or disallow specific device types (such as VoIP phones or Wi-Fi equipped game systems).
http://www.practicallynetworked.com/security/packet_fence_tutorial.htm
. IP be easily spoofed is based
https://blog.microfocus.com/research/geo-fencing-securing-authentication/4275/
- What is
Packetfence ?Simply put , it's a Network Access Control (NAC) solution.In other words, if you want to controlwhat devices are allowed on your network,you should considera NAC .
Captive-portal for registration and remediation
Centralized wired and wireless management
802.1X support
Layer-2 isolation of problematic devices
Integration with the Snort IDS and the Nessus vulnerability scanner
https://www.techrepublic.com/article/how-to-install-packetfence-on-centos-7/
PacketFence reuses many components in an infrastructure.Nonetheless, it will install the following ones and manage them itself:
database server (MariaDB)
web server (Apache)
DHCP server (PacketFence)
RADIUS server (
firewall (
3.2. Minimum Hardware Requirements
The following provides a list of the minimum server hardware recommendations:
Intel or AMD CPU 3 GHz, 2 CPU cores
12 GB of RAM (16 GB recommended)
100 GB of disk space (RAID-1 recommended)
1 network card (2 recommended)
3.3. Operating System Requirements
Red Hat Enterprise Linux 7
Community ENTerprise Operating System (CentOS) 7
Debian 9.0 (Stretch)
https://packetfence.org/doc/PacketFence_Installation_Guide.html
- Captive portal: Can
be used to require users to login before using the network or to present instructions to a user on a web page, blocking all other network traffic, when a problemis detected .
Malware detection and alerting: Along with internal features,
Vulnerability scans with Nessus: Can use the external Nessus program
Isolation of problematic devices: One of the several isolation techniques
DHCP fingerprinting: Used
http://www.practicallynetworked.com/security/packet_fence_tutorial.htm
- What is geo-fencing?
https://blog.microfocus.com/research/geo-fencing-securing-authentication/4275/
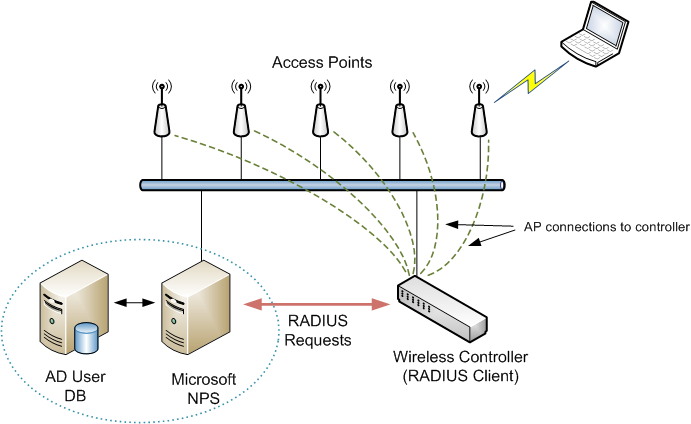
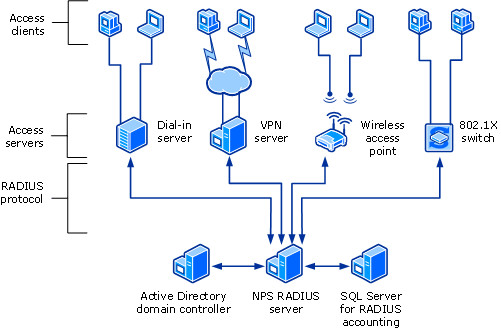
- Network Policy Server (NPS)
NPS is installed when you install the Network Policy and Access Services (NPAS) feature in Windows Server 2016 and Server 2019.
Network Policy Server (NPS) allows you to create and enforce organization-wide network access policies for connection request authentication and authorization.
You can also configure NPS as a Remote Authentication Dial-In User Service (RADIUS) proxy to forward connection requests to a remote NPS or other RADIUS server so that you can load balance connection requests and forward them to the correct domain for authentication and authorization.
RADIUS server
NPS performs centralized authentication, authorization, and accounting for wireless, authenticating switch, remote access dial-up and virtual private network (VPN)
connections
When you use NPS as a RADIUS server, you configure network access servers, such as wireless access points and VPN servers, as RADIUS clients in NPS.
You also configure network policies that NPS uses to authorize connection requests, and you can configure RADIUS accounting so that NPS logs accounting information to log files on the local hard disk or in a Microsoft SQL Server database
RADIUS proxy
RADIUS proxy. When you use NPS as a RADIUS proxy, you configure connection request policies that tell the NPS which connection requests to forward to other RADIUS servers and to which RADIUS servers you want to forward connection requests. You can also configure NPS to forward accounting data to be logged by one or more computers in a remote RADIUS server group
RADIUS accounting. You can configure NPS to log events to a local log file or to a local or remote instance of Microsoft SQL Server.
You can configure NPS with any combination of these features. For example, you can configure one NPS as a RADIUS server for VPN connections
and also as a RADIUS proxy to forward some connection requests to members of a remote RADIUS server group for authentication and authorization in another domain.
You can use NPS as a RADIUS server when:
You are using an AD DS domain or the local SAM user accounts database as your user account database for access clients.
You are using Remote Access on multiple dial-up servers, VPN servers, or demand-dial routers and you want to centralize both the configuration of network policies and connection logging and accounting.
You are outsourcing your dial-up, VPN, or wireless access to a service provider. The access servers use RADIUS to authenticate and authorize connections that are made by members of your organization.
You want to centralize authentication, authorization, and accounting for a heterogeneous set of access servers.
RADIUS server and RADIUS proxy configuration examples
NPS as a RADIUS server. In this example, NPS is configured as a RADIUS server, the default connection request policy is the only configured policy, and all connection requests are processed by the local NPS. The NPS can authenticate and authorize users whose accounts are in the domain of the NPS and in trusted domains.
NPS as a RADIUS proxy. In this example, the NPS is configured as a RADIUS proxy that forwards connection requests to remote RADIUS server groups in two untrusted domains.
NPS as both RADIUS server and RADIUS proxy. In addition to the default connection request policy, which designates that connection requests are processed locally, a new connection request policy is created that forwards connection requests to an NPS or other RADIUS server in an untrusted domain. This second policy is named the Proxy policy. In this example, the Proxy policy appears first in the ordered list of policies. If the connection request matches the Proxy policy, the connection request is forwarded to the RADIUS server in the remote RADIUS server group. If the connection request does not match the Proxy policy but does match the default connection request policy, NPS processes the connection request on the local server. If the connection request does not match either policy, it is discarded.
NPS as a RADIUS server with remote accounting servers. In this example, the local NPS is not configured to perform accounting and the default connection request policy is revised so that RADIUS accounting messages are forwarded to an NPS or other RADIUS server in a remote RADIUS server group. Although accounting messages are forwarded, authentication and authorization messages are not forwarded, and the local NPS performs these functions for the local domain and all trusted domains.
NPS with remote RADIUS to Windows user mapping. In this example, NPS acts as both a RADIUS server and as a RADIUS proxy for each individual connection request by forwarding the authentication request to a remote RADIUS server while using a local Windows user account for authorization. This configuration is implemented by configuring the Remote RADIUS to Windows User Mapping attribute as a condition of the connection request policy. (In addition, a user account must be created locally on the RADIUS server that has the same name as the remote user account against which authentication is performed by the remote RADIUS server.)
NPS logging is also called RADIUS accounting. Configure NPS logging to your requirements whether NPS is used as a RADIUS server, proxy, or any combination of these configurations.
https://learn.microsoft.com/en-us/windows-server/networking/technologies/nps/nps-top
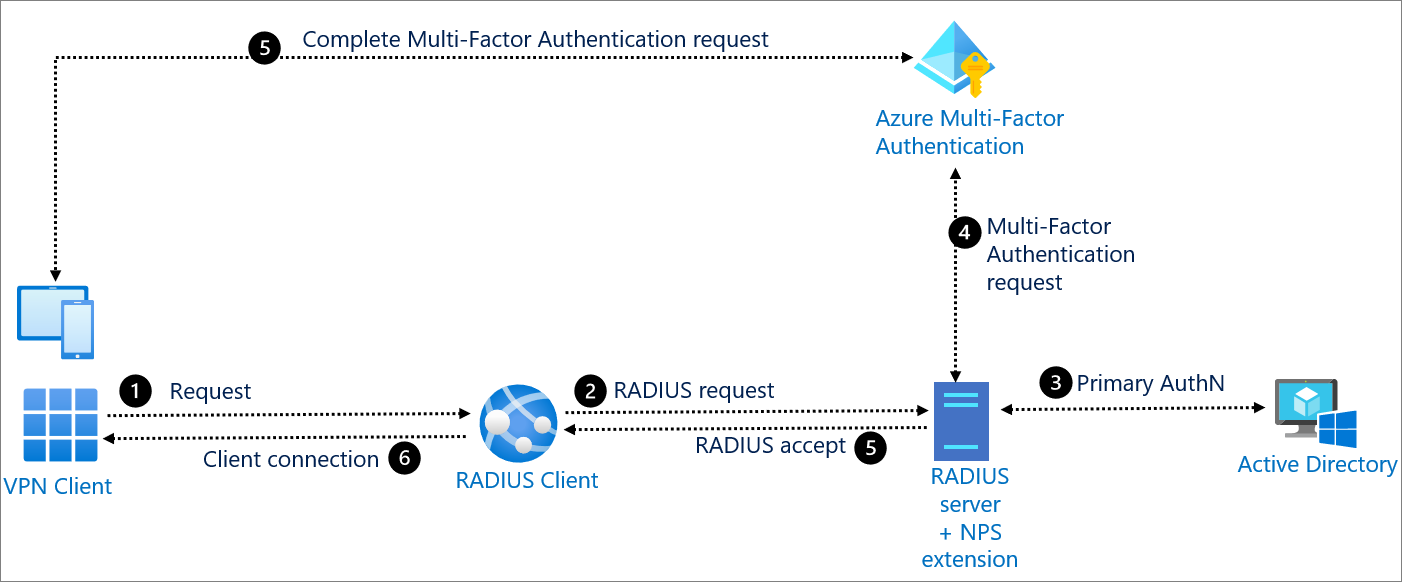
- Remote Authentication Dial-In User Service (RADIUS) is a networking protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use a network service.
RADIUS is a client/server protocol that runs in the application layer, and can use either TCP or UDP. Network access servers, which control access to a network, usually contain a RADIUS client component that communicates with the RADIUS server
RADIUS is often the back-end of choice for 802.1X authentication
Authentication and authorization
The user or machine sends a request to a Network Access Server (NAS) to gain access to a particular network resource using access credentials.
The credentials are passed to the NAS device via the link-layer protocol;for example, Point-to-Point Protocol (PPP) in the case of many dialup or DSL providers or posted in an HTTPS secure web form.
In turn, the NAS sends a RADIUS Access Request message to the RADIUS server, requesting authorization to grant access via the RADIUS protocol.
This request includes access credentials, typically in the form of username and password or security certificate provided by the user.
Additionally, the request may contain other information which the NAS knows about the user, such as its network address or phone number, and information regarding the user's physical point of attachment to the NAS.
The RADIUS server checks that the information is correct using authentication schemes such as PAP, CHAP or EAP.
The user's proof of identification is verified, along with, optionally, other information related to the request, such as the user's network address or phone number, account status, and specific network service access privileges
RADIUS servers checked the user's information against a locally stored flat file database. Modern RADIUS servers can do this, or can refer to external sources—commonly SQL, Kerberos, LDAP, or Active Directory servers—to verify the user's credentials
The RADIUS server then returns one of three responses to the NAS: 1) Access Reject, 2) Access Challenge, or 3) Access Accept
For example, the following authorization attributes may be included in an Access-Accept:
The specific IP address to be assigned to the user
The address pool from which the user's IP address should be chosen
The maximum length of time that the user may remain connected
An access list, priority queue or other restrictions on a user's access
L2TP parameters
VLAN parameters
Quality of Service (QoS) parameters
Accounting
Accounting is described in RFC 2866.
Packet structure
RADIUS is transported over UDP/IP on ports 1812 and 1813.
Attribute value pairs
The RADIUS Attribute Value Pairs (AVP) carry data in both the request and the response for the authentication, authorization, and accounting transactions.
Vendor-specific attributes
many vendors of RADIUS hardware and software implement their own variants using Vendor-Specific Attributes (VSAs).
https://en.wikipedia.org/wiki/RADIUS
- FreeRADIUS is a modular, high performance free RADIUS suite
The FreeRADIUS Suite includes a RADIUS server, a BSD-licensed RADIUS client library, a PAM library, an Apache module, and numerous additional RADIUS related utilities and development libraries
In most cases, the word "FreeRADIUS" refers to the free open-source RADIUS server from this suite.
It supports all common authentication protocols, and the server comes with a PHP-based web user administration tool called dialupadmin
It is the basis for many commercial RADIUS products and services, such as embedded systems, RADIUS appliances that support Network Access Control, and WiMAX
It is also widely used in the academic community, including eduroam.
Modules included with the server core support LDAP, MySQL, PostgreSQL, Oracle, and many other databases.
It supports all popular EAP authentication types, including PEAP and EAP-TTLS. More than 100 vendor dictionaries are included, ensuring compatibility with a wide range of NAS devices
https://en.wikipedia.org/wiki/FreeRADIUS
The FreeRADIUS Server Project is a high performance and highly configurable multi-protocol policy server, supporting RADIUS, DHCPv4 DHCPv6, TACACS+ and VMPS.
FreeRADIUS can authenticate users on systems such as 802.1x (WiFi), dialup, PPPoE, VPN's, VoIP, and many others.
https://github.com/FreeRADIUS/freeradius-server
- Network access control is a computer networking solution that uses a set of protocols to define and implement a policy that describes how to secure access to network nodes by devices when they initially attempt to access the network.
A basic form of NAC is the 802.1X standard
Network access control aims to do exactly what the name implies—control access to a network with policies, including pre-admission endpoint security policy checks and post-admission controls over where users and devices can go on a network and what they can do.
https://en.wikipedia.org/wiki/Network_Access_Control
- NAC is an appliance or virtual machine that controls device access to the network. It began as a
network authentication and authorization method for devices joining the network, which
follows the IEEE 802.1X standards
The authentication method involves three parties—
the Client device
the Authenticator
and the Authentication server
The authenticator could be a Network switch or Wireless access point that demarks the
protected network from the unprotected network. The client provides credentials in the form
of a Username and password, Digital certificate, or some other means, to the authenticator,
which forwards these credentials to the server. Pending on the outcome of authentication, the
authenticator will either block the device or allow it access to the network
Another method to
control access to a network, especially a publicly available network, is a Captive portal. If you’ve
ever connected to a network in an airport, hotel, or coffee shop, you might remember
interacting with a web page that asked you to agree to legal terms before granting access.
NAC evolved to accommodate:
Guest access
Bring Your Own Device BYOD
and the Internet of Things IoT
BYOD and IoT devices introduced new security challenges. One, BYODs
are personally owned, not assets of an organization
MIS does not control what runs on
these devices, for example, antivirus software or unsafe applications
IoT devices are hardware with a sensor that transmit data from one place to another over the internet,
dramatically expanding the attack surface
Organizations buy IoT-enabled devices from other
vendors, and these devices connect back to vendor networks to provide information about
product use and maintenance needs. Organizations tolerate this situation because IoT devices
save them time and money
For example, if a printer is low on toner, the vendor could notify
the network administrator by email, or even deliver new toner cartridges automatically. In a
smart home, IoT devices regulate heat and humidity, remotely control the locks on doors,
monitor what’s in the fridge, and even help with your grocery list
the variety of devices, the lack of standards, and the inability to secure these devices
make them a potential conduit for contagion to enter the network.
Many IoT devices lack the
CPU cycles or memory to host authentication and security software. They identify themselves
using a shared secret or unique serial number, which is inserted during manufacturing. But this
authentication scheme is very limited—should the secret become known, there is likely no way
to reset it, and without the ability to install security software, there is little visibility into those
devices
NAC evolved to solve these weaknesses
When MIS introduces NAC into a network, the first thing NAC does is create profiles of all
connected devices. NAC then permits access to network resources based on the device profile,
which is defined by function. This is similar to granting individuals access to sensitive
information based on their need to know. For example, NAC would permit an IP camera
connection to a network video recorder (NVR) server, but would prevent it from connecting to
a finance server. Based on its profile, an NVR has no business communicating with a finance
server. When access is granted this way, the network becomes segmented by device function. If
a device is compromised, malware can infect only those objects that the device is permitted to
connect to. So, the compromised IP camera from the earlier example could infect the NVR
server, but not the finance server
https://training.fortinet.com/pluginfile.php/1625583/mod_scorm/content/1/story_content/external_files/NSE%202%20NAC%20Script_EN.pdf



Great information. Also look into our top notch services and solution on IT infrastructure services in chennai . Experts in Annual Maintenance Contract (AMC) services in chennai, Cloud Management Services in chennai, Cyber Security Consulting Services in chennai, Access Points & Controllers in chennai NAC Implementation and Solutions in chennai
ReplyDeletesubcoosro Gary High https://wakelet.com/wake/g8WiBzA1SJb3gE5D_WgbU
ReplyDeletecarsingwhisfi